CODA a novel anti-malware system
•
0 likes•176 views
A new technology which can detect and prevent threats on Windows in real time
Report
Share
Report
Share
Recommended
Recommended
It’s that time of the year again. October is upon us, so get ready to spread some cybersecurity wisdom around you and, of course, a few candies here and there for the occasional Halloween visitors.The dark side of cybersecurity: International Awareness Cybersecurity Month

The dark side of cybersecurity: International Awareness Cybersecurity MonthITrust - Cybersecurity as a Service
More Related Content
Similar to CODA a novel anti-malware system
It’s that time of the year again. October is upon us, so get ready to spread some cybersecurity wisdom around you and, of course, a few candies here and there for the occasional Halloween visitors.The dark side of cybersecurity: International Awareness Cybersecurity Month

The dark side of cybersecurity: International Awareness Cybersecurity MonthITrust - Cybersecurity as a Service
Similar to CODA a novel anti-malware system (20)
The Internet is on fire – don't just stand there, grab a bucket!

The Internet is on fire – don't just stand there, grab a bucket!
The Best And Easiest Ways To Protect Yourself From Hackers

The Best And Easiest Ways To Protect Yourself From Hackers
ID cuffs: Hackers targeting international travelers

ID cuffs: Hackers targeting international travelers
The dark side of cybersecurity: International Awareness Cybersecurity Month

The dark side of cybersecurity: International Awareness Cybersecurity Month
How Safety Alarms and Methods Help to Combat Crime

How Safety Alarms and Methods Help to Combat Crime
Recently uploaded
Recently uploaded (20)
🍑👄Dehradun Esℂorts Serviℂe☎️9315791090🍑👄 ℂall Girl serviℂe in ☎️Dehradun ℂall...

🍑👄Dehradun Esℂorts Serviℂe☎️9315791090🍑👄 ℂall Girl serviℂe in ☎️Dehradun ℂall...
Thank You Luv I’ll Never Walk Alone Again T shirts

Thank You Luv I’ll Never Walk Alone Again T shirts
100^%)( POLOKWANE))(*((+27838792658))*))௹ )Abortion Pills for Sale in Sibasa,...

100^%)( POLOKWANE))(*((+27838792658))*))௹ )Abortion Pills for Sale in Sibasa,...
Production 2024 sunderland culture final - Copy.pptx

Production 2024 sunderland culture final - Copy.pptx
Reggie miller choke t shirtsReggie miller choke t shirts

Reggie miller choke t shirtsReggie miller choke t shirts
The Rise of Subscription-Based Digital Services.pdf

The Rise of Subscription-Based Digital Services.pdf
CODA a novel anti-malware system
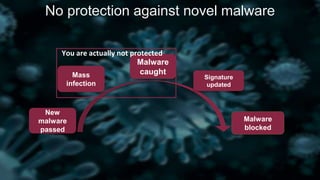
- 1. New malware passed Mass infection Malware caught Signature updated Malware blocked You are actually not protected No protection against novel malware
- 2. Dependence on internet In 2016 3.6 billion people in Internet. 65% paid to download or access some kind of online content Cybercrime catches our money The rapid digitization of people’s lives and enterprise records will increase the cost of data breaches to $2.1 trillion globally by 2019 20% of small to mid sized businesses have been cyber crime targets. In 2016 31.9% of user computers were subjected to at least one Malware-class web attack over the year. TOP 3 delusions There is no important information in my PC! Your PC may silently attack another users. If I don’t surfing on suspicious sites I malware will not catch me! To be careful is good, but you never know, where attack can occur. There are too many attack vectors. Any antivirus software will protect me against any malware! Imagine blackhat hacker who wants to attack you. He know that you have antivirus X. And so he install X too and fixes malware so that X would not detect it. Of cause sometimes it is difficult. But now it takes about 2 hours. The threat is growing from day to day
- 3. System behavior trace during N hours Model builder System trace database Model database System model Any available behavior Behavior allowed by model Encrypted channel Entire system behavior trace recording Building system model using trace and another models Detecting deviations from model Connection with Internet required rarely Principal scheme of CODA protection system
- 4. When you want to protect you home from thief. You hires guard He has all photos of well known thieves If in another house unknown thief has stolen money, guard will not let him enter your home But when thief changed clothes, he entered you home and stole you money He knows all harmful actions, which can be executed by your guests If guest want to switch on gas stove, butler will allow it, but if guest forgot fire, the home would be exploded When you want to protect you home from thief. You hires butler When you want to protect you home from thief. You creates a test room Guest supposes that test room is your real home. And if he try to pull your pouch and escape to window, he will not enter you real sweet home But if guest recognize that such a pure room is not your home, he will bypass your test When you want to protect you home from thief. You hires detective He starts too look at all your guests for a week and records all actions, which your guests executes in your home. If at learning week some guest switched on TV, washed hands and took your punch, then further he can take it only after that actions If detective doubts about behavior of a guest, he consults with other detectives Description of our technology with analogies
- 5. Frequent updates are not required Protection against novel and old threats Every client actually has his own malware behavior detector Update every 3 hours You are protected against only previously known threats Crime can install latest version of protection tool and test malware Instant reaction on unknown threats No protection against unknown threats Can work with another malware protection solutions Usually incompatible with each other Advantages of CODA compared with older solutions
Editor's Notes
- Imagine you want to protect you home from thief. You hires butler. He periodically receives photos of all nearby bandits and all criminal actions which they can make and every guest compares with this base. Now you recruites butler. He looks at you home for a week and remembers everybody who enters you home. Also he remembers what guests do in you home and in what sequence (maybe to switch on gas plate with no fire is bad idea). After learning he looks at all actions of you guests and controls that they execute all that they executed previously in strictly the same sequence. And if some action is novel (maybe you guests have never watched TV), butler consults with other butlers and allows it if in another houses it was safe.
