BitTruster EaaS
•
0 likes•162 views
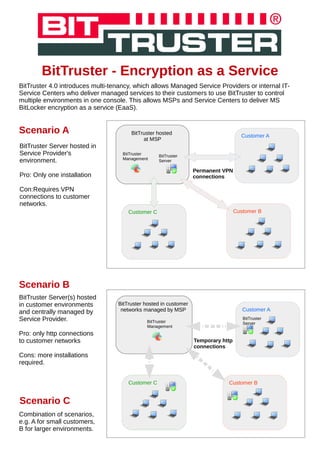
BitTruster 4.0 introduces multi-tenancy, which allows Managed Service Providers or internal IT-Service Centers who deliver managed services to their customers to use BitTruster to control multiple environments in one console. This allows MSPs and Service Centers to deliver MS BitLocker encryption as a service (EaaS).
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
More Related Content
Similar to BitTruster EaaS
Similar to BitTruster EaaS (20)
Building Powerful IoT Apps with AWS IoT and Websockets

Building Powerful IoT Apps with AWS IoT and Websockets
Connecting microcontrollers to the cloud using MQTT, BLE, and HTTP

Connecting microcontrollers to the cloud using MQTT, BLE, and HTTP
Cohesive Networks Support Docs: VNS3 Configuration for CenturyLink Cloud 

Cohesive Networks Support Docs: VNS3 Configuration for CenturyLink Cloud
Connectivity Options for VMware Cloud on AWS Software Defined Data Centers (S...

Connectivity Options for VMware Cloud on AWS Software Defined Data Centers (S...
How to Stream IoT MQTT Messages Into the Azure Event Hubs Service

How to Stream IoT MQTT Messages Into the Azure Event Hubs Service
Build your first blockchain application with Amazon Managed Blockchain - SVC2...

Build your first blockchain application with Amazon Managed Blockchain - SVC2...
Converging IPTV and OTT: Building an Enhanced Value Proposition for Consumers

Converging IPTV and OTT: Building an Enhanced Value Proposition for Consumers
Message queuing telemetry transport (mqtt) id and other type parameters

Message queuing telemetry transport (mqtt) id and other type parameters
VMware Certified Professional 5 - Data Center Virtualization Delta Exam

VMware Certified Professional 5 - Data Center Virtualization Delta Exam
(ARC205) Creating Your Virtual Data Center: VPC Fundamentals and Connectivity...

(ARC205) Creating Your Virtual Data Center: VPC Fundamentals and Connectivity...
Nagios Conference 2013 - Eric Loyd - Dynamic AWS Server Usage Using Nagios Core

Nagios Conference 2013 - Eric Loyd - Dynamic AWS Server Usage Using Nagios Core
GPSTEC322-GPS Creating Your Virtual Data Center VPC Fundamentals Connectivity...

GPSTEC322-GPS Creating Your Virtual Data Center VPC Fundamentals Connectivity...
Recently uploaded
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
BitTruster EaaS
- 1. BitTruster - Encryption as a Service BitTruster 4.0 introduces multi-tenancy, which allows Managed Service Providers or internal IT- Service Centers who deliver managed services to their customers to use BitTruster to control multiple environments in one console. This allows MSPs and Service Centers to deliver MS BitLocker encryption as a service (EaaS). Customer A BitTruster hosted at MSP Customer BCustomer C BitTruster Management BitTruster Server Permanent VPN connections Scenario A Customer A Customer BCustomer C BitTruster hosted in customer networks managed by MSP BitTruster Management BitTruster Server Temporary http connections Scenario B BitTruster Server(s) hosted in customer environments and centrally managed by Service Provider. Pro: only http connections to customer networks Cons: more installations required. Scenario C Combination of scenarios, e.g. A for small customers, B for larger environments. BitTruster Server hosted in Service Provider's environment. Pro: Only one installation Con:Requires VPN connections to customer networks.
