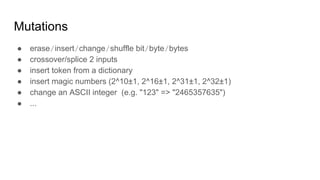
Fuzzing is a software testing technique that involves providing invalid, unexpected, or random data as inputs to a computer program to detect bugs. Coverage-guided fuzzing uses genetic algorithms to generate inputs that maximize code coverage. It is effective at finding security bugs like overflows, memory errors, and crashes. The presenter demonstrates finding 13 bugs in Boost regex in 30 minutes using libFuzzer. Fuzzing is widely used at Google to test critical software like browsers, libraries, and the Linux kernel due to its ability to find many bugs without requiring test cases.







![Coverage-guiding in action
if input[0] == '{' {
if input[1] == 'i' && input[2] == 'f' {
if input[3] == '(' {
input[input[4]] = input[5]; // potential OOB write
}
}
}
Requires "{if(" input to crash, ~2^32 guesses to crack when blind.
Coverage-guiding:
Guess "{" in ~2^8, add to corpus.
Guess "{i" in ~2^8, add to corpus.
Guess "{if" in ~2^8, add to corpus.
Guess "{if(" in ~2^8, add to corpus.
Total: ~2^10 guesses.
See: AFL: Pulling JPEGs out of thin air](https://image.slidesharecdn.com/fuzzing-thenewunittestingcrussia-170220114321/85/Fuzzing-The-New-Unit-Testing-10-320.jpg)