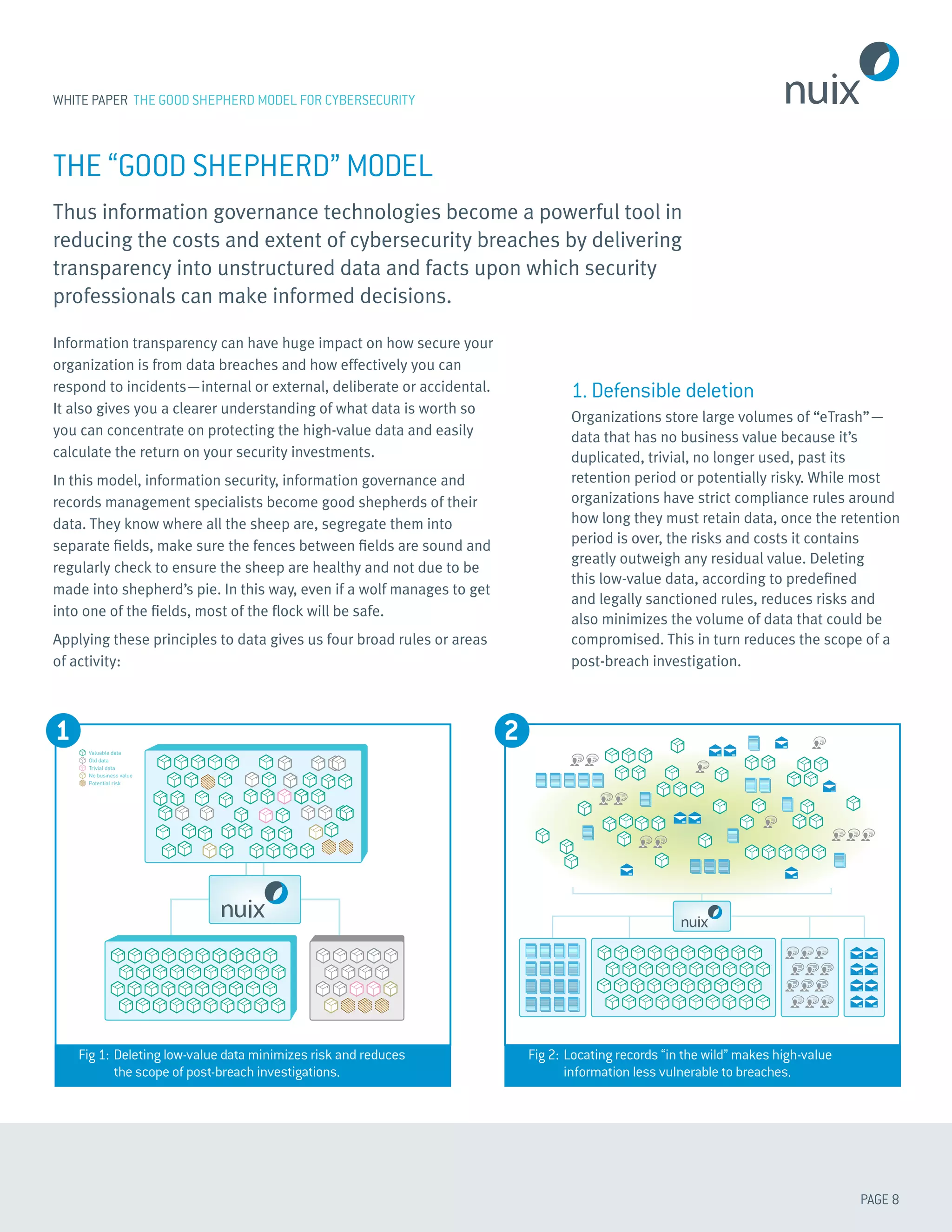
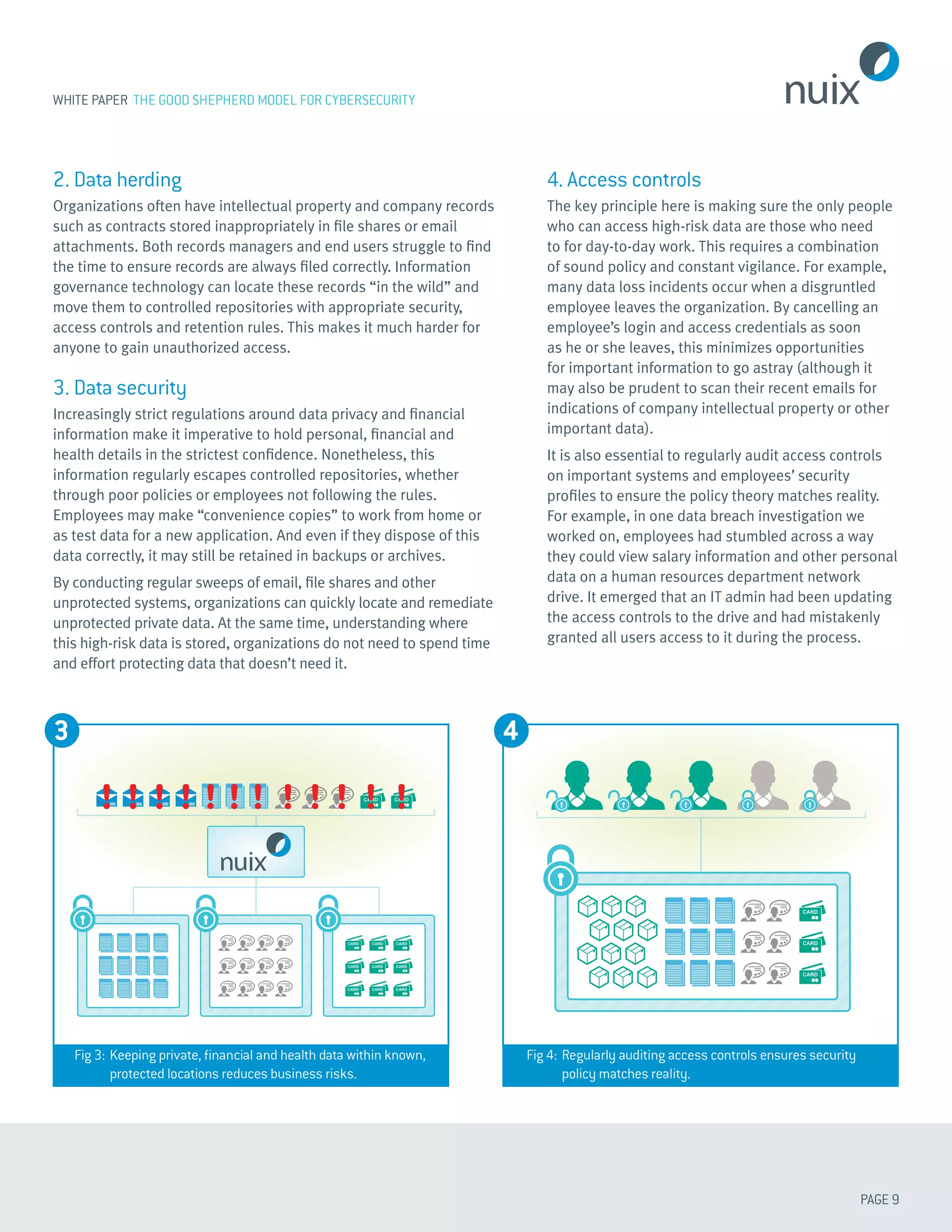
This white paper discusses adopting a "good shepherd model" for cybersecurity to minimize potential damage from data breaches. It recommends knowing where important data is stored, understanding its value, and protecting it accordingly. This involves four activities: 1) defensibly deleting low-value data to reduce investigation scope; 2) locating high-value records and moving them to secure repositories; 3) protecting high-risk private data with encryption and access controls; and 4) applying policies and audits to ensure only authorized users can access important data. Through these efforts, organizations can understand their data worth and reduce opportunities for breaches of important information.