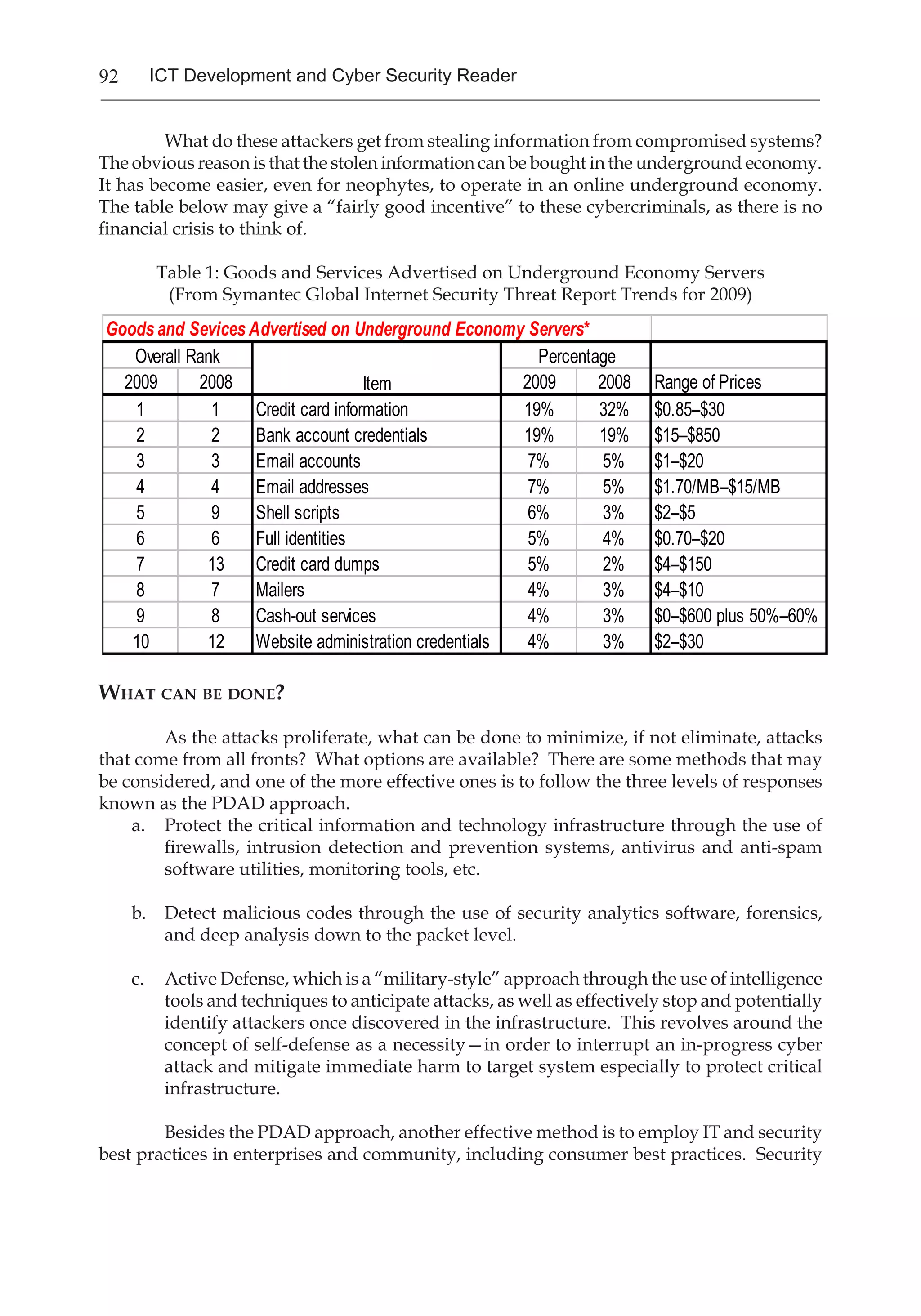
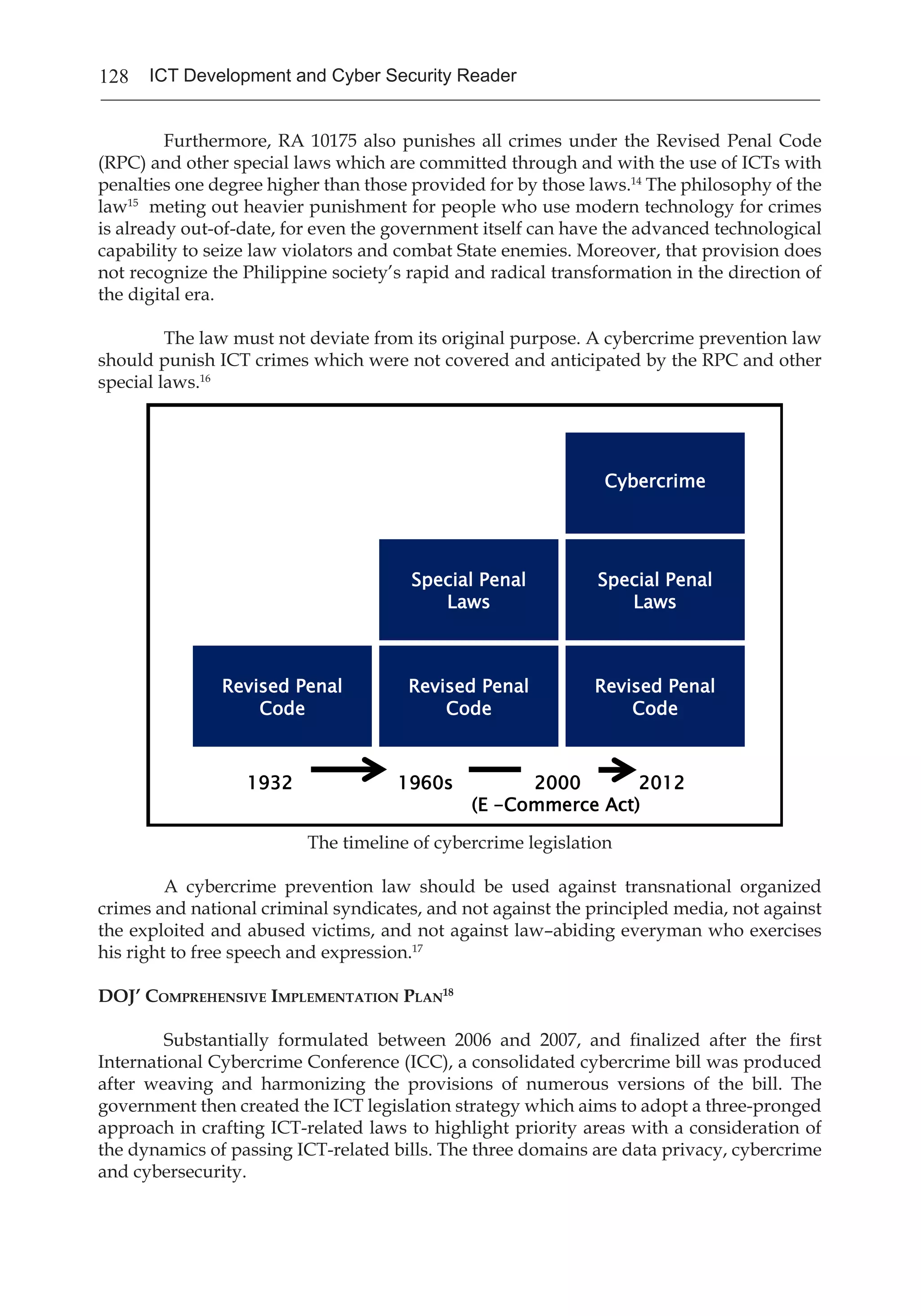
The document discusses the rapid growth of cyber threats as technology and internet usage has advanced. It notes that while the internet has provided many opportunities, it has also enabled criminal activities like hacking, identity theft, and network attacks. The keynote address argues that as both individuals and organizations increasingly rely on digital systems, enhancing cyber security is a shared responsibility to protect people from these growing cyber threats.











































































![77ICT Development and Cyber Security Reader
Philippine Cyber Security: General Situation
Angel S. Averia, Jr.
The paper is a post-write up of the presentation with the same title delivered at the seminar, “Towards
ICTD and Cyber Security Enhancement”, held at the National Defense College of the Philippines
on June 6-8 and 11, 2012.
_______________________________________________________________________________
What is Cyber Space?
B
efore we begin to gain an understanding and appreciation of the Philippine Cyber
Security Situation, let us first try to gain an understanding cyber space. There is an
abundance of literature that chronicles the development of the Internet that evolved
into a platform host of what we know today as cyber space. In the earlier days of the
Internet, the interconnectivity of independent networks allowed for the basic exchange
and sharing of data/information between and among select groups of individuals. The
development of packet switching, IP addressing, and domain name systems, among others,
provided the building blocks of the Internet.
Advancesinthedevelopmentofapplicationslikebrowsers,web-basedapplications,
and search engines provided efficiencies in information sharing and independent search
for information, ushering the transformation of the Internet into cyber space. As electronic
mail evolved in the Internet platform, groups or online communities started to develop
and, with the development of enabling applications, transformed and expanded into
what we now know as social networks. In the meantime, in parallel developments, online
market places also started to evolve, triggering commercial and trading activities.
Cyber space has not been fully defined, but it exists. As a virtual domain, cyber
space consists of physical, logical, and social components. [See: TRADOC Pamphlet 525-
7-8, U.S. Army, Cyberspace Operations Concept Capability Plan 2016-2028 at www.fas.
org/irp/doddir/army/pam525-7-8.pdf ]
The cyberspace components are:
1. Physical
a. Geographic Locations – locations in the physical world where computers,
electronic devices, networks, wired and wireless telecommunications facilities
and infrastructure, people, communities, and organizations may be found.
b. Networks – the interconnected information system networks and devices and
telecommunications infrastructure that make up the internet and allows easy
connectivity
2. Logical
a. IP Address – the logical address of devices connected to the internet, such devices
are used to access cyberspace](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-77-2048.jpg)


![80 ICT Development and Cyber Security Reader
• Department of Health
• Department of Social Welfare and Development
• Bases Conversion and Development Authority
• Philippine Nuclear Research Institute
• Department of Trade and Industry
• Department of Interior and Local Government
• Philippine Information Agency
• Philippine Army, 4th Infantry Division in Mindanao
• Housing and Land Use Regulatory Board
• Office of the Ombudsman
• www.e.com.ph
• mandaluyong.gov.ph
• www.undp.org.ph
• www.bayan.ph/petition
• www.epa.org.ph
• www.philproperties.ph
• www.insurance.gov.ph
• www.popcom.gov.ph
• http://webgis.dost.gov.ph/mindanao
The Culprits
The perpetrators identified themselves as:
• PrivateX
• Philker
• iSKORPiTX - a Turkey based group of hackers
• China Hacktivist
• BatangMahiligMagbatibot
• Black AtTacKer
• MISTA Haxor
• Clienc0de bgh7 m3rcil3sS
• Freeman
• KuTaHYaLıBeLa
• team crimes linux -
• 1923Turk Grup
• Ha[c]kingFor[c]es
• Mr-CaCaRoTe
• Saudi Arabia Hackers
• Ma3sTr0-Dz
Phishing
Phishing, a type of social engineering attack, is designed to lure netizens to
provide personal information. Phishers (as perpetrators of phishing attacks are referred
to) masquerade themselves by mimicking bank websites and requests random targets
to update their account information. Three local universal/commercial banks were
mimicked by phishers in 2011. Cost of damage is unreported as banks sought to protect
their identities and reputation.](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-80-2048.jpg)












![94 ICT Development and Cyber Security Reader
Cyberwar and Rules of Engagement
Drexx D. Laggui CISA, CISSP
____________________________________________________________________________________________________________________________________
Definitions
C
YBERWAR is generally defined as a hostile, state-sponsored operation to conduct
sabotage, espionage, or subversion through information systems, the Internet,
or other telecommunications media referred to as cyberspace. Another widely
accepted definition of "cyberwar" is the use of the Internet and related technological means
by one state against political, economic, technological and information sovereignty and
independence of any other state[1].
The employment of the word "war" is derived from a description of a conflict
between state or non-state peoples, declared or undeclared actions, and highly-organized,
politically controlled wars as well as culturally evolved, ritualistic wars and guerilla
uprisings, that appear to have no centrally controlling body and may perhaps be described
as emerging spontaneously[2].
Further, when considered from a strategic point of view, war in this context is an
actual, intentional and widespread conflict between political communities [3], with the less
violent design[4] of:
- crippling economies,
- manipulating political views,
- undermining the authority of a state,
- disturbing a state's relationship among its allies,
- reducing a state's military efficiency if not their effectiveness in physical
combat domains,
- equalizing the fighting capacity of richer nations to that of third-world nations,
and
- denying access to a nation's critical infrastructure so they can be coerced to
obey a dictated action.
Long-term threats
The conduct of cyberwar is an attractive option to a state because it is a relatively
cheap activity with remarkable benefits, vis-à-vis very low short-term risks on the lives
of its attacking combatants. However, the "use of force" in cyberspace can have violent or
crippling effects in the physical world of the state's targets.
As an identifiable long-term threat against Philippine national security, it is
often misunderstood and thus not managed correctly, simply because cyber warriors are
typically anonymous, that the individual users of ICT (information and communications
technology) assets believe they are very familiar with technology, and ICT administrators
can control cyber attacks in an ad hoc manner. The human mind reacts slowly to long-term](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-94-2048.jpg)
![95ICT Development and Cyber Security Reader
risks, thus comes the unfortunate realization that many elderly statesmen view cyberwar
as merely an abstract restricted to the imagination of science fiction writers.
The paradigm behind cyberwar is not a concept born out of a vacuum. Recent
developments reported on international news media brings to light the beginning, but
dramatically improving capabilities of state-actors. Famous examples include:
- 2003 to 2006: Titan Rain was the designation given by the US government to a
series of coordinated attacks on American computer systems by China [5].
- 2007: a three-week wave of massive cyber-attacks came upon Estonia by
Russia, the first known incidence of such an assault on a state, caused alarm
across the Western alliance, with NATO urgently examining the offensive and
its implications [6].
- 2008: Weeks before bombs started falling, attacks against Georgia’s Internet
infrastructure were conducted by Russians. The cyberwar had the effect
of silencing the Georgian media and isolating the country from the global
community. Furthermore, the Georgian population experienced a significant
informational and psychological defeat, as they were unable to communicate
what was happening to the outside world [7].
- 2009:GhostNetisthenamegivenbytheInformationWarfareMonitortoalarge-
scale espionage operation by China. High-value targets included ministries
of foreign affairs of Iran, Bangladesh, Latvia, Indonesia, Philippines, Brunei,
Barbados and Bhutan; embassies of India, South Korea, Indonesia, Romania,
Cyprus, Malta, Thailand, Taiwan, Portugal, Germany and Pakistan; the
ASEAN (Association of Southeast Asian Nations) Secretariat, SAARC (South
Asian Association for Regional Cooperation), and the Asian Development
Bank; news organizations; and an unclassified computer located at NATO
headquarters [8].
- 2010: Stuxnet is a highly sophisticated computer worm that sabotaged the
uranium enrichment equipment of the Natanz nuclear facility in Iran, by
Israel and USA [9]. This operation was deemed as a cheaper alternative than
sending attack aircraft to bomb the nuclear facility.
- 2011 and 2012: Duqu was found on 2011 [10], and Flame on 2012 [11]. Both
worms are related to Stuxnet.
- 2011: the Syrian Electronic Army used DDoS attacks, phishing scams, and
other tricks to fight opposition activists where they're strongest, which is
online[12]. Syrian President Bashar al-Assad's forces are currently in a state of
civil war, and determined to defeat the protest movement that toppled fellow
dictators in Egypt, Libya, and Tunisia.
- 2012: Here at home, a barrage of website vandalisms and e-mail intrusion
attempts were experienced and are co-related to the diplomatic tensions
between the Philippines and China arising from territorial disputes in the West
Philippine Sea. The events are tracked and reported by local news media[13].](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-95-2048.jpg)
![96 ICT Development and Cyber Security Reader
Known State Actors
Several nations have declared their respective government policies and military
strategies on cyberwar. Basically, these nations have come up with their cyberwar
doctrines and their rules of engagement, defined what can constitute an act of war, and
have established what are their proper measures to take in response.
The North Atlantic Treaty Organization (NATO) has established a strategic
concept for the defense and security of their member states. On 19 November 2010, NATO
stated that "We will ensure that NATO has the full range of capabilities necessary to deter
and defend against any threat to the safety and security of our populations. Therefore,
we will...develop further our ability to prevent, detect, defend against and recover from
cyber-attacks, including by using the NATO planning process to enhance and coordinate
national cyber-defence capabilities, bringing all NATO bodies under centralized cyber
protection, and better integrating NATO cyber awareness, warning and response with
member nations[14]."
Also on the later part of year 2010, U.S. DoD Deputy Secretary William J. Lynn III
said that "the Pentagon has formally recognized cyberspace as a new domain of warfare.
Although cyberspace is a man-made domain, it has become just as critical to military
operations as land, sea, air, and space. As such, the military must be able to defend and
operate within it. To facilitate operations in cyberspace, the Defense Department needs an
appropriate organizational structure." [15] On May 21 of 2010, the U.S. Cyber Command
(USCYBERCOM)achievedtheirinitialoperationalcapability,withGeneralKeithAlexander
as their commander [16].
USCYBERCOM is a sub-unified command subordinate to U. S. Strategic Command
(USSTRATCOM).Theirmissionstatementis"USCYBERCOMplans,coordinates,integrates,
synchronizes, and conducts activities to: direct the operations and defense of specified
Department of Defense information networks and; prepare to, and when directed, conduct
full-spectrum military cyberspace operations in order to enable actions in all domains,
ensure US/Allied freedom of action in cyberspace and deny the same to our adversaries."
The work focus is that "USCYBERCOM will fuse the Department’s full spectrum
of cyberspace operations and will plan, coordinate, integrate, synchronize, and conduct
activities to: lead day-to-day defense and protection of DoD information networks;
coordinate DoD operations providing support to military missions; direct the operations
and defense of specified DoD information networks and; prepare to, and when directed,
conductfullspectrummilitarycyberspaceoperations.Thecommandischargedwithpulling
together existing cyberspace resources, creating synergy that does not currently exist and
synchronizing war-fighting effects to defend the information security environment.
USCYBERCOMwillcentralizecommandofcyberspaceoperations,strengthenDoD
cyberspace capabilities, and integrate and bolster DoD’s cyber expertise. Consequently,
USCYBERCOM will improve DoD’s capabilities to ensure resilient, reliable information
and communication networks, counter cyberspace threats, and assure access to cyberspace.
USCYBERCOM’s efforts will also support the Armed Services’ ability to confidently
conduct high-tempo, effective operations as well as protect command and control systems
and the cyberspace infrastructure supporting weapons system platforms from disruptions,
intrusions and attacks."](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-96-2048.jpg)
![97ICT Development and Cyber Security Reader
IntheUnitedKingdom,theUKCyberSecurityStrategy[17]publishedonNovember
2011, called for the creation of a dedicated and integrated civilian and military capability
within their MoD, and setting up the Defence Cyber Operations Group (DCOG)[18]. An
interim DCOG is supposed to be in place by April 2012, and is expected to achieve full
operational capability by April 2014. The DCOG "will include a Joint Cyber Unit hosted
by GCHQ at Cheltenham whose role will be to develop new tactics, techniques and plans
to deliver military effects." "A second Joint Cyber Unit embedded within the centre at
Corsham will develop and use a range of new techniques, including proactive measures,
to disrupt threats to (UK's) information security." Basically, DCOG is developing an
offensive capability to respond to UK's enemies who are trying to launch attacks against
their critical infrastructure, detect and disrupt espionage operations, or disable weapons
of mass destruction through cyber attacks.
Many counter-terrorist operators in the world appreciated a taste of British humor,
when MI6's "Operation Cupcake" became public on June 2011 [19]. British intelligence
penetrated an al-Qaeda online magazine and replaced bomb-making instructions with a
recipe for cupcakes.
Australia's Cyber Security Operations Centre (CSOC), based within the Defence
Signals Directorate (DSD), focuses on identifying and responding to cyber incidents of
national significance[20]. It is interesting to note that the language used by CSOC is less
aggressive than their American and British counterparts.
Unit 8200 is from Israel, and known to be one of the most active and advanced
group of cyberwar operators in the world[21]. Although they are the largest unit in the
Israel Defense Forces (IDF), and their alumni have started-up many international high-tech
companies like Check Point Software Technologies, there is not much information known
about them. It is observed that their missions fit very well the Israel's defense doctrine,
including conduct of pre-emptive strike operations, and that any combat should take place
on enemy territory as much as possible.
In the South East Asian region, South Korea's Ministry of National Defense [22]
launched a Cyber Command on January 2010, under the control of their Defense Security
Command (DSC). They also added that with their 200 specialists, they have the capability
to conduct both defensive and offensive cyber operations, under the direction of the
defense minister.
Meanwhile, North Korea's Reconnaissance Bureau of the General Staff Department
[23] is credited to be trailing only with the capabilities of the Americans and the Russians
[24]. On April 28 until May 13 of 2012, GPS signals were jammed in S. Korea by the electronic
combatants of N. Korea, causing difficulties in air and marine traffic controls.
Senior Colonel Geng Yansheng, spokesperson for the China's Ministry of National
Defense as well as director-general of the Information Office of the Ministry of National
Defense, announced on May 2011 that their People's Liberation Army (PLA) established
an "Online Blue Army" in order to enhance Chinese troops' network protection only [25].
Many observers worldwide however, believe that their unit with at least 30 operators,
organized under the Guangdong Military Command, is an essential part of China's assets
who are responsible for being the single largest source of cyber attacks [26].](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-97-2048.jpg)
![98 ICT Development and Cyber Security Reader
Very recently however, Chinese telecom companies Huawei and ZTE are tagged
by the U.S. Congress as a security threat to the critical infrastructure of the United States,
by providing equipment that are alleged to be capable of relaying American secrets back
to China. In their intelligence report, the Americans state that "China has the means,
opportunity and motive to use telecommunications companies for malicious purposes."
"Based on available classified and unclassified information, Huawei and ZTE cannot be
trusted to be free of foreign state influence and thus pose a security threat to the United
States and to our systems," the report says [27].
Casus Belli
Article II, Section 2, of the 1987 Constitution of the Philippines states that our
nation "renounces war as an instrument of national policy, adopts the generally accepted
principles of international law as part of the law of the land and adheres to the policy
of peace, equality, justice, freedom, cooperation, and amity with all nations" [28]. Article
II, Section 7 also says that "The State shall pursue an independent foreign policy. In its
relations with other states, the paramount consideration shall be national sovereignty,
territorial integrity, national interest, and the right to self-determination."
The Philippines is a very peaceful nation, and throughout history, it has never
even dreamt of occupying another nation-state. On the contrary, the Philippines have
been occupied by other nation-states in its hundreds of years of existence as a nation. The
rejection of war as a national policy is consistent with the Charter of United Nations, which
says in Chapter I, Article 1, that "All Members shall refrain in their international relations
from the threat or use of force against the territorial integrity or political independence of
any state, or in any other manner inconsistent with the Purposes of the United Nations"
[29].
However, the 1987 Constitution of the Philippines only disowns aggressive war,
but not defensive war which will only for the preservation of national honor, integrity,
and the security of the Filipino. The nation-state of the Philippines will not waive the
fundamental right of self-preservation. President Benigno S. Aquino III upholds the 1987
Constitution by documenting his statement of principles in his National Security Policy
2011-2016, saying that "The Philippines needs to develop a defensive capability against
perceived or real external security threats" [30].
The National Security Policy intends to promote internal socio-political stability
by: ensuring the effective delivery of basic services; helping to protect the nation's natural
resources and reducing the risks of disasters; promoting economic reconstruction and
ensuringsustainabledevelopmentthroughincreasedinvestmentsincriticalinfrastructures;
pursuing reforms in the security sector; strengthening institutions and internal mechanisms
to safeguard public order and security; contributing in the strengthening of the rule of law
throughout the country; promoting the peace process as the centerpiece of the Internal
Security Program; and launching a holistic program to combat terrorism. The National
Security Policy also wants the Philippines to develop a defense capability to protect its
soveriegnty and strategic maritime interests.
The term "critical infrastructure" has been officially defined and recognized
back in 24 September 2003 when the Cabinet Oversight Committee on Internal Security](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-98-2048.jpg)
![99ICT Development and Cyber Security Reader
(COC-IS) created the Task Force for Security of Critical Infrastructures (TFSCI), headed
by Undersecretary Abraham Purugganan [31]. Critical infrastructures are vital not only
for economic growth and development, but also as necessary means for the conduct of
each Filipino's daily lives. Critical infrastructure include assets or facilities for: energy
generation, transmission and distribution; information and communications systems;
transportation systems; public health facilities; financial services; government public
safety and emergency services; agriculture and food production and distribution; strategic
commercial centers; as well as religious and cultural centers. TFSCI, now defunct, then
coordinated all government efforts to manage and mitigate any threats against the critical
infrastructure as those are deemed threats to the national security of the Philippines.
Any threat or attack conducted through cyberspace, against the national security
of the Philippines, should be identified, assessed, and then mitigated, if not eliminated.
These threats involve espionage, terrorism, sabotage, or subversive activities. If an attack
through the domain of cyberspace by another state yields death or physical injury of
people, property damage, disruption of critical infrastructure, overthrow of the legitimate
government of the Philippines, hostile disclosure of state secrets, with an outcome
equivalent to a conventional military attack, then that event should merit an appropriate
military action. The amount of damage caused by the cyber attack, whether actual or
implied, should be used a metric as to what will justify proper retribution.
To add to previously mentioned real-world examples of cyberwar operations, other
scenarios that could cause harm to the national security of the Philippines are not limited
to: opening of dams to intentionally drown entire communities; disruption of air traffic
navigation controls to chaos in, or death from the skies; suppression of TV or public radio
infrastructure; theft of confidential e-mail containing state secrets regarding the diplomatic
position of the Philippines versus China, in relation to disputes in economic trade as well
as territories in the West Philippine seas; as well hijacking of phone and Internet assets for
espionage purposes.
The guidelines set by the National Security Policy of President Aquino may be
interpreted to allow only the undertaking of defensive actions in a foreign state, or if
within the Philippines, only if reliable intelligence reports indicate that there is a clear
and present danger against national security, that would have disastrous consequences
like death or loss of critical infrastructure. This practically means that the Armed Forces
of the Philippines may not be tasked to employ kinetic weapons against the aggressor, but
instead employ cyberwar operations to stop the source of cyber attacks.
Rules of Engagement (ROE)
The directive that controls the use and degree of force, how and when, for what
duration and what target, that generally specifies the circumstances and limitations for
engagement, is called the Rules Of Engagement. The complexity and technical aspect of
a cyber attack operation, coupled with the fact that targets may appear or disappear in a
matter of seconds, would required careful planning and development of the ROE.](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-99-2048.jpg)
![100 ICT Development and Cyber Security Reader
Guidelines for crafting the ROE
ROE must take into consideration all applicable domestic and international law,
operational concerns, and political considerations [32]. The recommended underlying
doctrine for drafting the ROE should be Bellum Iustum, or the Just War theory. Part 3,
Section 2, Chapter 2, Article 5, Paragraph 2309, from the Catechism of the Catholic Church
[33], gives us the following "conditions that are subject to the prudential judgement of
those who have responsibility for the common good."
- The damage inflicted by the aggressor on the nation or community of nations
must be lasting, grave, and certain;
- All other means of putting an end to it must have been shown to be impractical
or ineffective;
- There must be serious prospects of success;
- The use of arms must not produce evils and disorders graver than the evil to
be eliminated.
In general peacetime conditions, which the Philippines expect to find itself in most
of the time, the ROE is to be dictated by the principles of necessity and proportionality [34].
"Necessity" requires that cyber operations conducted in self-defense require that a hostile
act occur (i.e. acts of espionage, sabotage, or subversion), or a force or terrorist unit exhibit
hostile intent. An example would include a cyber attack on a positively identified target
that has been qualified by reliable intelligence reports. The "proportionality" principle
states that the force used must be reasonable in intensity, duration, and magnitude, based
on all facts known to the cyber commander at the time, to decisively counter the hostile act
or hostile intent.
Components, other than hostile threat or hostile act, that affect the principles of
necessity and proportionality may include:
- Threat sources and their identification, capabilities of the adversary,
characteristics of adversary's intent, how the adversary analyzes their target,
and range of effects for non-adversarial threat sources
- Threat event identification, and its relevance
- Vulnerabilities of Philippine critical infrastructure and other assets affecting
national security, pervasiveness and severity of the said vulnerabilities
- Likelihood of the hostile threat to occur
- Impact or effects on critical infrastructure and other assets affecting national
security
After the ROE has been analyzed, and permissions have been granted to the
cyber combatant by the commander, the following steps may occur in the cyber attack:
Set Mission Objectives > Establish Baseline Condition of Targets > Recon: Research Target
Information > Discover and Assess Vulnerabilities > Analyze Situation; Plan Attack >
Execute War Plans; Exploit Vulnerabilities; Escalate System Privileges > Re-Engage Other
Targets > Produce Analysis and Report > Re-Set Targets Information Systems to Original
Condition (Optional)](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-100-2048.jpg)
![101ICT Development and Cyber Security Reader
Conclusion
Mary Ann Davidson, the Chief Security Officer of Oracle Corporation, testified on
10March2009totheHomelandSecuritySubcommitteeonEmergingThreats,Cybersecurity
and Science and Technology. She says that there are a few challenges to when applying the
American's Monroe Doctrine on Cyberspace [35].
- Credibility: the deterrence strategy needs teeth to be credible.
- Invocation Scenarios: there should be an escalation framework, where some
instances can invoke cyberwar.
- Attribution: Detecting attacks is hard enough already, and attributing them
correctly is even harder, but not impossible.
Taking those said technical and ethical challenges into consideration, the unsettled
doctrine guiding cyberwar, the unformulated jus ad bellum of cyberwar, while state and
non-state actors in cyberspace build up their capacity for initiating threat events, the time
to recognize cyberspace as a new combat domain, is now. The correct time to investigate
the Philippine capacity to engage in cyberwar, should be prior to the conduct of cyber
operations, not during an emotional or desperate situations, or after being shamed on the
international scene. The Philippines have all the pieces to put a Cyber Command in place,
and can have it done right from the start, to engage, sustain, and achieve objectives in
cyberspace.
# # #
Endnotes
[1] Alexander Merezhko; International Convention on Prohibition of Cyberwar in
Internet; http://www.Politik.org.UA/vid/publcontent.php3?y=7&p=57
[2] Alexander Moseley; The Philosophy of War; http://www.IEP.UTM.edu/war/
[3] Brian Orend; War; http://Plato.Stanford.edu/entries/war/
[4] Sandro Gaycken; Cyberwar – Das Internet als Kriegsschauplatz;, https://www.
OpenSourcePress.DE/index.php?26&tt_products=313
[5] Nathan Thornburgh; The Invasion of the Chinese Cyberspies; http://www.Time.
com/time/printout/0,8816,1098961,00.html
[6] Ian Traynor; Russia Accused Of Unleashing Cyberwar To Disable Estonia; http://
www.Guardian.co.UK/world/2007/may/17/topstories3.russia
[7] Capt. PShakarian; The 2008 Russian Cyber Campaign Against Georgie;
http://USACAC.Army.mil/CAC2/MilitaryReview/Archives/English/
MilitaryReview_20111231_art013.pdf
[8] Information Warfare Monitor; Tracking GhostNet; http://www.InfoWar-Monitor.
net/research/
[9] NateAnderson;Confirmed:UsAndIsraelCreatedStuxnet,LostControlOfIt;http://
Arstechnica.com/tech-policy/2012/06/confirmed-us-israel-created-stuxnet-lost-
control-of-it/
[10] Budapest University of Technology and Economics; Duqu: A Stuxnet-Like
Malware Found In The Wild; http://www.CrySys.HU/publications/files/
bencsathPBF11duqu.pdf
[11] Kim Zetter; Meet ‘Flame,’ The Massive Spy Malware Infiltrating Iranian Computers;
http://www.Wired.com/threatlevel/2012/05/flame/](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-101-2048.jpg)
![102 ICT Development and Cyber Security Reader
[12] Max Fisher & Jared Keller; Syria's Digital Counter-Revolutionaries; http://
www.TheAtlantic.com/international/archive/2011/08/syrias-digital-counter-
revolutionaries/244382/
[13] Chiara Zambrano; Chinese Hackers Have More Sinister Plans; http://rp1.ABS-
CBNnews.com/nation/04/27/12/chinese-hackers-have-more-sinister-plans-
experts-warn
[14] NATO; Active Engagement, Modern Defence; http://www.NATO.int/cps/en/
natolive/official_texts_68580.htm
[15] William J. Lynn III; Defending a New Domain; http://www.Defense.gov/home/
features/2010/0410_cybersec/lynn-article1.aspx
[16] https://www.CYBERCOM.mil (Access restricted.)
[17] The UK Cyber Security Strategy; http://www.CabinetOffice.gov.UK/sites/default/
files/resources/uk-cyber-security-strategy-final.pdf
[18] http://www.MoD.UK/DefenceInternet/AboutDefence/WhatWeDo/
DoctrineOperationsandDiplomacy/JFC/
[19] http://www.Telegraph.co.UK/news/uknews/terrorism-in-the-uk/8553366/MI6-
attacks-al-Qaeda-in-Operation-Cupcake.html
[20] http://www.DSD.gov.AU/infosec/csoc.htm
[21] http://Dover.IDF.IL/IDF/English/News/today/2008n/09/0101.htm
[22] http://www.KoreaTimes.co.KR/www/news/nation/2009/12/205_56502.html
[23] http://www.GlobalSecurity.org/intell/world/dprk/rb.htm
[24] Choi He-Suk, The Korea Herald; N. Korea Has Third Most Powerful Cyberwar
Capabilities; http://www.Stripes.com/news/pacific/n-korea-has-third-most-
powerful-cyberwar-capabilities-1.179826
[25] http://English.People.com.CN/90001/90776/90786/7392182.html
[26] http://www.FoxNews.com/tech/2011/05/26/china-confirms-existence-blue-
army-elite-cyber-warfare-outfit/
[27] U.S. House of Representatives; Investigative Report on the U.S. National Security
Issues Posed by Chinese Telecommunications Companies Huawei and ZTE; http://
Intelligence.House.gov/sites/intelligence.house.gov/files/documents/Huawei-
ZTE%20Investigative%20Report%20%28FINAL%29.pdf
[28] The 1987 Constitution Of The Republic Of The Philippines; http://www.Gov.
PH/the-philippine-constitutions/the-1987-constitution-of-the-republic-of-the-
philippines/the-1987-constitution-of-the-republic-of-the-philippines-article-ii/
[29] Charter of the United Nations; http://www.UN.org/en/documents/charter/
chapter1.shtml
[30] National Security Policy 2011-2016: Securing the Gains of Democracy; http://www.
Gov.PH/2011/08/18/national-security-policy-2011-2016/
[31] Rose Palacio; Task Force To Protect Critical Infrastructure; http://Archives.PIA.
gov.PH/?m=12&sec=reader&rp=1&fi=p040916.htm&no=7&date=09/16/2004
[32] https://rdl.Train.Army.mil/catalog/view/100.ATSC/0EF89CA1-2680-4782-B103-
D2F5DC941188-1274309335668/7-98-1/chap2l4.htm
[33] Catechism of the Catholic Church; http://www.Vatican.VA/archive/ENG0015/__
P81.HTM
[34] Defining The Rules Of Engagement; http://www.GlobalSecurity.org/military/
library/report/call/call_96-6_roesec2b.htm
[35] MaryAnnDavidson;TheMonroeDoctrineinCyberspace;http://www.WhiteHouse.
gov/files/documents/cyber/Davidson%20MaryAnn%20-%20The%20Monroe%20
Doctrine%20in%20Cyberspace.pdf](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-102-2048.jpg)
![103ICT Development and Cyber Security Reader
The Evolving Landscape on
Information Security
Wilfred G. Tan, Carlos T. Tengkiat & Simoun S. Ung
Introduction
W
e all have a preconceived notion on information technology security; however
for a lot of organizations this value is subjective because there is an acceptability
of risk. This is not to imply a particular organization is unaware of the value
of security; it may simply be that the organization needs to consider the allocation of its
resources for security relative to the value of the asset being protected.
A large number of organizations, as evidenced by strong growth and interest in
security standards such as PCI-DSS [1], either depend on or follow guidelines set forth by
government institutions and standards bodies. Conventional wisdom dictates that following
guidelines is normally a good approach. As a security officer, planner or executive, one
should always consider going beyond the existing standard and to be reminded that the
security standards are developed in response to already recorded and occurring incidents.
Moreover, security standards take time for the standard setting bodies to create, review,
approve and implement. Security is a living practice and needs the proper attention, time
and consideration.
Laying out and maintaining a comprehensive cyber security plan not only requires
expertise, but also involves careful thought, assessment, and constant refinement and
adjustments. In addition, legal frameworks differ from country to country; therefore, best
practices in one country are not directly portable to a different country, even within similar
industries. Unlike more traditional crimes such as theft and robbery, the specific rules and
regulations tend to be varied at best for cyber-security and cyber-crime related incidents.
Computer security related incidents have risen significantly over the past decade
[2] and there is every indication that this trend will continue for the foreseeable future. The
Global Security Report of Trustwave[3] presents the origin of cyber-attacks:
Russia leads the statistics with 29.6% in the data[3]. However, because 32.5% of all
attacks are from of unknown origin, it can be as likely (or equally unlikely) that any one
nation is the single source or culprit of all of the incidents. Pinpointing the location in a
timely manner is very difficult, if not impossible, given that the technology today allows
users to use anonymous proxies to connect to the Internet which further compounds the
problem.
This article is written for non-technical executives and policy makers, whose
responsibilities require them to interact with information security professionals, as a primer
on the current landscape of information security as well as its likely evolution. Security
professionals and practitioners are already well-versed in the material contained herein.
The paper examines the motivation behind cyber-attacks followed by a survey of common
threats and attack variants. It then presents the popular defensive strategies followed by a
discussion of future challenges and developments.](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-103-2048.jpg)
![104 ICT Development and Cyber Security Reader
Motivation
Behind all threats and cyber security breaches are either individuals or organizations.
Cyber security incidents do not occur in a vacuum. Generally, the motive behind a cyber-
attack can be classified as follows: personal reasons, unlawful profiteering, corporate or
national interests, and other purposes.
Personal Reasons
Personal reasons for conducting a cyber-attack include peer recognition, revenge,
personal gain or satisfaction, and even curiosity. Some intruders derive a perverse sense
of fun from conducting the attack and revel in the psychic income of being noted for
notoriety.
Unlawful Profiteering
Perhaps the most common motivation for conducting a cyber-attack is financial
gain. The primary goal of fraud is to gather information that can be used to access funds of
other entities for illicit proceeds. Popular targets include savings accounts and payment,
debit and credit, card data. Organized criminal syndicates are the primary perpetrators of
these attacks. Inopportunely, the skill and savoir-faire developed are often adopted for use
in cyber-terrorism and other cyber-attacks.
Although there is no data for the Philippines, a study conducted by eWEEK Europe
in 2010[4] on a simulated auction of stolen data determined that the relative value of data](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-104-2048.jpg)
![105ICT Development and Cyber Security Reader
is primarily determined by purchaser. The end goal remains the same, obtain information
through illegal and fraudulent means which can be used for financial gain. Information
itself has become a commodity; it can be traded, bought and sold.
Corporate or National Interests
The strategic objectives for a corporation or nation-state are sometimes achieved by
attacking others using cyber-warfare capabilities. The intent may be to disable a nuclear
enrichment program or a more mundane purpose such as spy, steal or subvert a rival’s
plans and secrets.
In mid-2010, Stuxnet was discovered. The singular target of this worm was to disable
and destroy Siemens industrial equipment which were specifically used to control centrifuges
that create nuclear material for a fissionable weapon. According to a study by Symantec in
August, 2010 [5], 60% of the computers infected by Stuxnet were in Iran suggesting a highly
‘targeted’ operation. The worm’s sophistication and intelligence suggested a nation-state
level of sponsorship; speculation was rife that the United States and Israeli forces were at
least partially responsible for the development and deployment of the worm.[5]
Threat Evolution
Approaches to attacks have evolved over time, adapting to developments in
technology. Tools for exploiting systems have evolved considerably; likewise, tools that
are available for testing and exploiting vulnerabilities are readily available in the market.
There are even attack platforms freely available that ironically were intended to test the
security of a system. Several of the more common threats are outlined below: physical,
cyber-stalking, social engineering, phishing, distributed denial of service, network attacks
and malwares.
Physical
In the 1980s, the common practice was to actually go onto the premises of the
target company or to harvest data from unprotected sources. Criminals would find ways
to physically obtain storage media or hardcopies of data. Dumpster diving, or the sifting
through garbage and trash to find bits and pieces of information, is still practiced today.
The careless disposal of seemingly innocuous information such as an obsolete version of an
information security plan, PIN mailers, passwords, social security numbers, et cetera can
facilitate an attack via social engineering or phishing.
Today, practices have improved to include tapping into data cabling that are
accessible from unsecured areas and the access of unlocked, accessible computer servers
and systems. It is still a common occurrence for unencrypted, sensitive data to be lost or
stolen from physical media such as USB flash drives, laptops and cellular phones.
Cyber-Stalking
Cyber-stalkers assault their victims using electronic communication: email, instant
messaging (IM) and/or posts to a website or discussion group. While most cyber-attacks
target an organization, cyber-stalking tends to be of a more personal nature. Cyber-stalkers](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-105-2048.jpg)
![106 ICT Development and Cyber Security Reader
typically gather personal and private information about their target then send them harassing
or threatening messages.
Trolling is a form of cyber-stalking in which negative posts, comments or other
defamatory statements are made which are injurious to the reputation or emotional health
of the victims. When committed by more than one individual, trolling is also known as
cyber-bullying. Sadly, there are cases involving teens which have resulted in the victims
committing suicide.
Social Engineering
Social engineering cyber-attack involves the manipulation of people to perform
certain actions that can compromise security; this requires a solid understanding of human
responses and behaviour. Although physical contact is not necessary, some form of trickery
to gain the confidence of the target is employed. Social engineering attack occurs in two
phases: information gathering then the pretext stage in which a believable story is crafted
in order to earn legitimacy and gain the trust of the target.
Social engineering is not strenuous on the attacker, thus it is normally employed
in conjunction with other forms of cyber-attack. The insertion of malware into otherwise
hardened, secure systems is a common combination with social engineering. Many enterprise
systems are well protected and require significant time and effort to breach. However, if
the attackers are able to use social engineering to insert physical media such as USB flash
drives into the internal network, then all the external defences are immediately bypassed.
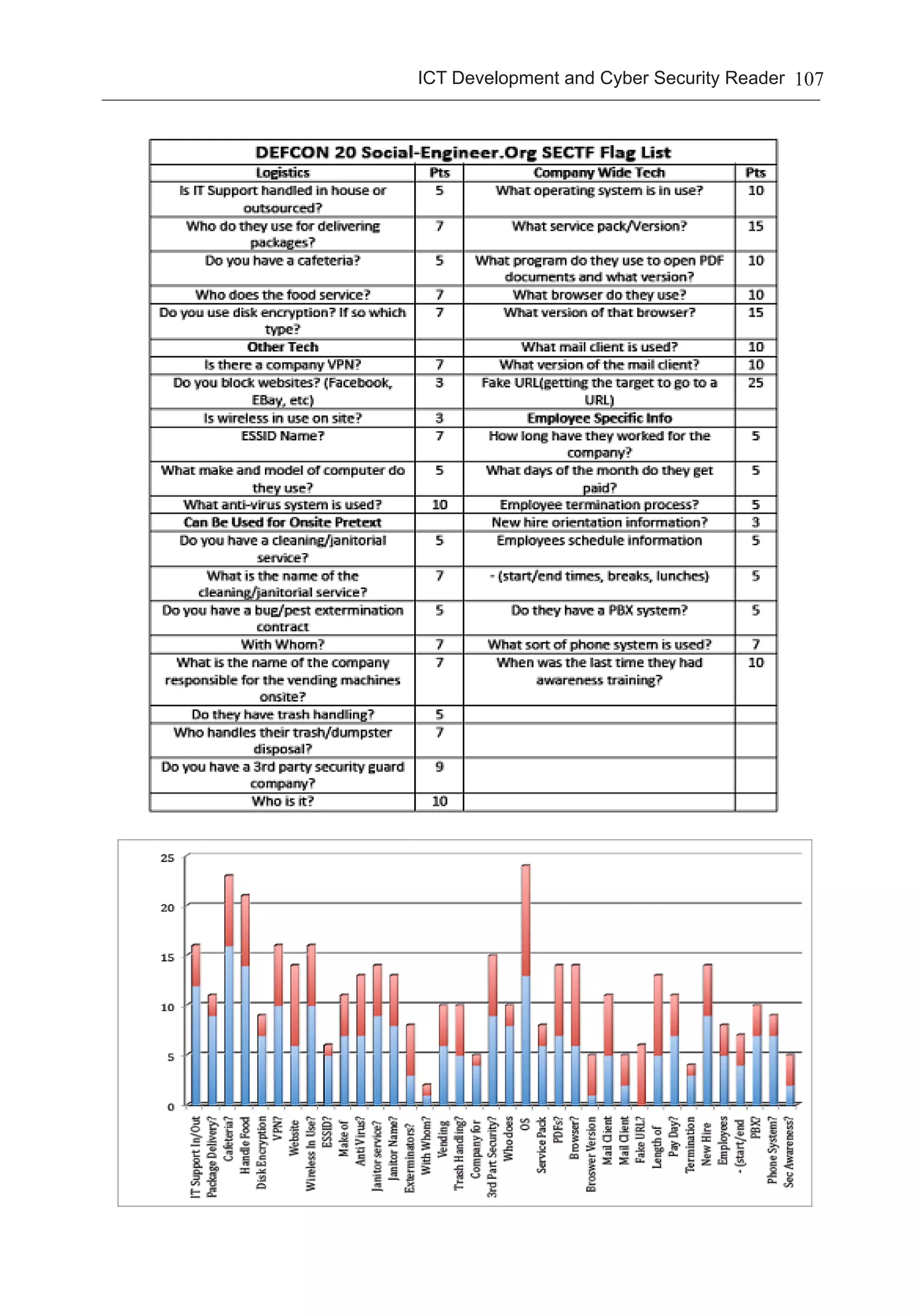
Based on recently conducted social engineering study[6], companies with well-
implemented security awareness protocols are more resistant to social engineering tactics.
Participants in the oil industry fared better compared to less security aware industries
like retail. This study was designed such that questions were designed that would expose
security design and architecture of the respondent’s organization:
The study[6]revealed that certain data can be harvested from the internet itself.
Researchers were able to utilize the data culled from the internet in their social engineering
tasks to profile a target’s internal security implementation. The table below displays the
details gathered from the questionnaire above in blue while the additive information
garnered from the internet is shown in red:
Recently, face-to-face social engineering tactics have been increasing; this is
disquieting since it may expose the targeted individual to physical danger.](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-106-2048.jpg)


![110 ICT Development and Cyber Security Reader
Distributed Denial of Service (DDOS)
DDOS is one of the older forms of attacks that are still popular today. In a DDOS
attack scenario, the victim typically finds their system slows to a crawl or unable to respond
at all. There are several variants that are commonly used such as ICMP Flooding, SYN
flooding, Teardrop, and others. The defining aspect of DDOS attacks is the rendering of
the target system crippled or inoperable, thereby denying service to the system’s legitimate
users. As recent as mid-2012, DDOS attacks against major financial institutions such as
HSBC, Bank of America, and JP Morgan Chase were recorded. [7]
The duration and severity of the attack is dependent on the number of zombies,
or slave computers, used by the attacker, and the resiliency of the target computer(s) to
withstand the attack. A DDOS attack may be used in conjunction with other attacks to exploit
vulnerabilities exposed while the DDOS attack is in progress; sometimes, a DDOS attack is
a diversionary tactic to enhance the probability of success of other attack methods. Major
disruptions to critical infrastructure like defense, utilities and banking will result not only
in mere inconvenience due to loss of services but cause significant financial and economic
losses.
Network attacks
TheU.S.DepartmentofDefensereferstonetworkattacksas“…actionstakenthrough
the use of computer networks to disrupt, deny, degrade, or destroy information resident in
computers and computer networks, or the computers and networks themselves.”[8]If an
attacker successfully connects to the network of the target, innumerable opportunities to
launch attacks are made available.
Commonmistakesinnetworksecurityareweak,defaultornon-existentadministrator
passwords. Moreover, ill-designed networks also allow easy access to database servers,
the usual targets for data mining. Attackers can use SQL injection, in which direct SQL text
is encoded as part of the attack stream, in an attempt to subversively access a back-end
database system.
Malwares
The current trend of cyber-attacks is predominantly associated with malwares.
Trustwave defines malware as “… often purposefully designed to capture and extricate
data, provide remote access, or automate compromised systems into a botnet — or to just
cause general mayhem.”[9]Malware comes in a myriad of types and varieties. The common
categories known today include computer viruses, worms, trojan horses, spyware, adware
and root kits.
Entire software product suites and solutions have been created to combat malwares.
However, malwares have evolved and continue to do so; they are constantly being updated
to meet challenges of exploiting new vulnerabilities and avoid detection by the users and
by third-party security products. These accounts for the discouraging statistics that show
infections often go undetected. The popularity of malware as an attack vector is evident in
the fact that by 2007 the number of malwares created on that one year alone is the equivalent
to the combined total of the previous twenty years.[10]](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-110-2048.jpg)
![111ICT Development and Cyber Security Reader
Malwares are used with great efficacy to achieve a beachhead in infiltrating systems. Some
of the recent incidents involving malware are listed below:
Flame
Discovered by the Iranian National Computer Emergency Response Team (CERT),
Kaspersky and CrySyS Lab, Flame is widely considered as one of the most sophisticated
malware ever created.[11] It spreads via local area network or USB. Infected computers act
as a bluetooth beacon and attempts to harvest contact information from nearby bluetooth-
enabled devices. At twenty megabytes, Flame is uncharacteristically large for a malware. Its
capabilities include recording of audio, keystrokes, screenshots and Skype conversations;
thus Flame is deemed a cyber-espionage tool.
RSA Breach
RSA experienced a security breach in 2011.[12] The attack vector was an email
sent to an employee with an Excel attachment that contained a malware. This malware
exploited vulnerabilities in Adobe Flash and installed a variant of Poison Ivy, a common
remote administration tool. The attackers then obtained critical information including the
token seeds in SecureID and algorithm designs used by RSA; consequently, the RSA security
tokens were rendered vulnerable for exploitation. This directly resulted in cyber-attacks
against Lockheed Martin and L3 Communications, both US military contractors.
Malwares have proven to be a very effective and potent tool for cyber-attacks
and their continued use will foster further evolution in sophistication and complexity.
Organizations should take steps to detect and eradicate malwares; depending solely on the
hardening of perimeter defense is a common fallacy to prevent malwares from infiltrating
an organization.
Common Defensive Strategies
Information security personnel and teams tend to use several common defensive
strategies. Unfortunately, there is no perfect defensive strategy; therefore, to be effective,
a defensive strategy must be continuously upgraded and assessed against the constantly
evolving cyber-attack mechanisms and methodologies.
Physical
There are numerous physical defensive strategies; the most common are the
following:
1. Deployment of access systems secured by biometric, ID card, PIN and/or a
combination thereof;
2. Closed circuit TV (CCTV) security cameras; and
3. Doors, cages, locks and man-traps.
One of the simplest and cost-effective strategies is to locate critical servers and
systems in a secure facility; failing that, the servers and systems should be locked in a cage
to prevent unauthorized tampering and access.](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-111-2048.jpg)

![113ICT Development and Cyber Security Reader
property rights, this is the most important, self-serving incentive to procure properly
licensed software as it guarantees that there will be support and maintenance. With open-
source software, it is critical to implement a maintenance cycle to ensure that any bugs or
vulnerabilities in the software are patched quickly and consistently.
Firewalls
Firewalls are network devices that filter traffic; it attempts to segregate public or
open traffic that exist beyond the organization’s network perimeter. Firewalls range from
the basic that protect your home network costing a few thousand pesos to the enterprise
versions costing several millions. There are many brands of firewalls from manufacturers:
Cisco, Juniper, Checkpoint, Fortinet, Huawei, ZTE among others. Of special interest lately
is the Congress of the United States position that Huawei and ZTE pose a security threat.
[13]
A properly configured and maintained firewall defends against many threats. It is
a key component in many security strategies implemented today. Ensuring that the firewall
is properly patched is another important key to having a good defensive strategy.
Regular Testing and Backups
Regular tests of information security systems are crucial in maintaining readiness.
Internal and external penetration tests, scans, and verification procedures all contribute
towards ensuring that systems are configured properly. Regular backups are akin to buying
insurance. Failures are an unavoidable part of the human experience and information
systems are not exempt. Having a ready backup is no longer a luxury but a necessity.
Intrusion Detection Systems/Intrusion Prevention Systems
Intrusion detection and intrusion prevention systems(IDPS) are a class of devices
that have come into the forefront of defensive arsenal about a decade ago. Such devices
are capable of detecting incidents by monitoring events or inspecting packets and, at the
start of an incident, trigger some automated response including reconfiguration of firewalls,
sending out alerts by SMS or email, locking down ports, et cetera.
Most systems in the market today involve the deployment of hardware appliances,
few are software based, and these are usually installed in-line either behind, or adjacent to
the firewall(s) in an organization’s network. The NIST[14]lists four types of technologies
available today:
1. Network based: examination and detection based on network segments, or network
and application protocol.
2. Wireless: examination of wireless network traffic.
3. Network behaviour analysis: examination of system-wide behaviour including the
sudden rise of packets, policy violations, et cetera.
4. Host-based: limited to single host examination and events linked to the single
host.](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-113-2048.jpg)
![114 ICT Development and Cyber Security Reader
IDPS are useful in detecting and identifying potential incidents. Therefore, they
are an indispensable tool in the defensive toolkit of many information security managers.
An IDPS provides intrinsic value by adding automated detection, logging, recording, and
monitoring capabilities to an organization, when configured and maintained properly.
Outsourcing of information security
Within the Philippine context, many organizations, including government agencies,
do not have the budget, expertise or capability internally to properly secure their information
systems. Accordingly, to properly prepare for a cyber-attack, organizations may resort to
outsourcing, analogous to the deployment of private security guards for the protection of
physical assets.
There is a prevailing misconception regarding the role of law enforcement in
information security. By definition, law enforcement agencies provide post-incident
investigation, apprehension and filing of charges against suspected perpetrators. Their
responsibilities do not include ensuring an organization’s systems are safe and secure.
Typically, a Computer Security Incident Response Team (CSIRT) or a Computer Emergency
Response Team (CERT) is engaged to assist an organization to prepare, simulate cyber-
attacks and conduct post-assessments of information security systems.
Future Developments and Challenges
Current technological trends are likely to continue in the foreseeable future. With
the rapid and accelerating pace of change in technology, a discussion of the pervasive
technologies and their prospective impact to information security is warranted.
Mobile technology
Today’s smart phones are truly mobile computers; some have greater processing
power than desktops from less than a decade ago. Penetration rates in more advanced
countries have exceeded 50% and have reached 78% in the United States. [15] This trend
will rapidly be replicated in emerging markets like the Philippines, particularly with the
commonplace availability of smart phones retailing for less than one hundred US dollars.
With the advent of mobile commerce and the Philippine propensity for rapid
adoption of mobile phones, there will be a host of new, unforeseen security challenges. This
will be accelerated by the deployment of LTE empowering mobile broadband by the local
telecommunication carriers. Compounding the security challenges with mobile is the lack
of a legal framework and the non-existent registry of mobile SIM cards: attackers utilizing
a mobile platform will enjoy even greater anonymity.
Initial malware on the mobile platform were largely limited by the fragmented,
proprietary operating systems that ran the previous generation of phones. The industry
has already consolidated to four major mobile platforms: Apple’s IOS, Google’s Android,
Windows Mobile and Blackberry. With this convergence, the mobile platform presents a
tantalizing target for cyber-attackers. There have been numerous incidents involving social
engineering with deceptive messages sent to victims asking them to send money to process
their contest winnings or to help a friend or relative in a supposed emergency situation.](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-114-2048.jpg)
![115ICT Development and Cyber Security Reader
Video/Voice Over IP (VOIP)
Skype™
was one of the pioneers that allowed people to make voice calls, later adding
video calls, for free utilizing IP technology. Nowadays, multi-party video conferencing is
already commonplace. The National Telecommunication Commission has issued VOIP
licenses for several years already. From an implementation and technology angle, VOIP is
terrific: provision of clear communications enabled by constantly improving compression
technology. Commercialized form of 3-D hologram communication may soon be
achievable.
Cyber-attackers recognize that networks carrying voice and video data as an
attractive target. A Brazilian CERT noticed an upsurge in scanning for VOIP traffic in their
honey pot network. [16] Intruders that gain access to a VOIP system would potentially be
able to monitor, access and even reroute all communications made through it.
Outsourcing cyber-attacks
Insofar as protecting information security systems are being outsourced to trusted
professionals, cyber-attackers have also begun to resort to outsourcing. The Russian
underground market in cybercrime is vibrant. The inexpensive cost for outsourcing of
various methods of cyber-attacks is alarming; a sampling of the available services and its
prices is listed below: [17]
Service Price in US dollars
Hiring a DDOS attack $30 to $70 per day
Email spam $10 per million emails
Bots for a botnet $200 for 2,000 bots
ZeuS source code $200 to $500
Hacking a Facebook or Twitter acct $130
Hacking a Gmail account $162
Scans of legitimate passports $5 each
Traffic $7 to $15 per 1,000 visitors from US & EU
As cyber-attacks continue to grow in sophistication, this development of outsourcing
cyber-attacks will not only continue unabated, but likely escalate geometrically.
Conclusion
The notion of information security tends to be organization-specific. In the
Philippine context, there is a relatively high tolerance for risk. Even within the defence
establishment, some of the prevailing attitudes are best characterized by the tongue-in-
cheek responses gathered in a series of interviews: “Our approach is security through
obsolescence” and “It’s only 1’s and 0’s anyways, who can read it?” With the pervasiveness
of the internet and technology in human society today and the resultant diminishing barriers
of distance and geopolitical borders, information security must be everyone’s problem and
responsibility.
The Information and Communications Technology Office under the Department
of Science and Technology has already set policy that information and communications](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-115-2048.jpg)
![116 ICT Development and Cyber Security Reader
technology must be governed due to its pervasive and essential nature in today’s society.
[18] The recent attacks to deface government websites should serve as a clarion call for
imperative action. Perhaps due to the technical or the rapidly evolving nature, some of the
national leadership still do not recognize the gravity of the situation, or lamentably, simply
choose to believe it will go away.
For some context within the Philippine environment, consider the IT-BPO industry,
a sunshine and rapidly growing sector of the Philippine economy:[19]
2011 2012 2013
Industry revenues (USD) $11 Billion $13.6 Billion $16 Billion
Full-time employees 638,000 772,000 926,000
How much loss, potential or otherwise, must be suffered by the Philippine economy
for information security to be considered a matter of national security? What is the impact
to this single sector of a single or a series of cyber-attacks or data breaches exacerbated by
inadequate response from government? Government and the private sector must work
together to secure our national interest.
This article presented an overview of the current landscape of information security.
From the motivational aspects behind cyber-attacks to a review of current common
threats and attack variants to a presentation of the popular defensive strategies ending
with a forward look to future challenges and developments. Although technology and
methodologies continue to evolve, the human factor, not rapid technological advancement,
continues to be the biggest source of vulnerability:
· Many continue to blindly follow security standards set by governments and
standards bodies without proper evaluation of their suitability for their own
situation.
· Lax stewardship is the leading cause of security breaches in established
organizations.
· Social engineering is still the most prevalent cause of data compromises.
· Senior leadership, especially at the national level, typically fail to recognize the
critical nature of information security to their organizations until after a breach or
other incident has occurred.
If the Philippines were to experience a cyber-attack today, there is no single office
of primary responsibility within government to mount a coordinated response. At best, the
country can only rely on the Philippine Computer Emergency Response Team (PHCERT),
“… a non-profit aggrupation of Information Security Professionals providing Technical and
Policy Advisory Services Pro Bono Publico.”[20] The National Computer Center recognizes
the limited programs and projects that PHCERT can support: “PHCERT ONLY accepts
security incident reports from its members. Technical advice may be provided depending
on volunteer availability. Forwarding and coordination to the appropriate law enforcement
agency can also be done if the situation warrants or member organization desires to do](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-116-2048.jpg)
![117ICT Development and Cyber Security Reader
so.”[21] On the legal front, although the Philippines recently enacted the Cybercrime
Prevention Act of 2012,Republic Act 10175, to empower law enforcement to better combat
cybercrime, the Supreme Court issued a Temporary Restraining Order delaying its
implementation by 120 days in response to questions about the constitutionality of certain
provisions.
Information security is so pervasive that even a superpower like the United
States and advanced societies like Japan with relatively unlimited budgets find it difficult
to cope with the immense challenges. Government and private sector must cooperate to
make significant progress in this regard. Forging ahead, given the current landscape of
information security and its likely progression, the Philippines must take two foundational
steps to improve its information security:
1. Government must designate a single office of primary responsibility to prepare,
mitigate, and coordinate a response to cyber-attacks; and
2. Government and the private sector must work together and establish a pro-active,
independent, fully-functional Computer Emergency Response Team (CERT) and/
or Computer Security Incident Response Team (CSIRT).
# # #
References
This article relied extensively on the collective knowledge-base and
experience of the authors as well as sources from both the internet and
printed material. Similar references were grouped together for brevity.
1 http://blog.elementps.com/element_payment_solutions/2011/11/visa-releases-pci-compliance-
level-stats.html
2 http://www.pcworld.com/article/79303/article.html
3 http://2011.appsecusa.org/p/gsr.pdf
4 http://www.techweekeurope.co.uk/news/experts-admit-motivation-for-cyber-attacks-
overlooked-6696
5 http://www.symantec.com/connect/blogs/hackers-behind-stuxnethttp://www.symantec.com/
connect/blogs/stuxnet-introduces-first-known-rootkit-industrial-control-systems; http://www.
airdemon.net/stuxnet.html; http://www.reuters.com/article/2010/09/24/security-cyber-iran-
idUSLDE68N1OI20100924
6 http://www.social-engineer.org/social-engineering-ctf-battle-of-the-sexes/
7 http://arstechnica.com/security/2012/10/ddos-attacks-against-major-us-banks-no-
stuxnet/;http://nakedsecurity.sophos.com/2012/09/27/banks-targeted-ddos-attacks/;
http://www.bloomberg.com/news/2012-09-28/cyber-attacks-on-u-s-banks-expose-computer-
vulnerability.html; http://threatpost.com/en_us/blogs/historic-ddos-attacks-against-major-us-
banks-continue-092712
8 U.S. Department of Defense, Joint Publication 1–02: DOD Dictionary of Military and Associated
Terms (November 8, 2010, as amended through May 15, 2011).
9 http://www.iseprograms.com/lib/Trustwave_2012GlobalSecurityReport.pdf
10 http://web.archive.org/web/20071207173837/http://www.f-secure.com/2007/2/
11 http://www.symantec.com/connect/blogs/flamer-highly-sophisticated-and-discreet-threat-
targets-middle-east; http://www.crysys.hu/skywiper/skywiper.pdf
12 Cyber-warfare – The new battlefront for Defence Forces by Dr. Peter Holliday](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-117-2048.jpg)

















![136 ICT Development and Cyber Security Reader
nations around the world. The transnational nature of cybersecurity underscores the need
for transborder cooperation and dialogue since this threat cannot be solved by any one
nation.
The Power of Social Media in Southeast Asia
Southeast Asia is ably considered as one of the promising techno hubs for young
and gadget-oriented consumers in the world. With over half a billion population livable
with hip and young dynamic peoples and growing economy, it is only fitting to admit
that this region will have tremendous contributions and adaptations to the interactive
and high-tech world of social media. Expectedly, there are also dangers caused by the
phenomenal success of social networks in the region’s cybersecurity infrastructures.
Social Media is defined as a group of new kinds of online media, which shares most
or all of the following characteristics that [1] encourages participation, [2] open to feedback,
[3] two-way conversation, [4] forms communities, and [5] thrives on connectedness
(Mayfield, 2008).
Henceforth, social media has created, mobilized, and demonstrated waves
of consciousness and action that reach much more people than traditional industrial
media. As much as social media has the ability to draw together mass involvement in a
personalized way, it also does so in an unsupervised manner, thus crafting it as a potential
threat to human security. Consequently, this formulates social media to be a tool that both
augments and degrades human security (Romero, 2009) with leveled off boons and banes
of cybersecurity landscapes in the current deterritorialized playing field.
A 2012 report released by Nielsen revealed that social media receives a strong
trust rating among consumers in the ASEAN region particularly in Vietnam, Thailand,
the Philippines, and Indonesia. Accordingly, although television still reigns (9 out of 10
people in Southeast Asia watch “Free to Air TV”), but online has grown rapidly in reach
and influence in the last decade.5
Others would believe that there are benefits of social media marketing that includes
the following: [1] it generates exposure for the products/business, [2] it improves web
traffic and the opportunity to build new partnerships, and [3] it generates qualified leads.
In the sphere of social media to date, Twitter – a popular microblogging service
that was launched in July 2006 claims popularity based on userbase in the world, topping
all other social networking services. In a report by the social media monitor Semiocast
revealed that in the “Twitterverse” two Southeast Asian countries, namely, Indonesia
which ranks 5th spot while the Philippines which places 10th spot are hooked to Twitter’s
ever growing 517 million users based from the worldwide rankings (Montecillo, 2012).
Initially, it was Facebook that held the most popular spot among the social networking
sites around the world having 835,525,280 users as of 31 March 2012.
The Wall Street which purports to offer analysis and commentary for investors
proclaimed the Philippines as the “Social Networking Capital of the World,” (Hamlin,
2011). Furthermore, in a 2008 study conducted by McCann Universal, Filipino netizens
ranked: first in social networking, first in sharing photos, first in viewing videos, second to
South Korea in reading blogs, second to Brazil in sharing videos, fourth in writing blogs,](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-136-2048.jpg)
![137ICT Development and Cyber Security Reader
fourth in downloading podcast, and sixth in using RSS/feeds. Accordingly, email (63%),
instant messaging (63%), and search (58%) are the most common online activities for
Filipino internet users with social network site usage at (51%).6
Reasonably, the Philippines is leading other member-countries of ASEAN in
examining conscientiously many pivotal issues of cybersecurity threats in the region.
Having been recently achieved the newly-industrialized country status, our country is
now becoming a hot player and emerging powerhouse in the global village’s playing
field when it comes to ICTs. It is now ranked as the global topnotch for Business Process
Outsourcing (BPO) in the voice sector; still considered as the “texting” or SMS capital
and one of the active hot players in social networking around the world. Previously, the
Philippines was cited in 2002 by Global New Economy Index of the Meta Group for its
“excellent availability” of skilled IT workers with compliment for the Filipinos’ technical
and business skills, such as in mainframes, minicomputers, and microcomputers, and for
their technical and business skills in ICT projects.7
Thus with the expanding sphere of influence of social media worldwide, it has
led many governments to acknowledge the power of social media to engage its citizens
to participate in state-sponsored activities such as elections and policy-making. Now
individuals with well-known reputations such as journalists have a well-established
readership. Other individuals have emerged as “stars” within the political blogosphere,
developing an established network of contacts and readers. Popularity is driven by group
identity be it race, ethnicity, gender or sexual orientation. These blogs draw readers that
are untapped by traditional media. Thus, blogs facilitate the creation of a network of like-
minded individuals (Pole, 2010).
However, there are various social media governance issues that must be addressed,
as pointed out by experts and practitioners, such as the following: [1] how should
organizations regulate and mange the use social media by their staff during work hours?
[2] what sort of risks do organizations face, in terms of potential data loss, unregulated
communication of confidential information and work time? [3] should social media sites
be blocked or disallowed in government institutions and private firms as a whole? [4]
how should the government address the use and abuse of social media in its campaign for
transparency, fair and open exchange of information, and reducing corruption to ensure
wise use of resources? and [5] how to define and adopt a social media policy, including
roles and responsibilities, communications and training, and metrics and monitoring?
(Malacaman, 2010).
New Forms of Cybercrimes
The cyberspace has led to some government and private experts to conclude that
cybercriminals are at the threshold of using the internet as a direct instrument of heinous
crimes and bloodshed. The new threat bears little resemblance to familiar financial
disruptions by hackers for viruses and worms (Cabalza, 2011).
The United States’ Federal Bureau of Investigation (FBI) recently estimated that the
“lovebug”8
made by a Filipino student in 2000 has caused worldwide damage amounting
to approximately USD$12 billion. Hence, threats to the financial systems will have dire
consequences for nations’ ability to operate effectively and efficiently.9](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-137-2048.jpg)


![140 ICT Development and Cyber Security Reader
In addendum, it would not be surprising, if by all means government official
websites, usually hosted by sloppy private industries’ Internet Service Providers (ISP)
could increase espionage from cyberterrorists and can cause massive electronic attacks due
to lack of security mechanisms on computer systems. Violations occur when unauthorized
user illegally accesses network computers that are forbidden to access.
Recently, alien or foreign hackers and cyber attackers infiltrated some Philippine
government sites.17
Thus, study would show that there is leeway that they could scythe
even critical and vital military, commercial, or monetary institutions from remote locations
to disrupt the free world’s defense and communications systems. Possibly, attackers could
hack into computer systems for information gathering or data altering, sabotage, and
installing malicious codes. These malicious codes may be distorted in the forms of Trojans,
worms, and viruses. There are also Deadly Distributed Denial of Service (DdoS) attacks
which employ “zombie” machines that are controlled by a master server. More or less, it
has the ability for taking down entire networks.
Cyberterrorists could also apply information hiding by means of stegonography
where one can simply take one piece of information and hides with another picture or
document. This well-planned strategy could cripple infrastructures and bug down key
government sites and services.18
They have the clout to destroy and disrupt critical infrastructures in split seconds.
With just the hit of a keystroke, one can send a fatal blow by simply sitting in his armchair,
from thousands of miles away. That could wreak greater threats to a wider gamut of
annihilation from a mere nuisance to a larger national security problem.
Jurisdictional Problems And Lack Of Laws On Cybersecurity
I would still cling with my advocacy for a collective action to look at the problem
of jurisdictional and lack of laws related to cybersecurity in Southeast Asia and other
regional blocs in the world that may impede investigations on cyber crimes and cyber
terrorism.
The task of enforcing laws would legitimize the prosecution and extradition of
cyber criminals in a globalizing world and transnational border. I am optimist that cyber
terrorism is now being fought at the international level and recently the UN Counter
Terrorism Committee (UNCTC) is responsible for coordinating cyberterrorism-related
response and information exchange. Meanwhile, legal and security practitioners must
keep abreast of this emerging non-traditional security and must be trained conscientiously
with the fast-changing fads of technology and the many surprises of the internet.
I would still suggest the same mechanisms I addressed in 2007 for the ASEAN
member-countries to achieve a more responsive policy in a volatile and gullible security
environment of cybersecurity. Southeast Asia, which has tremendously experienced
different facets and prisms of terrorism, is now experiencing the effects of cybercrimes
and cyberterrorism. Therefore, I propose that ASEAN countries should forge realistic
agreements based from the following recommendations: [1] to build cooperation and
networks for intelligence reports among ASEAN countries; [2] to engage in government
andprivatecooperation.Toundertakecollaborativecollectionandanalysisofcybersecurity](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-140-2048.jpg)
![141ICT Development and Cyber Security Reader
related information; [3] to increase intensive research on the security of the region’s
cyber structures and minimize duplication of efforts, [4] to organize fora/forums for
stakeholders (e.g. enforcers, prosecutors, and cyber users); and [5] to forge cooperation and
international treatise initiated by governments and private cyber industries in the region
that are necessary mainly because cybercrime and cyberterrorism are multi-jurisdictional
and cuts across border. Hence, there is a need to increase and ignite high-awareness level
on cybersecurity.
Conclusion
The regional security outlook in Southeast Asia is indeed faced with a wide range
and/or combination of traditional, non-traditional, transnational, and crisis management
challenges. The weight of cybersecurity which I proposed and adopted as one of the top five
security issues in the region,19
during the Fifth Network of ASEAN Defense and Security
Institutes (NADI), is an affirmation that cyber infrastructures apparently affect regional
and worldwide security. Future norms on this emerging security threat in the region must
be further enhanced now to lessen the burden of destruction of life, liberty, property, and
security of individuals and nation-states.
Cybersecurity is a new battlefront considered unimaginable in the past, one which
created a borderless world. Cyber attacks on national scale can make or break a nations’
political and economic position. Nations with differences in policy and particular matters
of state interest will look beyond the traditional means of solving disputes and resort to
these cyber attacks. However, he still encouraged everyone to be unified and continue to
strengthen the collaboration not only with the private sector but also to global counterparts
in gearing towards an improved resilience to cyber incidents and to proactively reduce
cyber threats. Through shared principles, countries in the region as well, will build not
only stance as credible gatekeepers of cybersecurity but valuable guardians of national
security (Binay, 2012).
In the end, the proper handling of related information through the use of various
cyber investigative techniques is very significant to help eliminate or reduce such threats.
Sustaining institutionalized cybersecurity programs in Southeast Asia region will be
helpful to continuously develop and improve the competency and skills of leaders and
law enforcers in confronting this international security threat.
# # #
Endnotes
1. Cybersecurity is the protection of data and systems in networks that are connected
to the internet. See information security, as defined in http://www.newswithviews.
com/Trinckes/john100.htm.
2. Cited from Chester Cabalza’s blog article on, “Cyberterrorism and Its Implications
on Global-Local Discourse in Southeast Asia,” uploaded on October 2009 at http://
cbclawmatters.blogspot.com/2009/10/cyberterrorism and-its-implications-on.html.](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-141-2048.jpg)





![147ICT Development and Cyber Security Reader
S. No. 2796
H. No. 5808
Republic of the Philippines
Congress of the Philippines
Metro Manila
Fifteenth Congress
Second Regular Session
Begun and held in Metro Manila, on Monday the Twenty-fifth day of July two thousand
eleven.
[Republic Act No. 10175]
AN ACT DEFINING CYBERCRIME, PROVIDING FOR THE PREVENTION,
INVESTIGATION, SUPPRESSION AND THE IMPOSITION OF PENALTIES
THEREFOR AND FOR OTHER PURPOSES
Be it enacted by the Senate and House of Representatives of the Philippines in Congress
assembled:
CHAPTER I
PRELIMINARY PROVISIONS
SECTION 1. Title. — This Act shall be known as the “Cybercrime Prevention
Act of 20123 .
SEC. 2. Declaration of Policy. — The State recognizes the vital role of information
and communications industries such as content production, telecommunications,
broadcasting electronic commerce, and data processing, in the nation’s overall social
and economic development. The State also recognizes the importance of providing an
environment conducive to the development, acceleration, and rational application and
exploitation of information and communications technology (ICT) to attain free, easy, and
intelligible access to exchange and/or delivery of information; and the need to protect and
safeguard the integrity of computer, computer and communications systems, networks,](https://image.slidesharecdn.com/nsrcyber5-130519204802-phpapp02/75/National-Security-Review-147-2048.jpg)


































































