Embed presentation
Download to read offline




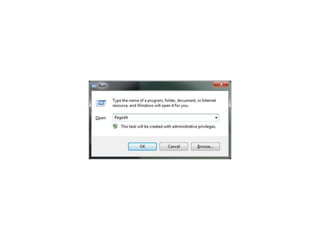









This document provides instructions to remove the Aplore malware from an infected Windows system. It involves deleting a registry entry and specific files from the Windows System directory to remove the malware and restore the system to normal functionality.























