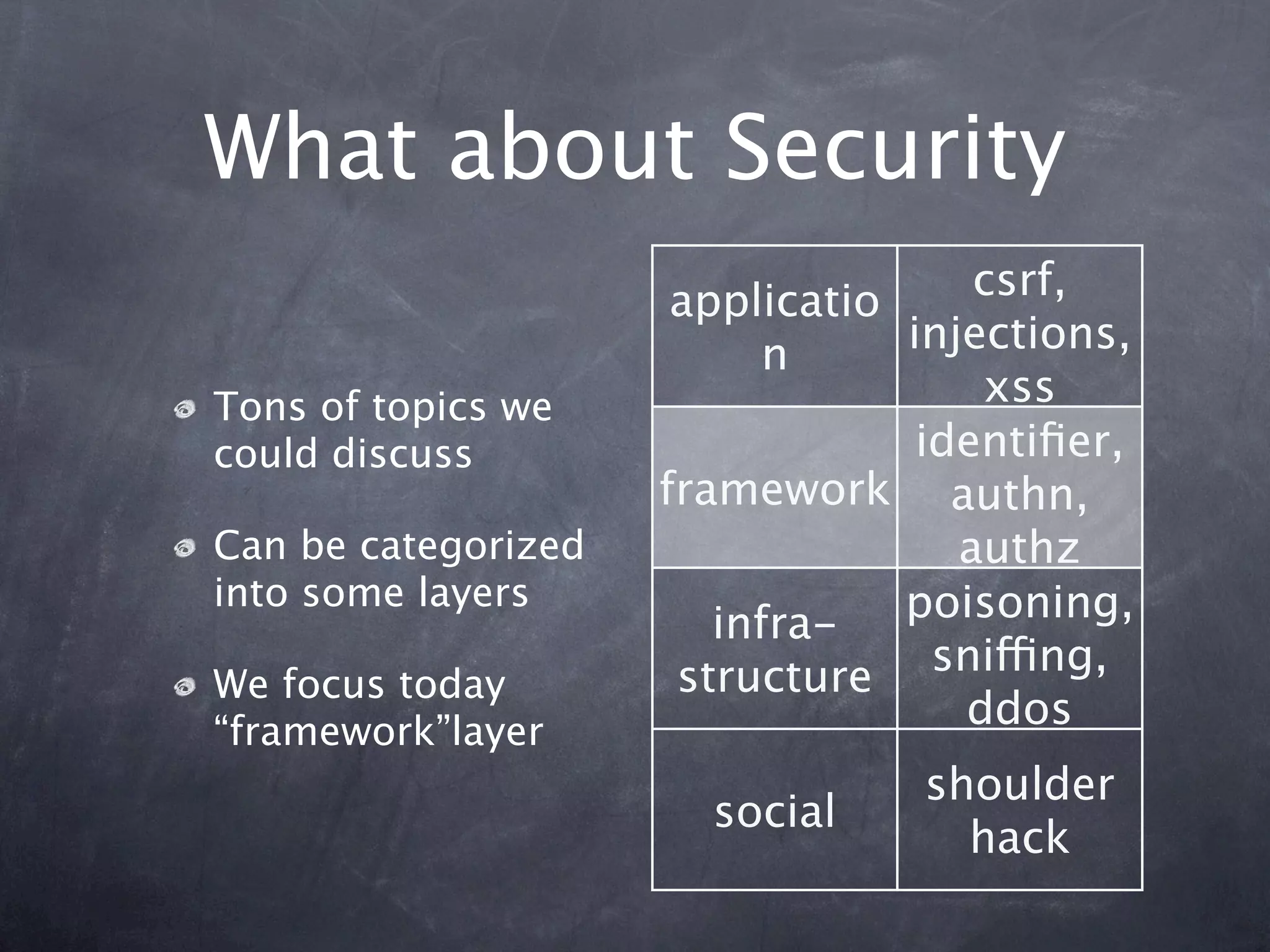
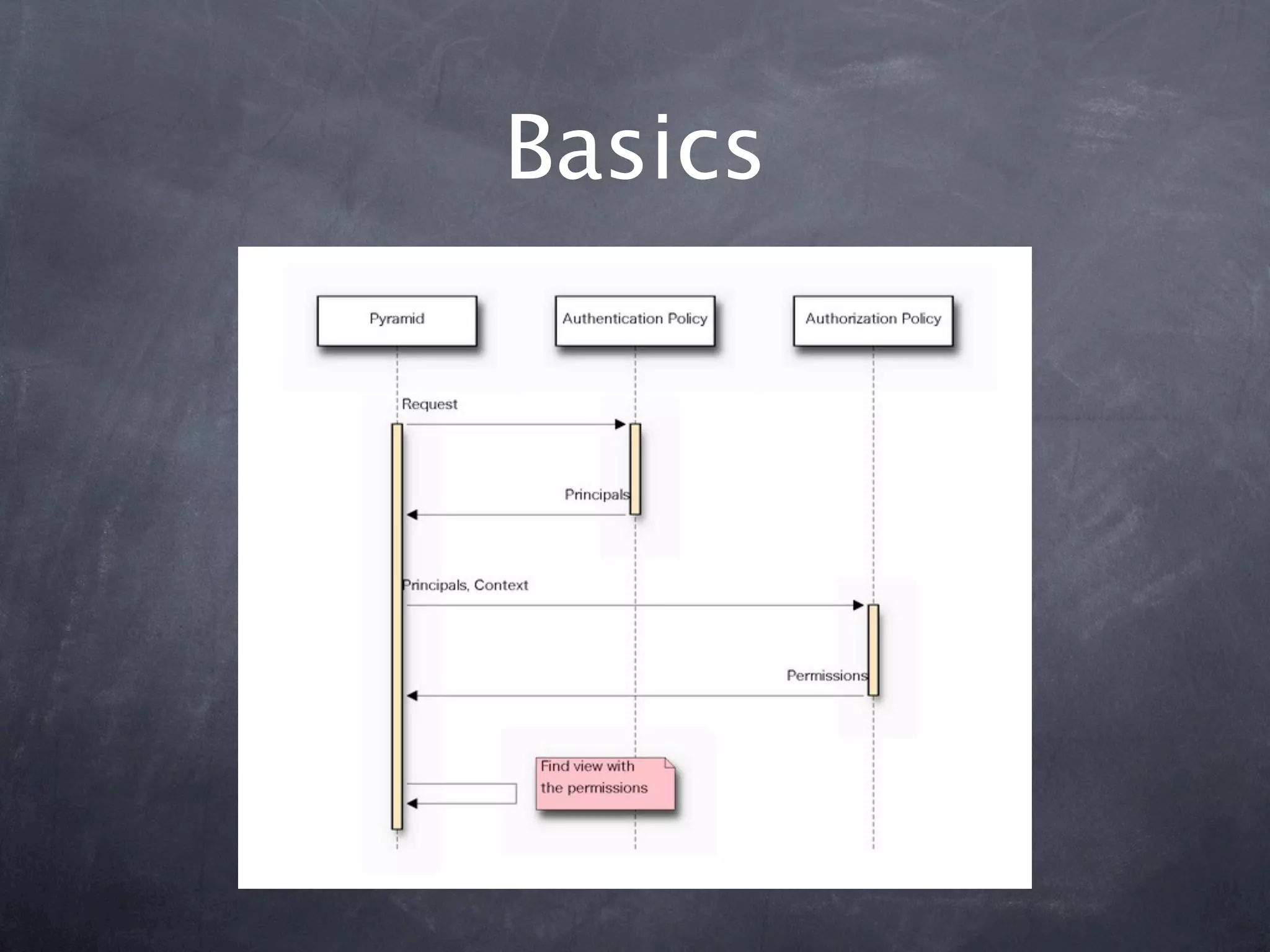
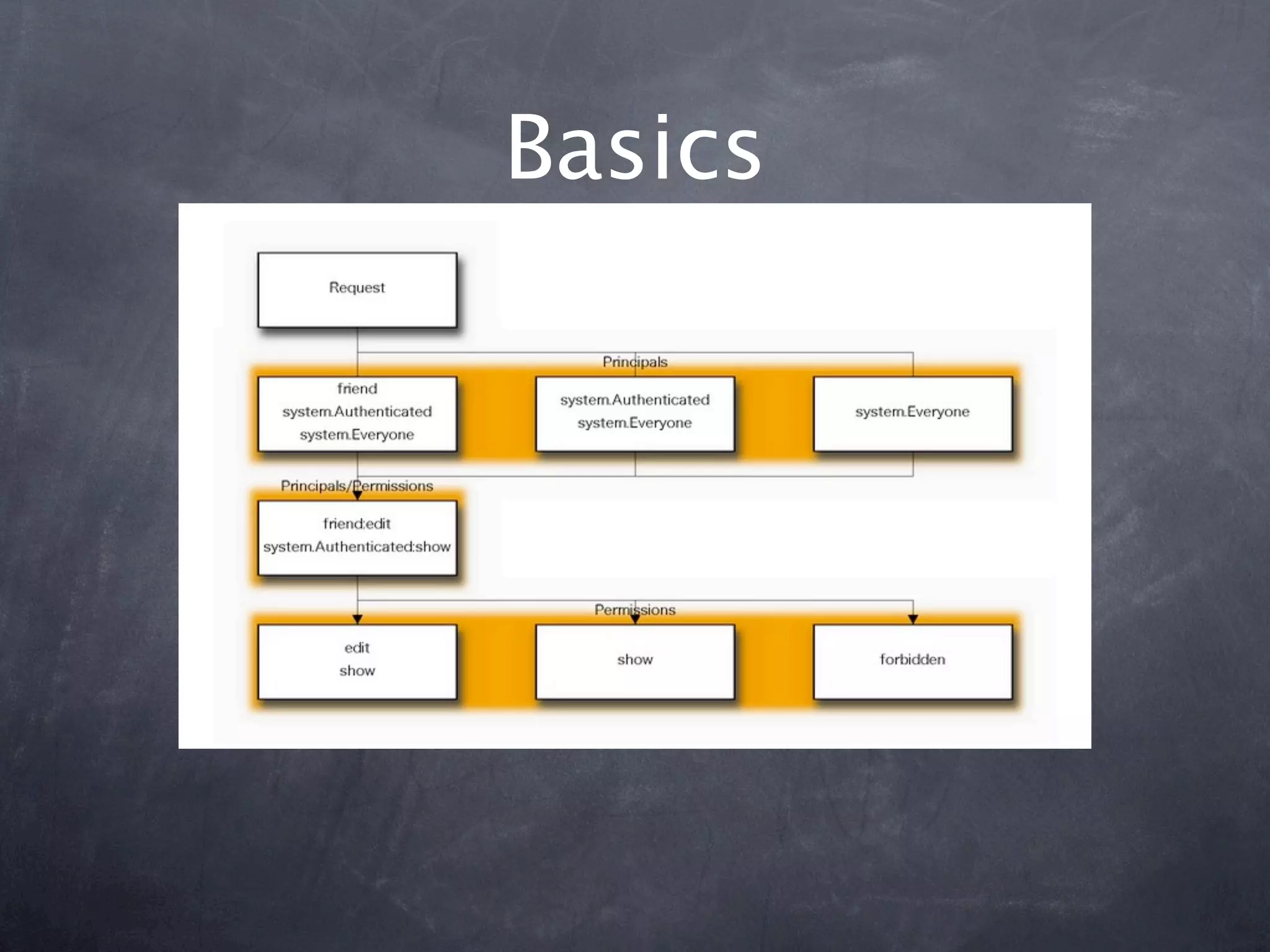
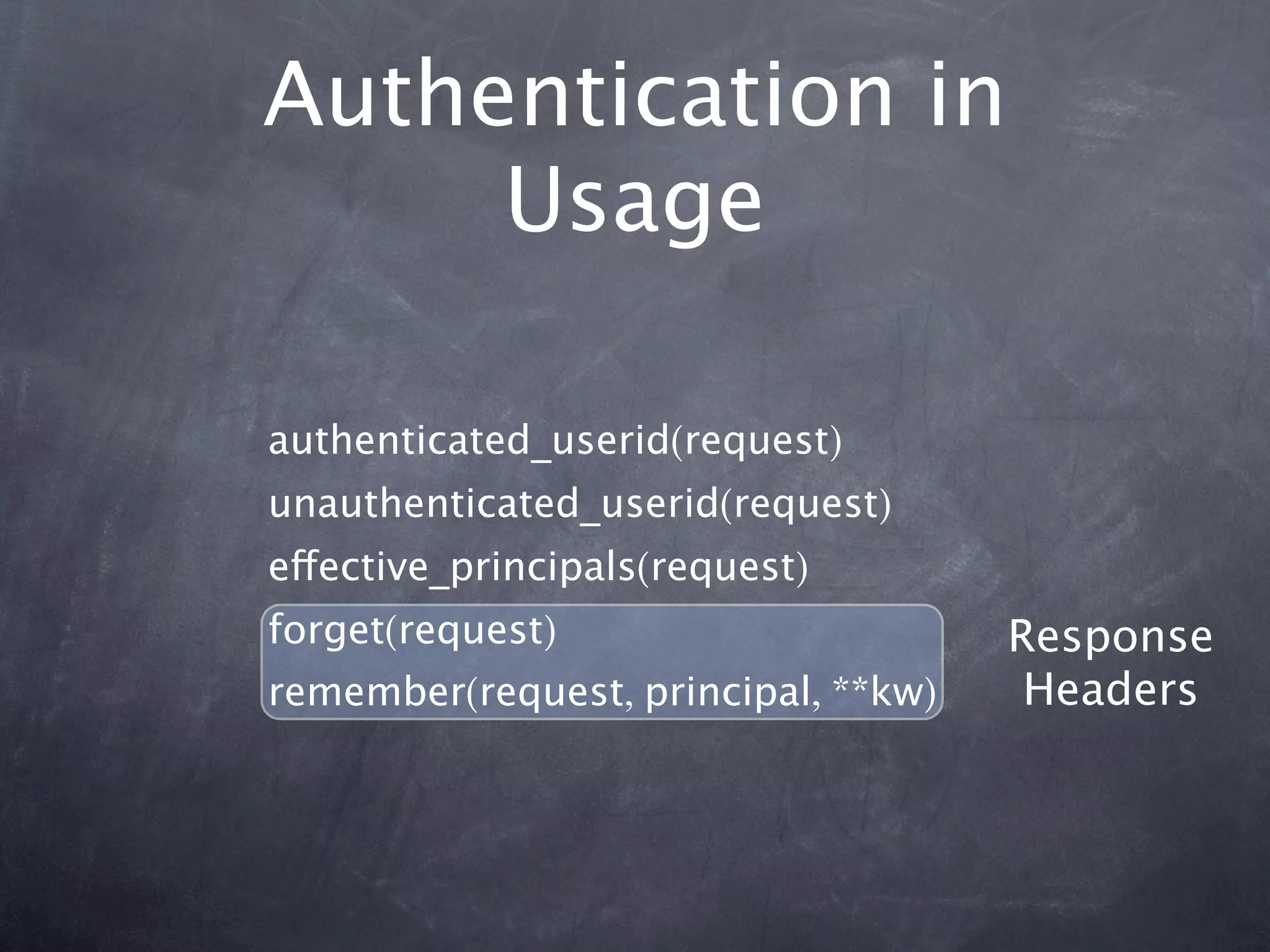
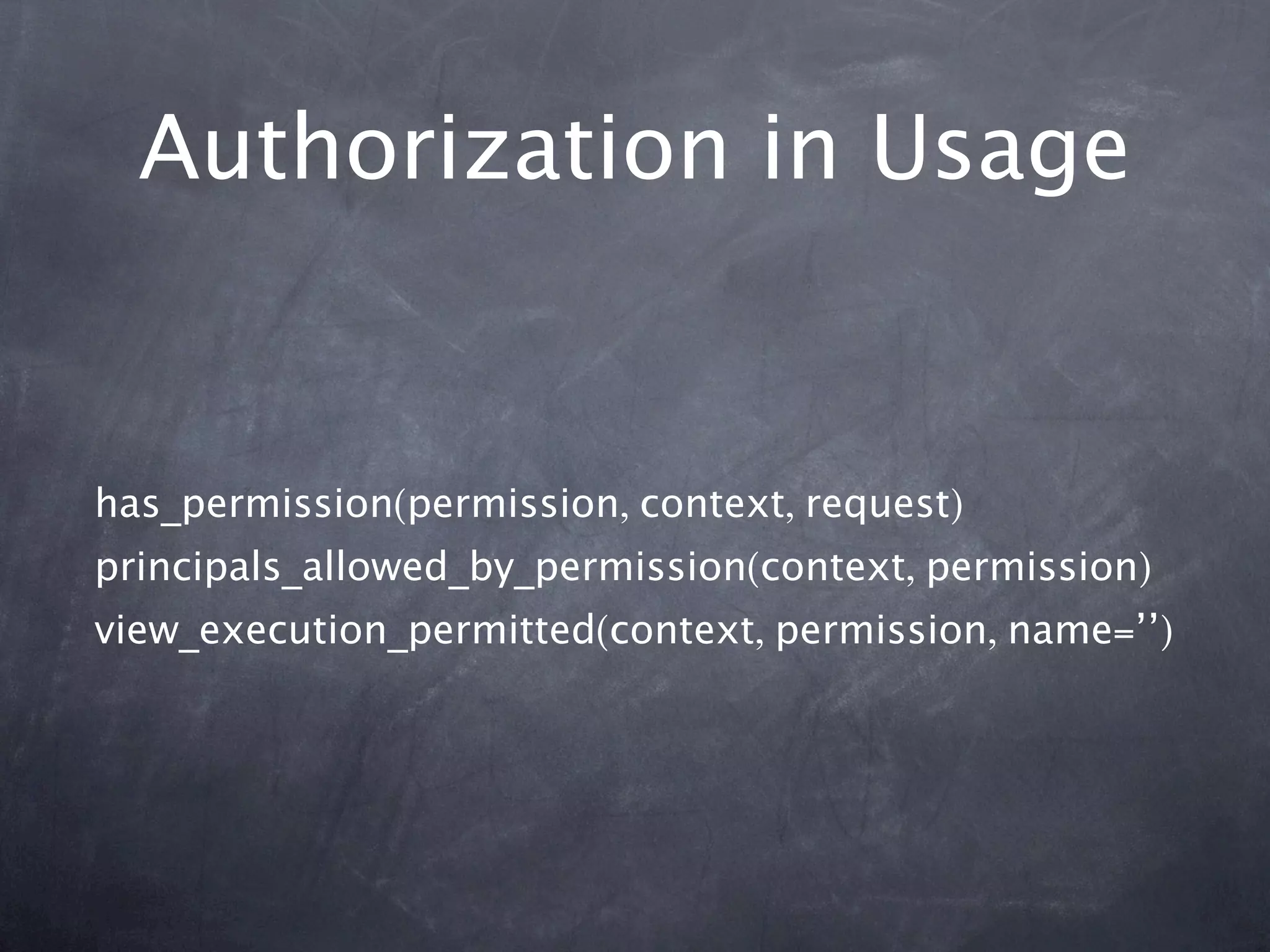
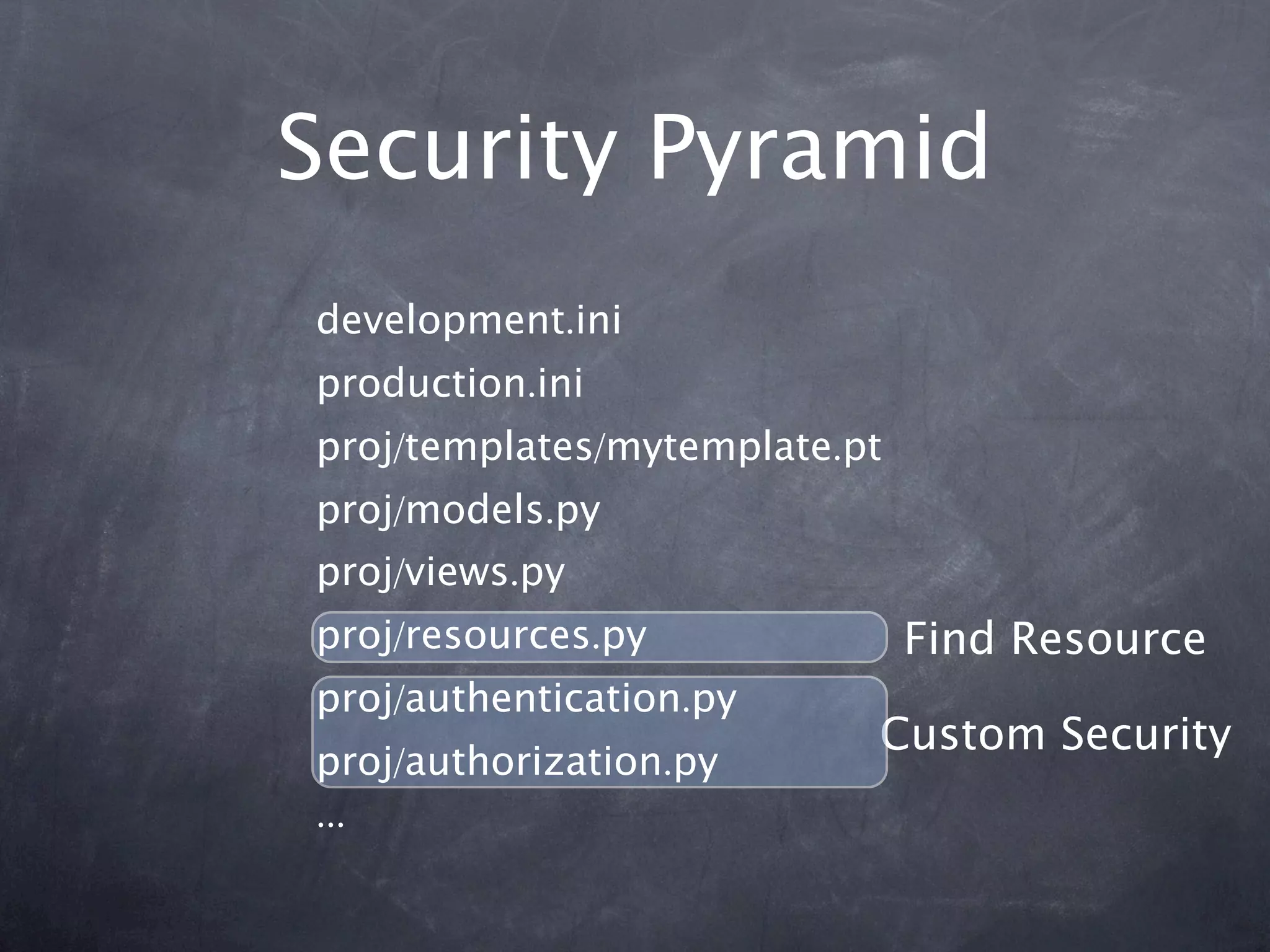
The document provides an overview of security concepts in Pyramid including authentication, authorization, and implementing a security pyramid. It discusses authentication basics like authenticated_userid and remember/forget. Authorization basics like has_permission and principals_allowed_by_permission are also covered. The document then demonstrates how to enable authentication and authorization policies in Pyramid. Common bundled policies like AuthTktAuthenticationPolicy are described. More advanced topics covered include implementing custom authentication and authorization as well as using ACLs and resources to control access.





















![Typical Stack
# in bootstrap
authentication_policy =
CustomAuthTktAuthenticationPolicy('seekrit')
authorization_policy = ACLAuthorizationPolicy()
config.add_route(..., ..., factory=resources.find_object)
# in resources
def find_object(request):
obj = ...
assert getattr(obj, ‘__acl__’, None) is not None
return obj
# in models
class Model:
__acl__ = [(Allow, Authenticated, ‘view’)]](https://image.slidesharecdn.com/pyramidsecurity-120915092455-phpapp02/75/Pyramid-Security-28-2048.jpg)
![Always Tom
Authentication
class AlwaysTomPolicy(CallbackAuthenticationPolicy):
def unauthenticated_userid(self, request):
return ‘tom’
def remember(self, request, principal, **kw):
return []
def forget(self, request):
return []](https://image.slidesharecdn.com/pyramidsecurity-120915092455-phpapp02/75/Pyramid-Security-29-2048.jpg)


