Video and slides synchronized, mp3 and slide download available at URL https://bit.ly/2Mb3oWl.
Thomas Graf talks about a new efficient in-kernel programming language called eBPF. It allows everyone to extend existing kernel components or glue them together in new forms without requiring to change the kernel itself. Filmed at qconsf.com.
Thomas Graf is co-founder & CTO at Covalent and creator of the Cilium project. Before this, he has been a Linux kernel developer at Red Hat for many years. Over the more than 15 years working on the Linux kernel, he was involved in a variety of networking and security subsystems. For the past couple of years, he has been involved in the development of BPF and XDP.









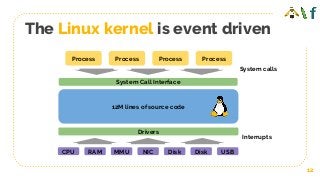
![Run BPF program on event
13
Process
NICDisk
Process
BPF
BPF
BPF
IORead
Sendnetwork
packet
connect()
Sockets
TCP/IP
Network Device
BPF
TCP
retrans
BPF
read()
File Descriptor
VFS
Block Device
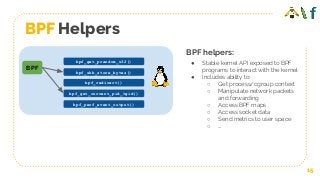
Attachment points
● Kernel functions (kprobes)
● Userspace functions (uprobe)
● System calls
● Tracepoints
● Network devices (packet level)
● Sockets (data level)
● Network device (DMA level) [XDP]
● ...](https://image.slidesharecdn.com/untitled-190114125152/85/How-to-Make-Linux-Microservice-aware-with-Cilium-and-eBPF-15-320.jpg?cb=1547470526)