Qubes os presentation_to_clug_20150727
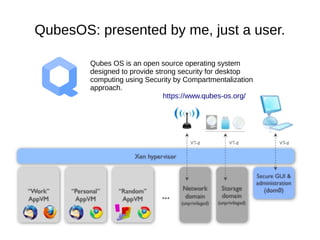
- 1. QubesOS: presented by me, just a user. Qubes OS is an open source operating system designed to provide strong security for desktop computing using Security by Compartmentalization approach. https://www.qubes-os.org/
- 2. Qubes OS is an open source operating system designed to provide strong security for desktop computing using Security by Compartmentalization approach. https://www.qubes-os.org/ Talk contains bias, errors, grudges, revisionist tendencies, misunderstandings and the seeds of its own destruction
- 3. What QubesOS is ● Not a Linux distro - though it runs Fedora on dom0 (admin) domain – Debian, Arch Linux and other TemplateVMs available ● Not a Hypervisor - though it boots Xen – QubesOS R3 (still in development) design abstracts VMM to more easily allow non-Xen implementations – KVM, LXC, Microsoft App- V (one or more of these appear to have been dead-ends) – NICTA has hosted some efforts to port Qubes to seL4, inter-VM communications services apparently done ● Often described as a Xen distro, but has lots of components in domU guests to facilitate the Qubes mission...
- 4. The problem: The endpoint PC ● Most security – especially in Linux – is intended for servers... ● … static. Deterministic lifecycle, predictable observable behaviours, management processes, audit logging, measurable/designable/configurable exposure to 3rd-parties ● Security policy is tractable and definable: network in/egress whitelisting, SELinux, AppArmor, setfacl, etc. ● Configuration management: puppet/chef/salt/ansible/etc ● Extra kernel hardening possible, Eg. TrustedGrub, Grsec, locking down loadable kernel modules, etc. ● Some of this is vaguely achievable in corporate SOEs, but.. ● … without all this bling that breaks client PCs, our operating systems only have process-level isolation to fall back on
- 5. The problem: The endpoint PC
- 6. Process isolation solves nothing Mac, Linux & Windows provide user apps APIs for: ● Capturing keystrokes regardless of which app is in focus – MacOS: addGlobalMonitorForEventsMatchingMask:NSKeyDownMask, Windows: LowLevelKeyboardProc/SetWindowsHookEx, Linux: xev EDIT 2016-02-04 – MacOS requires user intervention to grant permissions to NSKeyDown, thanks https://twitter.com/co60ca ● Screenshotting the desktop, including other applications ● Snooping clipboard contents (password managers!) ● Outbound internet access (sometimes, even inbound!) ● Filesystem access as the logged-in human user (home dir!) ● Accessing devices, services, sometimes IPC of other apps All our MMUs/protected memory, ACLs, ring0/kernel vs ring3/user space means nothing - who needs privilege escalation or authentication bypass when you've got “isolation” like this!
- 7. Process isolation solves nothing
- 8. “So what? I'll just be careful” ● It's true, on Linux we usually install packages from trusted sources. Package managers verify signatures with PGP. ● On Windows, AppLocker allows configuration to only install and run signed software from trusted publishers. ● On MacOS, GateKeeper allows configuration to only install and run signed software from the App Store or Apple approved publishers. ● Yet it's easy to bypass in just a few clicks. ● Studies show human brains are not suited to rationally navigating security warnings; the whole concept is flawed. ● “Antivirus is dead” - crypting services make evasion child's play. ASD lists it at #22 out of 35 top targeted cyber intrusion mitigations! ● Malware needs only one opportunity, so you must never slip up.
- 9. “So what? I'll just be careful”
- 10. “I'm not a target and I know what I'm doing” ● Are you really immune to drive-by remote code execution? – CVE-2015-5119 flash exploit even escapes Google Chrome's sandbox, on all platforms including Linux – Adobe Acrobat Reader has had 62 CVEs scoring 10.0 (maximum) so far this year (55 involving code exec) – Don't be fooled by lack of researcher activity and CVEs on evince and friends. The two on evince are both remote code exec. ● Do you know how quick & easy it is for phishers to build or clone trojaned versions of sites with enticing content? ● Are you sure you don't work in an industry targeted by state- sponsored1 hackers? 1: Jose Pagliery Ex-NSA director: China has hacked 'every major corporation' in U.S., March 2015 http://money.cnn.com/2015/03/13/technology/security/chinese-hack-us/
- 11. Solution: VMs for isolation – enforcing fewer, smaller interfaces Source: Joanna Rutkowska Software compartmentalization vs. physical separation(Or why Qubes OS is more than just a random collection of Vms), 2014. Available from: <http://www.invisiblethingslab.com/resources/2014/Software_compartmentalization_vs_physical_separation.pdf> [2015-07-22]
- 12. Demo ● Qubes manager – Dom0 has no networking, no apps, no data (show /proc/net/dev) – Shared free memory – Config (create new USB VM) – “Global” vs AppVM copy-paste; show xev/xeyes; window decorations ● Net/firewall/proxy VMs/whonix – xl device pass-through ● Disposable VMs ● Template VMs – Non-persistent rootfs vs persistent storage ● USB storage VM – Demonstrate rubber ducky ● PDF reader/converter in DisposableVM ● Mention GPG