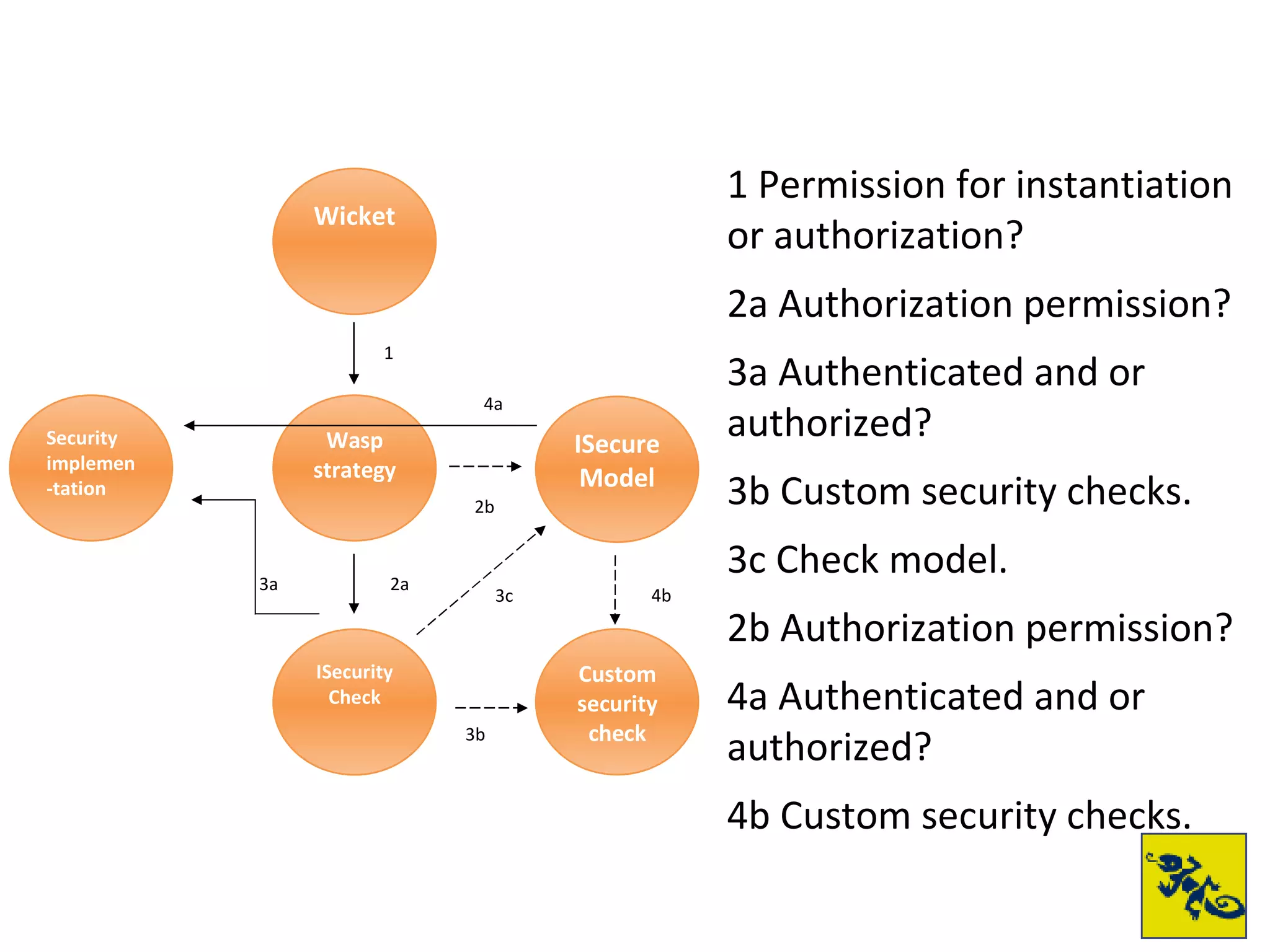
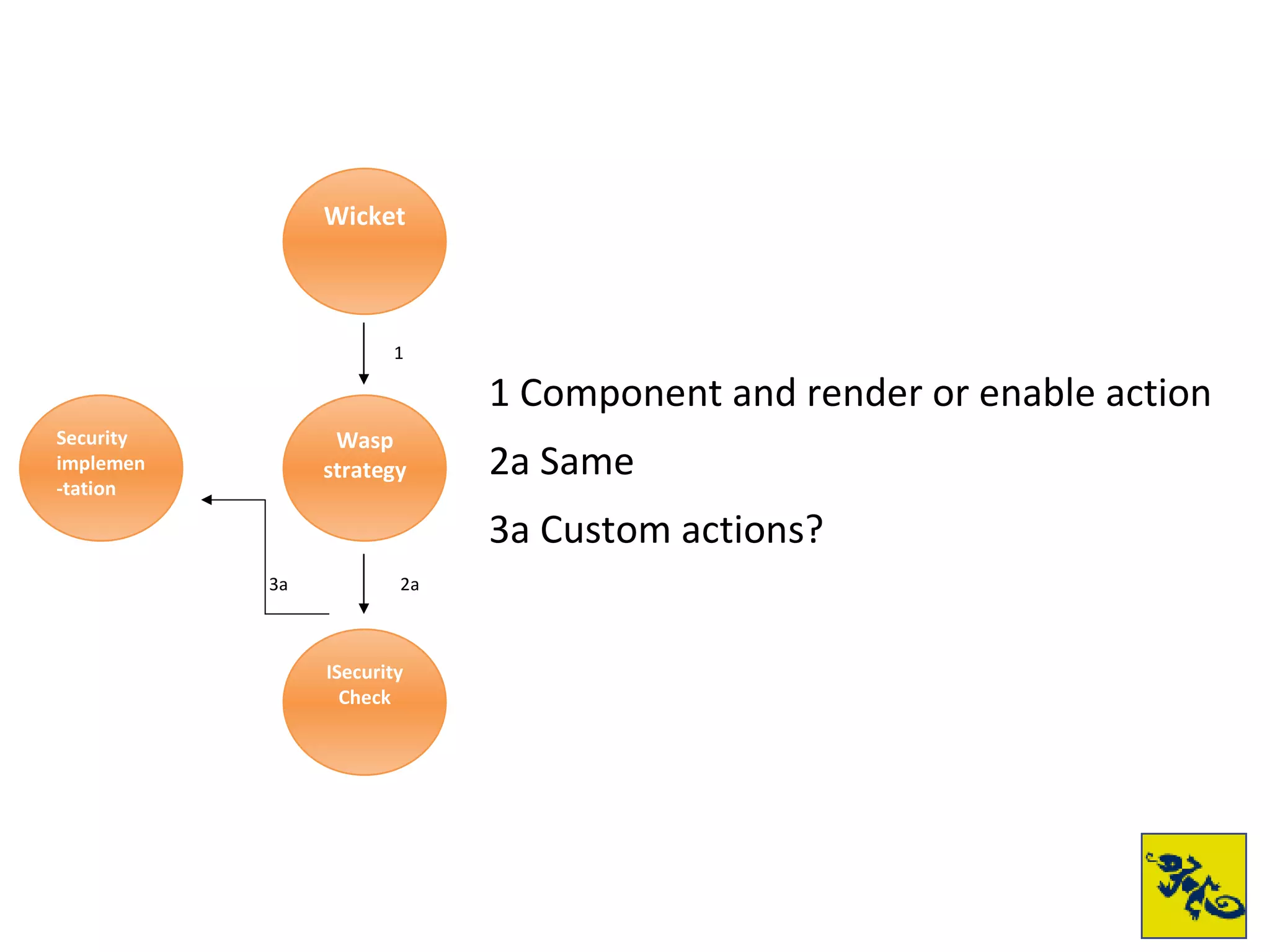
- Wicket Security Wasp & Swarm is a framework for adding authentication and authorization to Wicket applications. It provides flexible security models and permission checking.
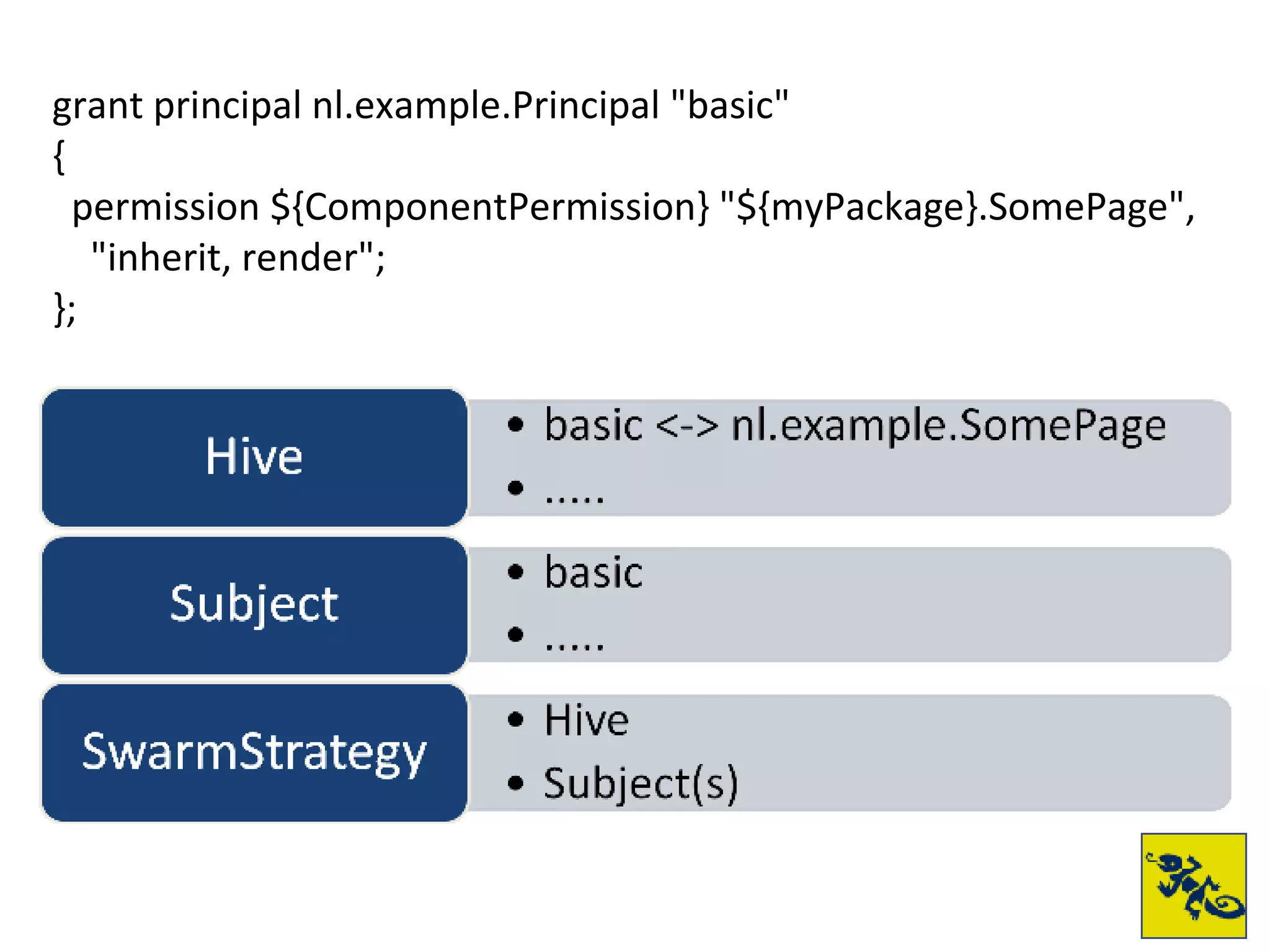
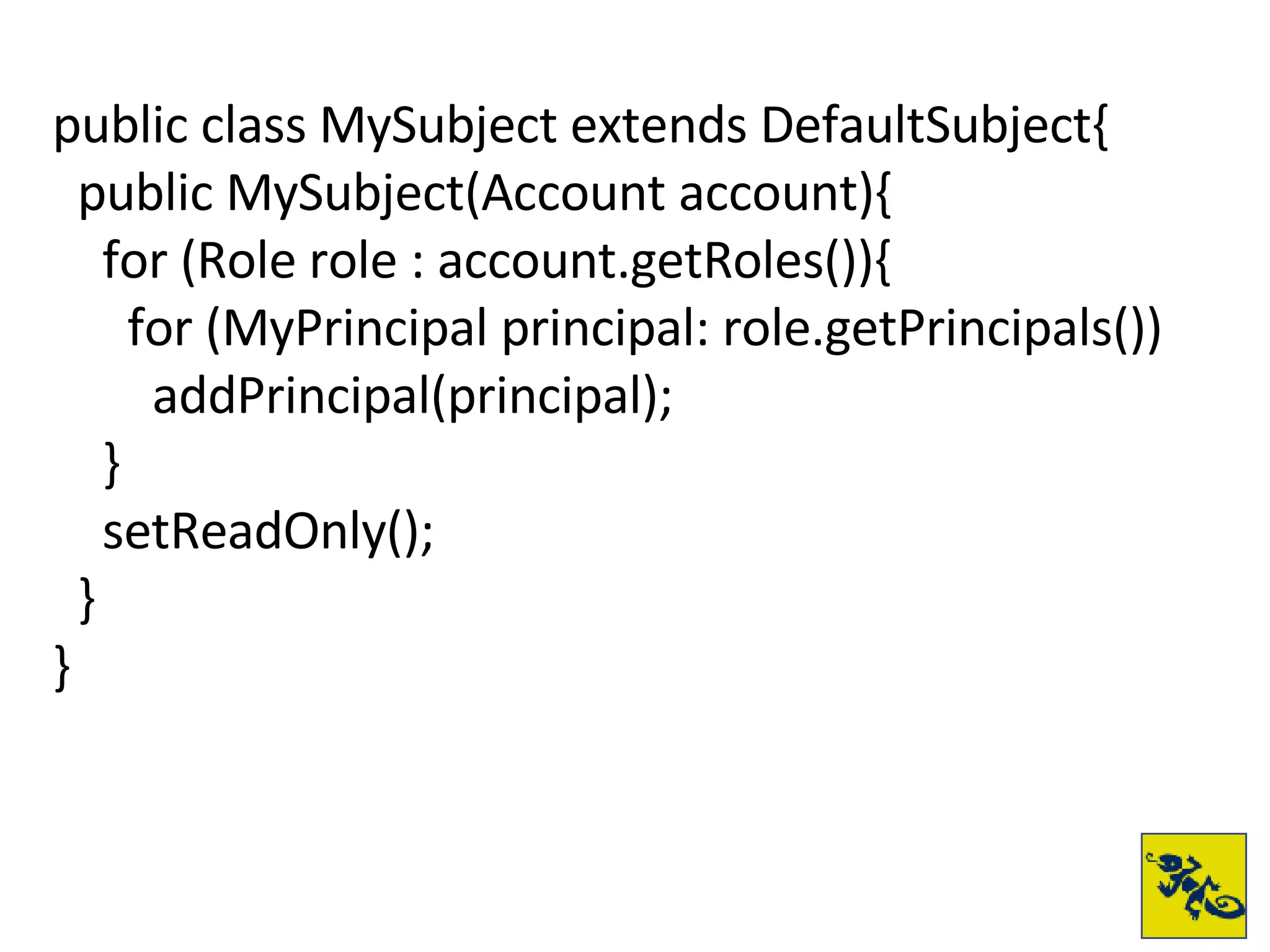
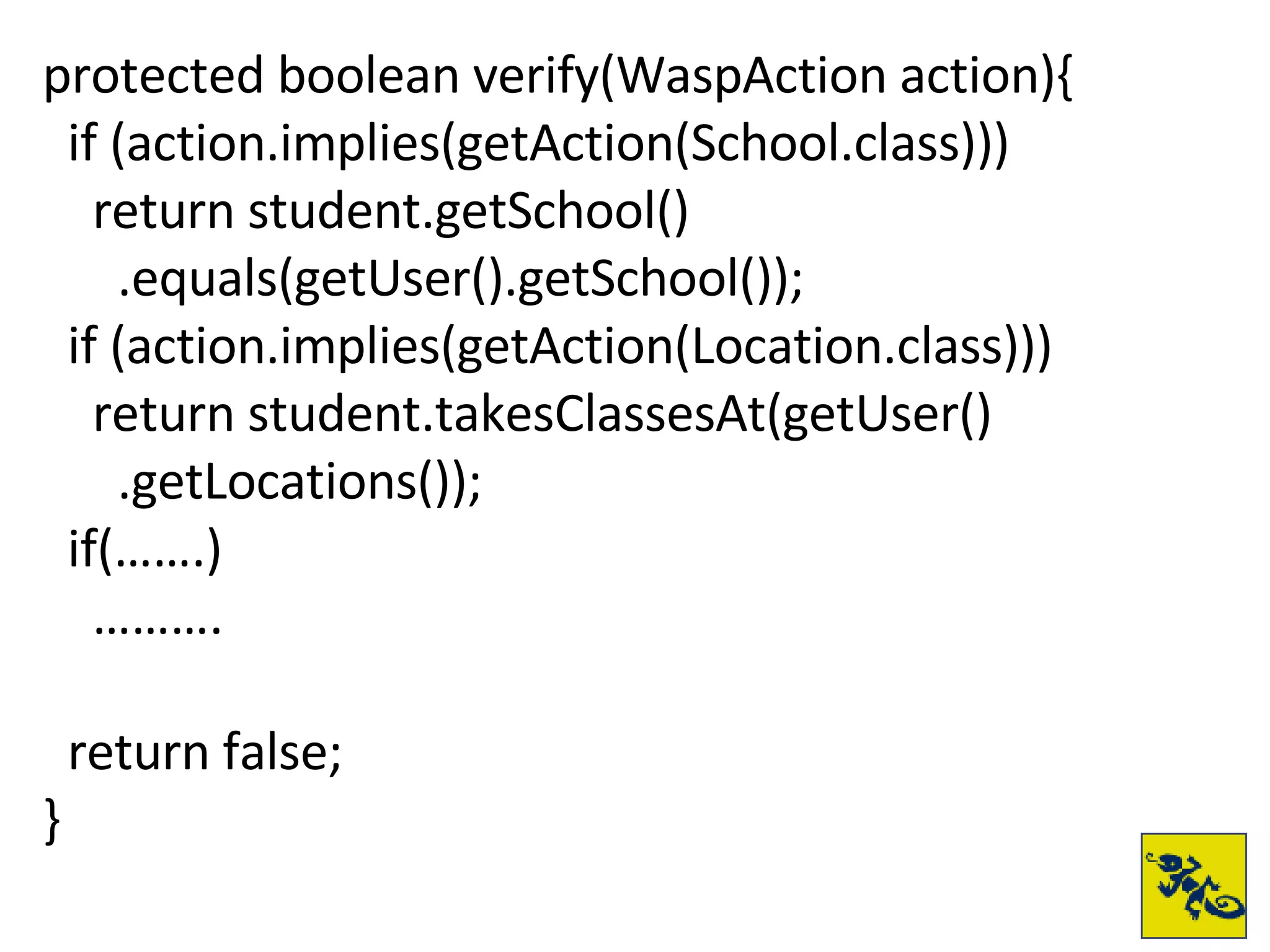
- Swarm builds on Wasp and provides standard authentication and role-based access control. It uses a HiveMind-based policy system for defining permissions.
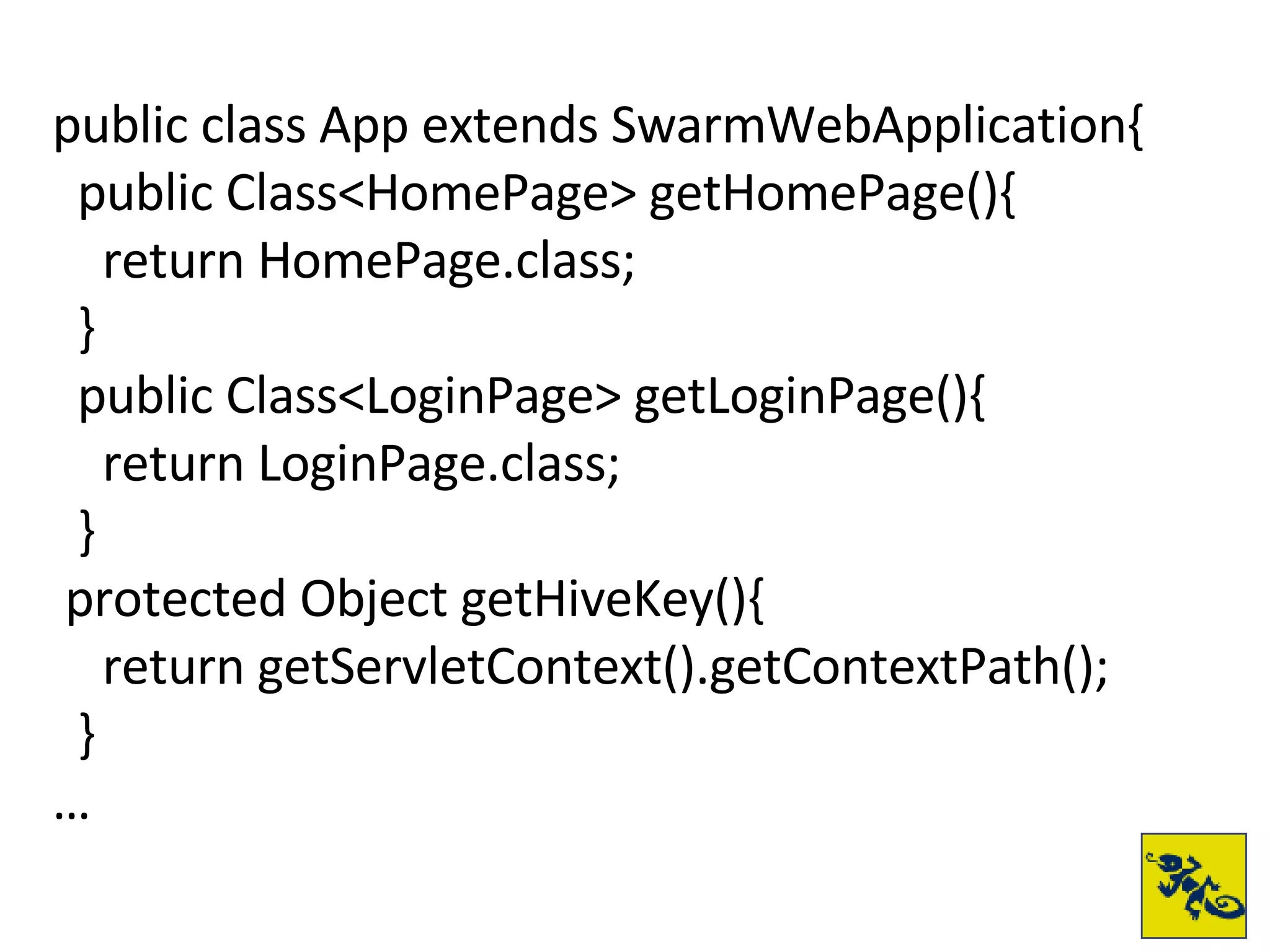
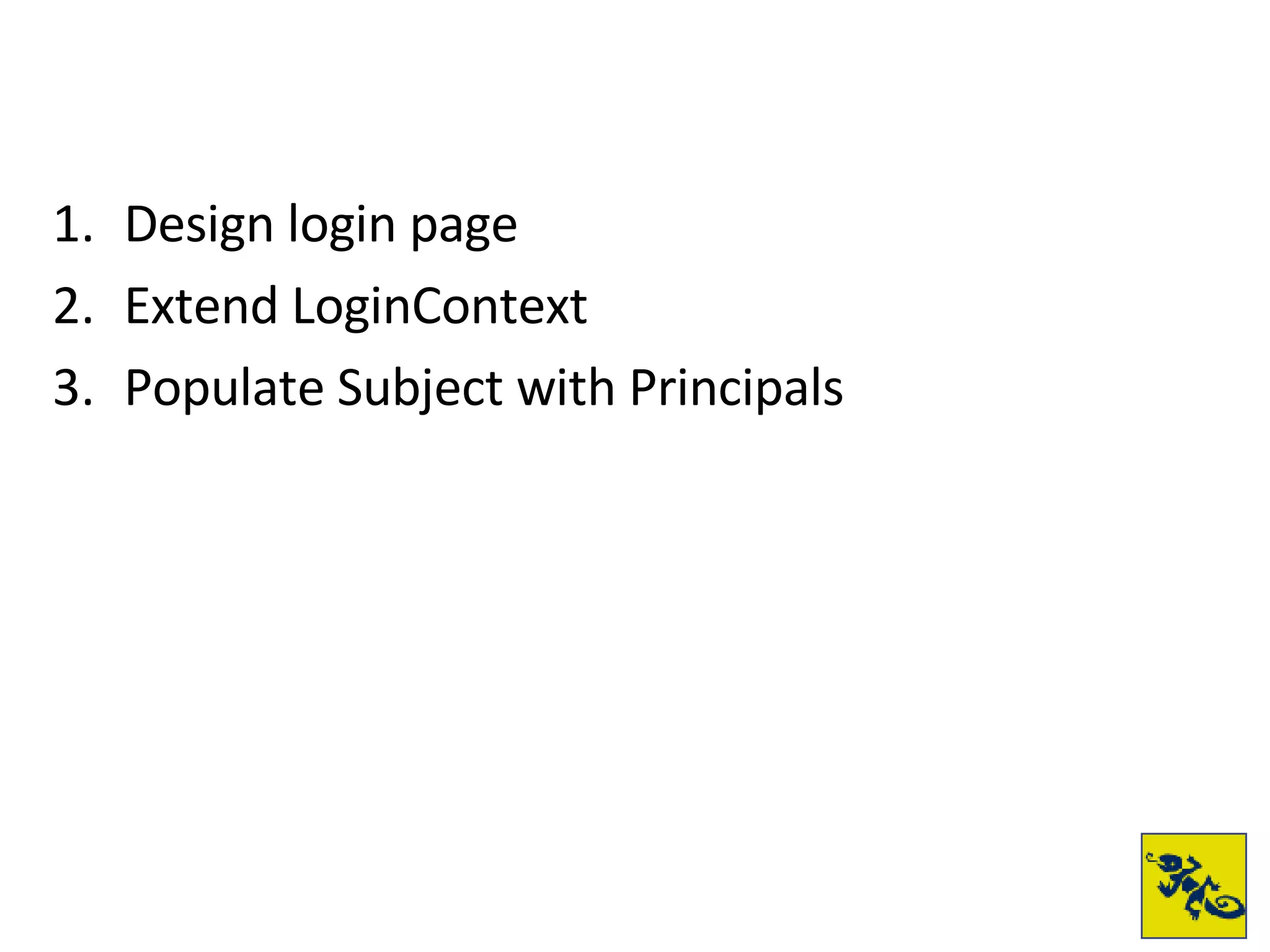
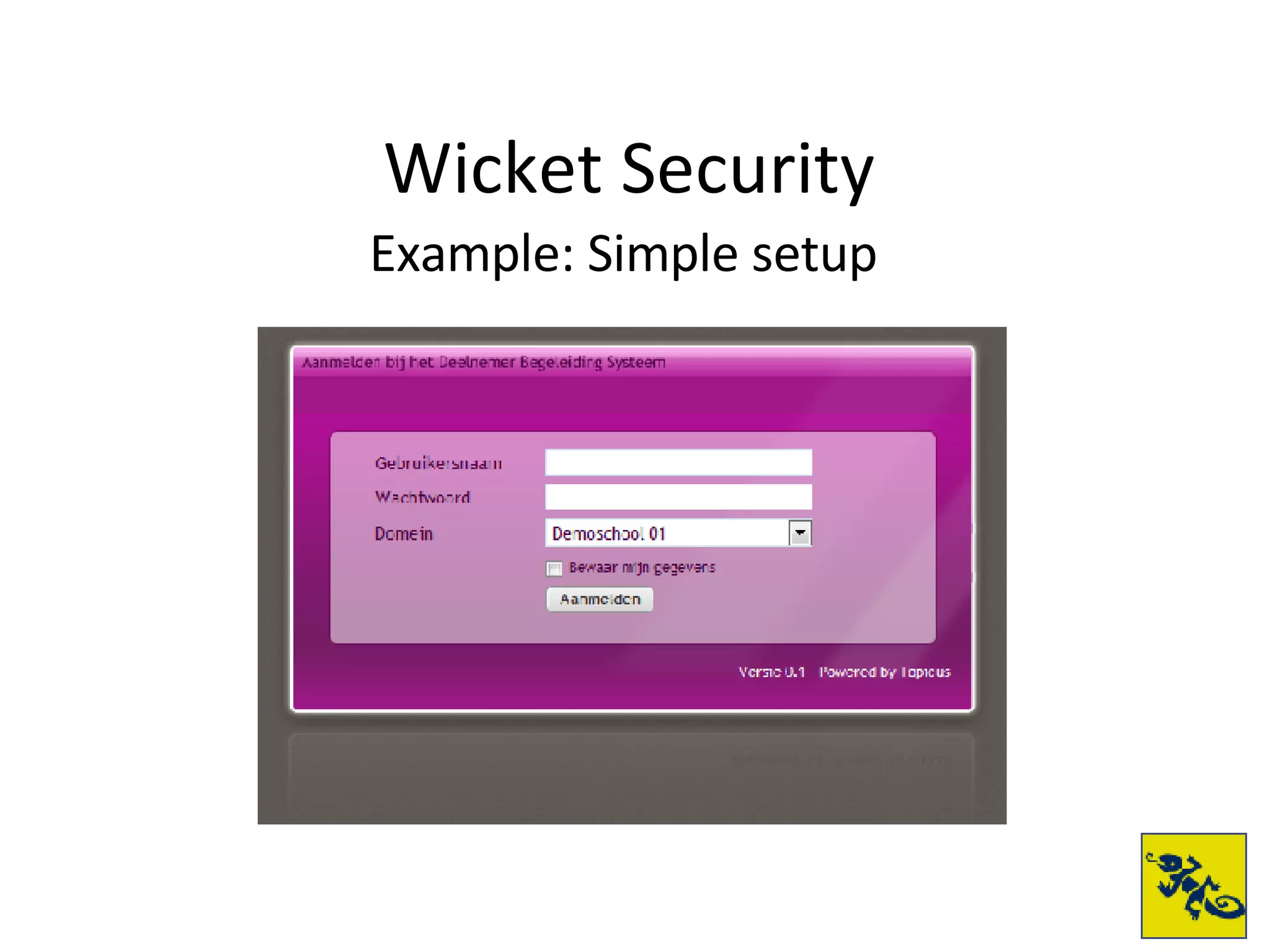
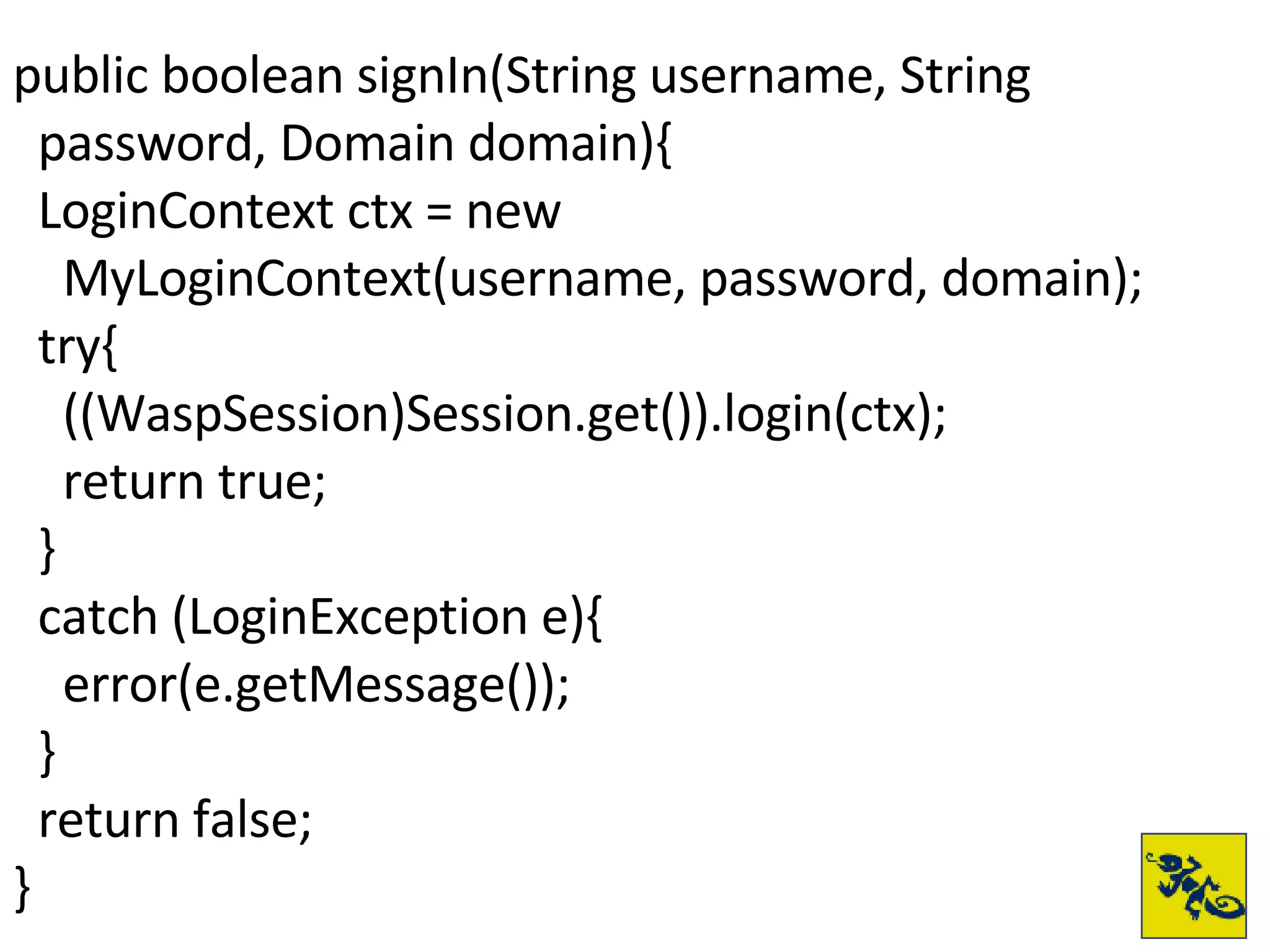
- The document provides examples of setting up a basic secure Wicket application using Swarm, defining principals and policies, and implementing authentication and authorization checks.