Preaparation for new software application
•Download as DOCX, PDF•
0 likes•265 views
This is a documentation that is for users who are installing software to their a computer system. This is part of my IT coursework*
Report
Share
Report
Share
Recommended
#ATAGTR2021 Presentation : "Chaos engineering: Break it to make it" by Anupa...

#ATAGTR2021 Presentation : "Chaos engineering: Break it to make it" by Anupa...Agile Testing Alliance
Recommended
#ATAGTR2021 Presentation : "Chaos engineering: Break it to make it" by Anupa...

#ATAGTR2021 Presentation : "Chaos engineering: Break it to make it" by Anupa...Agile Testing Alliance
More Related Content
What's hot
What's hot (20)
The complete guide for negative testing | David Tzemach

The complete guide for negative testing | David Tzemach
All you need to know about regression testing | David Tzemach

All you need to know about regression testing | David Tzemach
Fundamentals of testing (what is testing necessary)

Fundamentals of testing (what is testing necessary)
Black Friday Is Approaching. Are You Prepared- Infographic

Black Friday Is Approaching. Are You Prepared- Infographic
fundamentals of testing (Fundamental of testing why)

fundamentals of testing (Fundamental of testing why)
Phased conversion method of implementing new Information Systems ( By Jackson...

Phased conversion method of implementing new Information Systems ( By Jackson...
Similar to Preaparation for new software application
Similar to Preaparation for new software application (20)
More from Ajay Jassi
More from Ajay Jassi (20)
Hardware Documentation and Benefits of Hardware Provider

Hardware Documentation and Benefits of Hardware Provider
IT job role description for Technical Support Engineer

IT job role description for Technical Support Engineer
Reasons why Hardware is Installed and Potential Problems and the Precautions

Reasons why Hardware is Installed and Potential Problems and the Precautions
Potential problems that occur during hardware installation

Potential problems that occur during hardware installation
Health and safety requirements for computer maintenance

Health and safety requirements for computer maintenance
Recently uploaded
Recently uploaded (20)
Elevate Developer Efficiency & build GenAI Application with Amazon Q

Elevate Developer Efficiency & build GenAI Application with Amazon Q
Design and Development of a Provenance Capture Platform for Data Science

Design and Development of a Provenance Capture Platform for Data Science
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...

TrustArc Webinar - Unified Trust Center for Privacy, Security, Compliance, an...
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
Finding Java's Hidden Performance Traps @ DevoxxUK 2024

Finding Java's Hidden Performance Traps @ DevoxxUK 2024
Navigating Identity and Access Management in the Modern Enterprise

Navigating Identity and Access Management in the Modern Enterprise
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
JavaScript Usage Statistics 2024 - The Ultimate Guide

JavaScript Usage Statistics 2024 - The Ultimate Guide
CNIC Information System with Pakdata Cf In Pakistan

CNIC Information System with Pakdata Cf In Pakistan
The Zero-ETL Approach: Enhancing Data Agility and Insight

The Zero-ETL Approach: Enhancing Data Agility and Insight
How to Check CNIC Information Online with Pakdata cf

How to Check CNIC Information Online with Pakdata cf
Preaparation for new software application
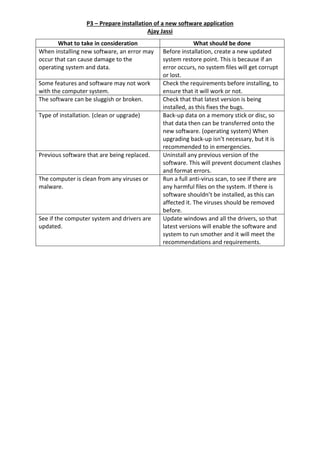
- 1. P3 – Prepare installation of a new software application Ajay Jassi What to take in consideration What should be done When installing new software, an error may occur that can cause damage to the operating system and data. Before installation, create a new updated system restore point. This is because if an error occurs, no system files will get corrupt or lost. Some features and software may not work with the computer system. Check the requirements before installing, to ensure that it will work or not. The software can be sluggish or broken. Check that that latest version is being installed, as this fixes the bugs. Type of installation. (clean or upgrade) Back-up data on a memory stick or disc, so that data then can be transferred onto the new software. (operating system) When upgrading back-up isn’t necessary, but it is recommended to in emergencies. Previous software that are being replaced. Uninstall any previous version of the software. This will prevent document clashes and format errors. The computer is clean from any viruses or malware. Run a full anti-virus scan, to see if there are any harmful files on the system. If there is software shouldn’t be installed, as this can affected it. The viruses should be removed before. See if the computer system and drivers are updated. Update windows and all the drivers, so that latest versions will enable the software and system to run smother and it will meet the recommendations and requirements.
