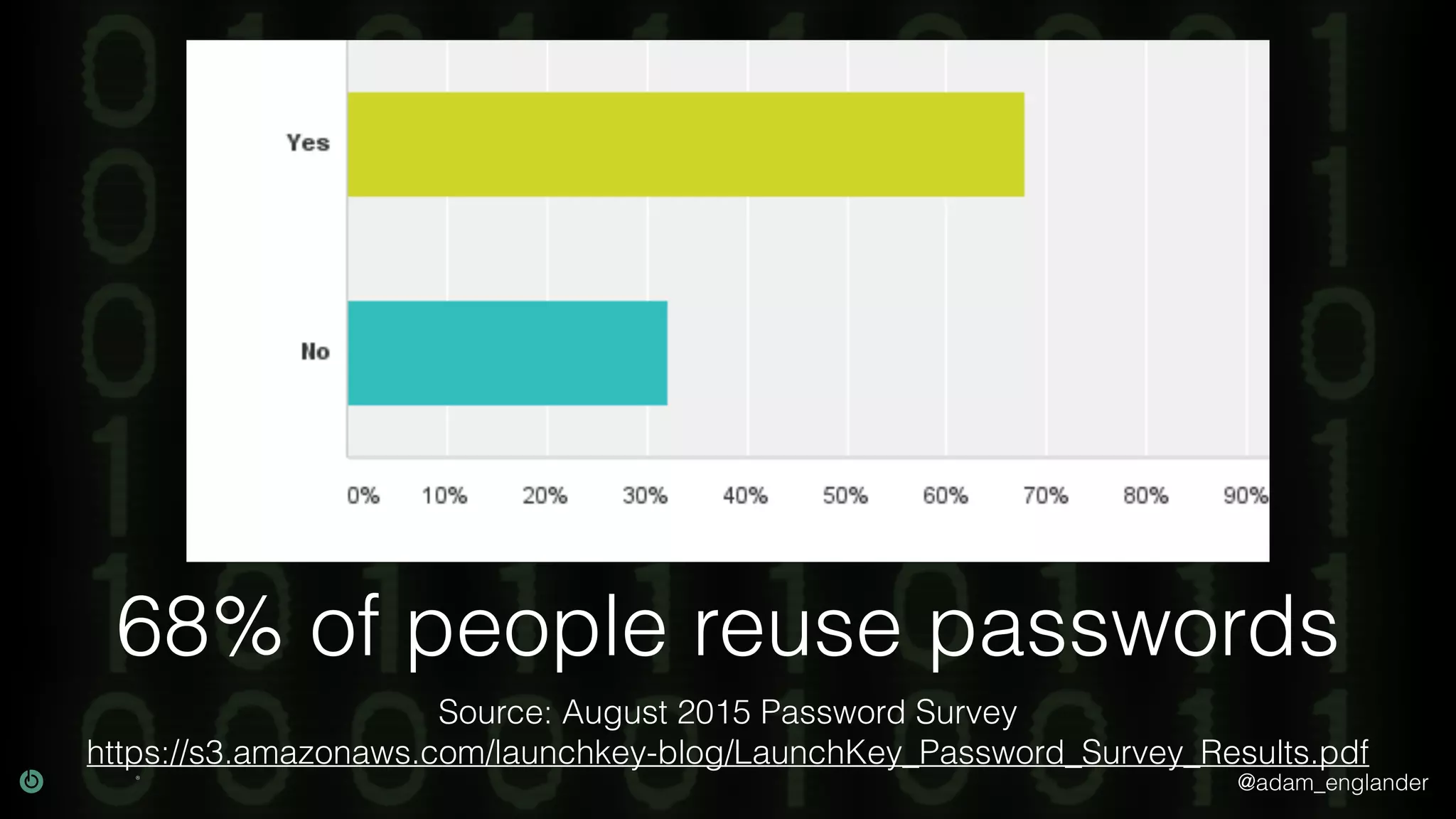
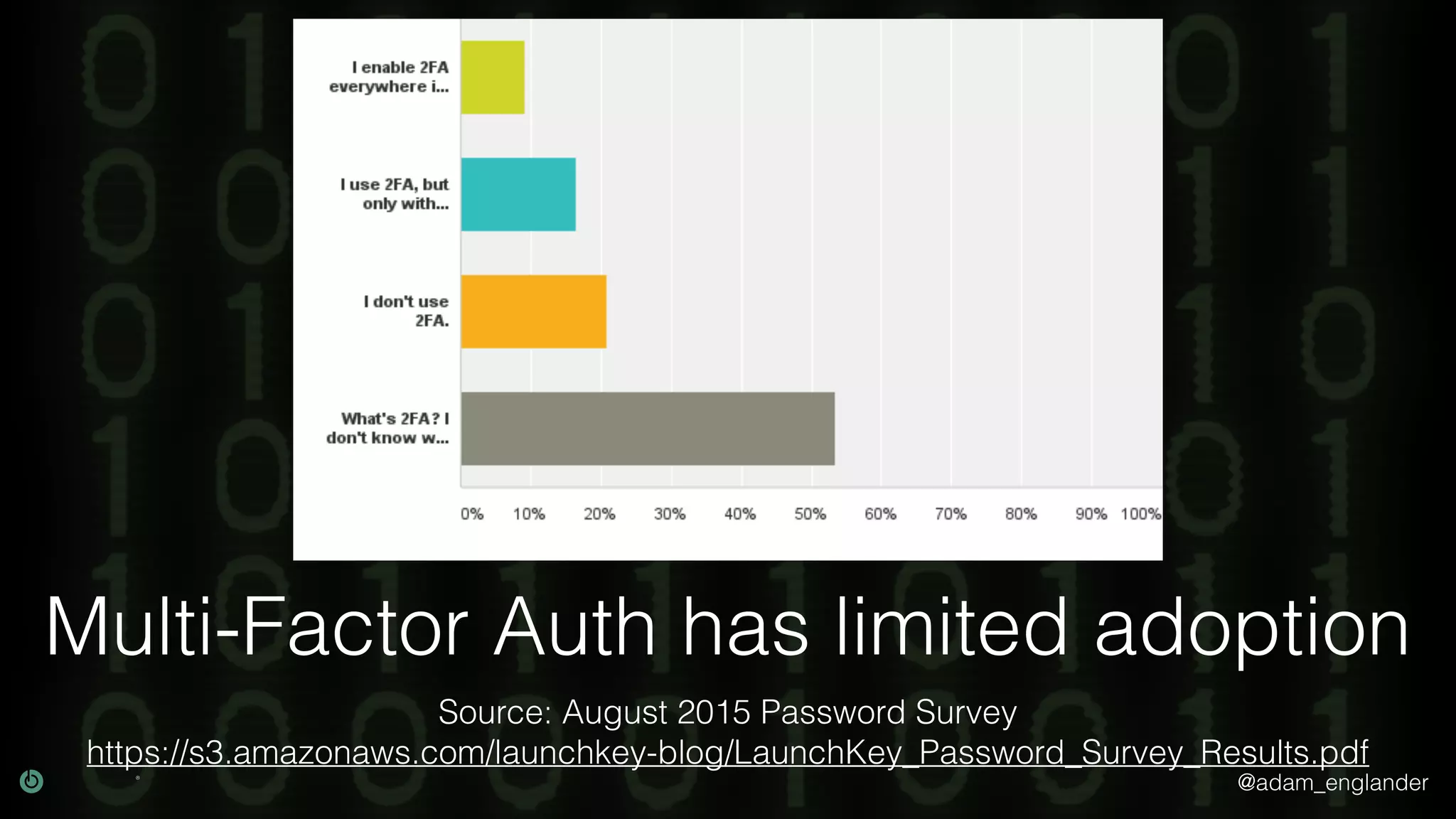
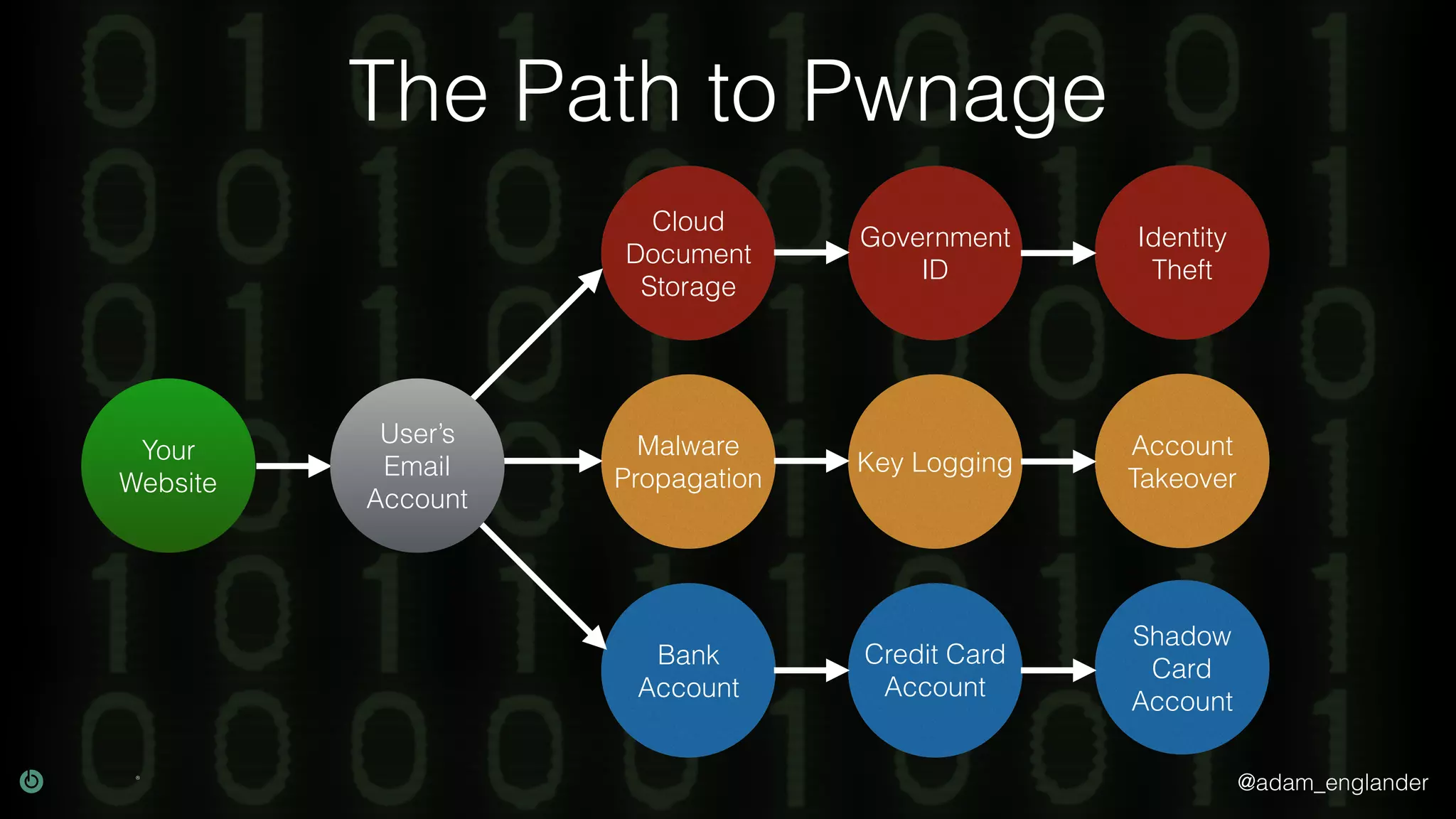
The document discusses cybersecurity threats, highlighting the prevalence of identity theft with 399,225 U.S. reports in 2017 and the challenges of password reuse and multi-factor authentication adoption. It cites sources such as consumer complaint reports and password surveys to emphasize the urgency of addressing these issues. Resources for improving security practices and understanding compliance are also mentioned.





















![@adam_englander
• Compliance: By Nick Young [CC BY-SA 3.0]
• Botnet: By Joey Devilla [CC BY-SA 4.0], via Wikimedia Commons
• The Red Pill or the Blue Pill: By Paul L Dineen [CC BY-SA 2.0]
• All other photos were public domain](https://image.slidesharecdn.com/zendcon2017-theredteamiscoming-171024180402/75/ZendCon-2017-The-Red-Team-is-Coming-29-2048.jpg)