PVS-Studio is a static code analyzer that offers over 320 diagnostics for C, C++, and more than 120 for C#. The tool has identified over 10,000 bugs across approximately 270 open-source projects, highlighting its efficacy without focusing solely on error detection. It employs advanced analysis techniques such as pattern-based analysis and symbolic execution to evaluate code quality and identify potential issues.









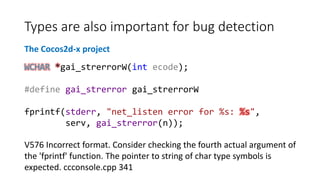
![if ((*path)[0]->e->dest->loop_father != path->last()->e->....)
{
delete_jump_thread_path (path);
e->aux = NULL;
ei_next (&ei;);
}
else
{
delete_jump_thread_path (path);
e->aux = NULL;
ei_next (&ei;);
}
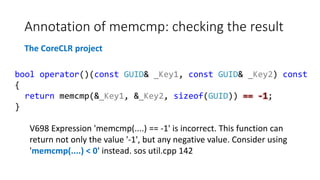
A simple case: copy-paste
The GCC Project
V523 The 'then' statement is equivalent to the 'else' statement. tree-ssa-
threadupdate.c 2596](https://image.slidesharecdn.com/ispras-2016-short-170105171218/85/The-operation-principles-of-PVS-Studio-static-code-analyzer-11-320.jpg)




![The values of variables: the size of the array,
indices
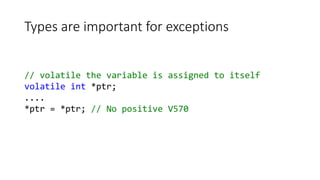
Handle<YieldTermStructure> md0Yts() {
double q6mh[] = {
0.0001,0.0001,0.0001,0.0003,0.00055,0.0009,0.0014,0.0019,
0.0025,0.0031,0.00325,0.00313,0.0031,0.00307,0.00309,
........................................................
0.02336,0.02407,0.0245 }; 60 elements
....
for(int i=0;i<10+18+37;i++) { i < 65
q6m.push_back(
boost::shared_ptr<Quote>(new SimpleQuote(q6mh[i])));
The QuantLib
project
V557 Array overrun is possible. The value of 'i' index could reach 64.
markovfunctional.cpp 176](https://image.slidesharecdn.com/ispras-2016-short-170105171218/85/The-operation-principles-of-PVS-Studio-static-code-analyzer-19-320.jpg)
![The values of variables: using conditions to
determine the range
std::string rangeTypeLabel(int idx)
{
const char* rangeTypeLabels[] = {"Self", "Touch", "Target"};
if (idx >= 0 && idx <= 3)
return rangeTypeLabels[idx];
else
return "Invalid";
}
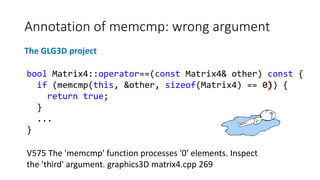
V557 Array overrun is possible. The value of 'idx' index could reach 3.
esmtool labels.cpp 502
The OpenMW project](https://image.slidesharecdn.com/ispras-2016-short-170105171218/85/The-operation-principles-of-PVS-Studio-static-code-analyzer-20-320.jpg)
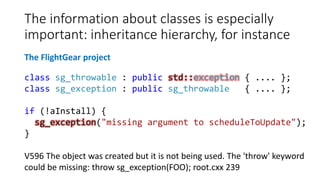
![The values of functions
static inline size_t UnboxedTypeSize(JSValueType type)
{
switch (type) {
.......
default: return 0;
}
}
Minstruction *loadUnboxedProperty(size_t offset, ....)
{
size_t index = offset / UnboxedTypeSize(unboxedType);
The Thunderbird project
V609 Divide by zero. Denominator range [0..8]. ionbuilder.cpp 10922](https://image.slidesharecdn.com/ispras-2016-short-170105171218/85/The-operation-principles-of-PVS-Studio-static-code-analyzer-21-320.jpg)