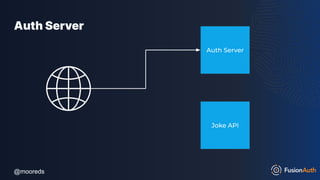
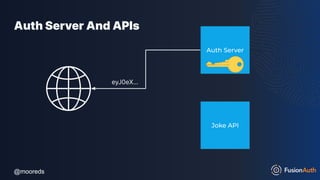
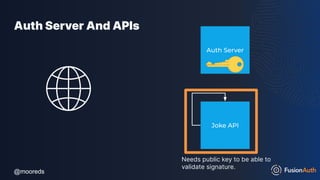
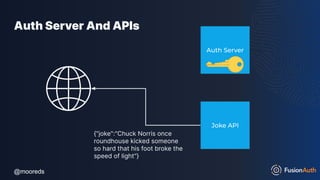
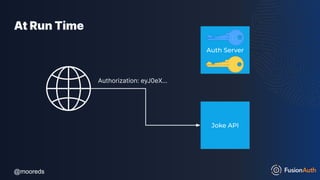
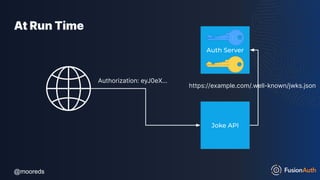
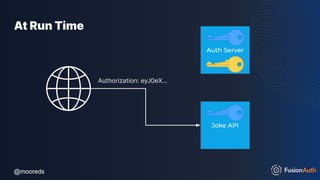
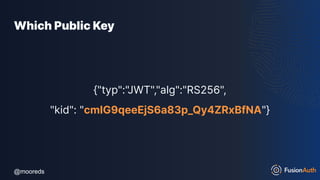
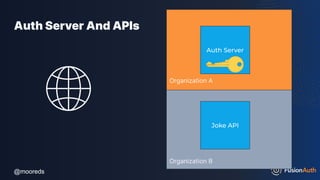
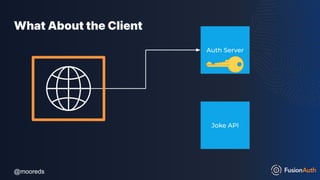
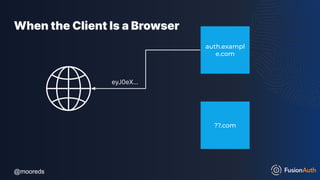
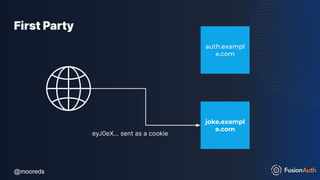
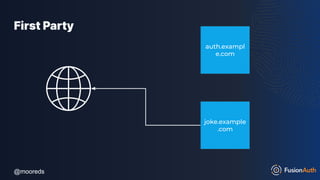
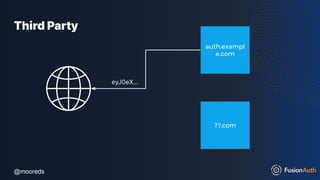
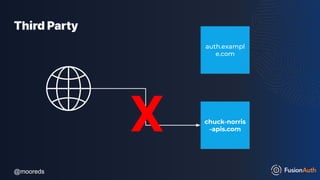
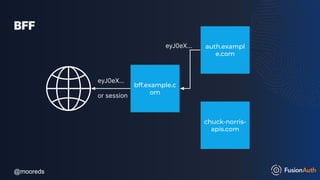
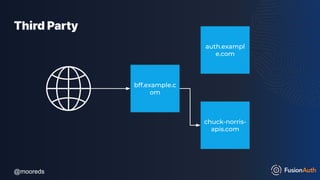
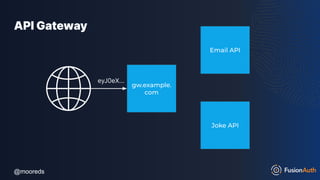
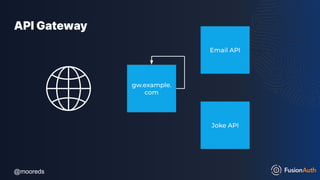
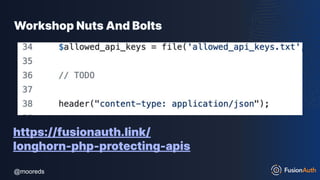
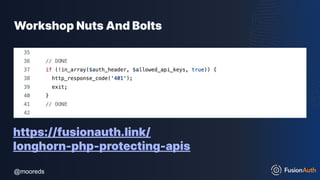
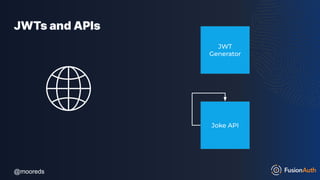
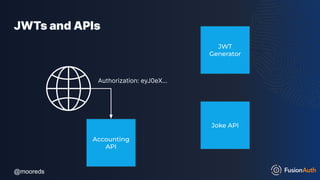
The document discusses protecting APIs using FusionAuth and various authentication methods, including API keys and JSON Web Tokens (JWTs). It covers the strengths and weaknesses of these methods, the structure of JWTs, and how they can be used to validate user identity and authorization. The workshop also includes interactive elements for attendees to engage with each other and explore API-related questions.





















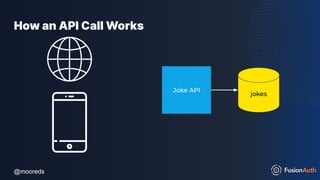
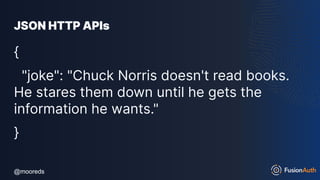
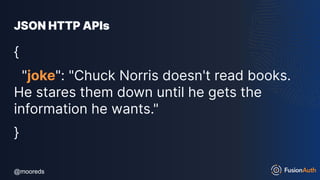


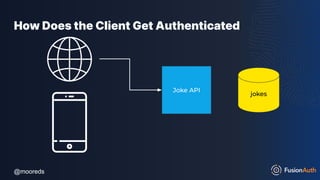




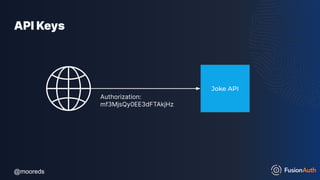









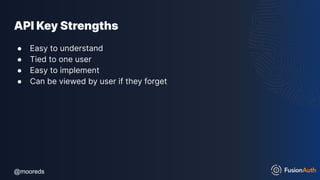






































![@mooreds
@mooreds
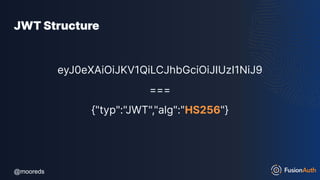
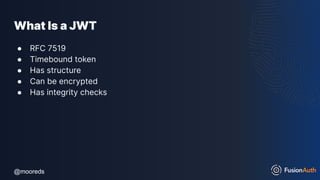
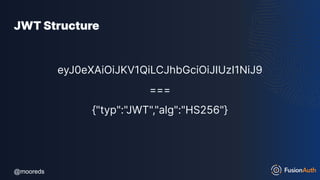
JWT Structure
eyJpc3MiOiJmdXNpb25hdXRoLmlvIiwiZXhwIjoxNjk3NzQxMTM1L
CJhdWQiOiIyMzhkNDc5My03MGRlLTQxODMtOTcwNy00OGVkO
GVjZDE5ZDkiLCJzdWIiOiIxOTAxNmI3My0zZmZhLTRiMjYtODBkO
C1hYTkyODc3Mzg2NzciLCJuYW1lIjoiRGFuIE1vb3JlIiwicm9sZXMi
OlsiUkVUUklFVkVfSk9LRVMiXX0=
===
{"iss":"fusionauth.io","exp":1697741135,"aud":"238d4793-70de-41
83-9707-48ed8ecd19d9","sub":"19016b73-3ffa-4b26-80d8-aa9
287738677","name":"Dan Moore","roles":["RETRIEVE_JOKES"]}](https://image.slidesharecdn.com/protectingyourapis-231103024257-47bb9cb3/85/Protecting-Your-APIs-pdf-101-320.jpg)

![@mooreds
@mooreds
JWT Body
{
"iss": "fusionauth.io",
"exp": 1697741135,
"aud": "238d4793-70de-4183-9707-48ed8ecd19d9",
"sub": "19016b73-3ffa-4b26-80d8-aa9287738677",
"name": "Dan Moore",
"roles": [
"RETRIEVE_JOKES"
]
}](https://image.slidesharecdn.com/protectingyourapis-231103024257-47bb9cb3/85/Protecting-Your-APIs-pdf-103-320.jpg)















![@mooreds
@mooreds
Validate the Issuer
{
"iss": "fusionauth.io",
"exp": 1697741135,
"aud": "238d4793-70de-4183-9707-48ed8ecd19d9",
"sub": "19016b73-3ffa-4b26-80d8-aa9287738677",
"name": "Dan Moore",
"roles": [
"RETRIEVE_JOKES", "RETRIEVE_ALL_JOKES"
]
}](https://image.slidesharecdn.com/protectingyourapis-231103024257-47bb9cb3/85/Protecting-Your-APIs-pdf-125-320.jpg)
![@mooreds
@mooreds
Validate the Expiration
{
"iss": "fusionauth.io",
"exp": 1697741135,
"aud": "238d4793-70de-4183-9707-48ed8ecd19d9",
"sub": "19016b73-3ffa-4b26-80d8-aa9287738677",
"name": "Dan Moore",
"roles": [
"RETRIEVE_JOKES", "RETRIEVE_ALL_JOKES"
]
}](https://image.slidesharecdn.com/protectingyourapis-231103024257-47bb9cb3/85/Protecting-Your-APIs-pdf-126-320.jpg)
![@mooreds
@mooreds
Validate the Audience
{
"iss": "fusionauth.io",
"exp": 1697741135,
"aud": "238d4793-70de-4183-9707-48ed8ecd19d9",
"sub": "19016b73-3ffa-4b26-80d8-aa9287738677",
"name": "Dan Moore",
"roles": [
"RETRIEVE_JOKES", "RETRIEVE_ALL_JOKES"
]
}](https://image.slidesharecdn.com/protectingyourapis-231103024257-47bb9cb3/85/Protecting-Your-APIs-pdf-127-320.jpg)
![@mooreds
@mooreds
Validate
{
"iss": "fusionauth.io",
"exp": 1697741135,
"aud": "238d4793-70de-4183-9707-48ed8ecd19d9",
"sub": "19016b73-3ffa-4b26-80d8-aa9287738677",
"name": "Dan Moore",
"roles": [
"RETRIEVE_JOKES", "RETRIEVE_ALL_JOKES"
]
}](https://image.slidesharecdn.com/protectingyourapis-231103024257-47bb9cb3/85/Protecting-Your-APIs-pdf-129-320.jpg)