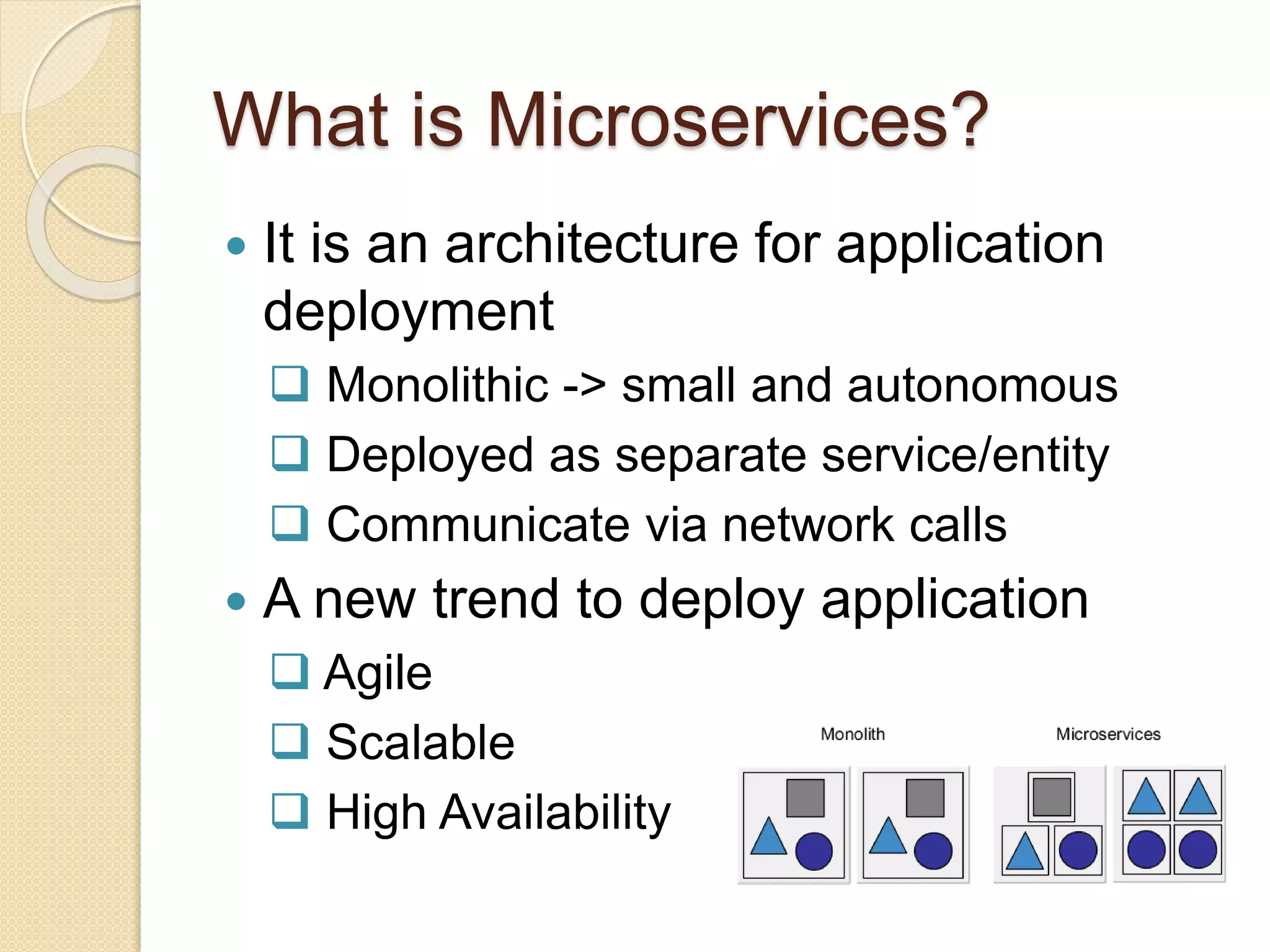
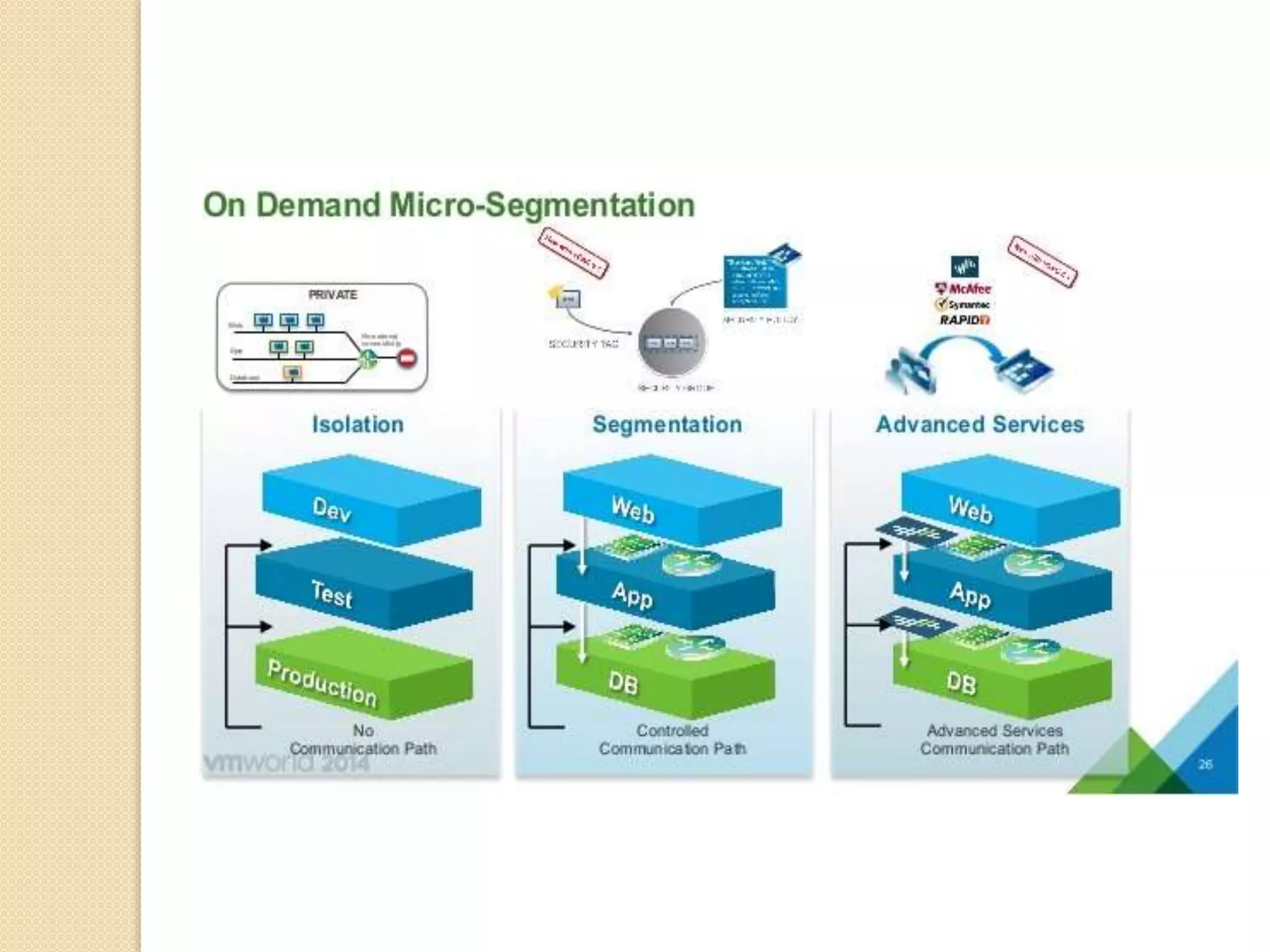
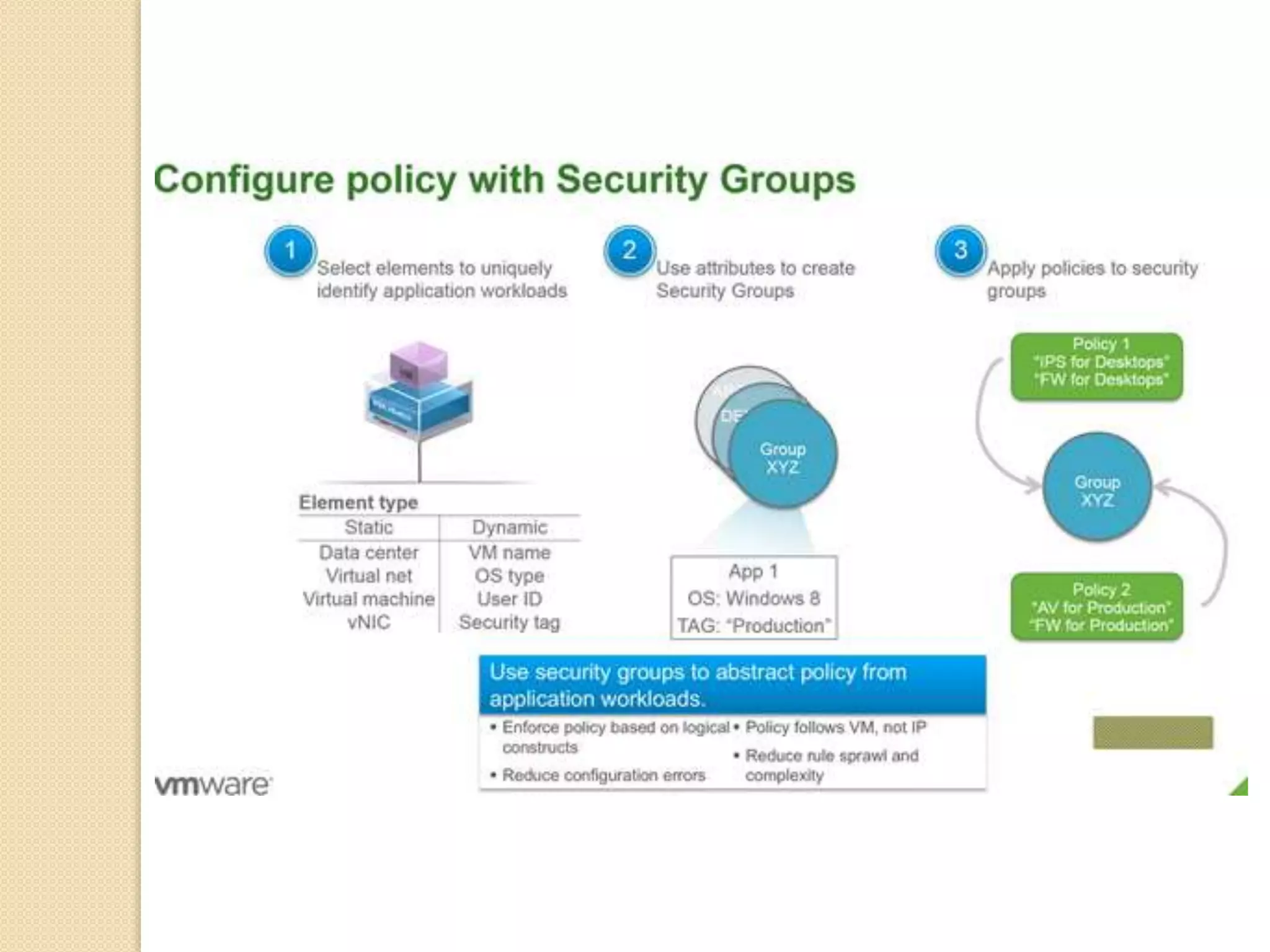
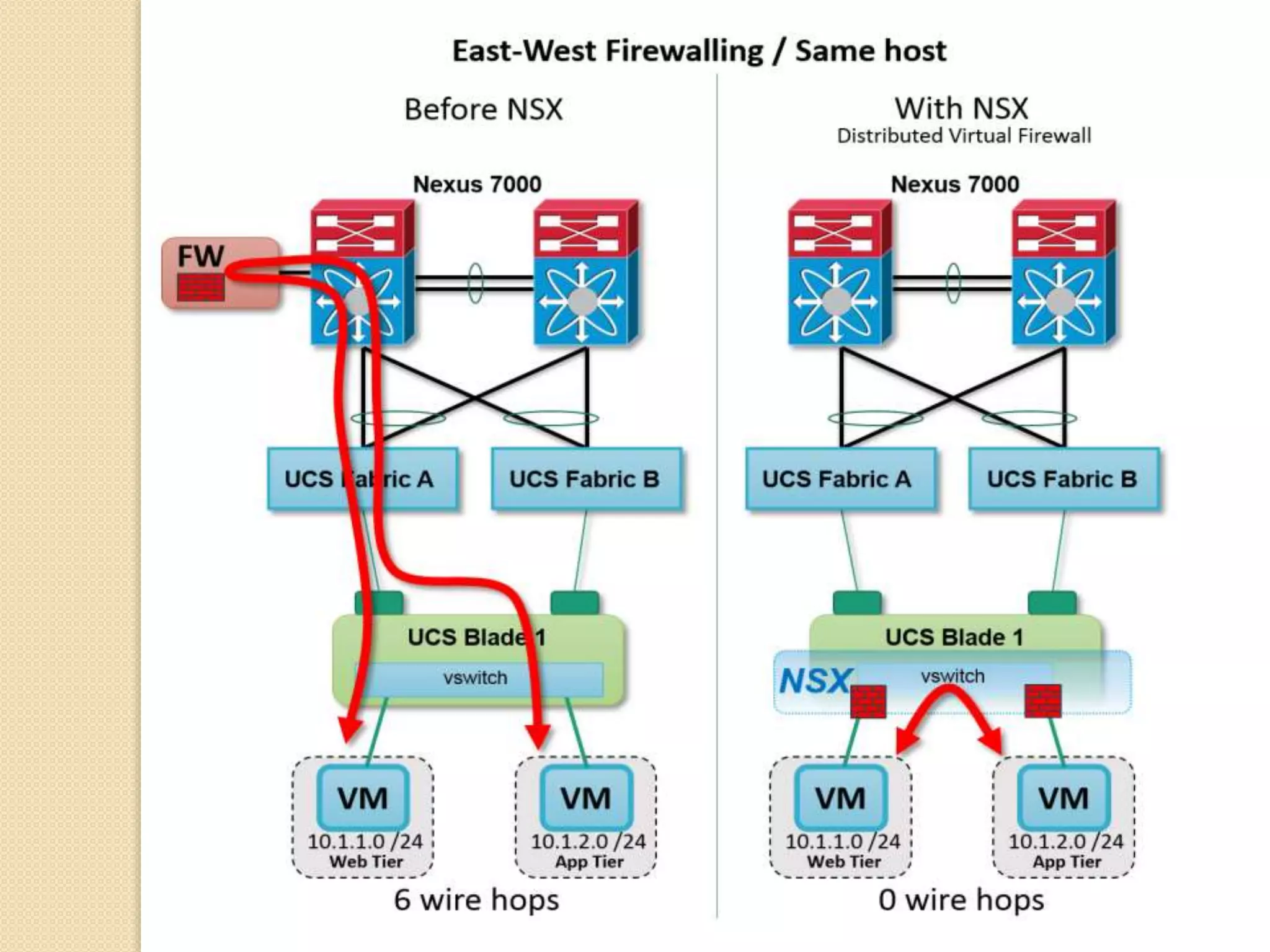
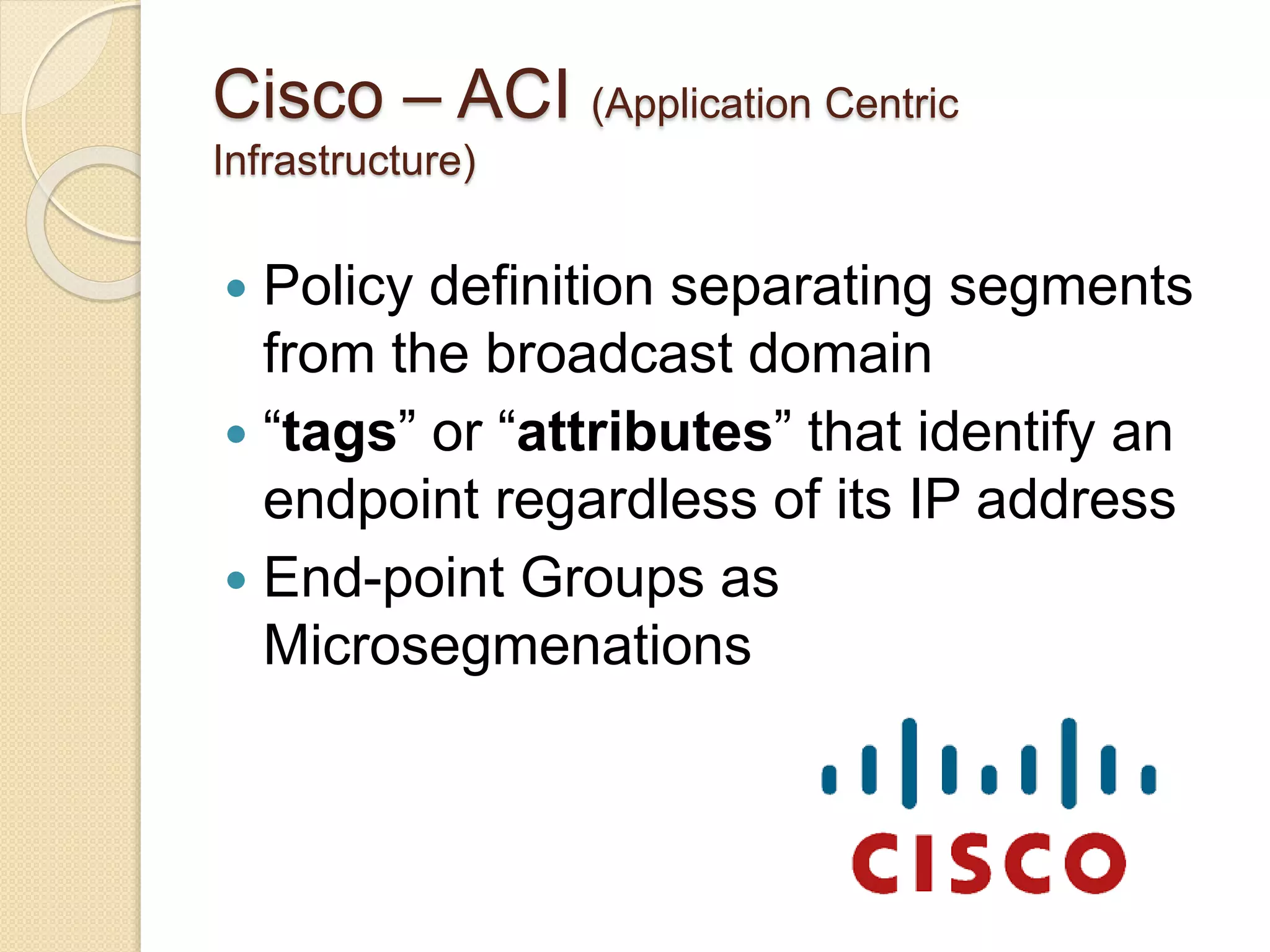
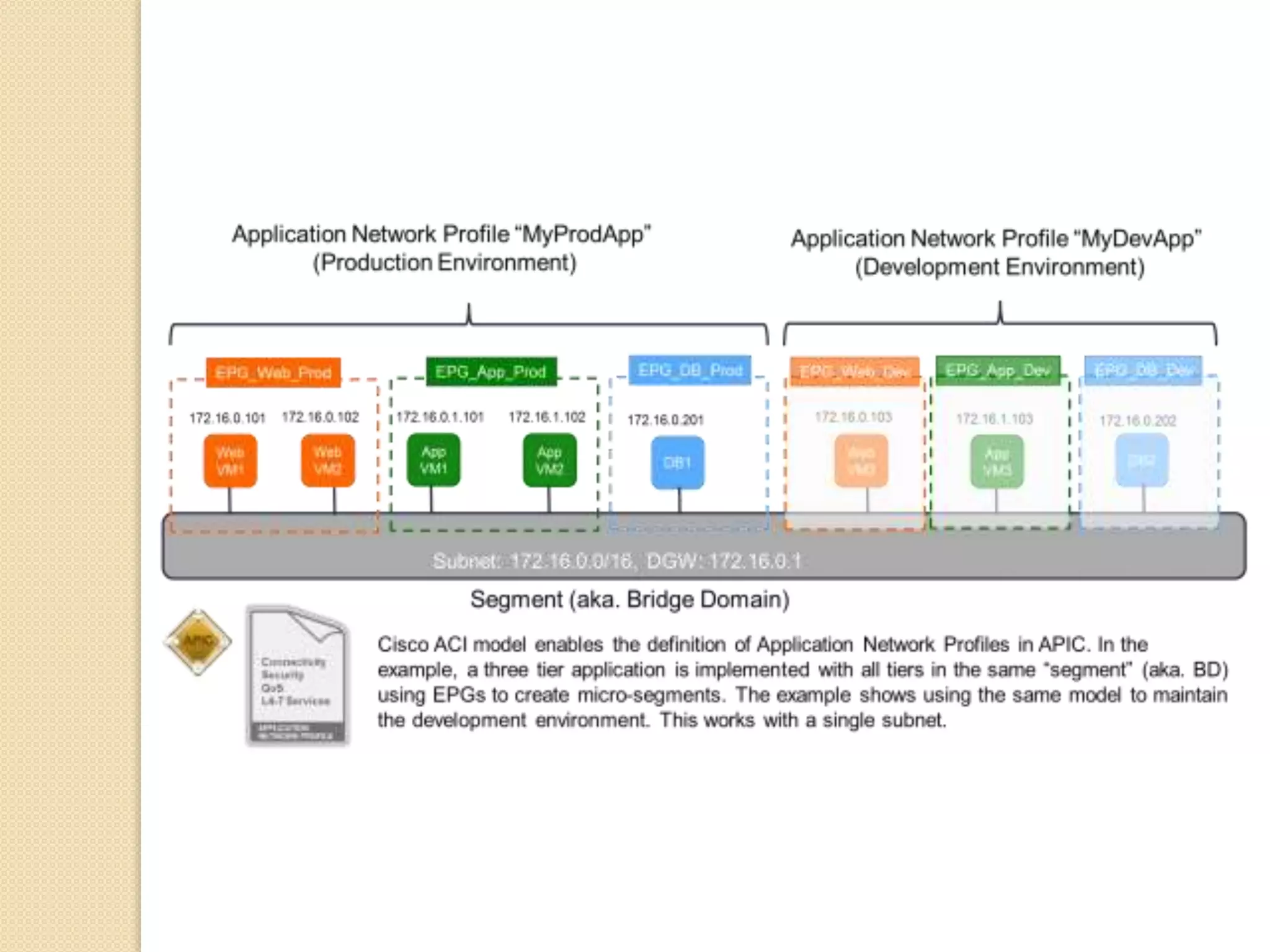
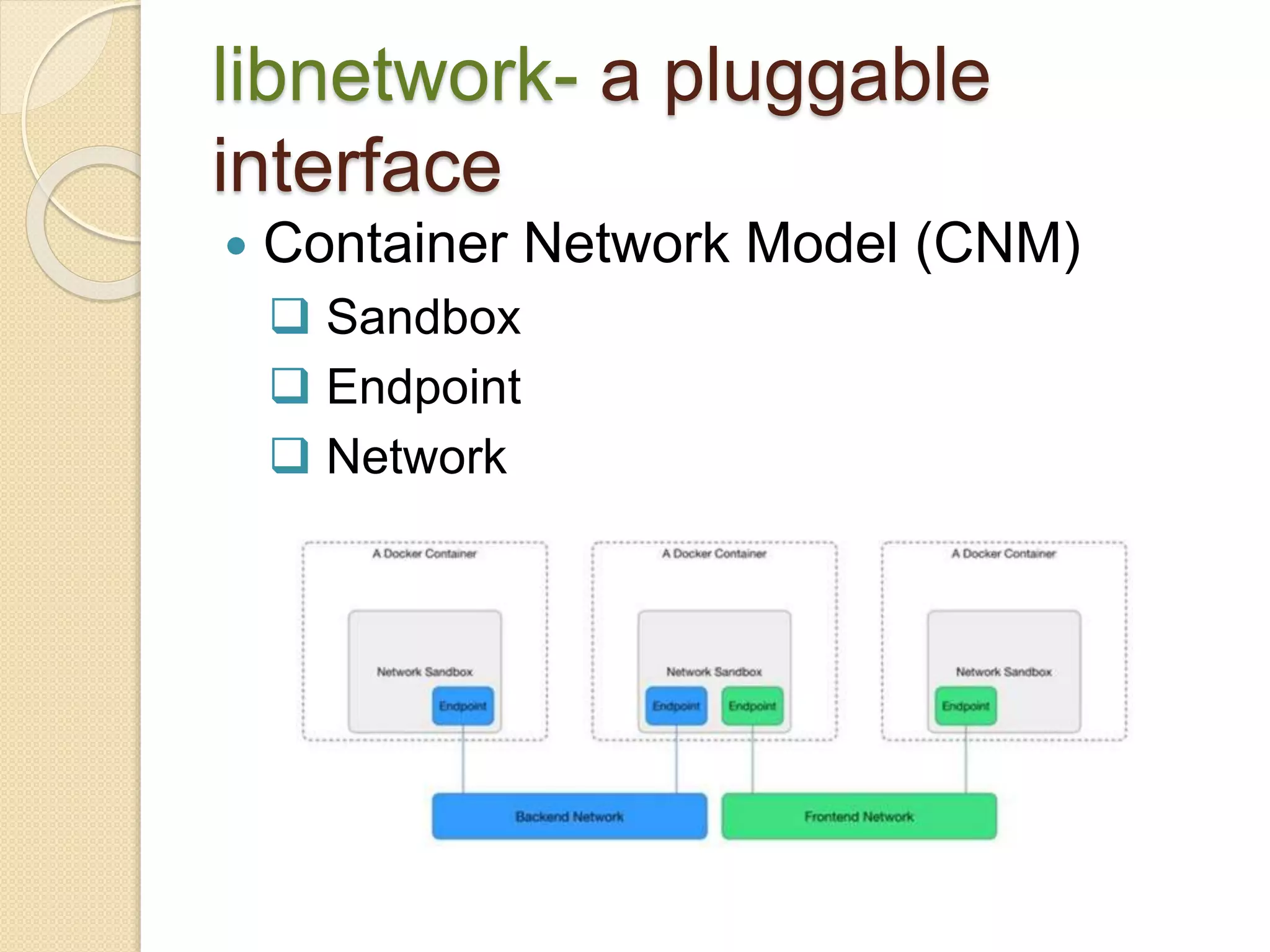
Microsegmentation, which groups network entities into segments and applies security policies to control traffic, is a perfect fit for securing microservices architectures. It allows for network-independent security policies to be defined and centrally managed at a fine-grained level, enabling policies to adapt to the dynamic and elastic nature of microservices. Major networking and security platforms like VMware NSX, Cisco ACI, and Docker's libnetwork support microsegmentation capabilities that are well-suited for microservices security through isolation, segmentation, and distributed policy enforcement.