Cybersecurity: Quick Preparedness Assessment
•
2 likes•548 views
Any company that relies on technology to manage client information is vulnerable to liability or loss if a data breach occurs. Use this quick assessment tool to determine whether your business is prepared for a cyber threat.
Report
Share
Report
Share
Download to read offline
Recommended
Recommended
Kevin Watkins, Enterprise Security Architect at BAT - BAT’s Managed Security ...

Kevin Watkins, Enterprise Security Architect at BAT - BAT’s Managed Security ...Global Business Events
Cisco Connect 2018 Malaysia - Cisco incident response services-strengthen you...

Cisco Connect 2018 Malaysia - Cisco incident response services-strengthen you...NetworkCollaborators
More Related Content
What's hot
Kevin Watkins, Enterprise Security Architect at BAT - BAT’s Managed Security ...

Kevin Watkins, Enterprise Security Architect at BAT - BAT’s Managed Security ...Global Business Events
Cisco Connect 2018 Malaysia - Cisco incident response services-strengthen you...

Cisco Connect 2018 Malaysia - Cisco incident response services-strengthen you...NetworkCollaborators
What's hot (20)
Kevin Watkins, Enterprise Security Architect at BAT - BAT’s Managed Security ...

Kevin Watkins, Enterprise Security Architect at BAT - BAT’s Managed Security ...
From Cave Man to Business Man, the Evolution of the CISO to CIRO

From Cave Man to Business Man, the Evolution of the CISO to CIRO
Partnership with a CFO: On the Front Line of Cybersecurity

Partnership with a CFO: On the Front Line of Cybersecurity
Cisco Connect 2018 Malaysia - Cisco incident response services-strengthen you...

Cisco Connect 2018 Malaysia - Cisco incident response services-strengthen you...
Bridging the Gap Between Threat Intelligence and Risk Management

Bridging the Gap Between Threat Intelligence and Risk Management
Cloud Storage and Security: Solving Compliance Challenges

Cloud Storage and Security: Solving Compliance Challenges
Security Program Development for the Hipster Company

Security Program Development for the Hipster Company
Cylance Information Security: Compromise Assessment Datasheet

Cylance Information Security: Compromise Assessment Datasheet
The Real Costs of SIEM vs. Managed Security Service

The Real Costs of SIEM vs. Managed Security Service
How to Steer Cyber Security with Only One KPI: The Cyber Risk Resilience

How to Steer Cyber Security with Only One KPI: The Cyber Risk Resilience
The Prescription for Protection - Avoid Treatment Errors To The Malware Problem

The Prescription for Protection - Avoid Treatment Errors To The Malware Problem
6 Biggest Cyber Security Risks and How You Can Fight Back

6 Biggest Cyber Security Risks and How You Can Fight Back
Viewers also liked
"India's National Disaster Management Authority's (NDMA) initiatives on safet...

"India's National Disaster Management Authority's (NDMA) initiatives on safet...SUNIL KUMAR KOHLI, IDAS ndc
Viewers also liked (18)
Big Data Viz (and much more!) with Apache Zeppelin

Big Data Viz (and much more!) with Apache Zeppelin
"India's National Disaster Management Authority's (NDMA) initiatives on safet...

"India's National Disaster Management Authority's (NDMA) initiatives on safet...
Boosting Machine Learning with Redis Modules and Spark

Boosting Machine Learning with Redis Modules and Spark
Similar to Cybersecurity: Quick Preparedness Assessment
Similar to Cybersecurity: Quick Preparedness Assessment (20)
CyberM3 Business Enablement: Cybersecurity That Empowers Your Business with C...

CyberM3 Business Enablement: Cybersecurity That Empowers Your Business with C...
BIZGrowth Strategies — Cybersecurity Special Edition 2023

BIZGrowth Strategies — Cybersecurity Special Edition 2023
Weakest links of an organization's Cybersecurity chain

Weakest links of an organization's Cybersecurity chain
BlueVoyant: 7 Experts Share Key Questions To Ask When Evaluating Providers

BlueVoyant: 7 Experts Share Key Questions To Ask When Evaluating Providers
For Public_ Cybersecurity_ Frameworks, Fundamentals, and Foundations 2023.pdf

For Public_ Cybersecurity_ Frameworks, Fundamentals, and Foundations 2023.pdf
Strategic Insights on IT & Cyber Risk Assessments.pdf

Strategic Insights on IT & Cyber Risk Assessments.pdf
Cyber Data Breach Review_ Key Steps to Protect Your Business in the Digital A...

Cyber Data Breach Review_ Key Steps to Protect Your Business in the Digital A...
10 Most Important Strategies for Cybersecurity Risk Mitigation.pdf

10 Most Important Strategies for Cybersecurity Risk Mitigation.pdf
More from CBIZ, Inc.
More from CBIZ, Inc. (20)
BIZGrowth Strategies - Back to Basics Special Edition

BIZGrowth Strategies - Back to Basics Special Edition
BIZGrowth Strategies - Workforce & Talent Optimization Special Edition

BIZGrowth Strategies - Workforce & Talent Optimization Special Edition
BIZGrowth Newsletter - Economic Slowdown Solutions Special Edition

BIZGrowth Newsletter - Economic Slowdown Solutions Special Edition
BIZGrowth Strategies - Cybersecurity Special Edition

BIZGrowth Strategies - Cybersecurity Special Edition
Connections Help Law Practice Efficiently Obtain $5 Million Line of Credit

Connections Help Law Practice Efficiently Obtain $5 Million Line of Credit
Custom Communication Plan & Active Enrollment Result in Increased Consumerism

Custom Communication Plan & Active Enrollment Result in Increased Consumerism
Experienced Consulting Approach Leads Engineering Firm to the Right CFO

Experienced Consulting Approach Leads Engineering Firm to the Right CFO
CBIZ Quarterly Manufacturing and Distribution "Hot Topics" Newsletter (May-Ju...

CBIZ Quarterly Manufacturing and Distribution "Hot Topics" Newsletter (May-Ju...
Rethinking Total Compensation to Retain Top Talent

Rethinking Total Compensation to Retain Top Talent
Common Labor Shortage Risks & Tips to Mitigate Your Exposures

Common Labor Shortage Risks & Tips to Mitigate Your Exposures
How the Great Resignation Affects the Tax Function

How the Great Resignation Affects the Tax Function
Experienced Consulting Approach Leads Engineering Firm to the Right CFO

Experienced Consulting Approach Leads Engineering Firm to the Right CFO
BIZGrowth Strategies - The Great Resignation Special Edition

BIZGrowth Strategies - The Great Resignation Special Edition
CBIZ Quarterly Commercial Real Estate "Hot Topics" Newsletter (Jan-Feb 2022)

CBIZ Quarterly Commercial Real Estate "Hot Topics" Newsletter (Jan-Feb 2022)
Changes in Lease Accounting Are About to Get Real for CRE

Changes in Lease Accounting Are About to Get Real for CRE
Recently uploaded
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Recently uploaded (20)
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Cybersecurity: Quick Preparedness Assessment
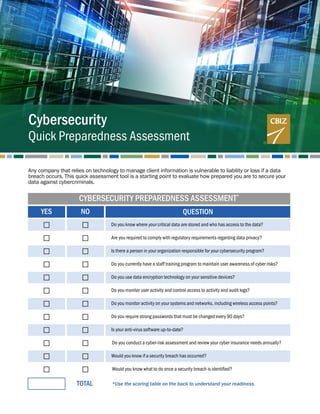
- 1. Cybersecurity Quick Preparedness Assessment CYBERSECURITY PREPAREDNESS ASSESSMENT* YES NO Do you know where your critical data are stored and who has access to the data? Are you required to comply with regulatory requirements regarding data privacy? Is there a person in your organization responsible for your cybersecurity program? Do you currently have a staff training program to maintain user awareness of cyber risks? Do you use data encryption technology on your sensitive devices? Do you monitor user activity and control access to activity and audit logs? Do you monitor activity on your systems and networks, including wireless access points? Do you require strong passwords that must be changed every 90 days? Is your anti-virus software up-to-date? Do you conduct a cyber-risk assessment and review your cyber insurance needs annually? Would you know if a security breach has occurred? Would you know what to do once a security breach is identified? QUESTION Any company that relies on technology to manage client information is vulnerable to liability or loss if a data breach occurs. This quick assessment tool is a starting point to evaluate how prepared you are to secure your data against cybercriminals. TOTAL *Use the scoring table on the back to understand your readiness.
- 2. Learn how our cybersecurity services can protect your company at www.cbiz.com/cybersecurity Our business is growing yours Copyright©2016.CBIZ,Inc.NYSEListed:CBZ.Allrightsreserved. CYBERSECURITY PREPAREDNESS ASSESSMENT Situations that could compromise the security of your data are inevitable, and unauthorized access can lead to devastating financial, legal and reputational consequences. Taking preventative steps to identify your areas of vulnerability and improvement is critical to protecting your organization. Based on your responses to the assessment, you can rank how prepared your organization is to face cyber crime. Regardless of your score, every organization can benefit from assessing its existing strategy to pinpoint potential areas for improvement. Even the most proficient cyber team can face daily distractions of financial, employee and technology issues that can diminish its ability to focus on cybersecurity. CBIZ is skilled in overcoming challenges inherent in defining realistic and effective safeguards. We can work with organizations at all levels of preparedness to design a strategy that meets their specific goals and objectives. CBIZ provides a number of services to help our clients manage cybersecurity, including: ■■ Penetration testing and vulnerability assessments ■■ Web and mobile application assessments ■■ IT audits and risk assessments ■■ Digital forensics and litigation support ■■ Security program development and reviews ■■ Infrastructure design and assessment ■■ Social engineering/facility breach exercises ■■ Incident response Let CBIZ Risk & Advisory Services help protect you from cyber risk. Christopher P. Roach 866.956.1983 | RASinfo@cbiz.com CBIZ Risk & Advisory Services offers leading edge evaluation and consulting services to help our clients navigate the complexities of controlling their business. While your organization has started to implement basic procedures, you could benefit from adding some additional levels of security to ensure your critical data are protected. 0 - 3 BEGINNER Your organization likely understands what is at risk and has steps in place to recover if a data breach does occur. Adding a continuous monitoring program to assess your risks can shift you to a more proactive approach. 4 - 6 INTERMEDIATE Your organization likely has a team devoted to cybersecurity and a strategy in place to combat cyber risks. Reevaluating your practices on a continuous basis can help you adapt to account for emerging risks. 7 - 9 ADVANCED Your organization has a defined cybersecurity strategy in place, regularly monitors cyber risks and trains its employees on cyber policies and procedures. You use a proactive approach to keep your organization prepared. 10 - 12 PROFICIENT TOTAL YOUR ‘YES’ ANSWERS TO CALCULATE SCORE: Results
