The Small Business Cyber Security Best Practice Guide
•
2 likes•512 views
Cyber security is a big problem for small business. Small business is the target of 43% of all cybercrimes. • 60% of small businesses who experience a significant cyber breach go out of business within the following 6 months. • 22% of small businesses that were breached by the 2017 Ransomware attacks were so affected they could not continue operating. • 33% of businesses with fewer than 100 employees don’t take proactive measures against cyber security breaches. • 87% of small businesses believe their business is safe from cyberattacks because they use antivirus software alone. • Cybercrime costs the Australian economy more than $1bn annually.
Report
Share
Report
Share
Download to read offline
Recommended
Cylance Ransomware - Remediation & Prevention Consulting Data-sheet: Current Ransomware Threat Environment
Today’s ransomware campaigns are very different from what we have seen in the past. On the one hand, ransomware can be easily obtained and used successfully by criminals that have little to no hacking skills, often referred to as Ransomware as a Service (RaaS). On the other hand, we are seeing ransomware being used for much more than just ransoms. In some cases, we have seen it used as a diversion; first harvesting credentials for later use, and then encrypting the drive to keep IT staff occupied while the attacker covers their tracks and accomplishes even more nefarious objectives. And more recently, we are seeing highly opportunistic campaigns that encrypt entire networks in an organization and delete host backups prior to encryption, leaving the entire organization held hostage and unable to operate.
Cylance® offers two complementary service offerings to help organizations address this evolving threat.
Cylance’s Proactive Prevention and Readiness services cater specifically to the ransomware epidemic by:
• Leveragingthepowerofmachinelearningandartificialintelligencetoallowpredictive,autonomous,pre-executionprevention • Providing world-renowned, highly sought after, knowledgeable consultants with the expertise to facilitate remediation of a
ransomware attack
• Imparting wisdom BEFORE the attack occurs to ensure the best preparation, preventative technologies, and workflows are
in placeCylance Ransomware-Remediation & Prevention Consulting Data-sheet

Cylance Ransomware-Remediation & Prevention Consulting Data-sheetInnovation Network Technologies: InNet
Recommended
Cylance Ransomware - Remediation & Prevention Consulting Data-sheet: Current Ransomware Threat Environment
Today’s ransomware campaigns are very different from what we have seen in the past. On the one hand, ransomware can be easily obtained and used successfully by criminals that have little to no hacking skills, often referred to as Ransomware as a Service (RaaS). On the other hand, we are seeing ransomware being used for much more than just ransoms. In some cases, we have seen it used as a diversion; first harvesting credentials for later use, and then encrypting the drive to keep IT staff occupied while the attacker covers their tracks and accomplishes even more nefarious objectives. And more recently, we are seeing highly opportunistic campaigns that encrypt entire networks in an organization and delete host backups prior to encryption, leaving the entire organization held hostage and unable to operate.
Cylance® offers two complementary service offerings to help organizations address this evolving threat.
Cylance’s Proactive Prevention and Readiness services cater specifically to the ransomware epidemic by:
• Leveragingthepowerofmachinelearningandartificialintelligencetoallowpredictive,autonomous,pre-executionprevention • Providing world-renowned, highly sought after, knowledgeable consultants with the expertise to facilitate remediation of a
ransomware attack
• Imparting wisdom BEFORE the attack occurs to ensure the best preparation, preventative technologies, and workflows are
in placeCylance Ransomware-Remediation & Prevention Consulting Data-sheet

Cylance Ransomware-Remediation & Prevention Consulting Data-sheetInnovation Network Technologies: InNet
More Related Content
What's hot
What's hot (20)
Cybersecurity: Cyber Risk Management for Banks & Financial Institutions

Cybersecurity: Cyber Risk Management for Banks & Financial Institutions
Proven cybersecurity tips to protect your business

Proven cybersecurity tips to protect your business
Proatively Engaged: Questions Executives Should Ask Their Security Teams

Proatively Engaged: Questions Executives Should Ask Their Security Teams
Lifecycle: Responding to a Ransomware Attack - A Professional Breach Guide's ...

Lifecycle: Responding to a Ransomware Attack - A Professional Breach Guide's ...
FireEye Cyber Defense Summit 2016 Now What - Before & After The Breach

FireEye Cyber Defense Summit 2016 Now What - Before & After The Breach
Information security awareness (sept 2012) bis handout

Information security awareness (sept 2012) bis handout
Similar to The Small Business Cyber Security Best Practice Guide
Small businesses are just as vulnerable to cyber security attacks as huge corporations. Every small business, irrespective of sector, must be aware of the risks posed by cybersecurity attacks.Small businesses often have less stringent technological defenses, less awareness of threats and less time and resource to put into cyber security ServicesCyber Security Threats For Small Business- Detox Technologies.pdf

Cyber Security Threats For Small Business- Detox Technologies.pdfCyber security professional services- Detox techno
Similar to The Small Business Cyber Security Best Practice Guide (20)
Netwealth educational webinar: Peace of mind in a digital world

Netwealth educational webinar: Peace of mind in a digital world
For Public_ Cybersecurity_ Frameworks, Fundamentals, and Foundations 2023.pdf

For Public_ Cybersecurity_ Frameworks, Fundamentals, and Foundations 2023.pdf
The Ultimate Guide to Protecting Your Business from Cyber Attacks by Greg Pie...

The Ultimate Guide to Protecting Your Business from Cyber Attacks by Greg Pie...
Cyber Risks & Liabilities - Cyber Security for Small Businesses

Cyber Risks & Liabilities - Cyber Security for Small Businesses
The Top Cybersecurity Threats Frightening Small Businesses Today

The Top Cybersecurity Threats Frightening Small Businesses Today
Cyber Security Threats For Small Business- Detox Technologies.pdf

Cyber Security Threats For Small Business- Detox Technologies.pdf
More from Inspiring Women
More from Inspiring Women (20)
The Marketing Touchpoints of one business during one year.

The Marketing Touchpoints of one business during one year.
Seniors Program Warringah Council 2014 - 15 March - 16 April

Seniors Program Warringah Council 2014 - 15 March - 16 April
Journey speech for Inspiring Women & Warringah Council: International Womens ...

Journey speech for Inspiring Women & Warringah Council: International Womens ...
International Women's Day - Women and Change by Professor Marian Baird

International Women's Day - Women and Change by Professor Marian Baird
Australian Local Government Womens Association Dec13/Jan14 Newsletter

Australian Local Government Womens Association Dec13/Jan14 Newsletter
Local business forum - Doing Business with Council

Local business forum - Doing Business with Council
Couse & Community Centre Activities for Warringah Centres in 2013

Couse & Community Centre Activities for Warringah Centres in 2013
Accumulating poverty? Women’s experiences of inequality over the lifecycle

Accumulating poverty? Women’s experiences of inequality over the lifecycle
Fair tradingnswexcellentreferencemarch2012running a_business

Fair tradingnswexcellentreferencemarch2012running a_business
Recently uploaded
Recently uploaded (20)
Tirupati Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service

Tirupati Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service
call Now 9811711561 Cash Payment乂 Call Girls in Dwarka

call Now 9811711561 Cash Payment乂 Call Girls in Dwarka
Connaught Place, Delhi Call girls :8448380779 Model Escorts | 100% verified

Connaught Place, Delhi Call girls :8448380779 Model Escorts | 100% verified
Sector 18, Noida Call girls :8448380779 Model Escorts | 100% verified

Sector 18, Noida Call girls :8448380779 Model Escorts | 100% verified
Shareholders Agreement Template for Compulsorily Convertible Debt Funding- St...

Shareholders Agreement Template for Compulsorily Convertible Debt Funding- St...
Enabling Business Users to Interpret Data Through Self-Service Analytics (2).pdf

Enabling Business Users to Interpret Data Through Self-Service Analytics (2).pdf
Hyderabad Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service

Hyderabad Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service
Dehradun Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service

Dehradun Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service
JAIPUR CALL GIRLS SERVICE REAL HOT SEXY 👯 CALL GIRLS IN JAIPUR BOOK YOUR DREA...

JAIPUR CALL GIRLS SERVICE REAL HOT SEXY 👯 CALL GIRLS IN JAIPUR BOOK YOUR DREA...
How Multicultural Toys Helps in Child Development.pptx

How Multicultural Toys Helps in Child Development.pptx
Bangalore Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service

Bangalore Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service
+971565801893>>Safe and original mtp kit for sale in Dubai>>+971565801893

+971565801893>>Safe and original mtp kit for sale in Dubai>>+971565801893
Sangareddy Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service

Sangareddy Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service
Jual Obat Aborsi Bojonegoro ( Asli No.1 ) 085657271886 Obat Penggugur Kandung...

Jual Obat Aborsi Bojonegoro ( Asli No.1 ) 085657271886 Obat Penggugur Kandung...
Karol Bagh, Delhi Call girls :8448380779 Model Escorts | 100% verified

Karol Bagh, Delhi Call girls :8448380779 Model Escorts | 100% verified
Lucknow Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service

Lucknow Call Girls Service ☎ ️82500–77686 ☎️ Enjoy 24/7 Escort Service
Sohna Call Girls Service ☎ ️93326-06886 ❤️🔥 Enjoy 24/7 Escort Service

Sohna Call Girls Service ☎ ️93326-06886 ❤️🔥 Enjoy 24/7 Escort Service
The Small Business Cyber Security Best Practice Guide
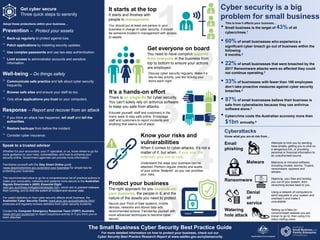
- 1. 5 4 3 2 1 It starts at the top It starts and finishes with people in management. Get everyone on board You need to have complicit support from everyone in the business from top to bottom to ensure your actions are employed. It’s a hands-on effort There is no single-fix for cyber security. You can’t solely rely on antivirus software to keep you safe from attacks. Know your risks and vulnerabilities When it comes to cyber-attacks, it’s not a matter of if, but when. If you use the internet, you are at risk. Protect your business The right approach for you depends on your business, the people in it, and the nature of the assets you need to protect. For more detailed information on how to protect your business, check out our Cyber Security Best Practice Research Report at www.asbfeo.gov.au/cybersecurity The Small Business Cyber Security Best Practice Guide Cyber security is a big problem for small business Cyberattacks • Small business is the target of 43% of all cybercrimes.1 • 60% of small businesses who experience a significant cyber breach go out of business within the following 6 months.2 • 22% of small businesses that were breached by the 2017 Ransomware attacks were so affected they could not continue operating.3 • 33% of businesses with fewer than 100 employees don’t take proactive measures against cyber security breaches.4 • 87% of small businesses believe their business is safe from cyberattacks because they use antivirus software alone.5 • Cybercrime costs the Australian economy more than $1bn annually.6 Malware Ransomware Denial of service Email phishing Attempts to trick you by sending hoax emails, getting you to click on a dangerous link, or providing personal or financial information to an unauthorised source. Malicious or intrusive software, including viruses, worms, Trojans, ransomware, spyware and adware. Hijacking your files and locking you out of your system, then ransoming access back to you. Using a network of computers to send requests to your system and overload it and make it unavailable. This is how it affects your business… Know what you are at risk from… Watering hole attack Setting up a fake (or compromised) website you are known to go to, then using it to infect visiting users. Get cyber secure Three quick steps to serenity Adopt these protections within your business… Whether it’s your accountant, your IT specialist, or us, know where to go for more guidance on your risks, vulnerabilities, and how to enhance your security online. Government agencies can provide more information: Familiarise yourself with the Stay Smart Online guide (www.staysmartonline.gov.au/protect-your-business) for simple tips for protecting your business. The recommended place to go for a comprehensive list of practical actions to make your computers, networks and systems more secure is the Australian Signals Directorate’s (ASD) Essential Eight (asd.gov.au/infosec/mitigationstrategies.htm), which aim to prevent malware from running, and to limit the extent of incident and recover data. For useful statistics on how cyber security affects small business, the Australian Cyber Security Centre (www.acsc.gov.au/publications.html) produces and regularly reviews statistics from cyber security incidents. Contact the Computer Emergency Response Team (CERT) Australia (www.cert.gov.au/advice) to report suspicious activity or if you think you’ve been attacked. Speak to a trusted advisor Prevention – Protect your assets • Back-up regularly to protect against loss. • Patch applications by installing security updates. • Use complex passwords and use two-step authentication. • Limit access to administrator accounts and sensitive information. Well-being – Do things safely • Communicate safe practice and talk about cyber security frequently. • Browse safe sites and ensure your staff do too. • Only allow applications you trust on your computers. Response – Report and recover from an attack • If you think an attack has happened, tell staff and tell the authorities. • Restore backups from before the incident. • Consider cyber insurance. You should put at least one person in your business in charge of cyber security. It should be someone trusted in management with access to assets. Discuss cyber security regularly. Make it a day-to-day priority, just like locking your doors each night. Educate yourself, staff and customers in the many ways to stay safe online. Encourage staff and customers to report incidents and anything that seems out of place. Understand the ways your business can be attacked. Perform regular checks and audits of your online ‘footprint’, so you can prioritise your risks. Secure your Point of Sale systems, mobile devices, networks and stored data with recommended actions. Familiarise yourself with more advanced techniques to become cyber secure.
- 2. References 1 smallbiztrends.com/2016/04/cyber-attacks-target-small-business.html 2 Testimony of Dr. Jane LeClair, Chief Operating Officer, National Cybersecurity Institute at Excelsior College, before the U.S. House of Representatives Committee on Small Business (Apr. 22, 2015), available at docs.house.gov/meetings/SM/SM00/20150422/103276/HHRG-114-SM00-20150422-SD003-U4.pdf. 3 go.malwarebytes.com/rs/805-USG- 300/images/Second%20Annual%20State%20of%20Ransomware%20Report%20-%20Australia.pdf 4 www.telstraglobal.com/images/assets/insights/resources/Telstra_Cyber_Security_Report_ 2017_-_Whitepaper.pdf https://www.myob.com/au/about/news/2017/cloud-security-the-silver-lining-for-smes 5 www.myob.com/au/about/news/2017/cloud-security-the-silver-lining-for-smes 6 acumeninsurance.com.au/2017/03/14/cybercrime-costs-the-australian-economy-over-4-5-billion-annually-and-is- now-in-the-top-5-risks-faced-by-businesses/ The Small Business Cyber Security Best Practice Guide Canberra Level 2 15 Moore Street Canberra ACT GPO Box 1791 Canberra City ACT 2601 T 1300 650 460 E info@asbfeo.gov.au Twitter : @ASBFEO Facebook: @ASBFEO LinkedIn: Australian Small Business and Family Enterprise Ombudsman YouTube : Australian Small Business and Family Enterprise Ombudsman Copyright notice http://creativecommons.org/licenses/by/3.0/au/ With the exception of coats of arms, logos, emblems, images, other third-party material or devices protected by a trademark, this content is licensed under the Creative Commons Australia Attribution 3.0 Licence. We request attribution as © Commonwealth of Australia (Australian Small Business and Family Enterprise Ombudsman) 2017 and 2018. All other rights are reserved. Some graphics in this document were used under a Creative Commons license from the Noun Project (http://thenounproject.com) Australian Small Business and Family Enterprise Ombudsman has undertaken reasonable enquiries to identify material owned by third parties and secure permission for its reproduction. Permission may need to be obtained from third parties to re-use their material. Written enquiries may be sent to: Manager Communications and Marketing Australian Small Business and Family Enterprise Ombudsman 02 6263 1500 media@asbfeo.gov.au
