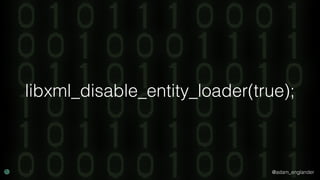
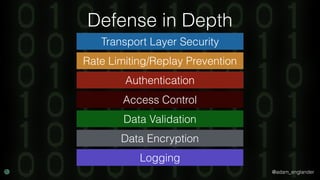
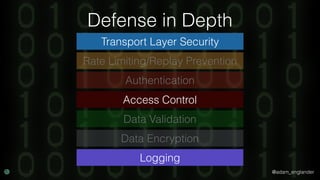
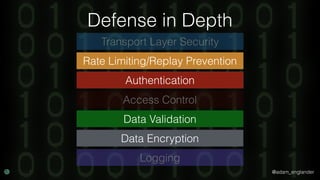
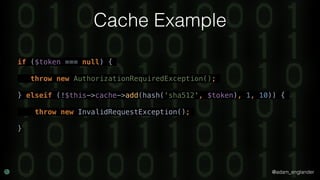
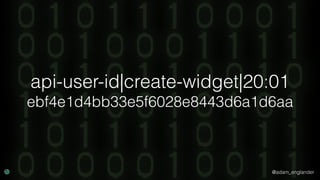
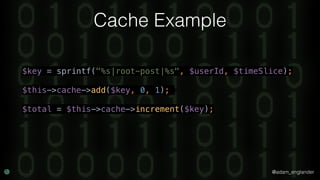
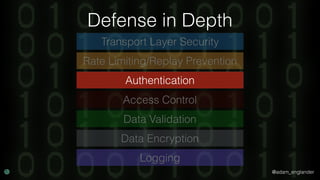
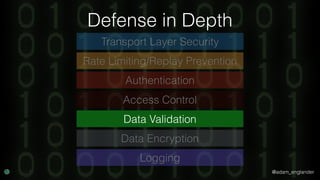
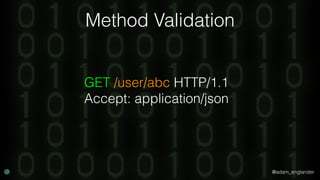
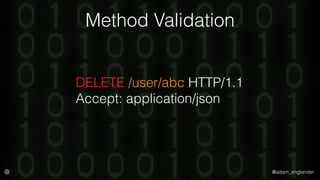
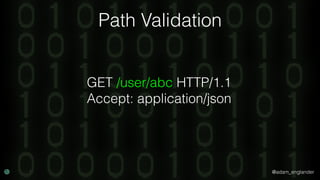
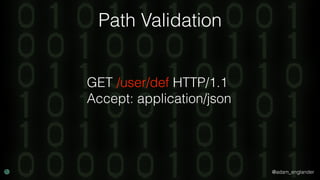
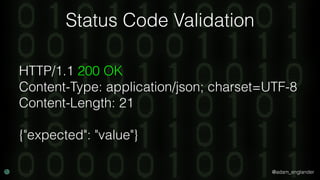
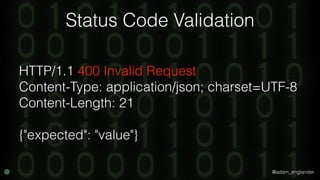
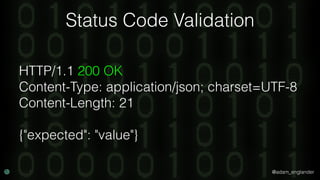
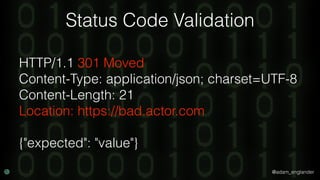
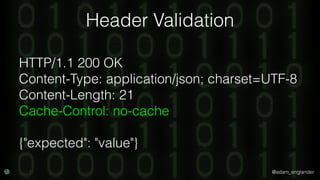
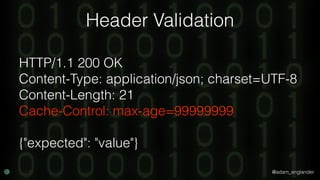
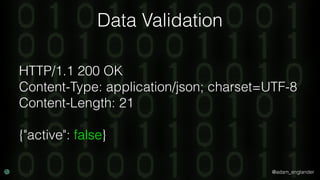
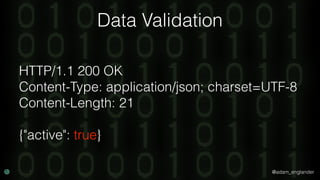
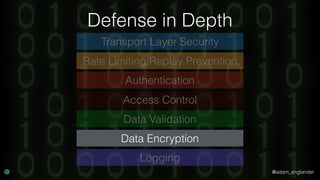
The document discusses practical API security and provides recommendations for securing APIs. It recommends implementing defense in depth with layers of security including transport layer security, rate limiting, authentication, data validation, encryption, logging, and access control. It then goes into more detail about how to implement specific security measures like replay prevention, rate limiting, authentication methods, message and response validation, encrypting data at rest and in transit, and logging recommendations.