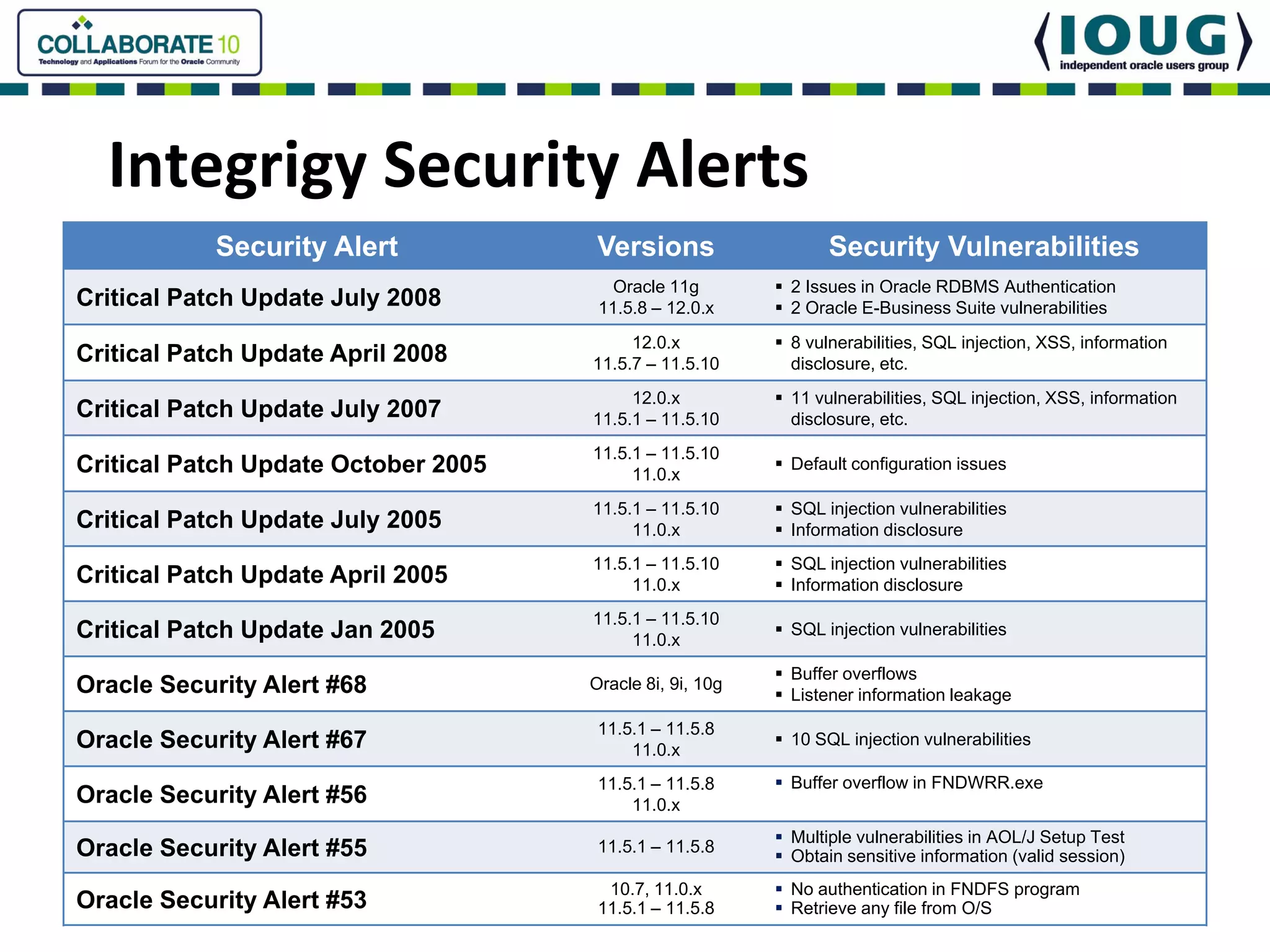
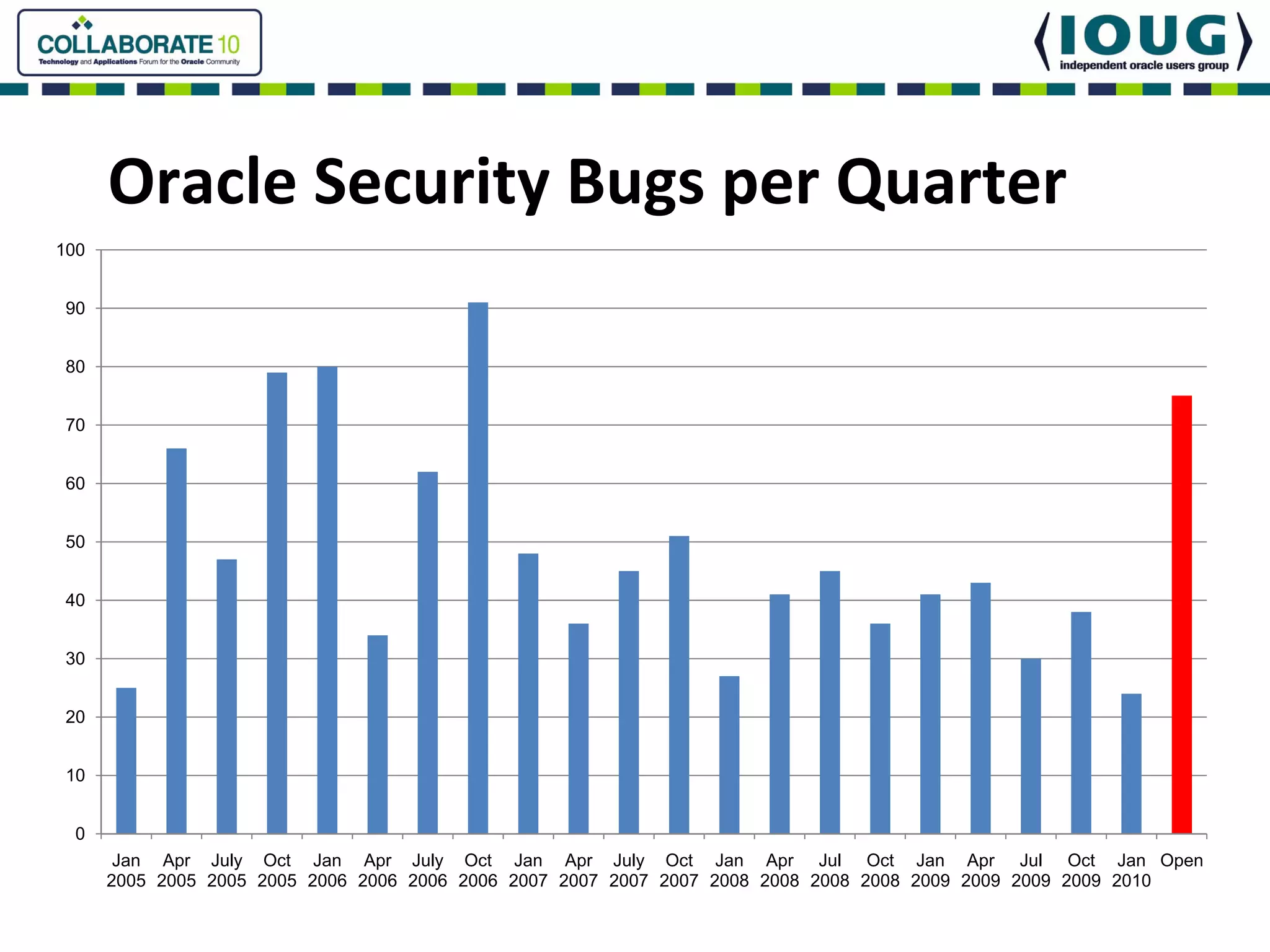
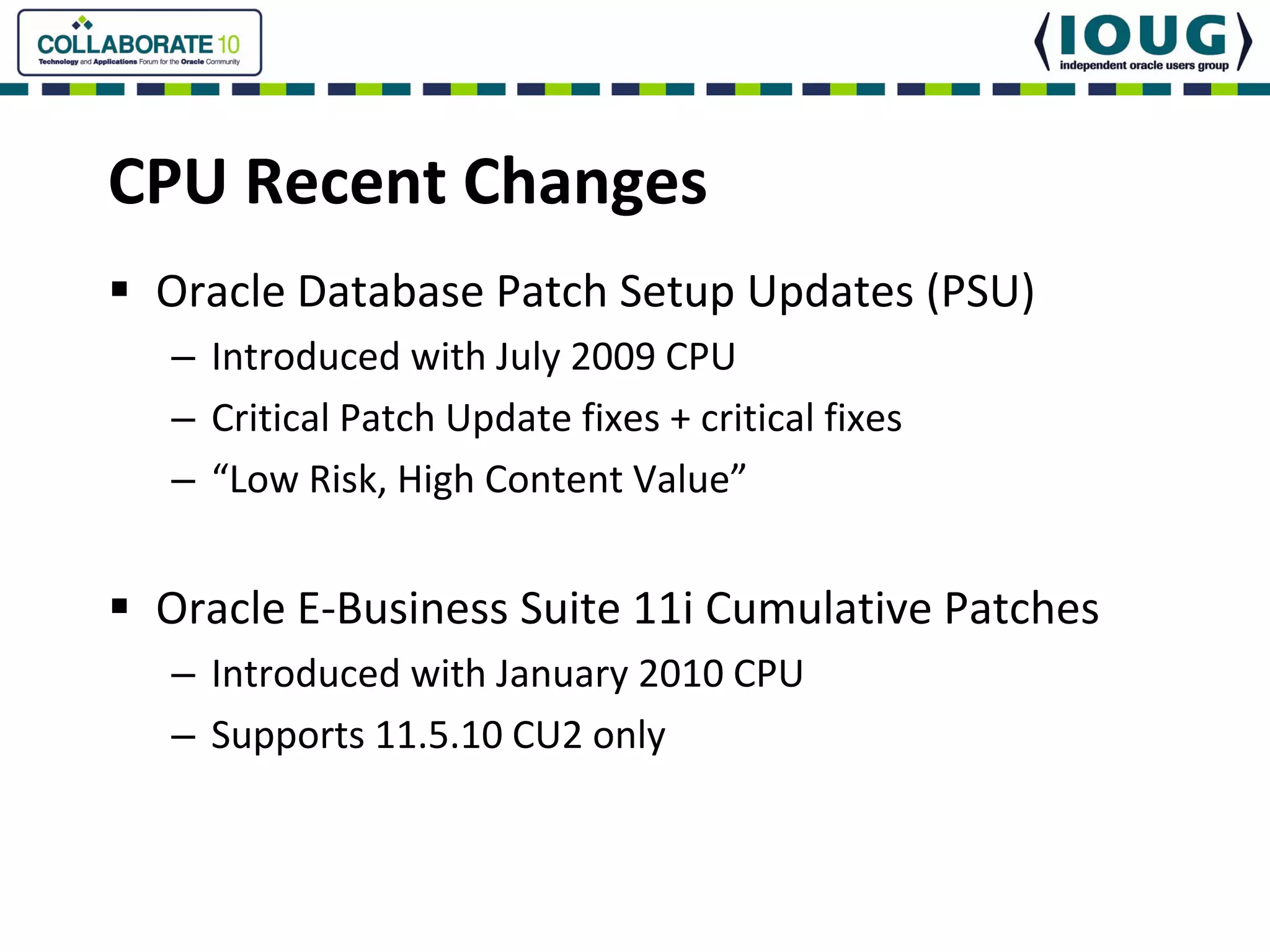
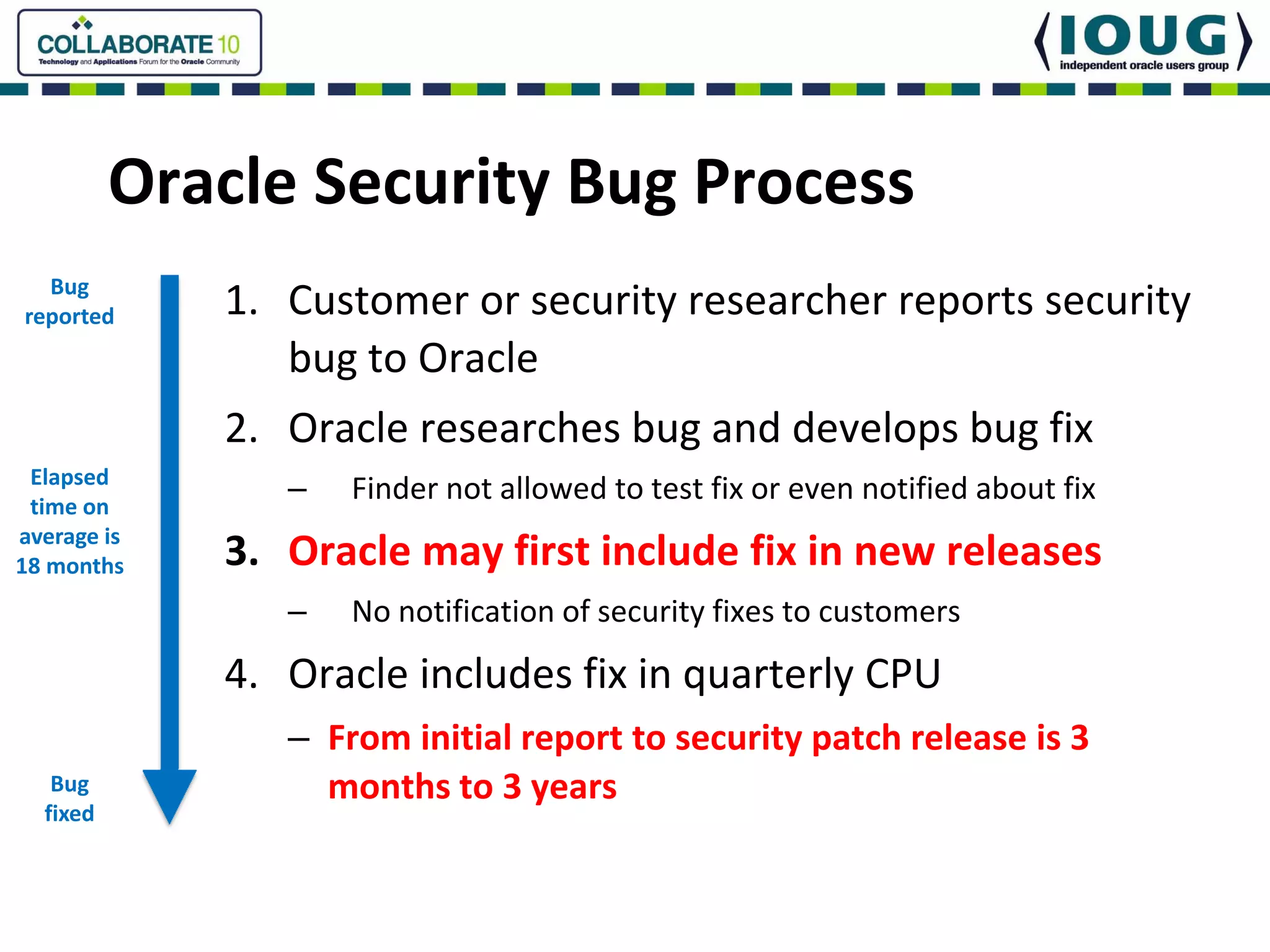
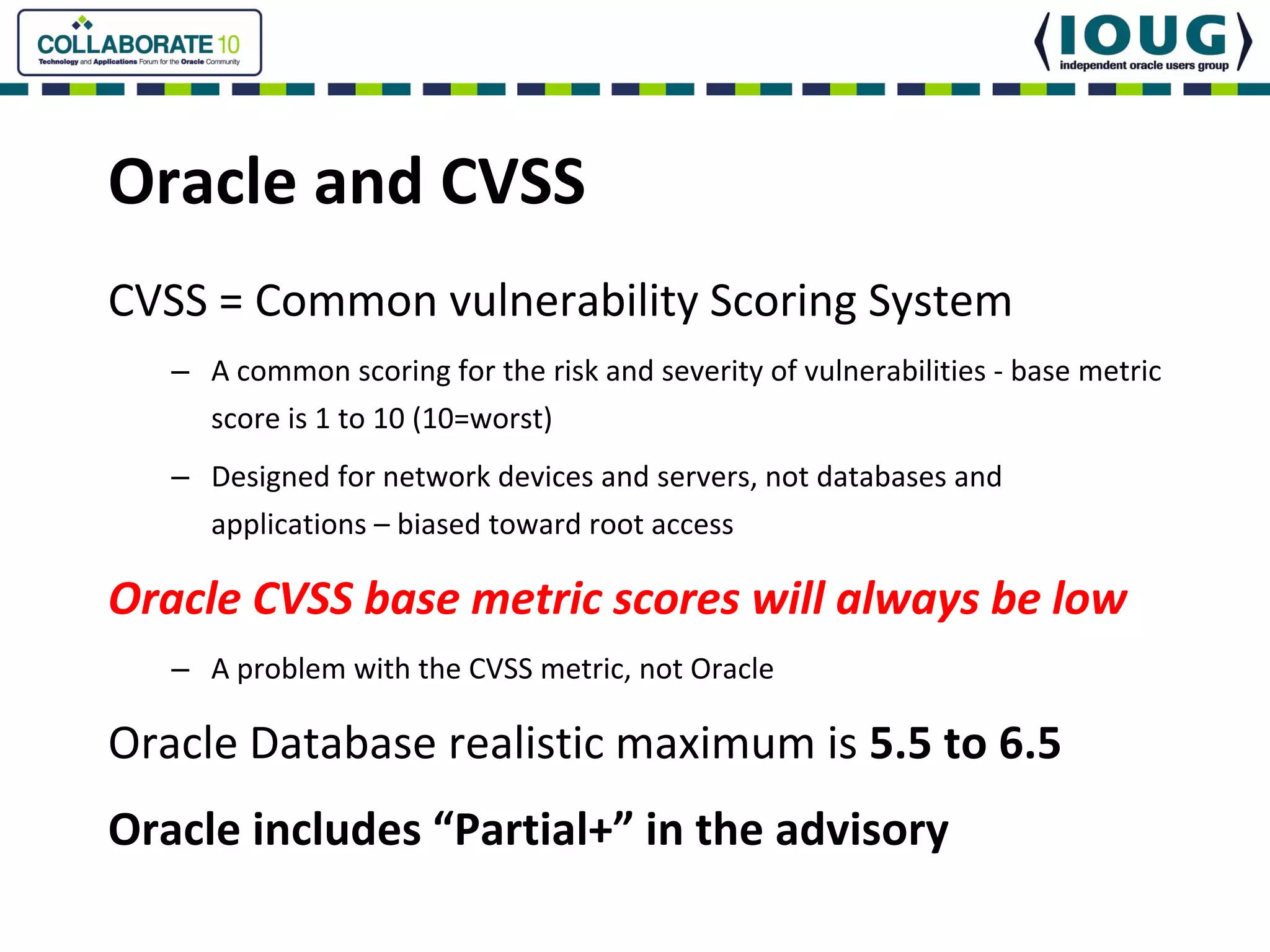
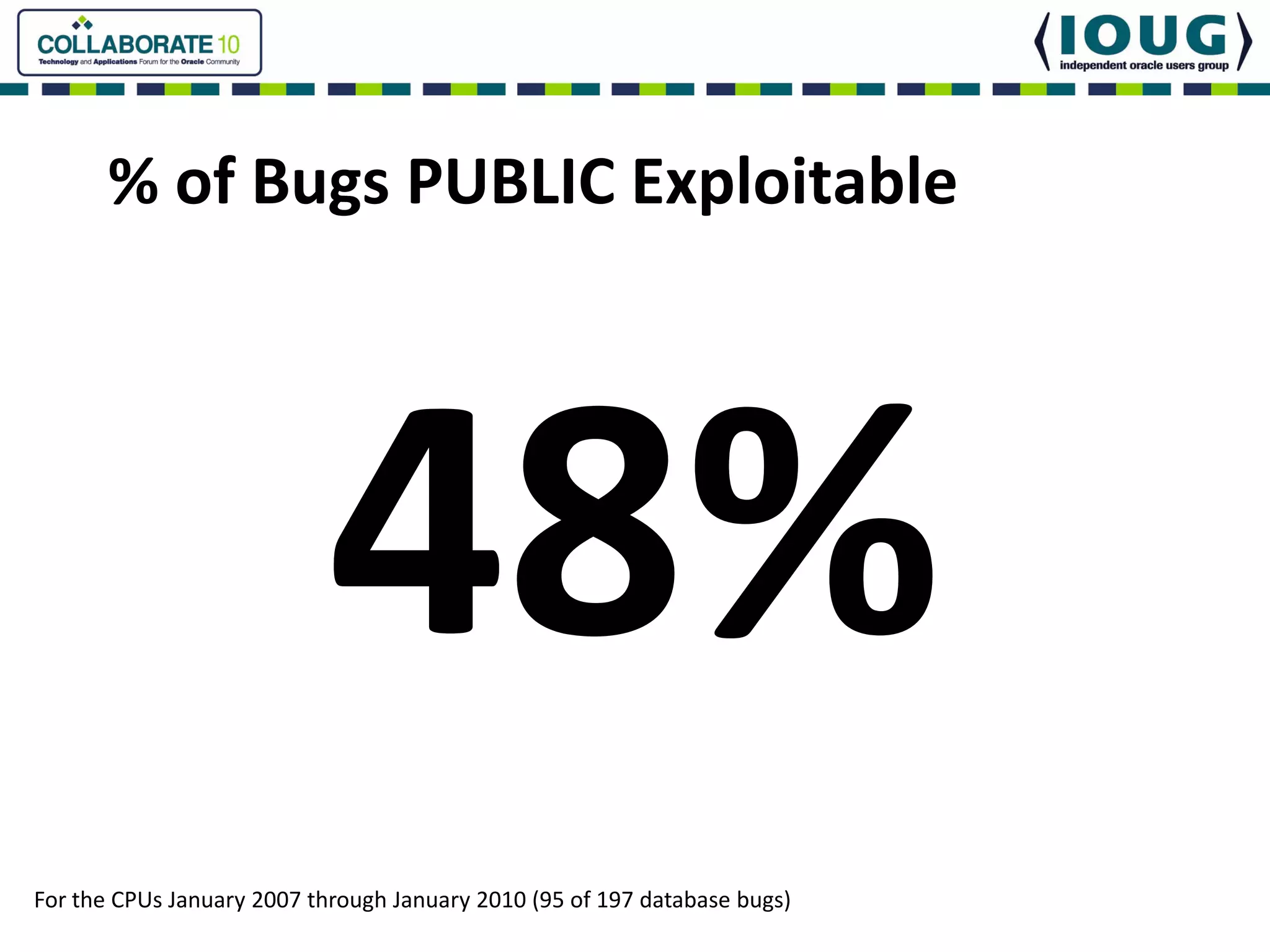
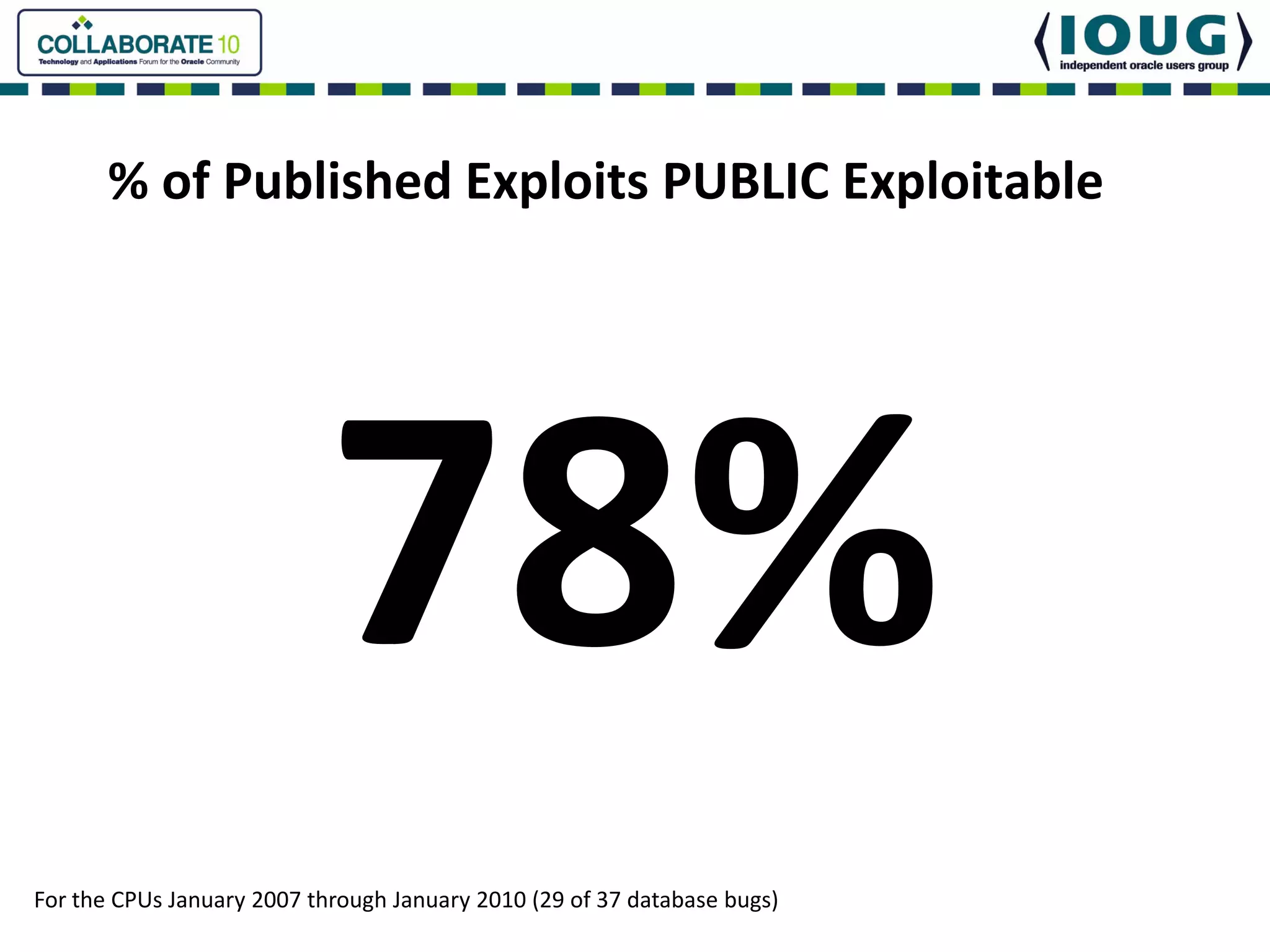
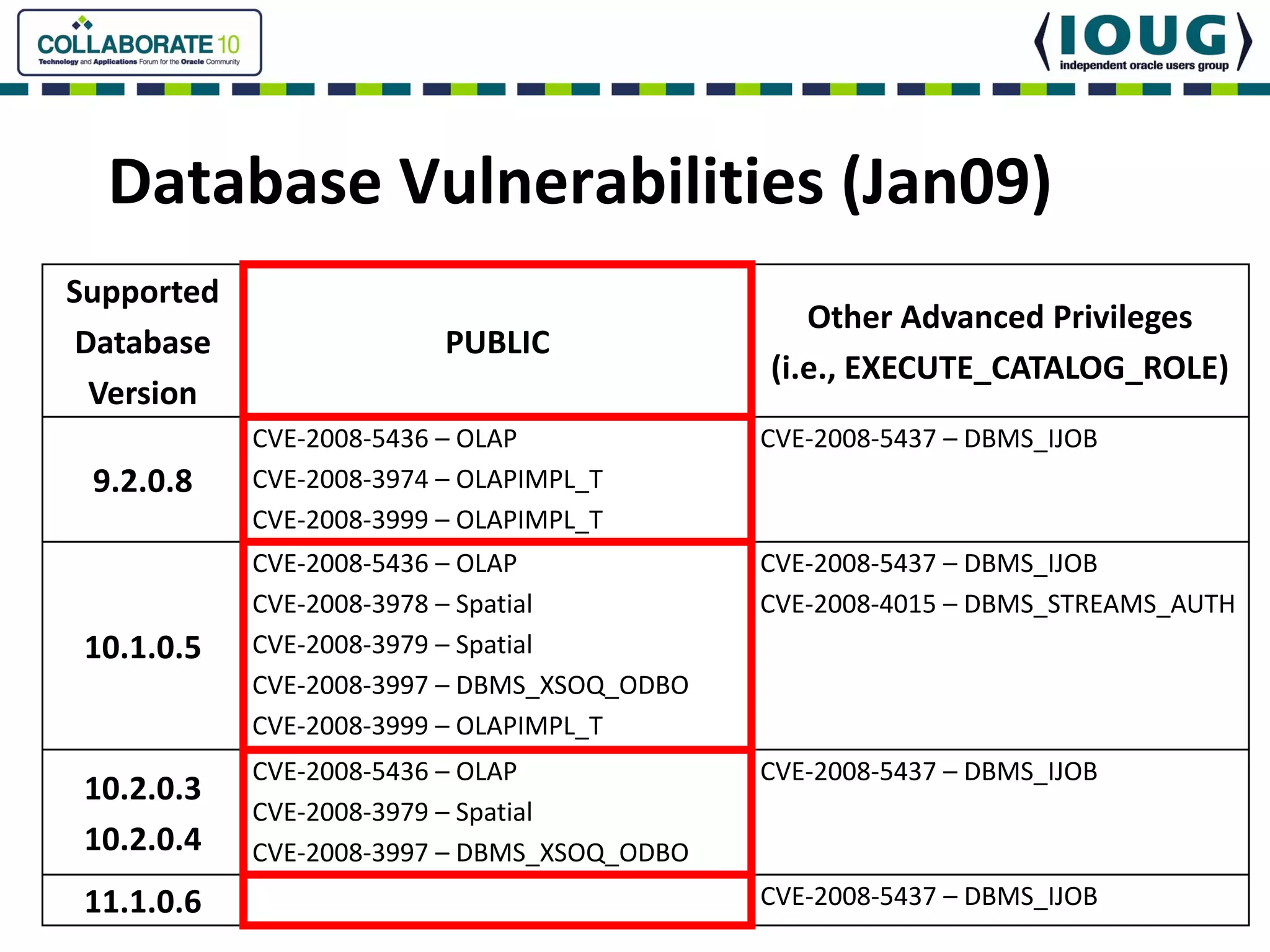
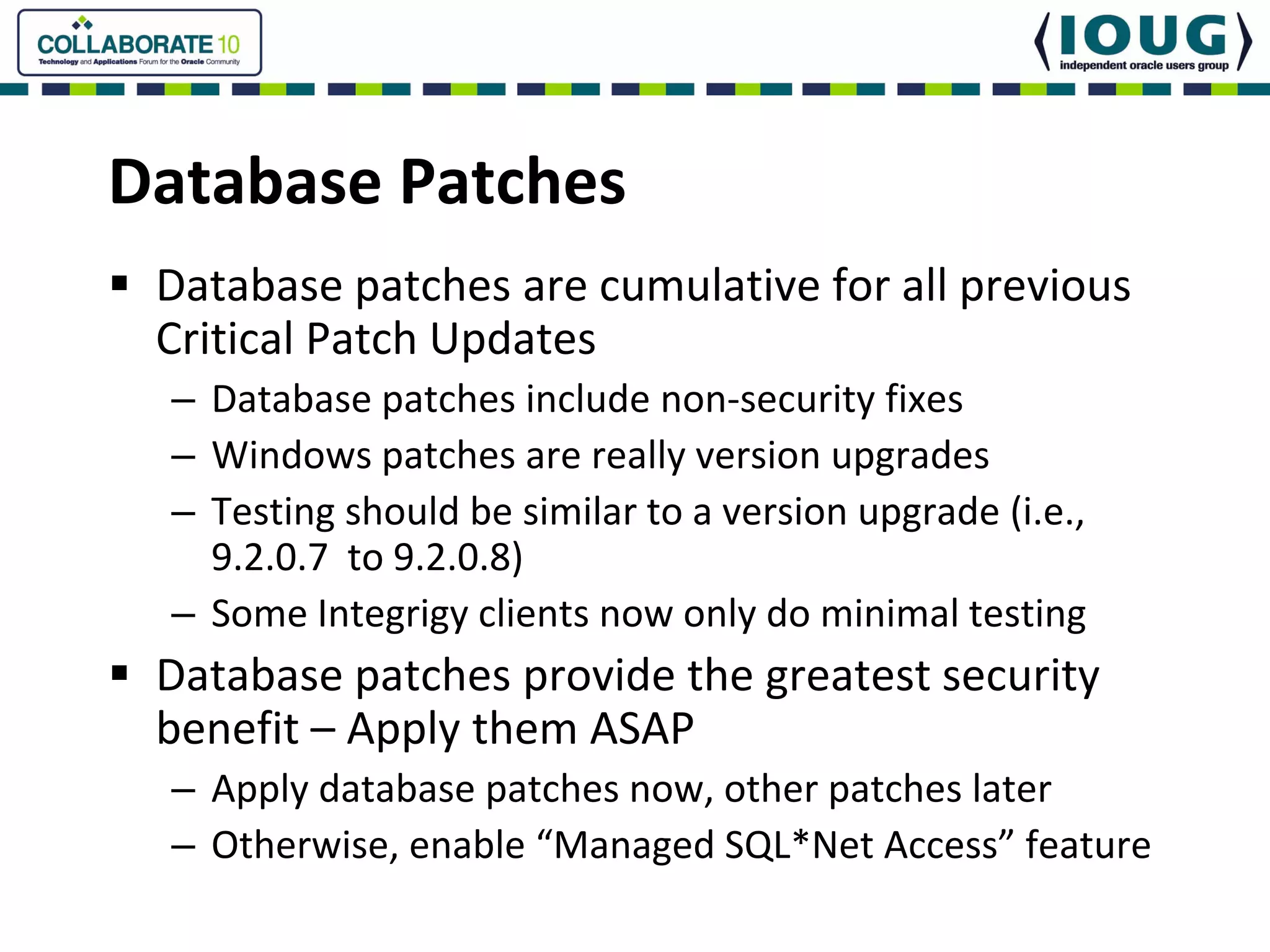
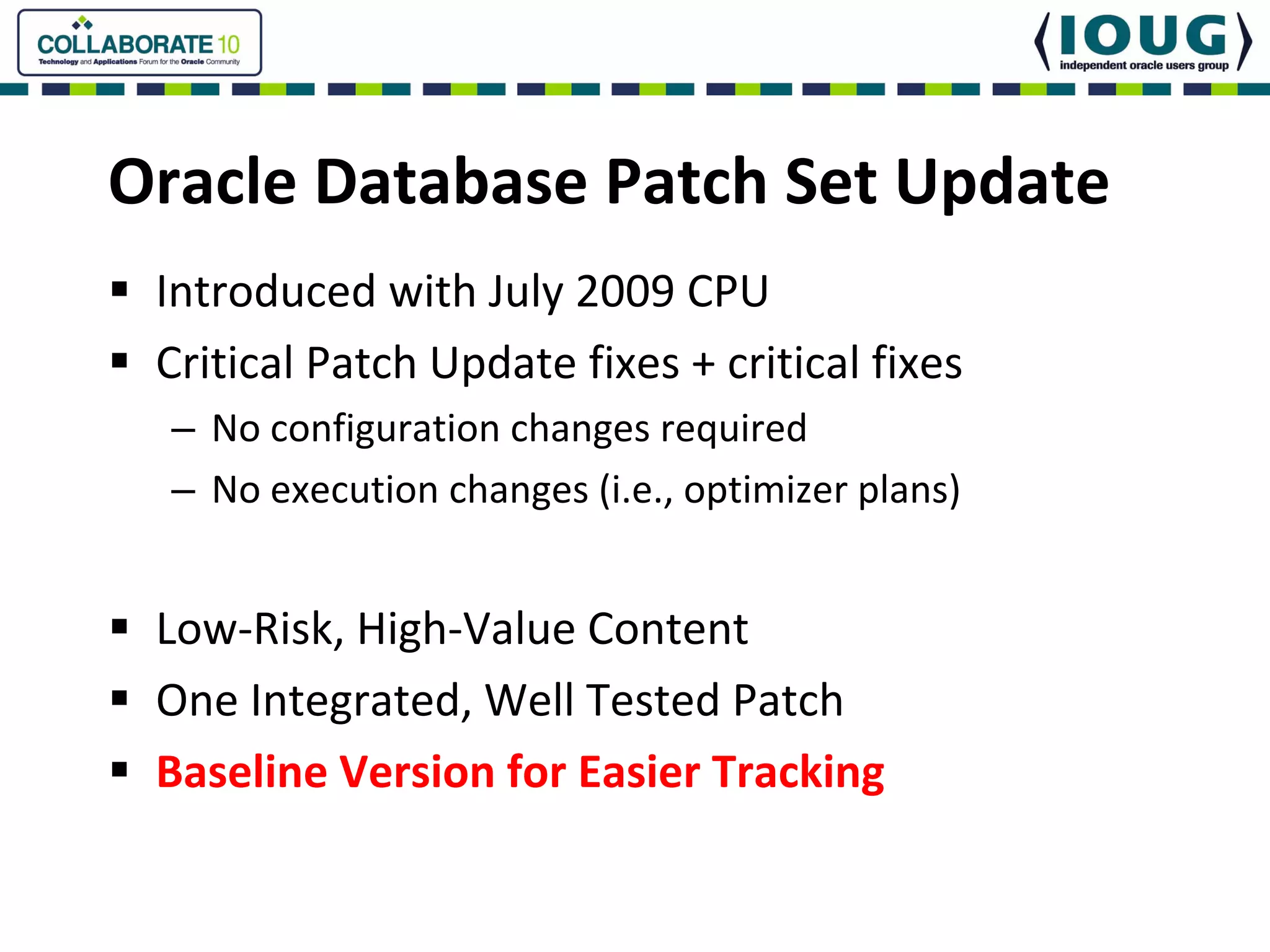
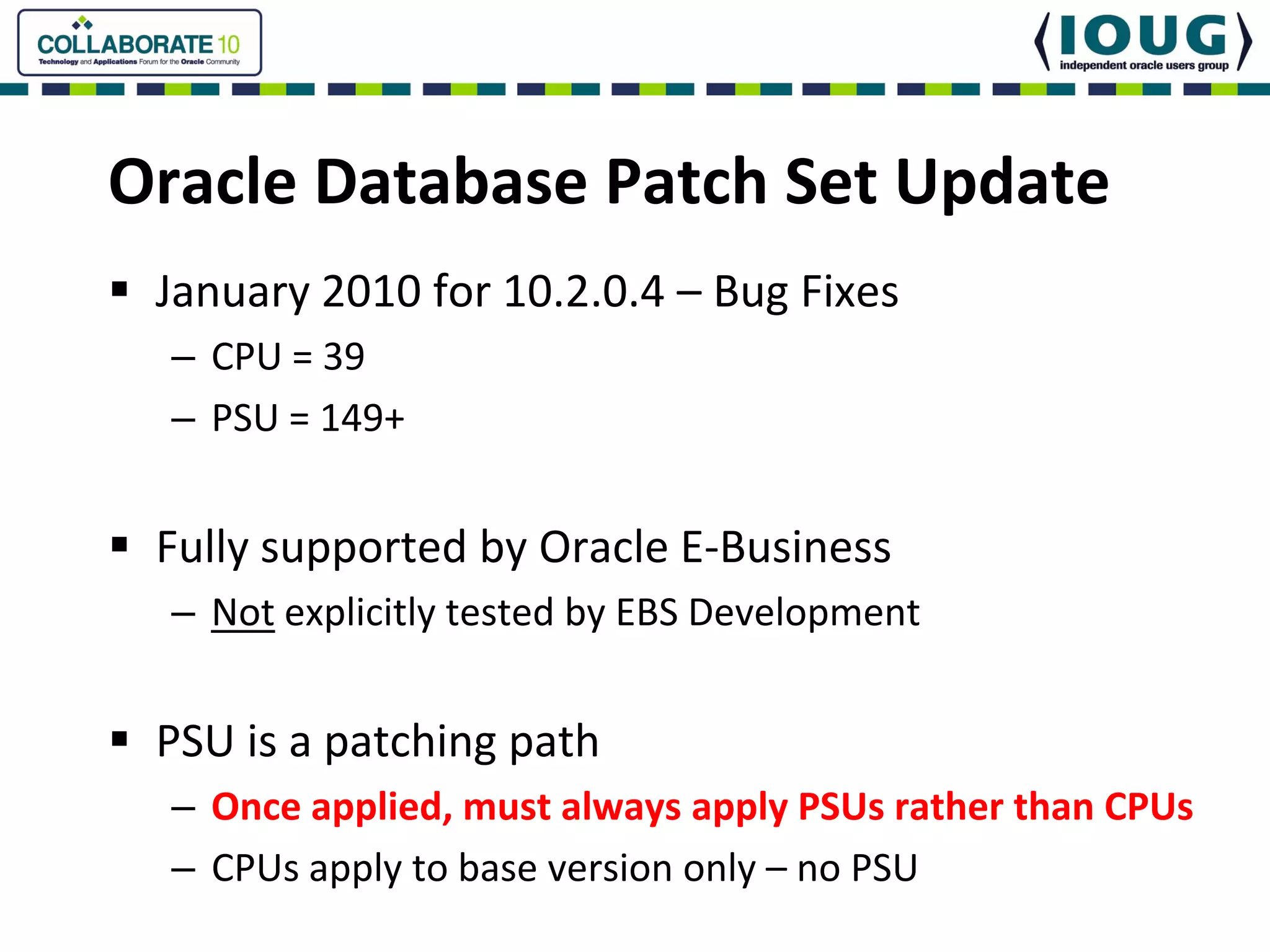
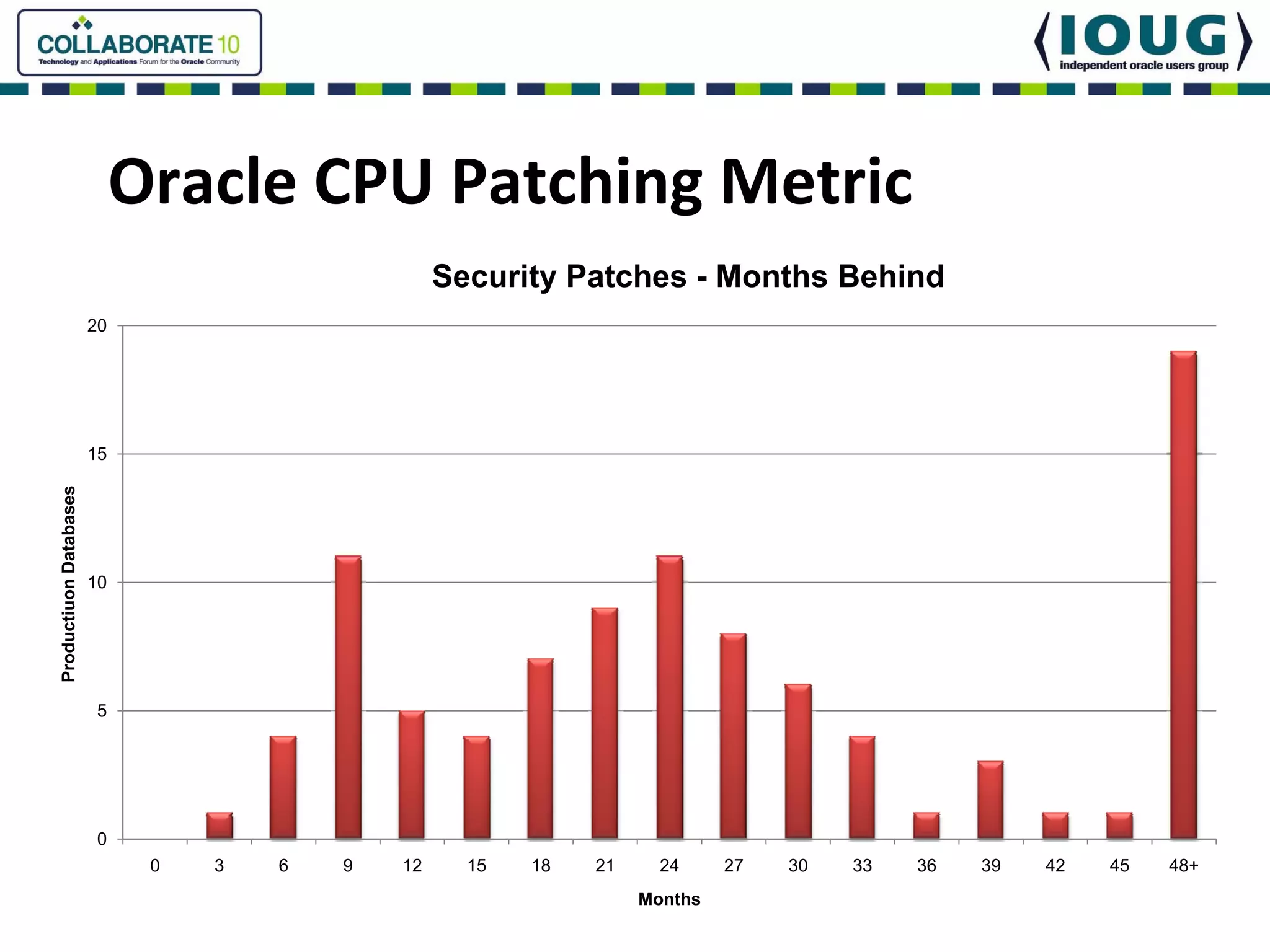
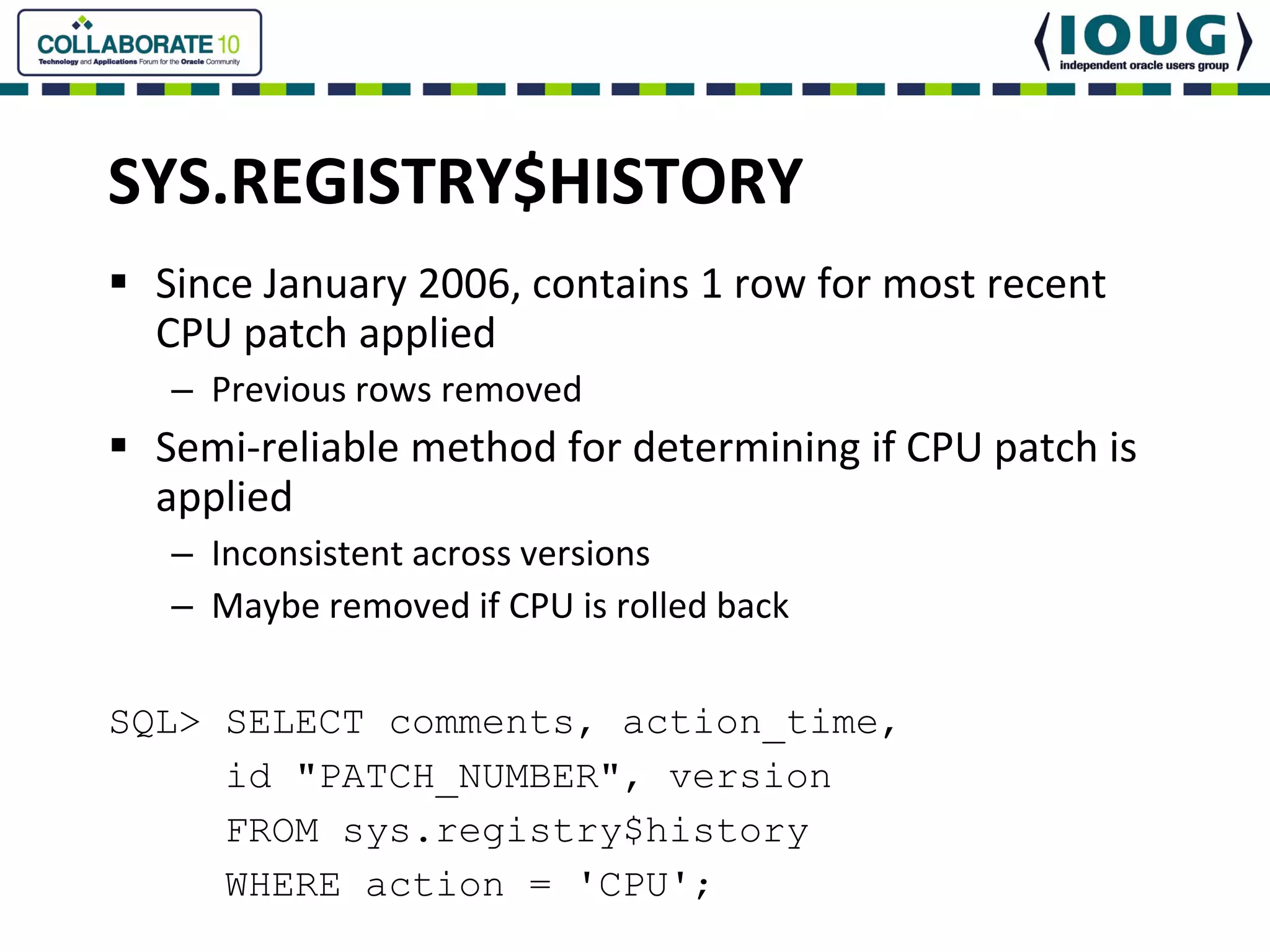
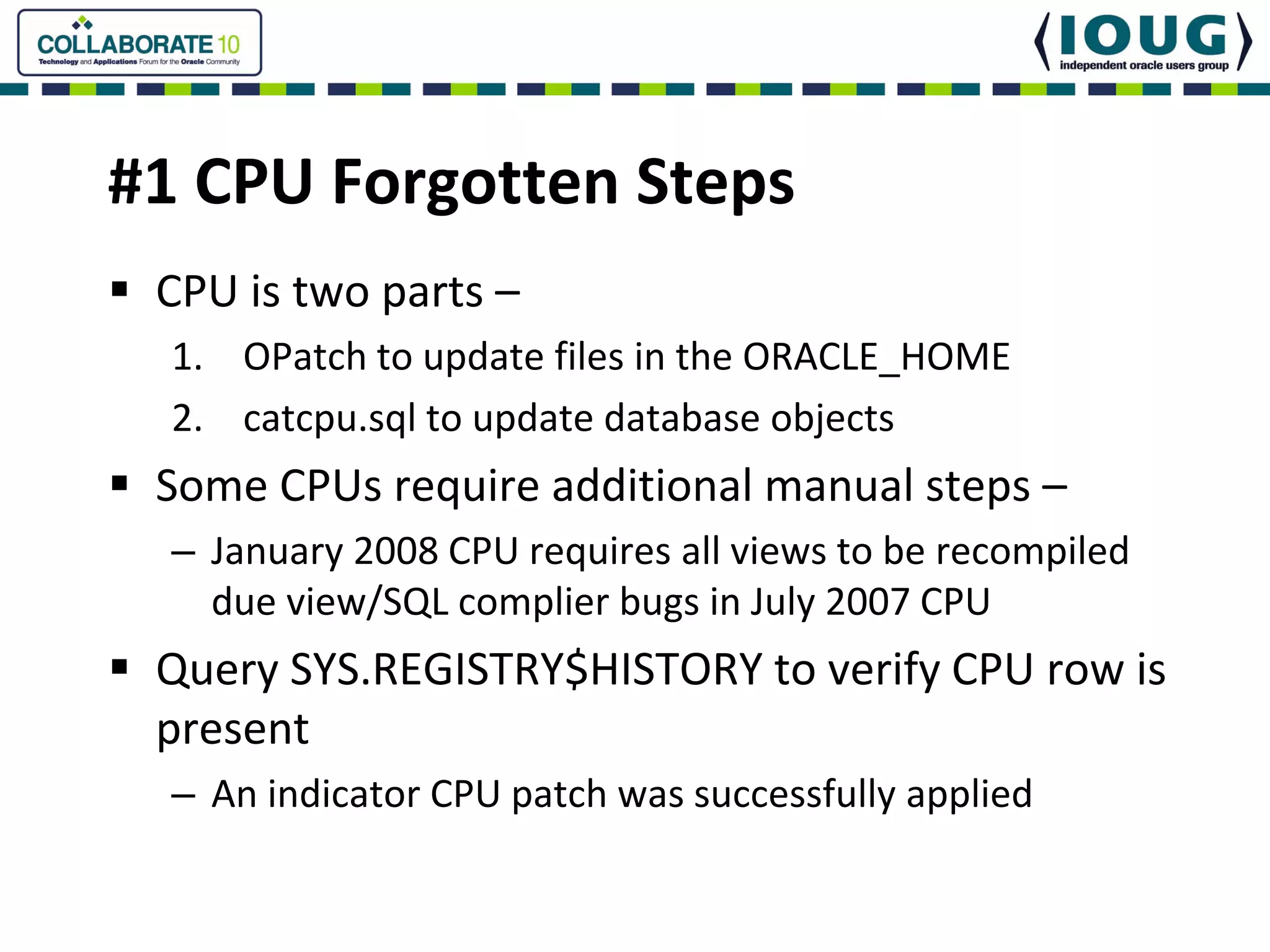
This document discusses Oracle Critical Patch Updates (CPUs). CPUs are released quarterly and fix security vulnerabilities in Oracle products. On average, 47 bugs are fixed per CPU. The document outlines the CPU patching process, common vulnerabilities addressed, and strategies for applying CPU patches. It also discusses tools for determining if a CPU has been applied and common mistakes in the CPU patching process.