Cost of Poor Cybersecurity.pdf
•
0 likes•2 views
There are many variables at play when it comes to analyzing the cost of poor cybersecurity and breaches. Businesses need to stop production and other activities in order to address the event that occurs. This loss in revenue is one such cost of the breach. Another major source of costs associated with a breach involves analyzing your infected systems. Doing so helps you understand what became compromised in the first place. Many companies pay for credit monitoring services, among other cleanup costs, adding to the total. Patching the breached system is also quite costly. So, is purchasing the necessary security so that it does not happen again.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
Similar to Cost of Poor Cybersecurity.pdf
Similar to Cost of Poor Cybersecurity.pdf (20)
The cyber insurance market in china report by daxue consulting asian risks

The cyber insurance market in china report by daxue consulting asian risks
What Are Cyber Attacks All About? | Cyberroot Risk Advisory

What Are Cyber Attacks All About? | Cyberroot Risk Advisory
Nearly 80 billion dollars were spent in 2016 to fight cybercrime

Nearly 80 billion dollars were spent in 2016 to fight cybercrime
BIZGrowth Strategies - Cybersecurity Special Edition

BIZGrowth Strategies - Cybersecurity Special Edition
Pat Pather- Cyber Security Unchartered: Vigilance, Innovation and Adaptability

Pat Pather- Cyber Security Unchartered: Vigilance, Innovation and Adaptability
Ninth Annual Cost of Cybercrime Study in Financial Services – 2019 Report

Ninth Annual Cost of Cybercrime Study in Financial Services – 2019 Report
Cybersecurity - you are being targeted -Keyven Lewis, CMIT SOLUTIONS

Cybersecurity - you are being targeted -Keyven Lewis, CMIT SOLUTIONS
Accounting for Cyber Risks - How much does Cyber actually cost the Industry?

Accounting for Cyber Risks - How much does Cyber actually cost the Industry?
Cybersecurity Context in African Continent - Way Forward

Cybersecurity Context in African Continent - Way Forward
CII Whitepaper India Cyber Risk & Resilience Review 2018

CII Whitepaper India Cyber Risk & Resilience Review 2018
PandaLabs Reveals its Predictions for Cybersecurity Trends in 2018

PandaLabs Reveals its Predictions for Cybersecurity Trends in 2018
More from ButterflyMeltzer
More from ButterflyMeltzer (8)
10 HIPAA Compliance Best Practices for Dental Offices.pdf

10 HIPAA Compliance Best Practices for Dental Offices.pdf
Recently uploaded
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Recently uploaded (20)
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
Tata AIG General Insurance Company - Insurer Innovation Award 2024

Tata AIG General Insurance Company - Insurer Innovation Award 2024
Kalyanpur ) Call Girls in Lucknow Finest Escorts Service 🍸 8923113531 🎰 Avail...

Kalyanpur ) Call Girls in Lucknow Finest Escorts Service 🍸 8923113531 🎰 Avail...
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Cost of Poor Cybersecurity.pdf
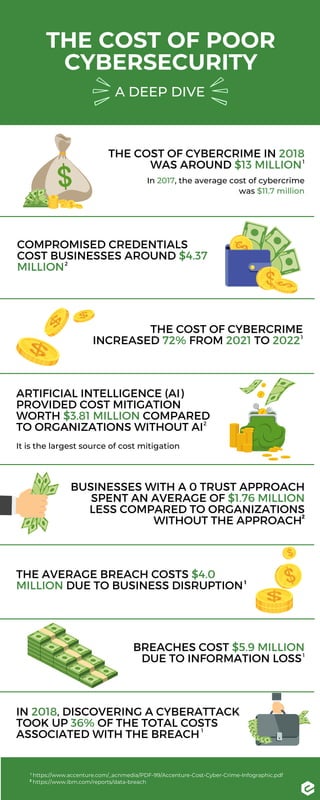
- 1. A DEEP DIVE THE COST OF POOR CYBERSECURITY THE AVERAGE BREACH COSTS $4.0 MILLION DUE TO BUSINESS DISRUPTION ARTIFICIAL INTELLIGENCE (AI) PROVIDED COST MITIGATION WORTH $3.81 MILLION COMPARED TO ORGANIZATIONS WITHOUT AI It is the largest source of cost mitigation THE COST OF CYBERCRIME INCREASED 72% FROM 2021 TO 2022 COMPROMISED CREDENTIALS COST BUSINESSES AROUND $4.37 MILLION THE COST OF CYBERCRIME IN 2018 WAS AROUND $13 MILLION In 2017, the average cost of cybercrime was $11.7 million BUSINESSES WITH A 0 TRUST APPROACH SPENT AN AVERAGE OF $1.76 MILLION LESS COMPARED TO ORGANIZATIONS WITHOUT THE APPROACH BREACHES COST $5.9 MILLION DUE TO INFORMATION LOSS IN 2018, DISCOVERING A CYBERATTACK TOOK UP 36% OF THE TOTAL COSTS ASSOCIATED WITH THE BREACH https://www.accenture.com/_acnmedia/PDF-99/Accenture-Cost-Cyber-Crime-Infographic.pdf https://www.ibm.com/reports/data-breach 1 1 1 1 1 1 2 2 2 2