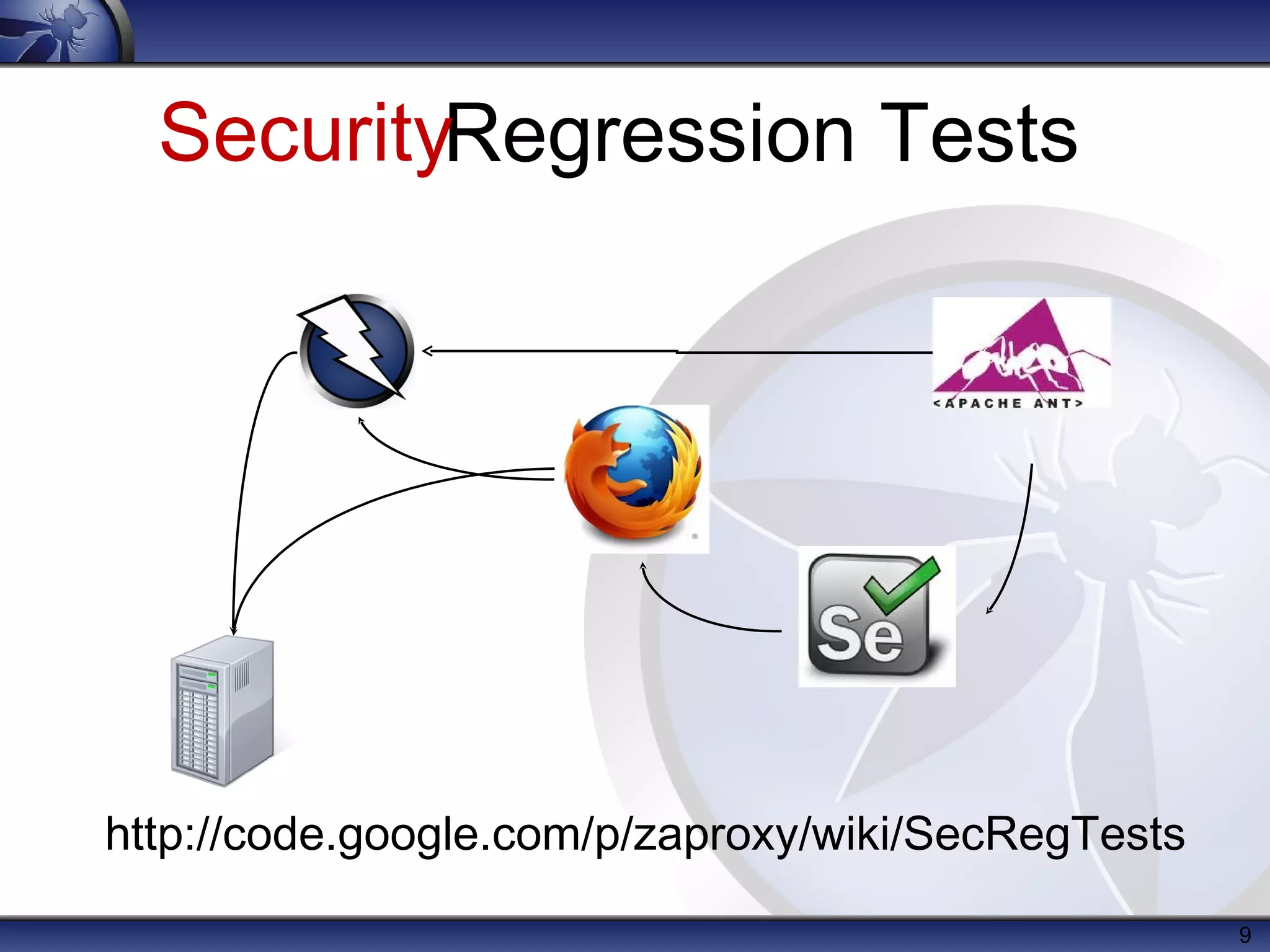
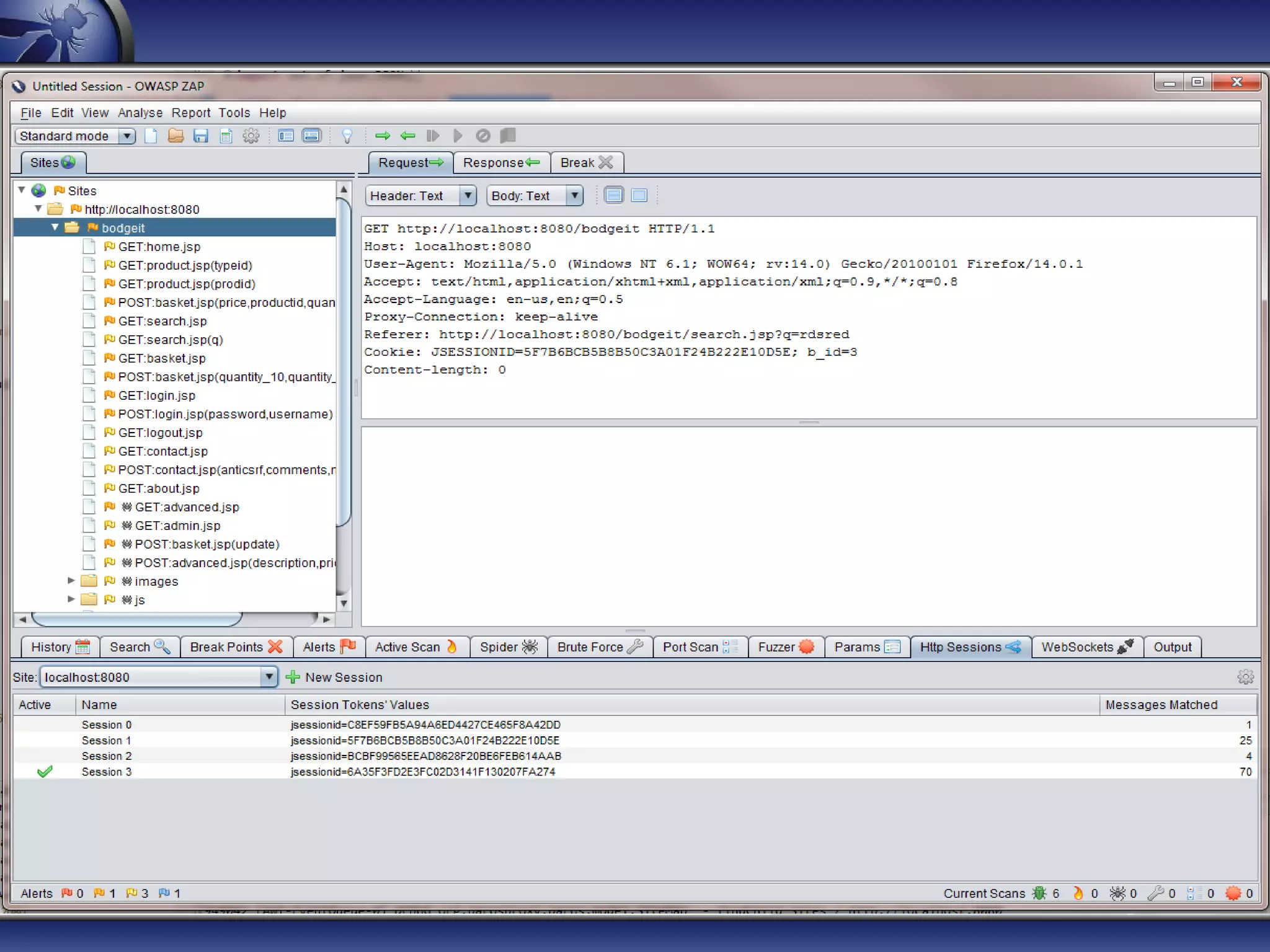
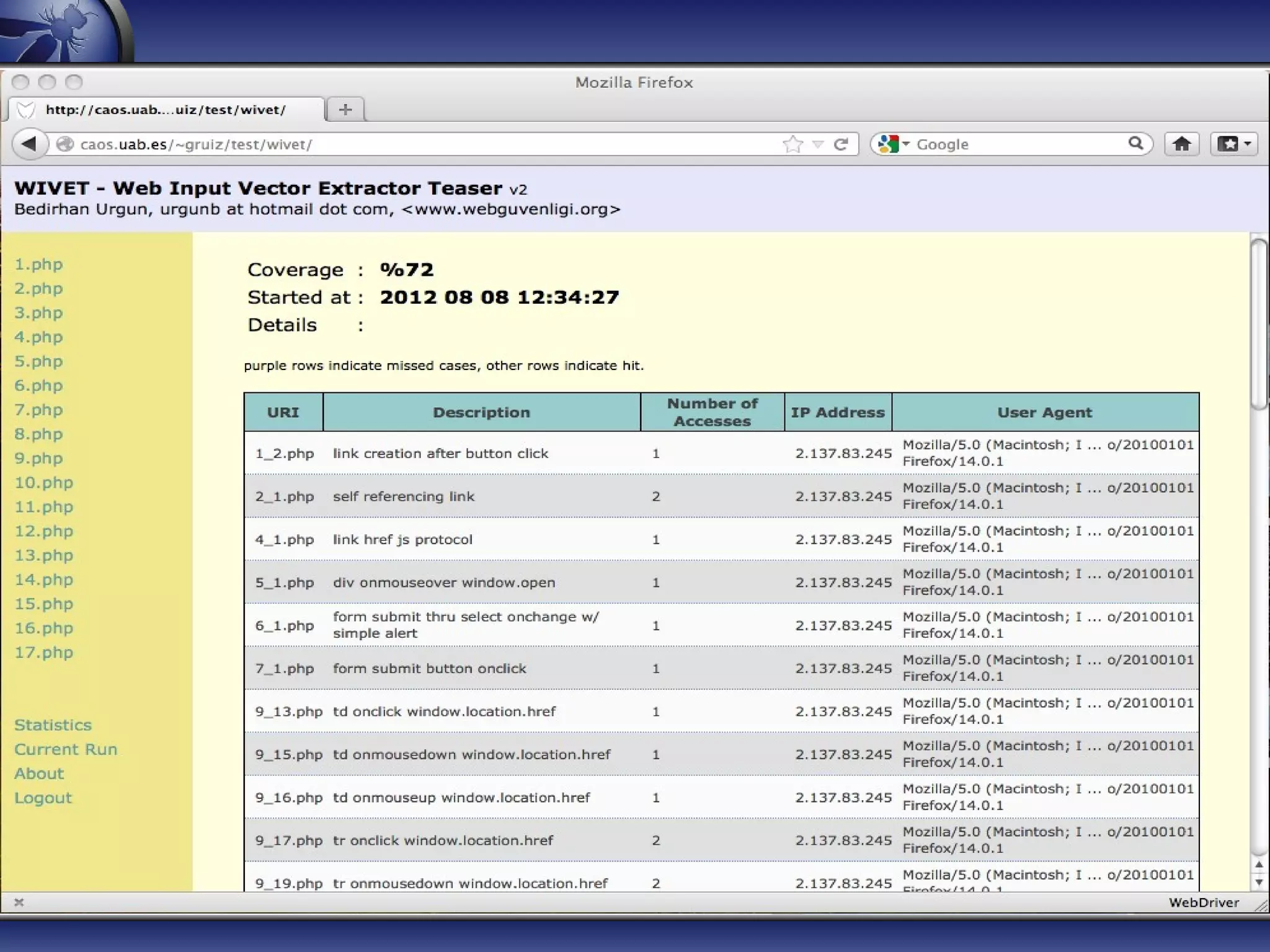
The document provides an introduction to OWASP ZAP, a free and open-source web application penetration testing tool ideal for both beginners and professionals. It outlines the tool's main features, such as an intercepting proxy, scanners, and extensibility, along with details on its development, usage statistics, and collaborations. Additionally, it highlights the upcoming features in version 2.0, including enhanced scanning capabilities and new session management functionalities.