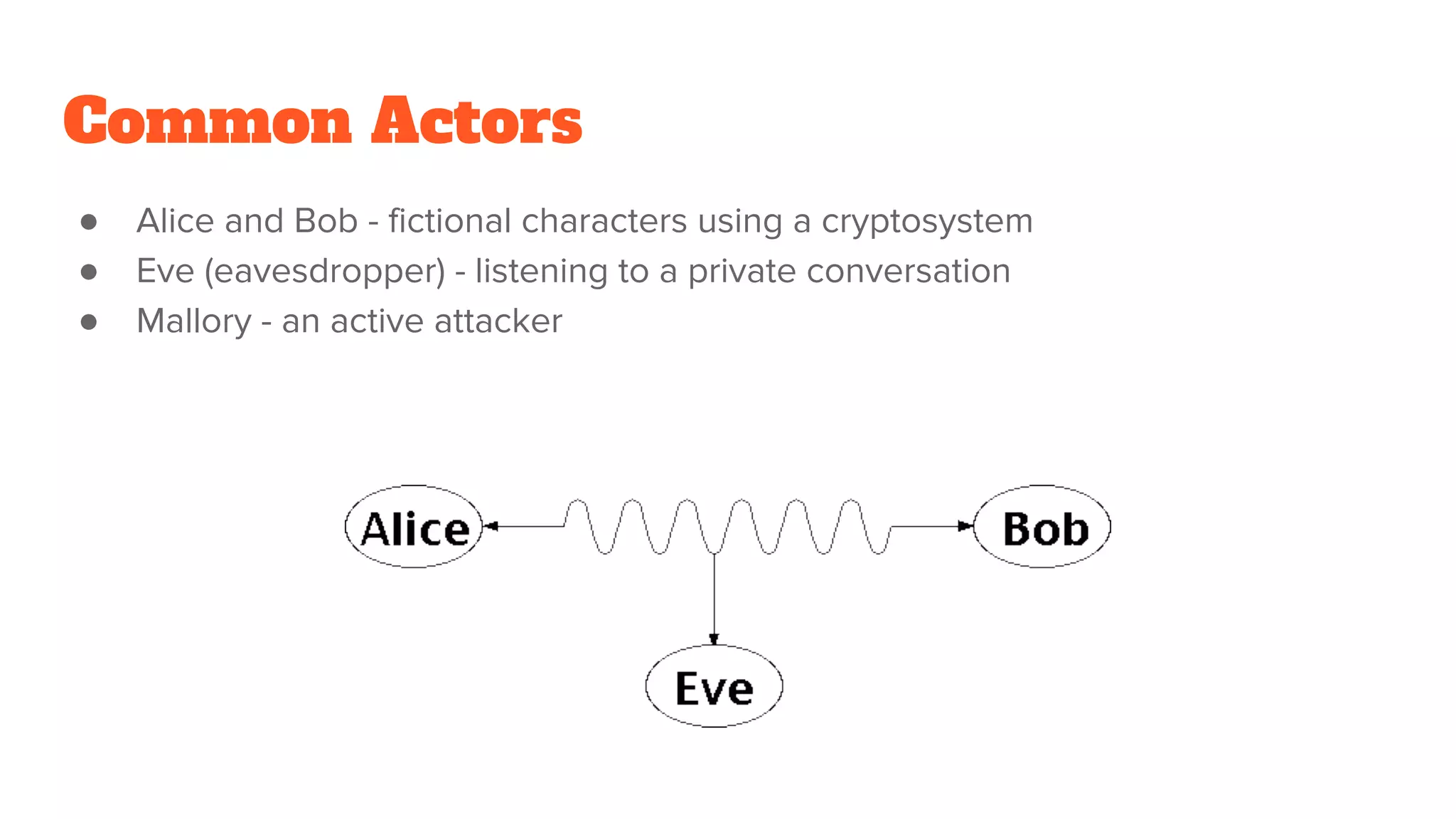
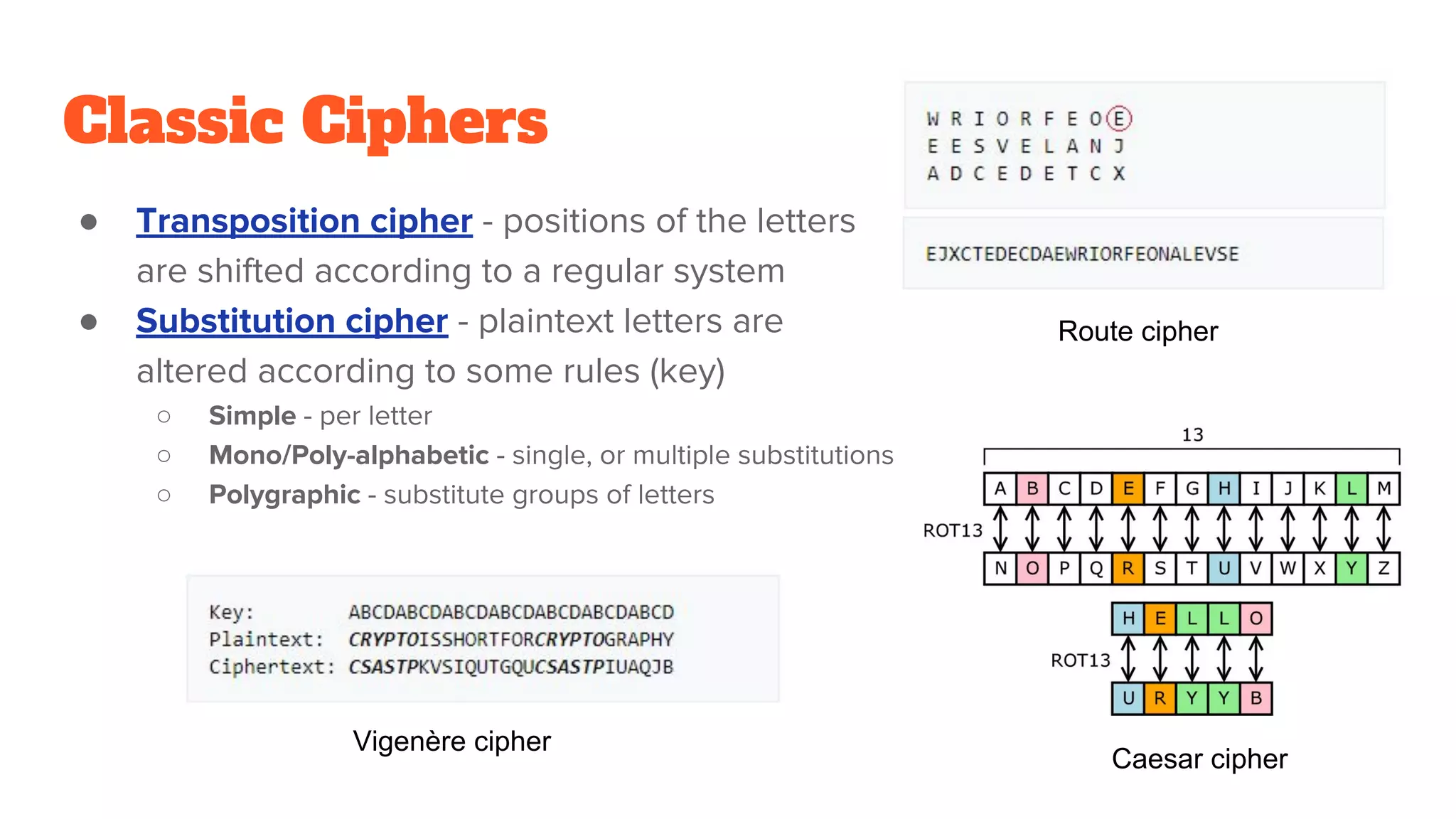
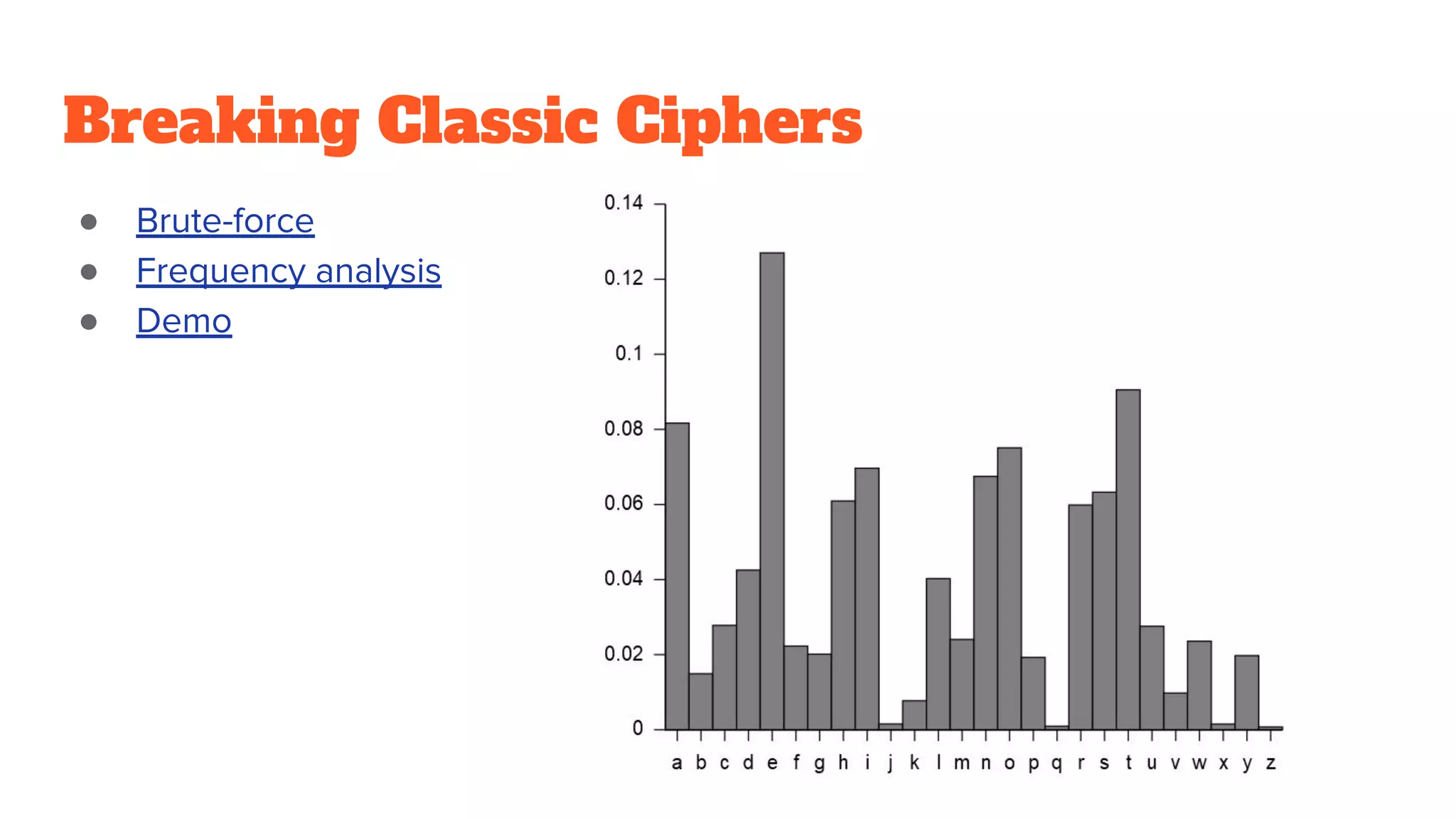
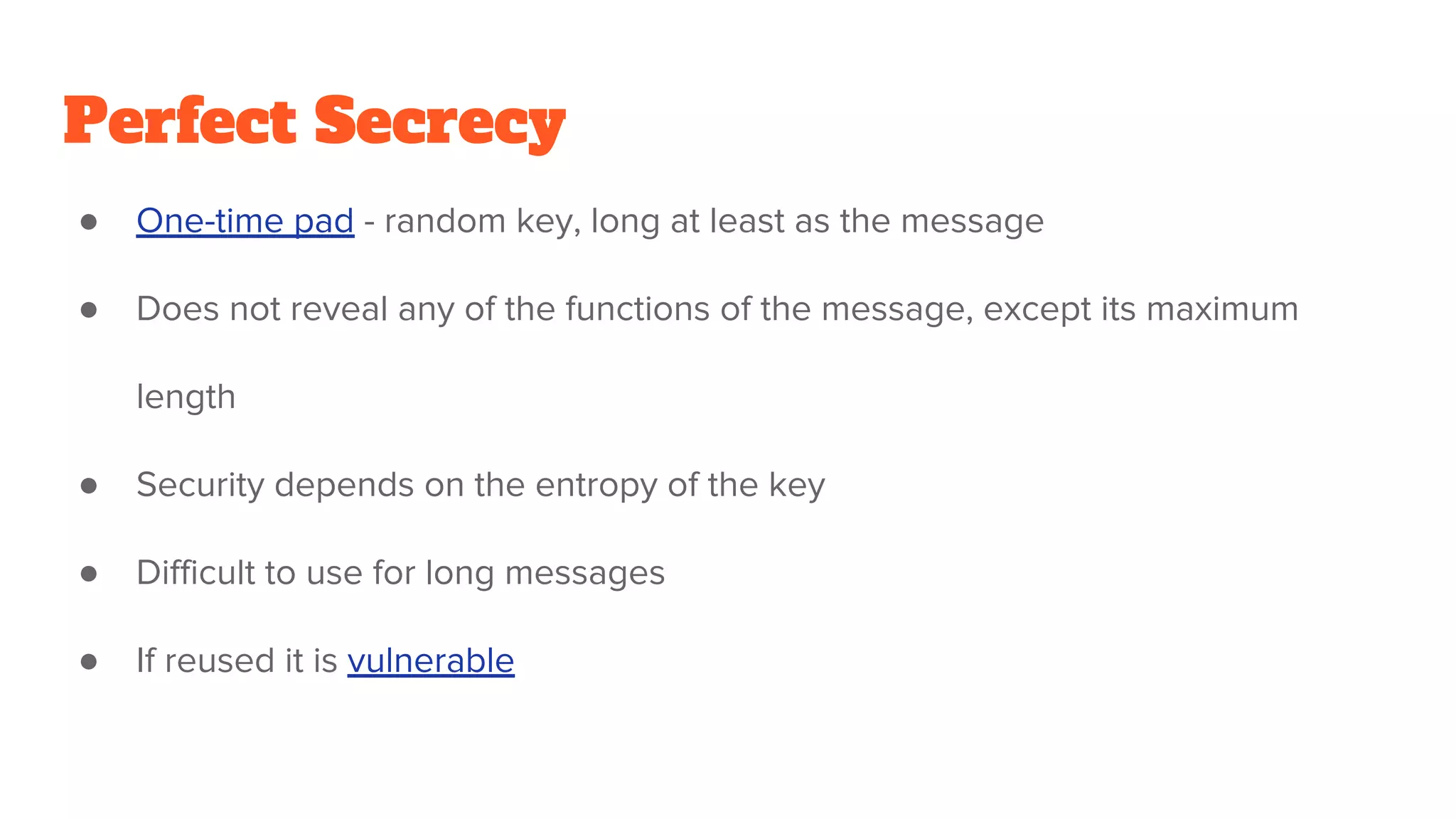
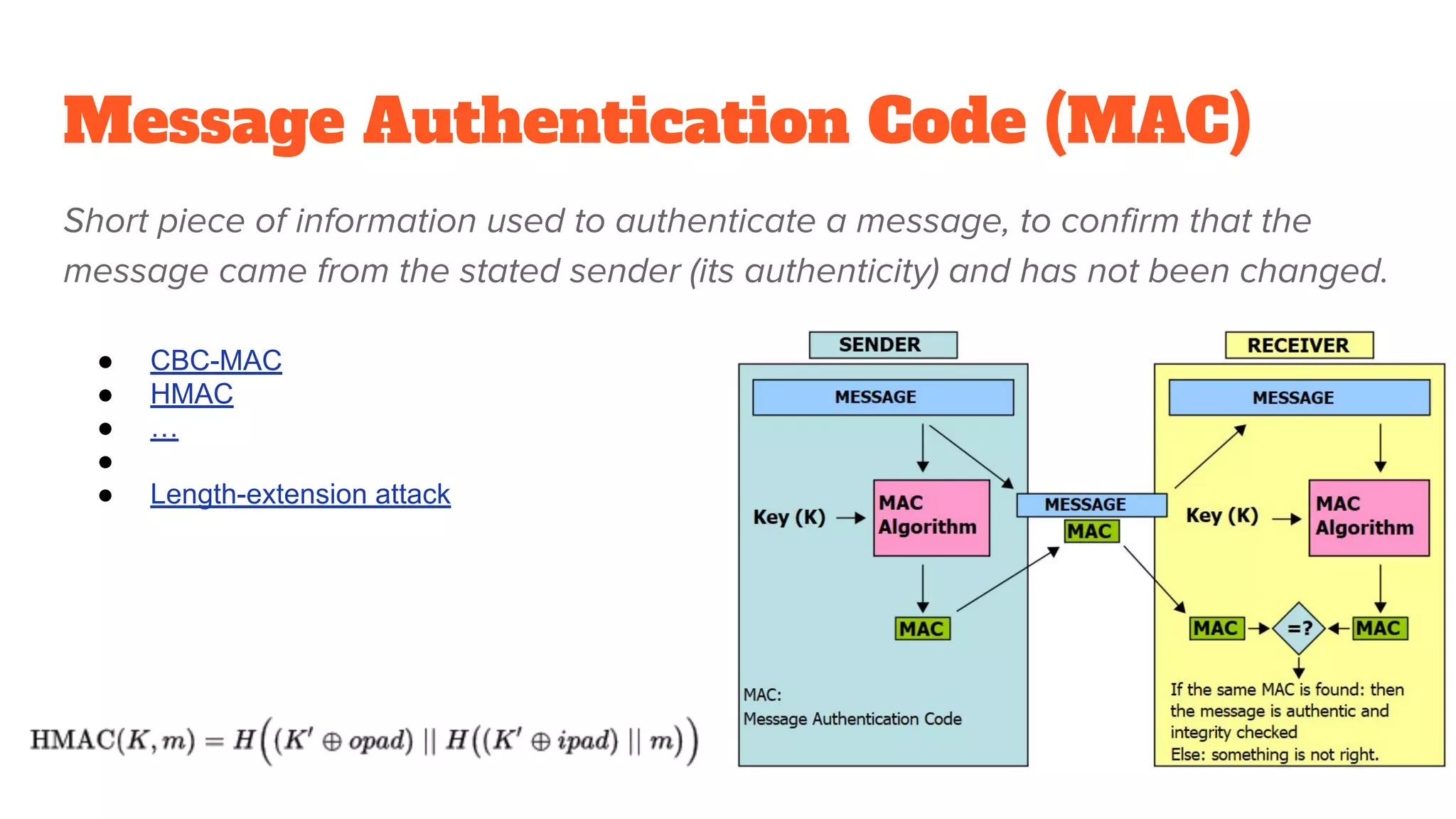
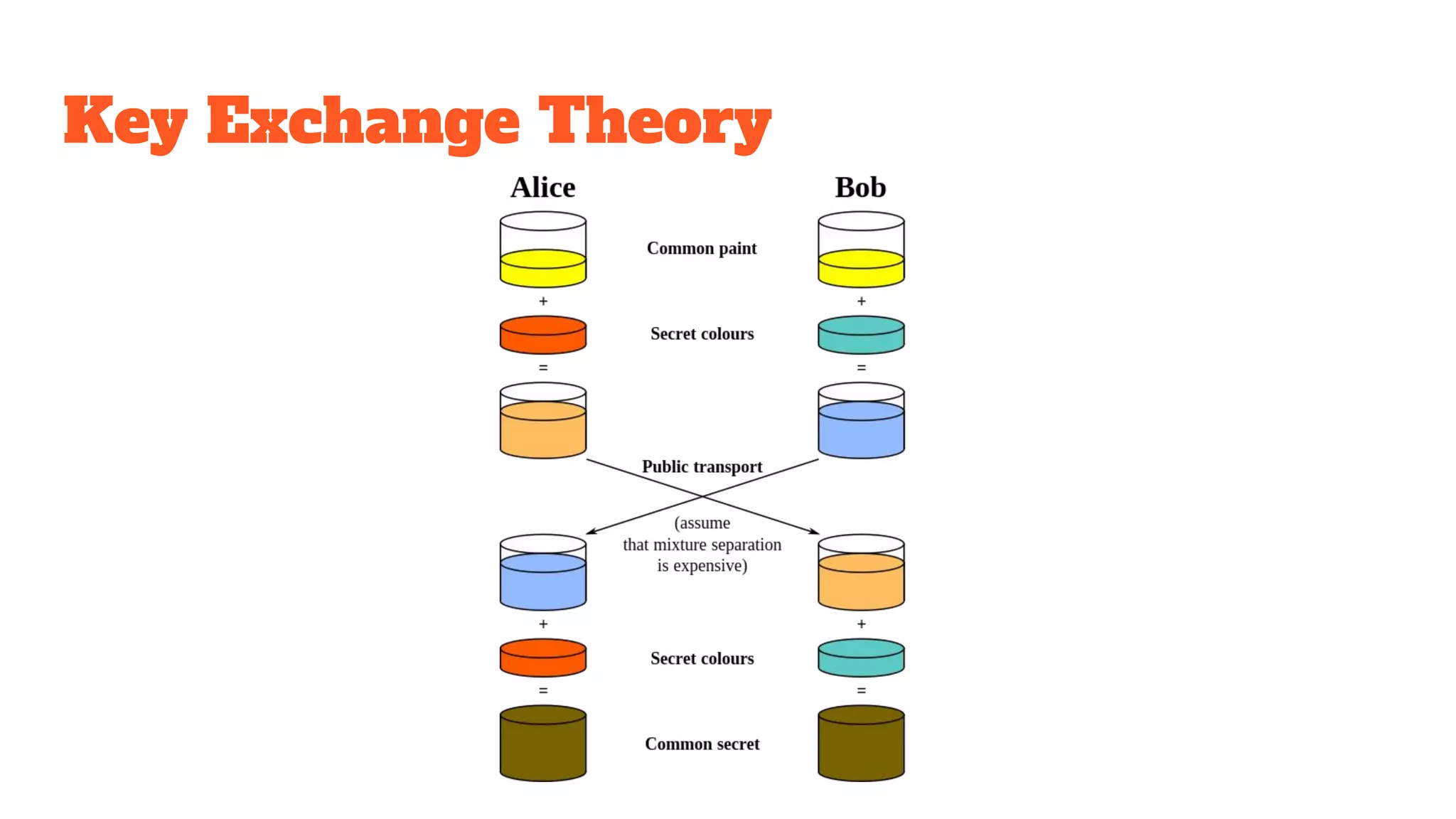
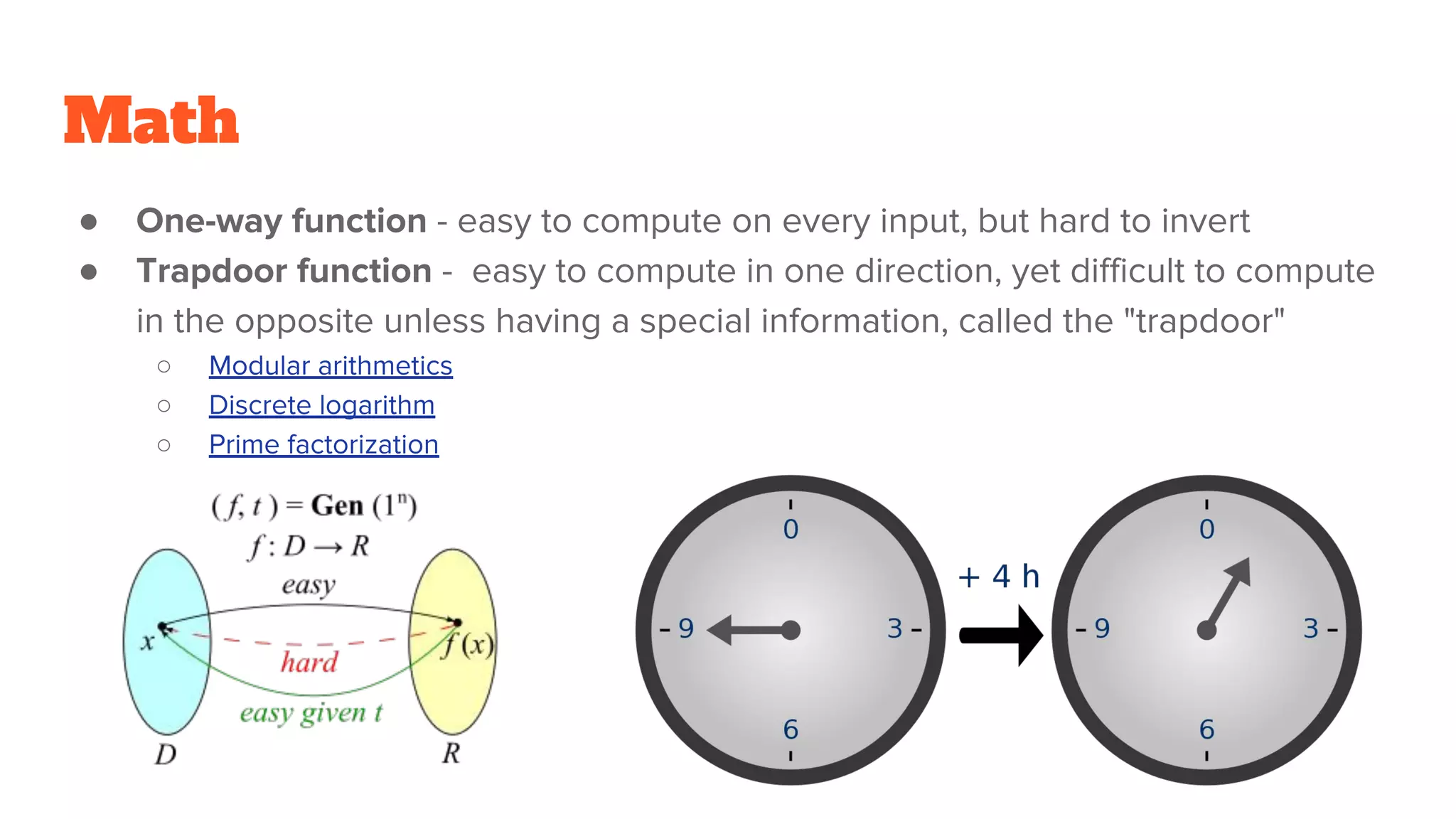
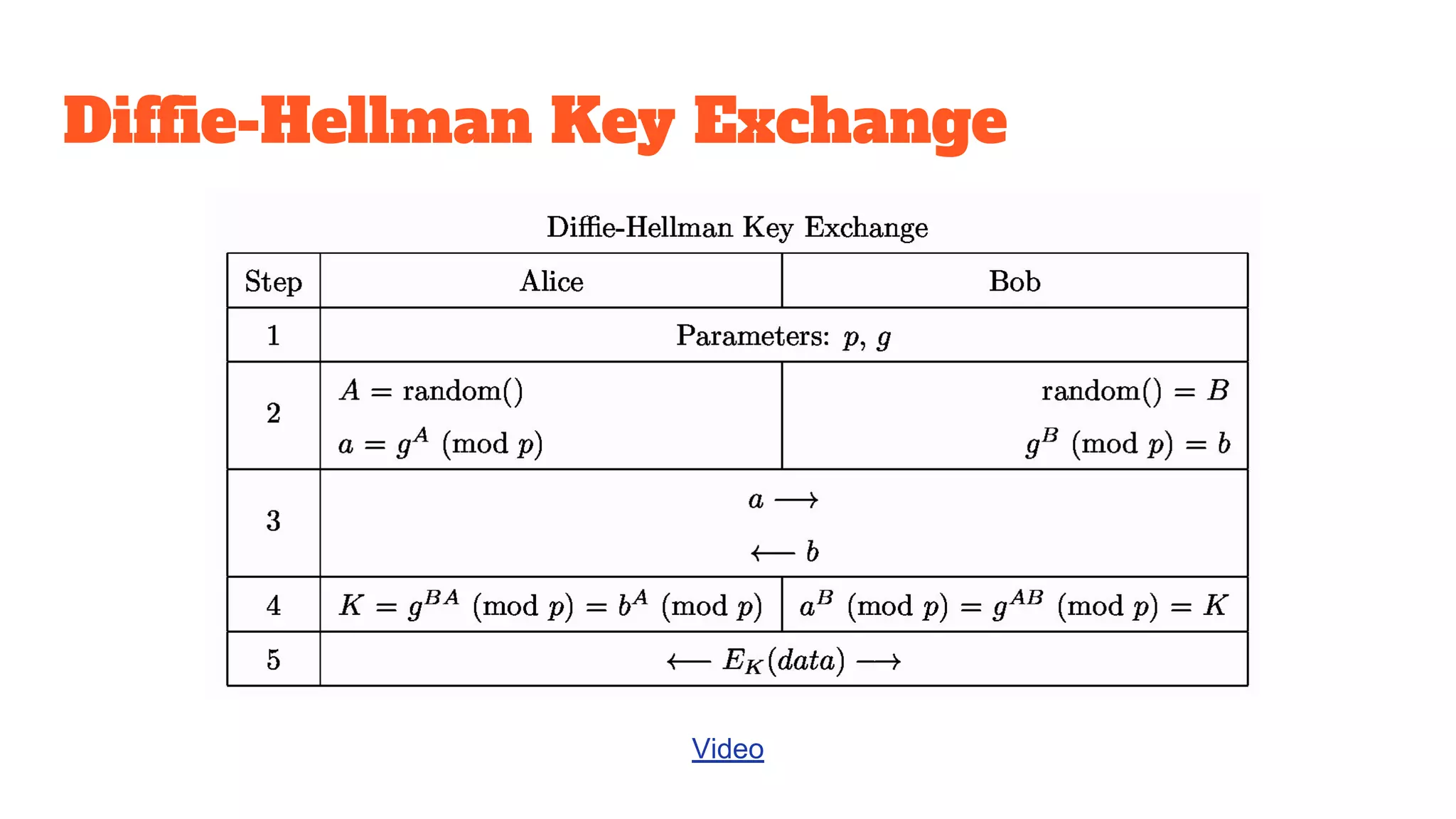
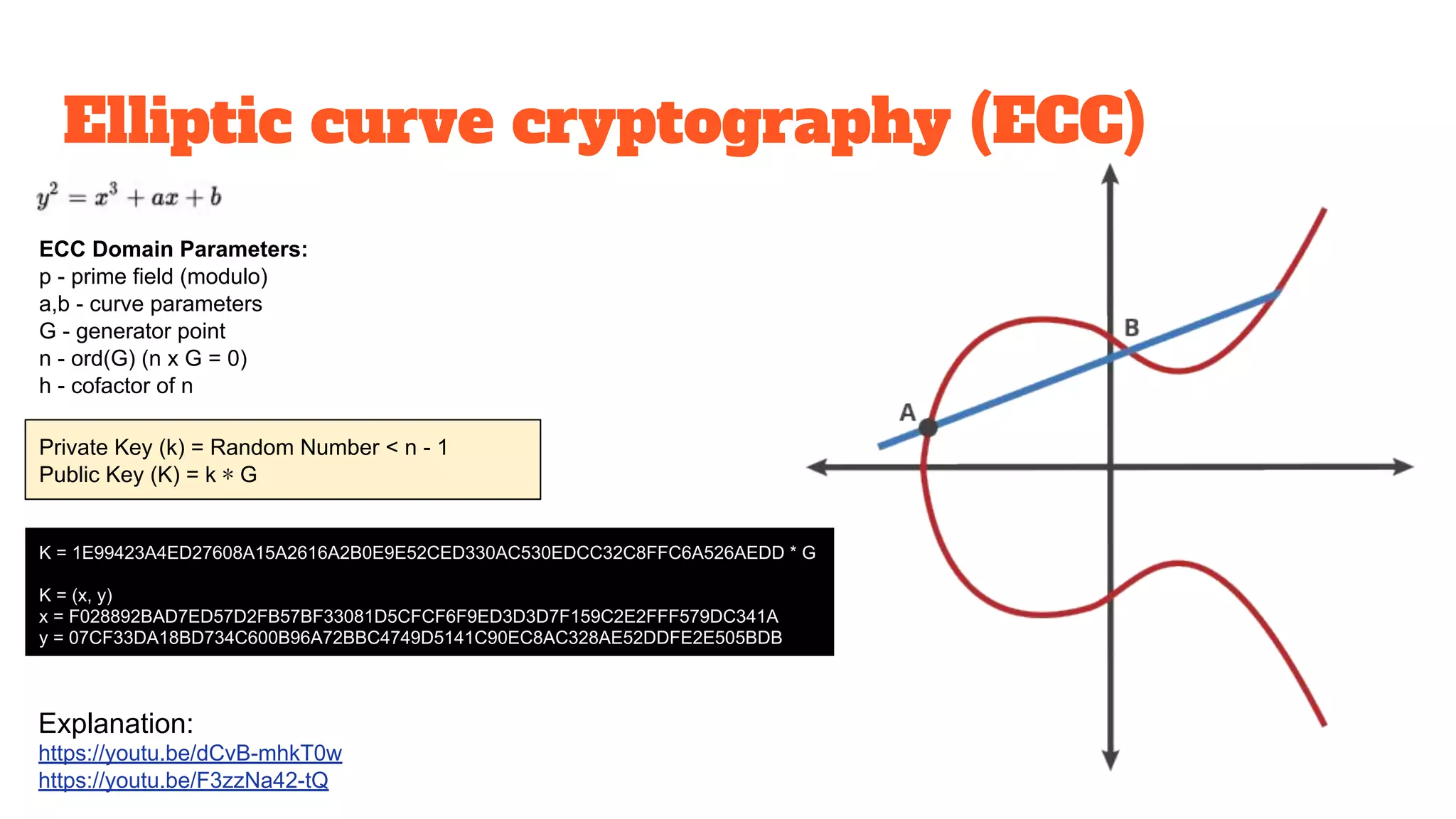
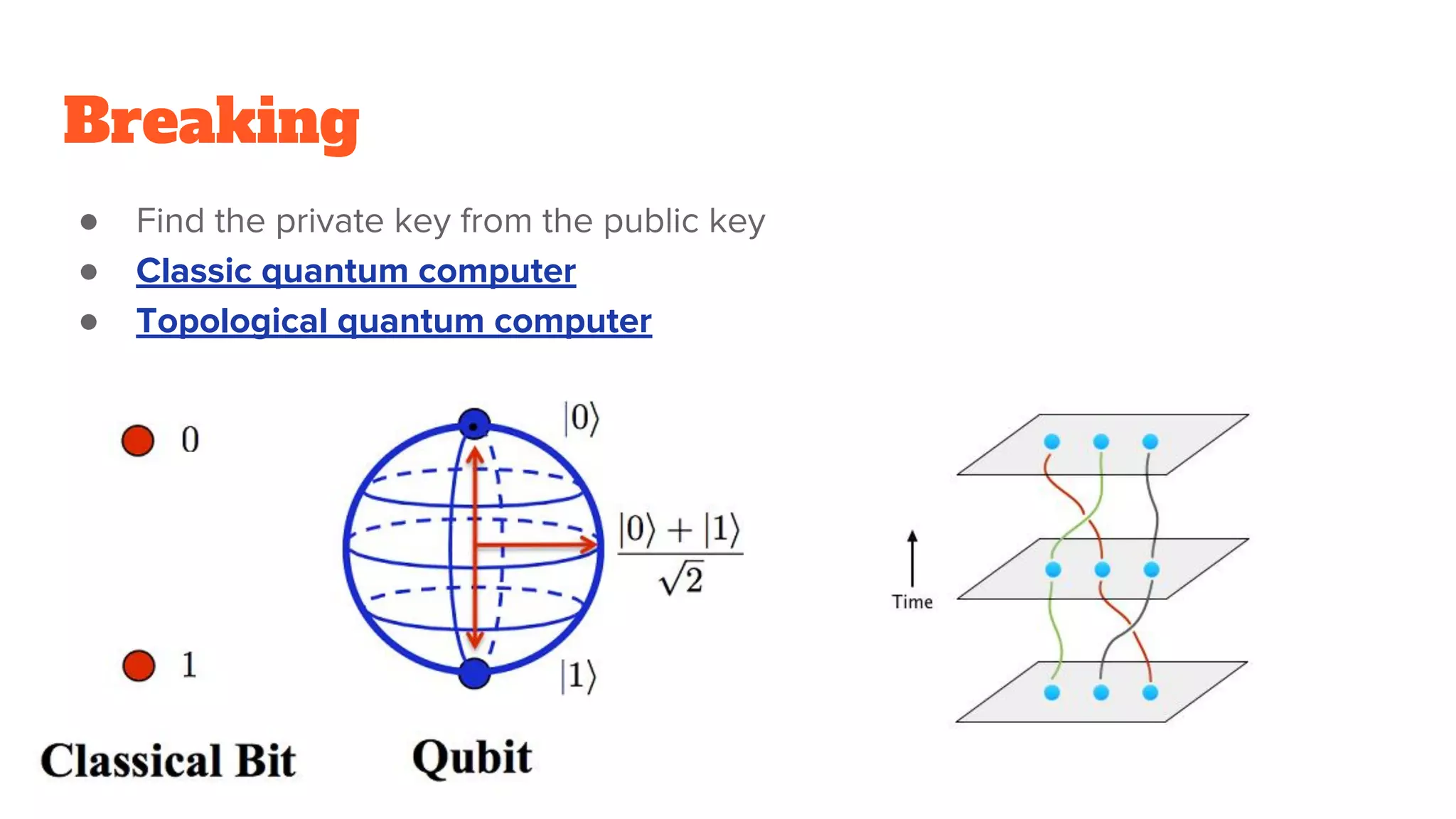
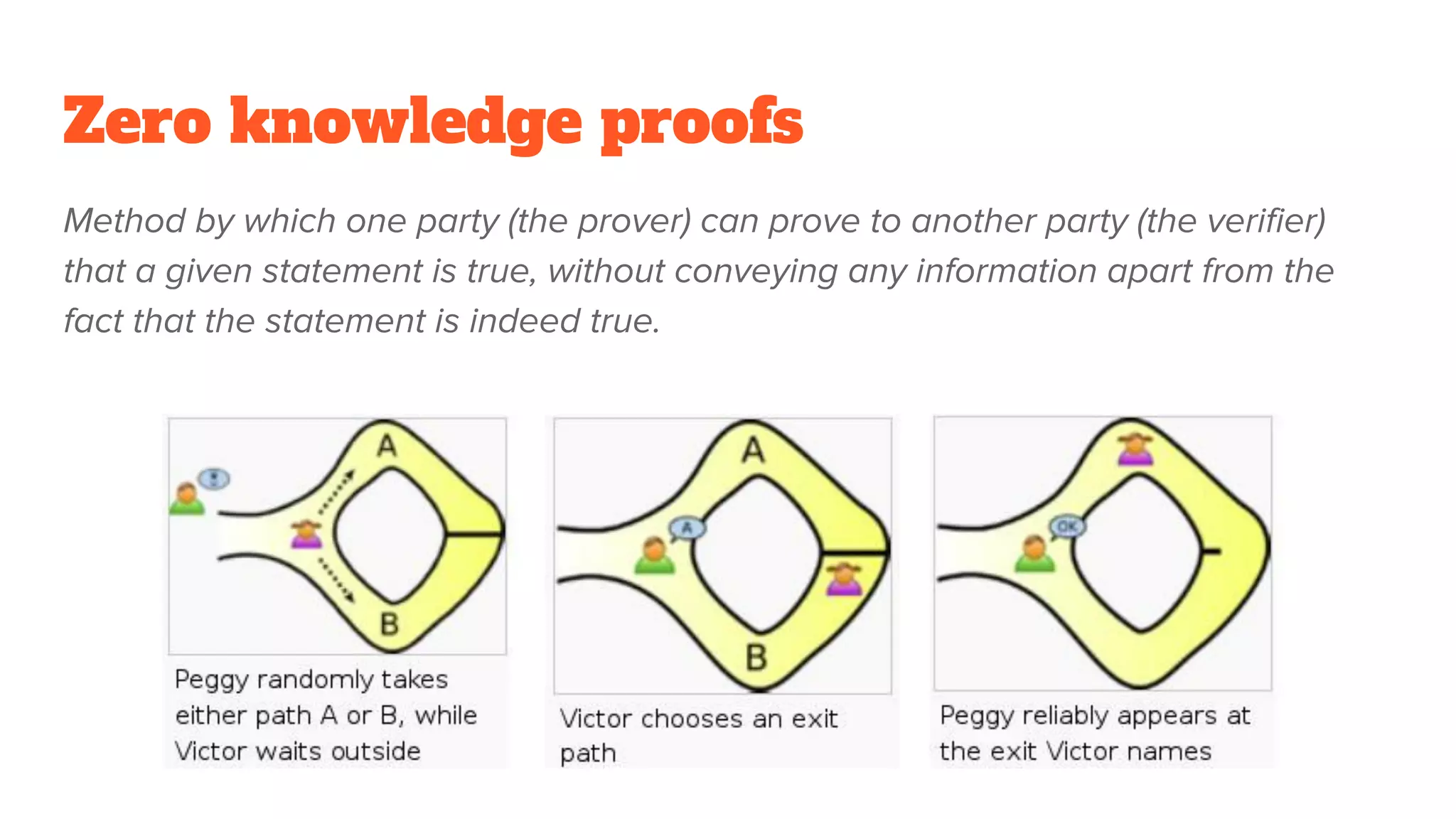
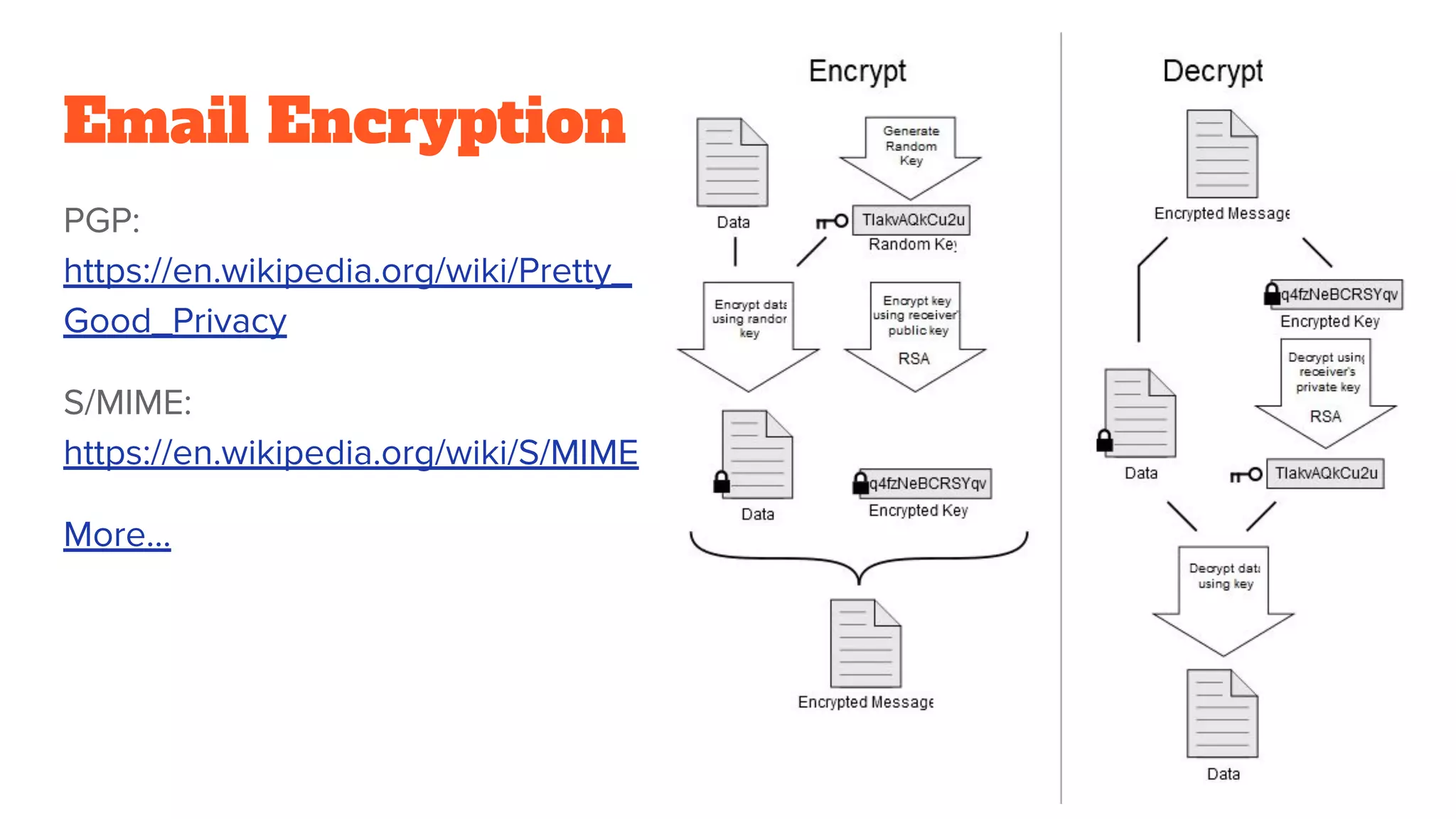
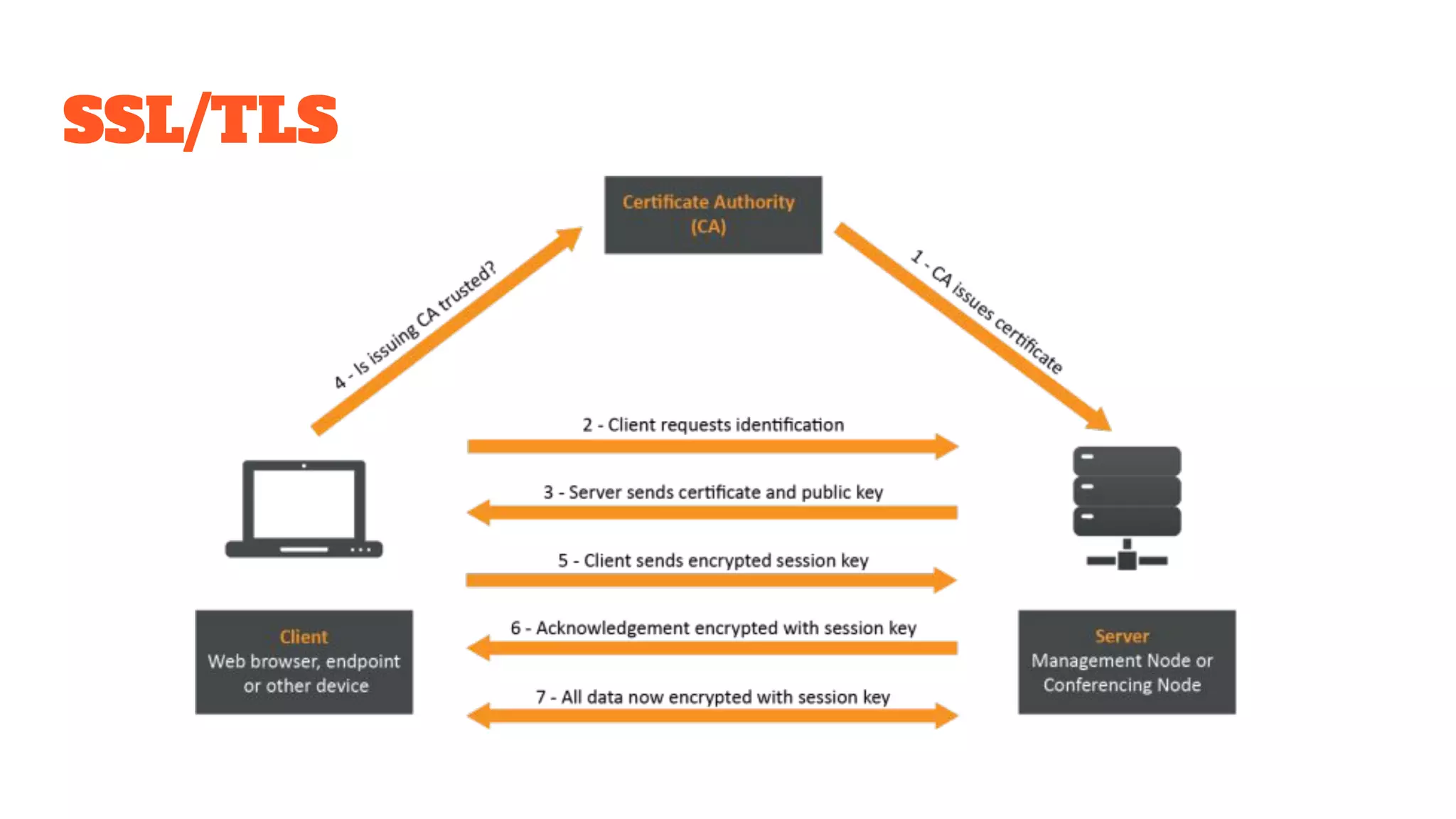
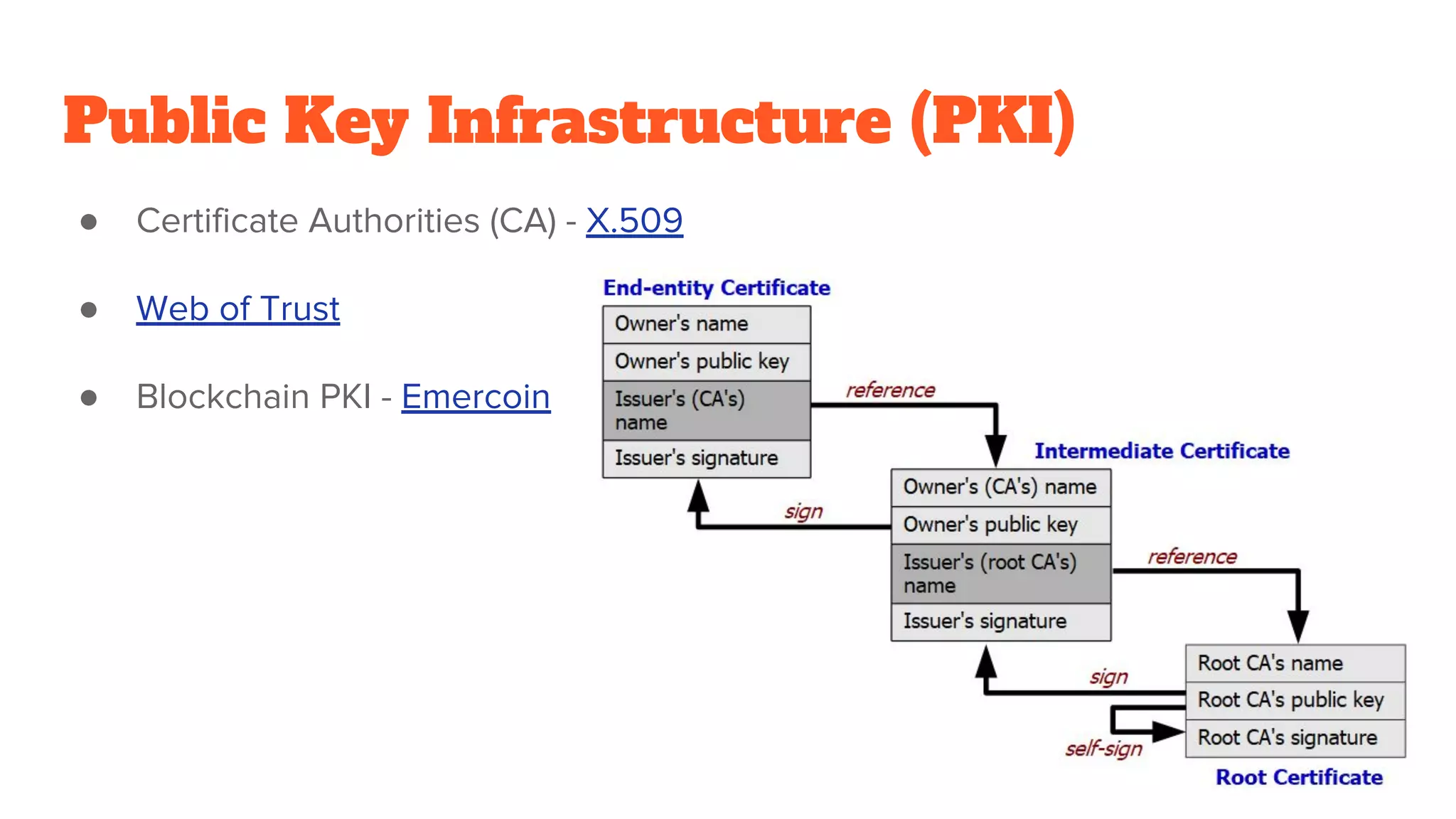
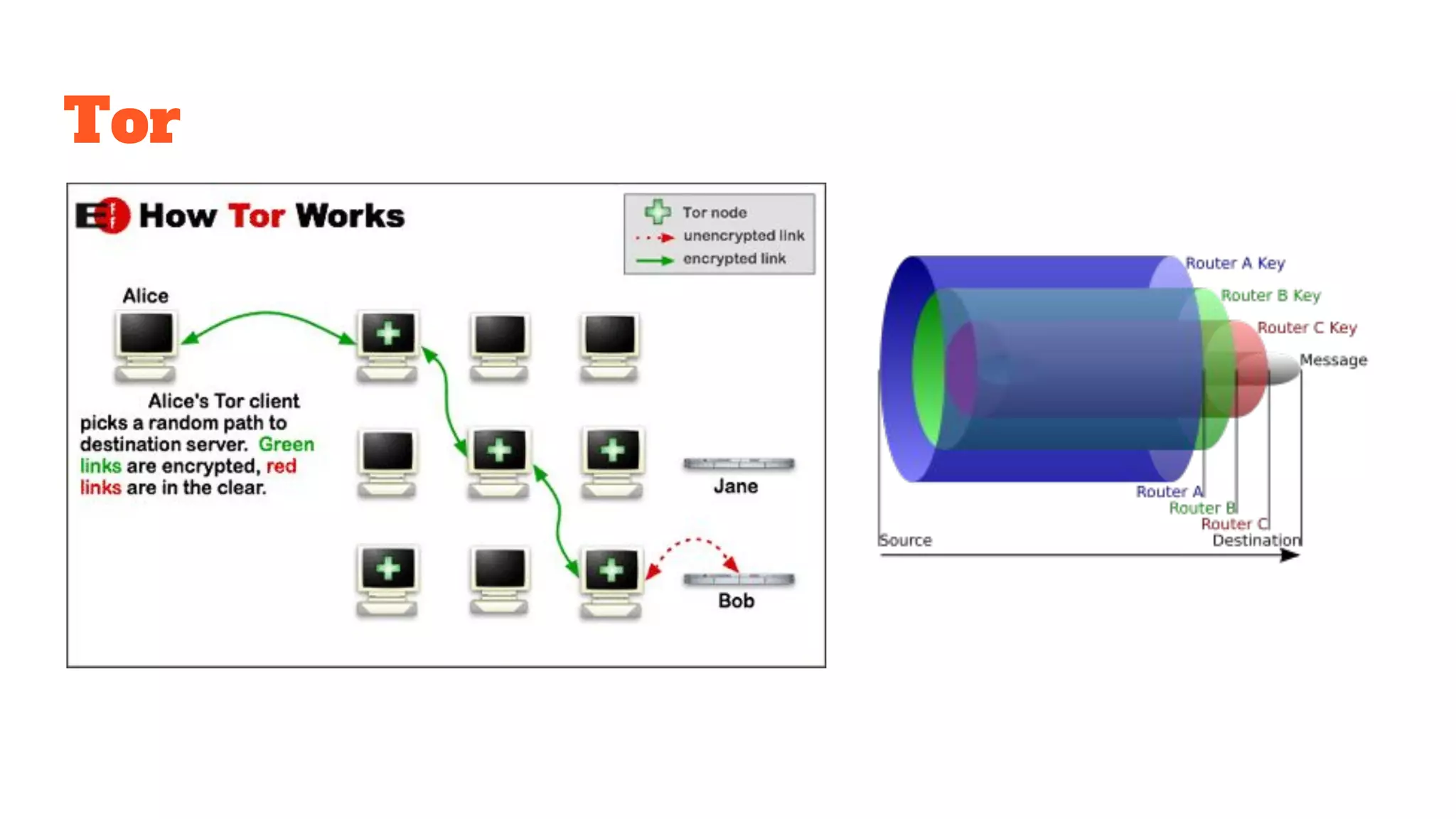
The document provides a comprehensive introduction to cryptography, discussing key concepts such as encryption, decryption, and the various types of cryptographic systems including symmetric and asymmetric methods. It covers historical and modern developments in the field, different ciphers, data integrity mechanisms like hash functions, and the principles of public-key cryptography. Additionally, it outlines techniques for secure communication and data sharing, along with practical applications in digital signatures and email encryption.