CVoR v0.4 DRAFT2
•
0 likes•147 views
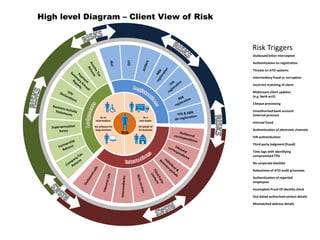
This document discusses various types of fraud risks that could impact the Australia Taxation Office's systems, including intermediary fraud, issues with client authentication and verification, potential threats to ATO systems, internal fraud, and risks related to client updates, electronic channels, tax file number monitoring, and audit processes. It also mentions developing a corporate blacklist and diagrams showing a client view of risk.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
What's hot
What's hot (15)
Suspicious Activities Reports, Perceptions and Reality in AML Investigations

Suspicious Activities Reports, Perceptions and Reality in AML Investigations
More from Daniel Grbac
More from Daniel Grbac (8)
CVoR v0.4 DRAFT2
- 1. Intermediary fraud or corruption Authentication on registration Outbound letter intercepted Threats on ATO systems IVR authentication Cheque processing Incorrect matching of client Internal fraud Out-dated authorised contact details Incomplete Proof Of Identity check Mismatched address details Third party lodgment (fraud) Unauthorised bank account (internal process) Midstream client updates (e.g. bank acct) Authentication of electronic channels Time lags with identifying compromised TFN No corporate blacklist Robustness of ATO audit processes Authentication of reported employees Risk Triggers High level Diagram – Client View of Risk Bob As an intermediary As a sole trader Via software for large business On behalf of his business