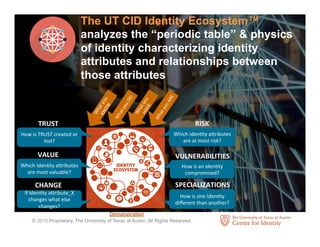
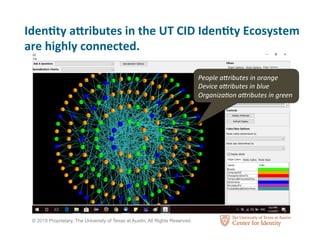
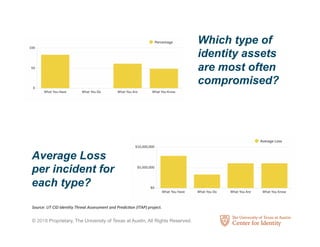
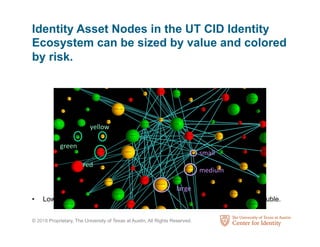
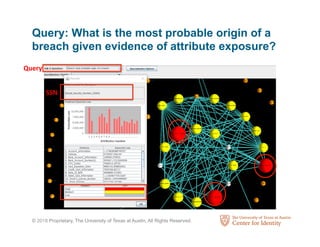
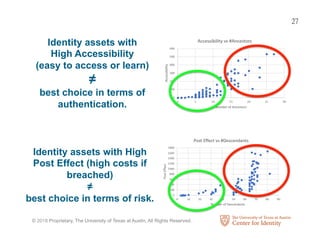
The Center for Identity at the University of Texas at Austin conducts interdisciplinary research on identity security and privacy. It aims to address identity challenges through research, education, and outreach. The Center studies how identity assets are used for legitimate and fraudulent purposes. It also analyzes hundreds of corporate privacy policies and investigates how identity attributes are connected and how their value and risk levels impact identity ecosystems. The Center educates professionals on identity leadership and management through certificates and courses.