INFOGRAPHIC▶ Spear Phishing Scammers Sharpen Their Attacks
•
2 likes•1,520 views
Attackers win your confidence with personalized, targeted emails.
Report
Share
Report
Share
Download to read offline
Recommended
Security Awareness Training: Are We Getting Any Better at Organizational and ...

Security Awareness Training: Are We Getting Any Better at Organizational and ...Enterprise Management Associates
More Related Content
What's hot
Security Awareness Training: Are We Getting Any Better at Organizational and ...

Security Awareness Training: Are We Getting Any Better at Organizational and ...Enterprise Management Associates
What's hot (20)
Five Reasons to Look Beyond Math-based Next-Gen Antivirus

Five Reasons to Look Beyond Math-based Next-Gen Antivirus
When thieves strike: Executive briefing on SWIFT attacks

When thieves strike: Executive briefing on SWIFT attacks
Four Network Security Challenges for the Cloud Generation

Four Network Security Challenges for the Cloud Generation
Security Awareness Training: Are We Getting Any Better at Organizational and ...

Security Awareness Training: Are We Getting Any Better at Organizational and ...
Similar to INFOGRAPHIC▶ Spear Phishing Scammers Sharpen Their Attacks
Similar to INFOGRAPHIC▶ Spear Phishing Scammers Sharpen Their Attacks (20)
Netwealth educational webinar: Peace of mind in a digital world

Netwealth educational webinar: Peace of mind in a digital world
How to assess your Cybersecurity Vulnerability_.pdf

How to assess your Cybersecurity Vulnerability_.pdf
How to assess your Cybersecurity Vulnerability_.pptx

How to assess your Cybersecurity Vulnerability_.pptx
[Infographic] Email: The First Security Gap Targeted by Attackers![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Infographic] Email: The First Security Gap Targeted by Attackers](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Infographic] Email: The First Security Gap Targeted by Attackers
Mark Villinski - Top 10 Tips for Educating Employees about Cybersecurity

Mark Villinski - Top 10 Tips for Educating Employees about Cybersecurity
How to Protect Your Business from Cyber Threats | The Entrepreneur Review

How to Protect Your Business from Cyber Threats | The Entrepreneur Review
The Small Business Cyber Security Best Practice Guide

The Small Business Cyber Security Best Practice Guide
Understanding the Risk & Challenges of Cyber Security

Understanding the Risk & Challenges of Cyber Security
5 Network Security Threats Facing Businesses Today

5 Network Security Threats Facing Businesses Today
Why Startups Need to Strengthen Application Security

Why Startups Need to Strengthen Application Security
5 Reasons Cyber Attackers Target Small and Medium Businesses 

5 Reasons Cyber Attackers Target Small and Medium Businesses
Managed Services: Turning Pandemic Into Profitable Protection

Managed Services: Turning Pandemic Into Profitable Protection
More from Symantec
More from Symantec (20)
Symantec Enterprise Security Products are now part of Broadcom

Symantec Enterprise Security Products are now part of Broadcom
Symantec Webinar | National Cyber Security Awareness Month: Fostering a Secur...

Symantec Webinar | National Cyber Security Awareness Month: Fostering a Secur...
Symantec Webinar | National Cyber Security Awareness Month: Protect IT

Symantec Webinar | National Cyber Security Awareness Month: Protect IT
Symantec Webinar | National Cyber Security Awareness Month: Secure IT

Symantec Webinar | National Cyber Security Awareness Month: Secure IT
Symantec Webinar | National Cyber Security Awareness Month - Own IT

Symantec Webinar | National Cyber Security Awareness Month - Own IT
Symantec Webinar: Preparing for the California Consumer Privacy Act (CCPA)

Symantec Webinar: Preparing for the California Consumer Privacy Act (CCPA)
Symantec Webinar | How to Detect Targeted Ransomware with MITRE ATT&CK

Symantec Webinar | How to Detect Targeted Ransomware with MITRE ATT&CK
Symantec Webinar | Security Analytics Breached! Next Generation Network Foren...

Symantec Webinar | Security Analytics Breached! Next Generation Network Foren...
Symantec Webinar | Implementing a Zero Trust Framework to Secure Modern Workf...

Symantec Webinar | Implementing a Zero Trust Framework to Secure Modern Workf...
Symantec Webinar | Tips for Successful CASB Projects

Symantec Webinar | Tips for Successful CASB Projects
Symantec Webinar: What Cyber Threats Are Lurking in Your Network?

Symantec Webinar: What Cyber Threats Are Lurking in Your Network?
Symantec Best Practices for Cloud Security: Insights from the Front Lines

Symantec Best Practices for Cloud Security: Insights from the Front Lines
Symantec - The Importance of Building Your Zero Trust Program on a Solid Plat...

Symantec - The Importance of Building Your Zero Trust Program on a Solid Plat...
Symantec Webinar | Redefining Endpoint Security- How to Better Secure the End...

Symantec Webinar | Redefining Endpoint Security- How to Better Secure the End...
Symantec Webinar Using Advanced Detection and MITRE ATT&CK to Cage Fancy Bear

Symantec Webinar Using Advanced Detection and MITRE ATT&CK to Cage Fancy Bear
Recently uploaded
Vip Call Girls Noida ➡️ Delhi ➡️ 9999965857 No Advance 24HRS Live

Vip Call Girls Noida ➡️ Delhi ➡️ 9999965857 No Advance 24HRS LiveCall Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...

Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...Call Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
Recently uploaded (20)
Optimizing AI for immediate response in Smart CCTV

Optimizing AI for immediate response in Smart CCTV
Short Story: Unveiling the Reasoning Abilities of Large Language Models by Ke...

Short Story: Unveiling the Reasoning Abilities of Large Language Models by Ke...
(Genuine) Escort Service Lucknow | Starting ₹,5K To @25k with A/C 🧑🏽❤️🧑🏻 89...

(Genuine) Escort Service Lucknow | Starting ₹,5K To @25k with A/C 🧑🏽❤️🧑🏻 89...
why an Opensea Clone Script might be your perfect match.pdf

why an Opensea Clone Script might be your perfect match.pdf
Right Money Management App For Your Financial Goals

Right Money Management App For Your Financial Goals
Learn the Fundamentals of XCUITest Framework_ A Beginner's Guide.pdf

Learn the Fundamentals of XCUITest Framework_ A Beginner's Guide.pdf
Diamond Application Development Crafting Solutions with Precision

Diamond Application Development Crafting Solutions with Precision
W01_panagenda_Navigating-the-Future-with-The-Hitchhikers-Guide-to-Notes-and-D...

W01_panagenda_Navigating-the-Future-with-The-Hitchhikers-Guide-to-Notes-and-D...
call girls in Vaishali (Ghaziabad) 🔝 >༒8448380779 🔝 genuine Escort Service 🔝✔️✔️

call girls in Vaishali (Ghaziabad) 🔝 >༒8448380779 🔝 genuine Escort Service 🔝✔️✔️
The Real-World Challenges of Medical Device Cybersecurity- Mitigating Vulnera...

The Real-World Challenges of Medical Device Cybersecurity- Mitigating Vulnera...
Vip Call Girls Noida ➡️ Delhi ➡️ 9999965857 No Advance 24HRS Live

Vip Call Girls Noida ➡️ Delhi ➡️ 9999965857 No Advance 24HRS Live
SyndBuddy AI 2k Review 2024: Revolutionizing Content Syndication with AI

SyndBuddy AI 2k Review 2024: Revolutionizing Content Syndication with AI
Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...

Call Girls In Mukherjee Nagar 📱 9999965857 🤩 Delhi 🫦 HOT AND SEXY VVIP 🍎 SE...
Unlocking the Future of AI Agents with Large Language Models

Unlocking the Future of AI Agents with Large Language Models
INFOGRAPHIC▶ Spear Phishing Scammers Sharpen Their Attacks
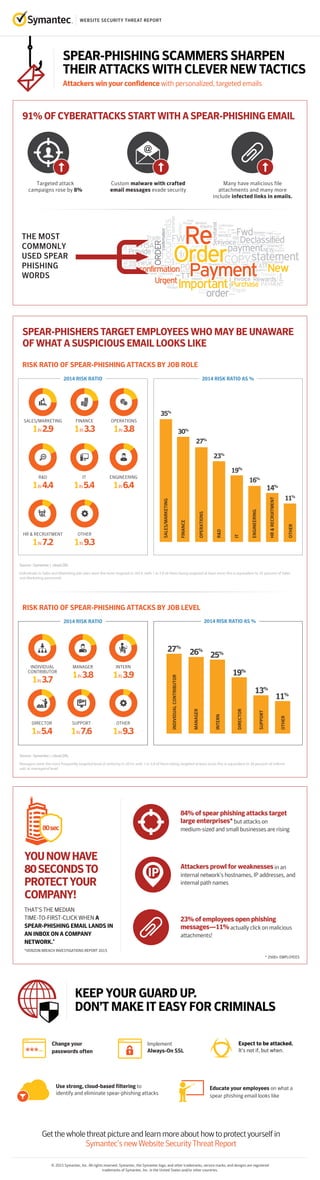
- 1. WEBSITE SECURITY THREAT REPORT © 2015 Symantec, Inc. All rights reserved. Symantec, the Symantec logo, and other trademarks, service marks, and designs are registered trademarks of Symantec, Inc. in the United States and/or other countries. SPEAR-PHISHING SCAMMERS SHARPEN THEIR ATTACKS WITH CLEVER NEW TACTICS Attackers win your confidence with personalized, targeted emails Getthewholethreatpictureandlearnmoreabouthowtoprotectyourselfin Symantec’snewWebsiteSecurityThreatReport Expect to be attacked. It’s not if, but when. Use strong, cloud-based filtering to identify and eliminate spear-phishing attacks 91% OF CYBERATTACKS START WITH A SPEAR-PHISHING EMAIL RISK RATIO OF SPEAR-PHISHING ATTACKS BY JOB ROLE SPEAR-PHISHERS TARGET EMPLOYEES WHO MAY BE UNAWARE OF WHAT A SUSPICIOUS EMAIL LOOKS LIKE THAT’S THE MEDIAN TIME-TO-FIRST-CLICK WHEN A SPEAR-PHISHING EMAIL LANDS IN AN INBOX ON A COMPANY NETWORK.* *VERIZON BREACH INVESTIGATIONS REPORT 2015 YOUNOWHAVE 80SECONDSTO PROTECTYOUR COMPANY! 27% 26% MANAGER 19% 13% 11% INDIVIDUALCONTRIBUTOR 25% INTERN DIRECTOR SUPPORT OTHER Attackers prowl for weaknessesin an internal network’s hostnames, IP addresses, and internal path names 80sec 84% of spear phishing attacks target large enterprises*but attacks on medium-sized and small businesses are rising THE MOST COMMONLY USED SPEAR PHISHING WORDS Targeted attack campaigns rose by 8% Custom malware with crafted email messages evade security Many have malicious file attachments and many more include infected links in emails. Source : Symantec | .cloud.SRL 35% 27% 30% 23% 19% 16% 14% 11% 1IN2.9 Individuals in Sales and Marketing job roles were the most targeted in 2014, with 1 in 2.9 of them being targeted at least once; this is equivalent to 35 percent of Sales and Marketing personnel. KEEP YOUR GUARD UP. DON’T MAKE IT EASY FOR CRIMINALS 23% of employees open phishing messages—11%actually click on malicious attachments! Implement Always-On SSL Educate your employees on what a spear phishing email looks like Change your passwords often SALES/MARKETING SALES/MARKETING 1IN3.8 OPERATIONS OPERATIONS FINANCE R&D IT ENGINEERING HR&RECRUITMENT OTHER 1IN3.3 FINANCE 1IN4.4 R&D 1IN5.4 IT 1IN7.2 HR & RECRUITMENT 1IN9.3 OTHER 1IN6.4 ENGINEERING 2014 RISK RATIO 2014 RISK RATIO AS % RISK RATIO OF SPEAR-PHISHING ATTACKS BY JOB LEVEL Source : Symantec | .cloud.SRL Managers were the most frequently targeted level of seniority in 2014, with 1 in 3.8 of them being targeted at least once; this is equivalent to 26 percent of individ- uals at managerial level. 1IN3.7 INDIVIDUAL CONTRIBUTOR 1IN3.9 INTERN 2014 RISK RATIO 2014 RISK RATIO AS % 1IN5.4 DIRECTOR 1IN7.6 SUPPORT 1IN9.3 OTHER * 2500+ EMPLOYEES 1IN3.8 MANAGER
