What is Android app Pentesting in 2022- DetoxTechnologies.pdf
- 1. 1/3 What is Android app Pentesting in 2022- Detox Technologies detoxtechnologies.wordpress.com/2022/04/14/what-is-android-app-pentesting-in-2022-detox-technologies/ Android applications have proven to be the most popular choice among consumers, surpassing desktop programmers. There is a diverse range of applications accessible for Android smartphones. But Insecure Android applications endanger consumers’ privacy and security. Furthermore, such programmers may cause financial losses. This is largely owing to the Android ecosystem’s openness. Cyberattacks on mobile applications are becoming more widespread than ever. Android penetration testing is one of the most efficient approaches for enhancing the security of an Android app. This blog article will explain the relevance of android penetration testing, how it helps organizations protect themselves against hackers and malicious, and much more about android penetration testing. What is Android Penetration Testing? Android penetration testing is the process of finding security bugs in an Android application.It is a methodical technique of searching for flaws in an Android app, confirming its security, and ensuring compliance with security regulations. It entails attempting to attack the Android application using various approaches and tools.
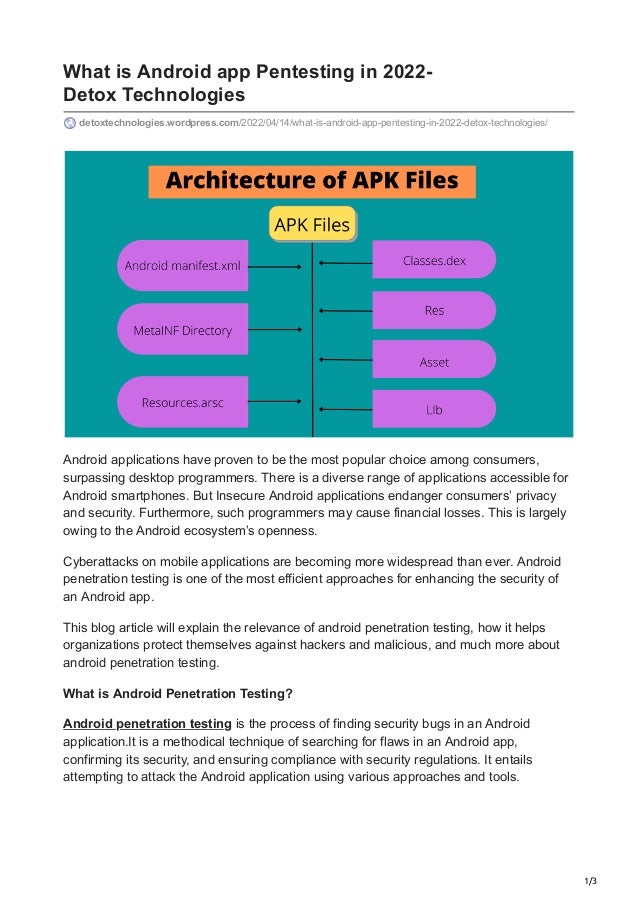
- 2. 2/3 The basic goal of android penetration testing is to identify and repair application vulnerabilities before hackers attack them. Data theft, information leakage, and other security threats are the most common. Understanding the Architecture of an Android App An APK file is an archive file that is used to send an application’s binary files to the end user. The APK file is not part of the Android operating system. The APK file, which is placed on the device’s system partition, is used to install applications on Android devices. Why is Android Penetration Testing so important? Android applications are utilized for a variety of purposes in today’s society, including mobile banking, shopping, exchanging personal information, social networking, and entertainment. Android devices are subject to a variety of hacking techniques, including buffer overflow, code injection, reverse engineering, malware, and others. Android penetration testing is the detection and testing of vulnerabilities in Android applications in order to identify and resolve application vulnerabilities. Some of the benefits of android penetration testing are as follows: · Discover the security flaws in Android apps. · Enhance the application’s efficiency. · gaining the trust of customers · Reduce the cost of a data breach. Focus Areas for Android Penetration Testing
- 3. 3/3 1. Data Retention Android penetration testing includes testing for data storage in an android application. These tests should contain the following: · Examining Hardcoded Credentials · Exposed sensitive data, such as API keys or tokens · Weak cryptography and encryption 2.Communication at the application level Communication between an app and other programmes, as well as with the app’s servers, can result in severe security breaches if not done through a secure channel. Man-in-the-middle attacks are used by hackers to intercept communication between mobile applications and servers. 3. Debug and error messages To identify particular application-level difficulties, developers employ a variety of error or debug messages while building an Android application. These error notices are frequently left even after the product has been manufactured. Hackers utilize these error messages to interpret the application’s flow and secret functionality. 4. Authentication and Authorization While performing Android penetration testing, it is critical to test authentication and authorisation. These tests should contain the following: Session-related security concerns Session token storage Checks for authentication on sensitive endpoints Inadequate access restrictions 5. Obfuscation of Code Code obfuscation is the process of concealing code in order to conceal its function.Obfuscated code is difficult to reverse-engineer. Obfuscation is used to protect intellectual property and to prevent tampering. Conclusion To summarize, there are several reasons why you should consider penetration testing for your Android apps. Whether you’re a minor startup or a large corporation, Android application penetration testing is essential and will continue to be so
