CompSec Direct is a security company based in Puerto Rico. The document discusses several security issues and efforts the company has worked on in Puerto Rico, including:
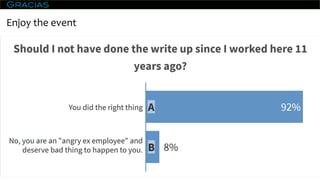
1) The Hacienda case, where the Treasury Department of Puerto Rico suffered a ransomware attack. The company was brought in but the IT staff were tired and did not provide written statements.
2) Exposing of court cases and personal information online from the judicial branch and a telecom provider. These issues have now been fixed.
3) Several other contributions and notifications to government entities regarding security issues, but the company has never been publicly thanked for their efforts.
4) Political discussions about campaign funding models in Puerto Rico and how securing