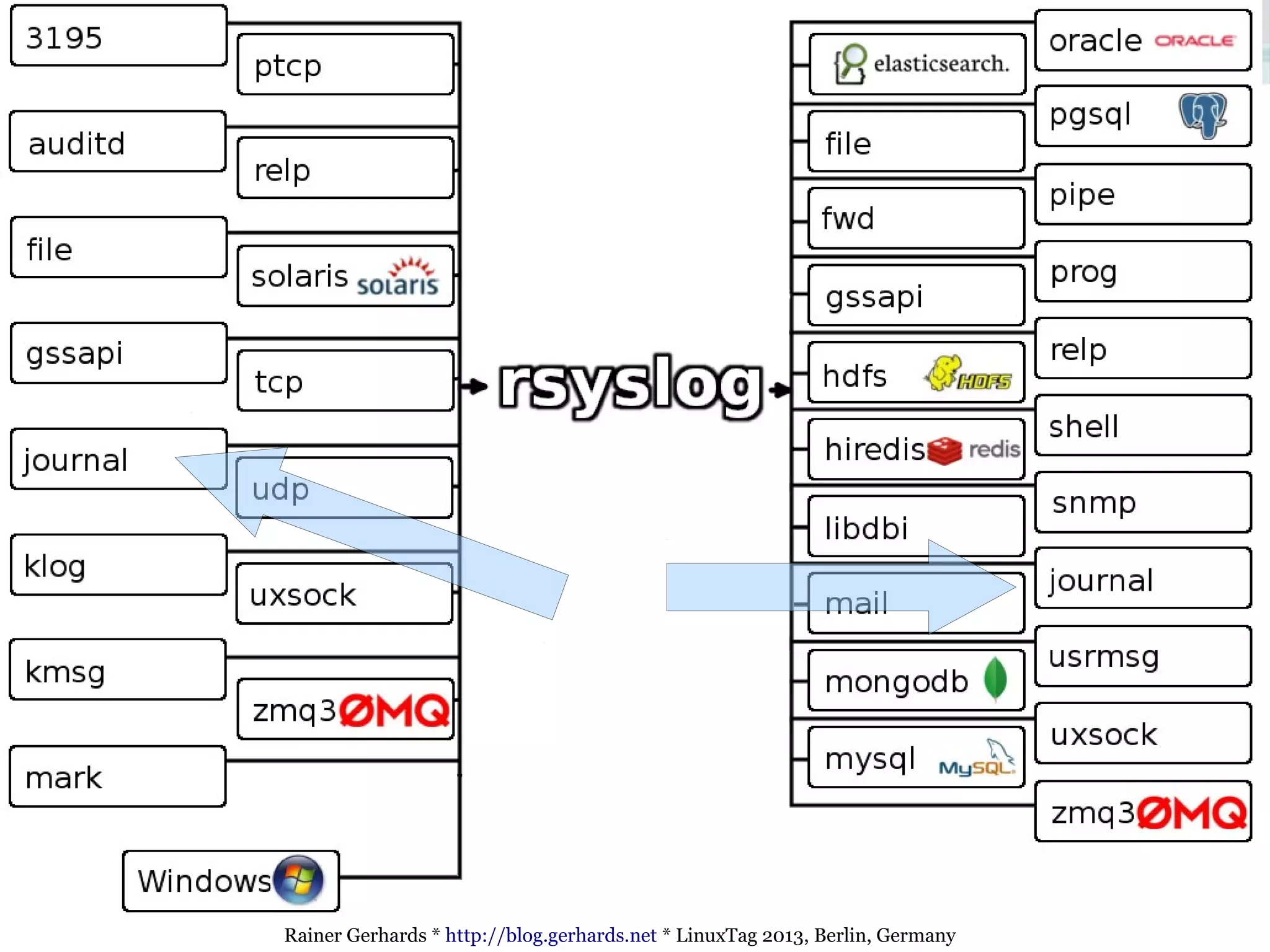
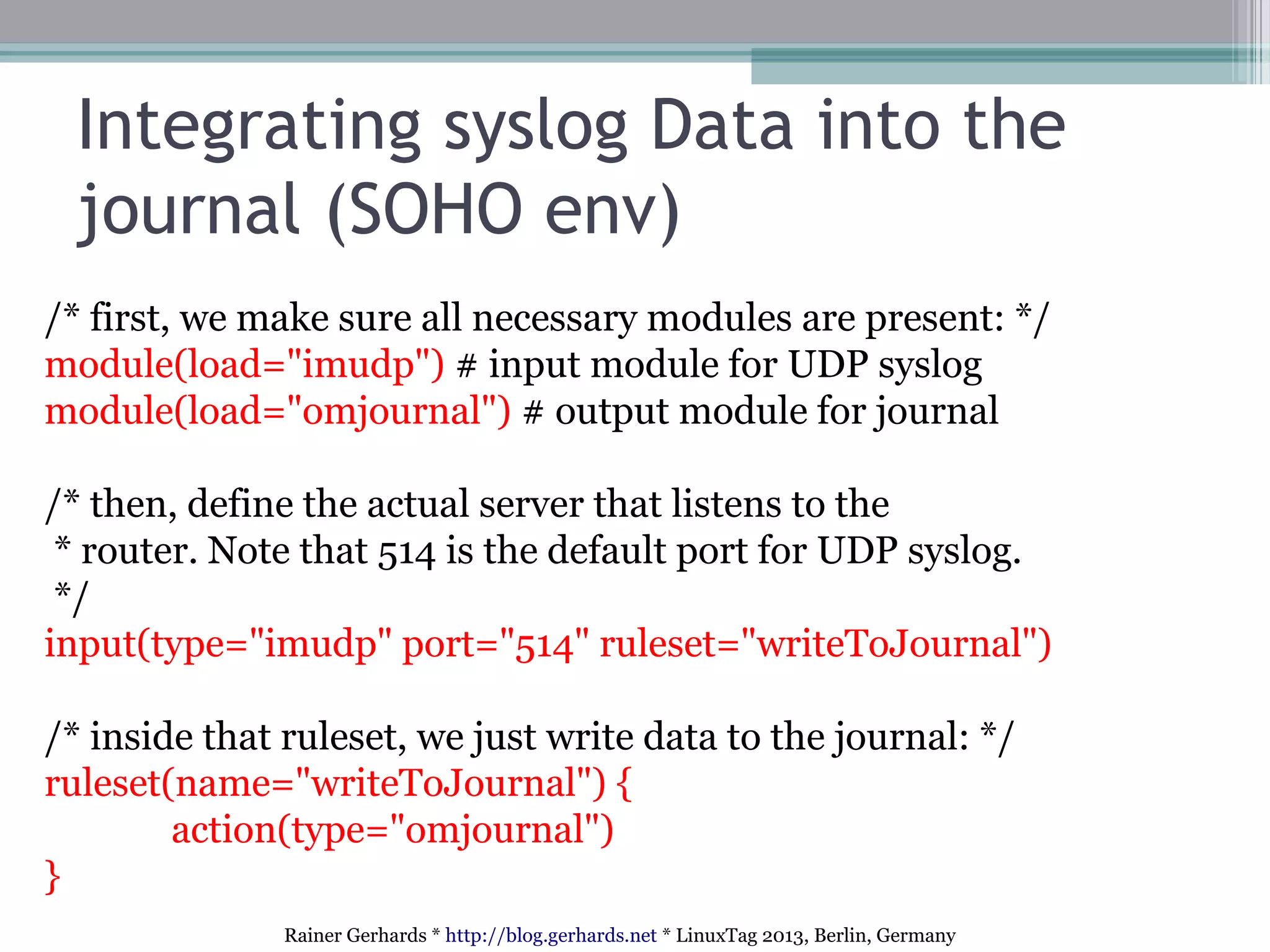
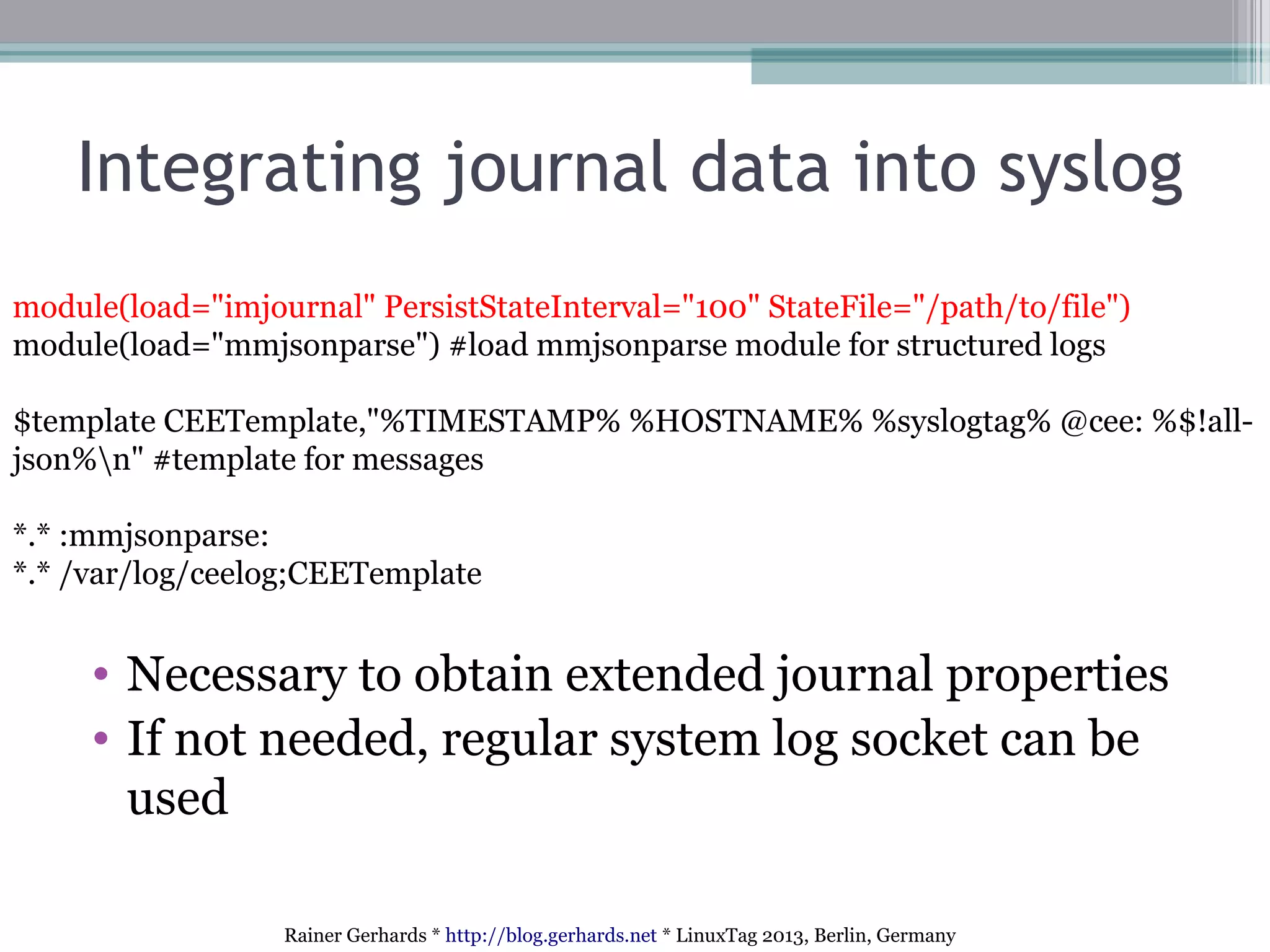
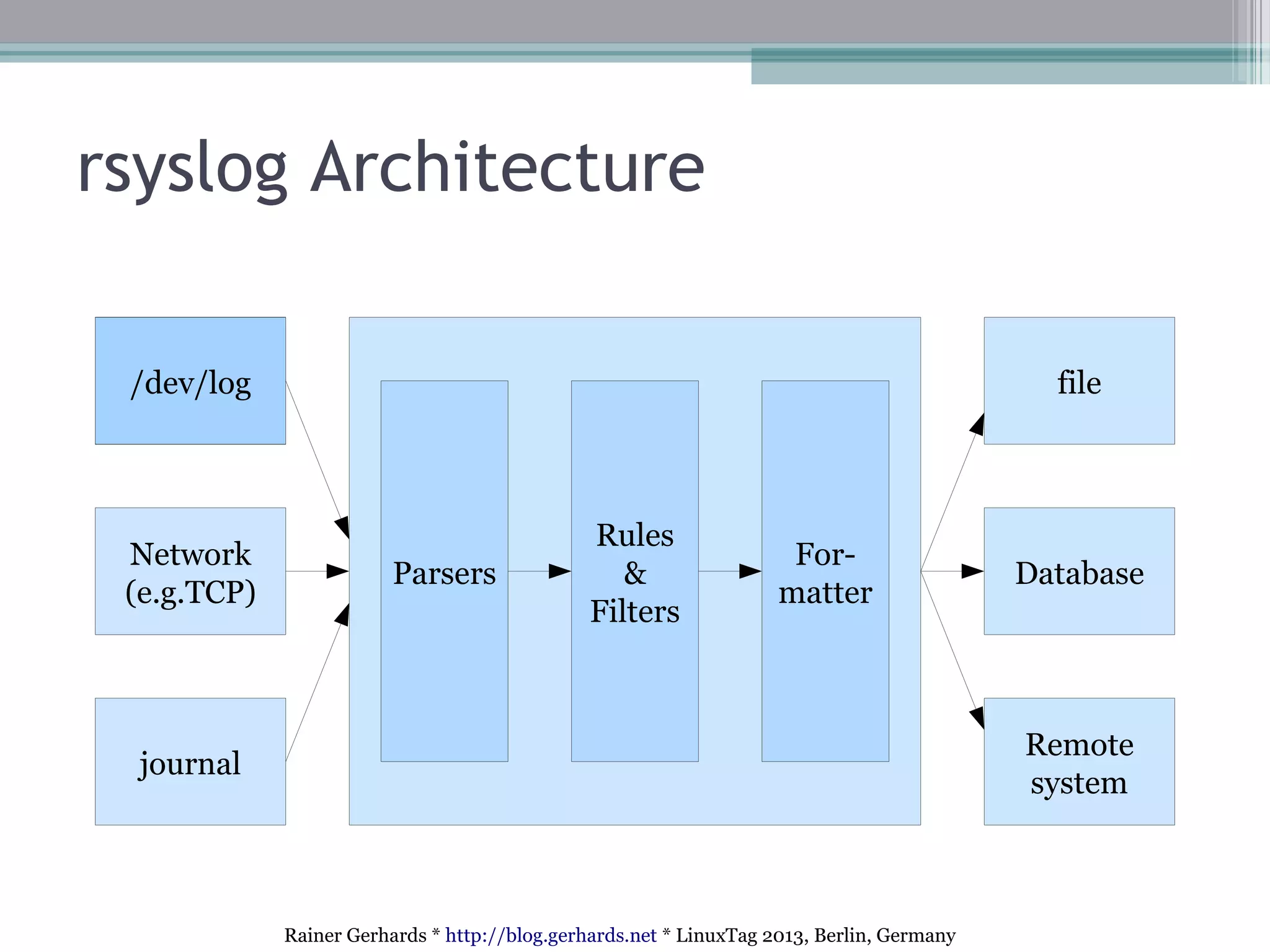
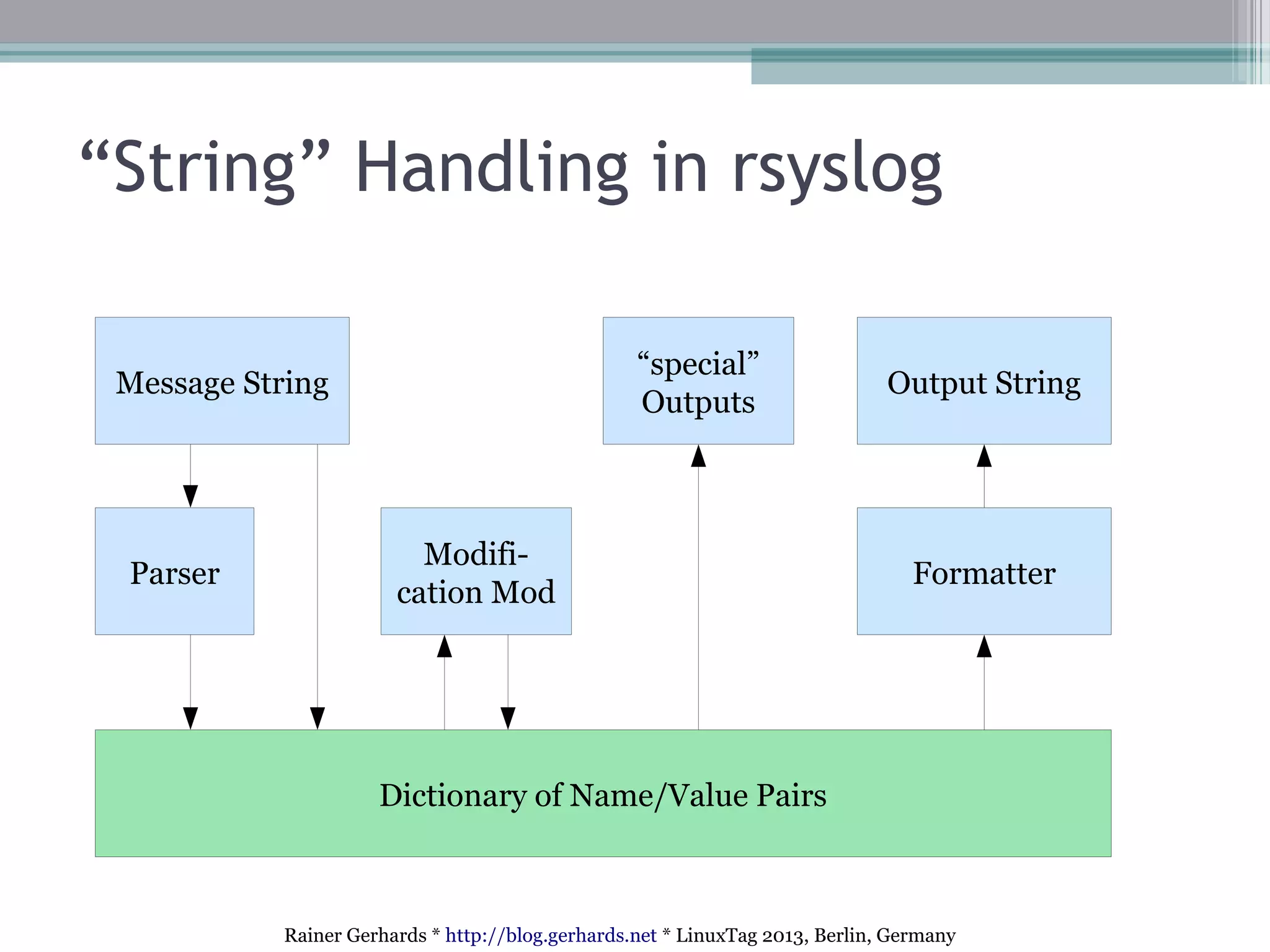
The document discusses the comparison and integration of rsyslog and systemd journal, highlighting their similarities and differences. It emphasizes that while journals offer certain conveniences, especially for troubleshooting, rsyslog remains essential for network event logging and integration across heterogeneous systems. The talk also outlines technical advances in rsyslog, such as improved security features, flexible integration options, and handling of various log formats.