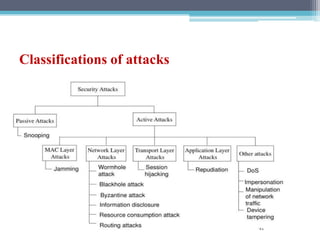
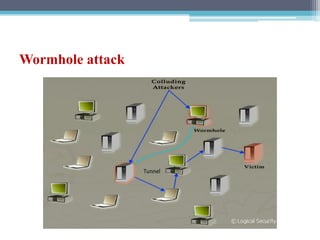
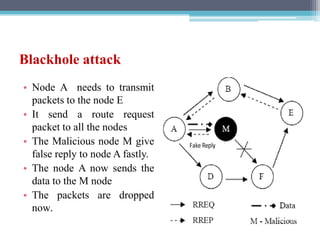
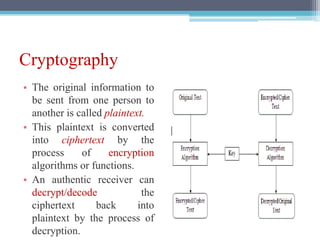
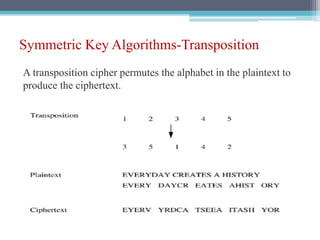
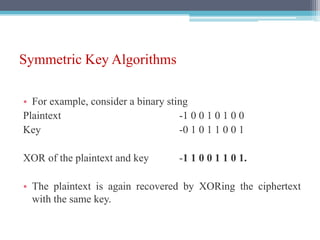
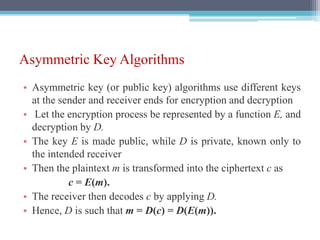
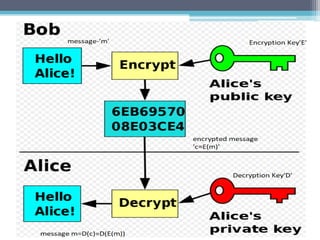
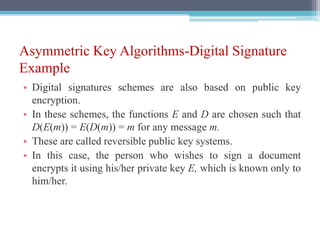
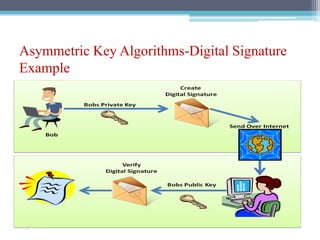
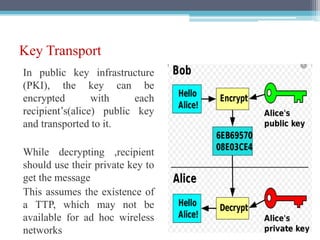
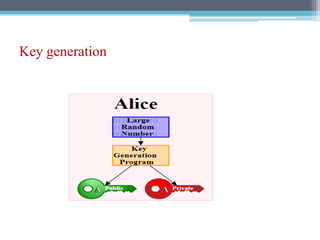
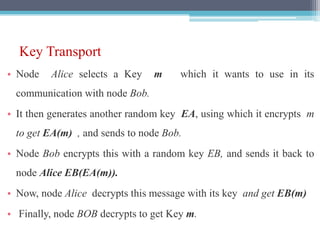
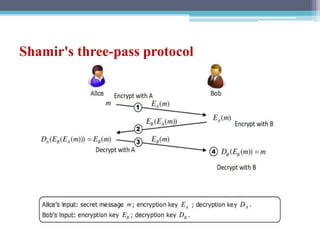
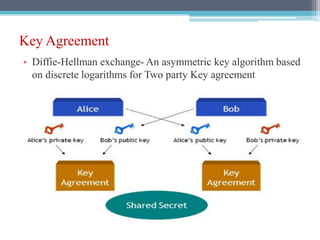
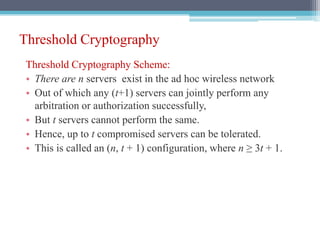
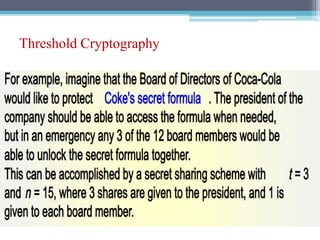
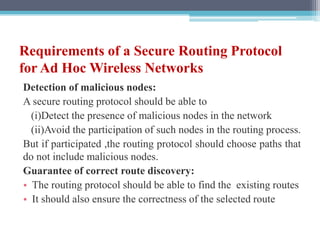
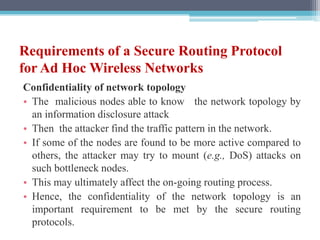
The document discusses security requirements, issues, and attacks in wireless sensor networks. It describes the key requirements of confidentiality, integrity, availability, and non-repudiation. It then outlines challenges in security provisioning due to characteristics like shared broadcast channels and lack of central authority. Various attacks are defined at the network, transport, application and multi-layers including jamming, blackhole, Byzantine, and denial of service attacks. Cryptography techniques including symmetric and asymmetric key algorithms are discussed as solutions for security provisioning.