TDK_IST711
•
0 likes•49 views
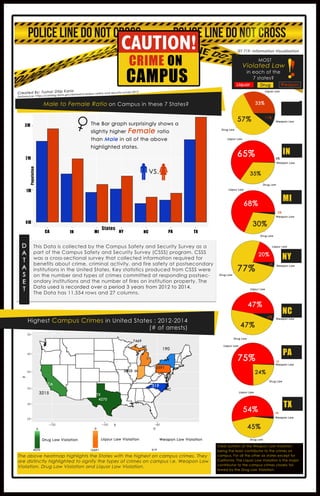
The document summarizes campus crime data collected from postsecondary institutions in the United States from 2012 to 2014. Key statistics included the number and types of crimes committed as well as fire safety information. The data showed clear patterns across states. For most states except California, liquor law violations were the major contributor to campus crimes, closely followed by drug law violations. Weapon law violations were the least common crimes reported on campus.
Report
Share
Report
Share
Download to read offline
Recommended
Using Narcotics Arrest Data To Predict Violent Crime

Research proposal for geographically weighted regression model of crime analysis.
Investigation

He was responsible for numerous police programs such as the Explosive Ordnance Detail, Critical Incident Investigations, Mobile Command Post Team, SWAT, and the Crisis Negotiations Team. In March 2012, Eric was appointed as the 49th Chief of Police for the Stockton Police Department.
Argosy psy 303 module 1 assignment 3 measures of crime new

psy 303 new,argosy psy 303 new,argosy psy 303 new complete course,argosy psy 303 new entire course,psy 303 all assignments new,argosy psy 303 new module 1,argosy psy 303 new module 2,argosy psy 303 new module 3m argosy psy 303 new module 4,argosy psy 303 new module 5,argosy psy 303 new tutorials,psy 303 new assignments,psy 303 new help
Argosy psy 303 module 1 assignment 3 measures of crime new

psy 303 module 1 assignment 2 new,psy 303 module 1 assignment 3 measures of crime new,argosy psy 303 new,psy 303 new,argosy psy 303 new module 1 tutorial,psy 303 new module 1 assignment,argosy psy 303 new module 1 help
2017 U.S. State of Cybercrime

With 74% of organizations more concerned with cybersecurity attacks than they were last year, it is important to understand the factors raising these concerns.
Crime prediction based on crime types

This paper focuses on finding spatial and temporal criminal hotspots. It analyses two different real-world crimes datasets for Denver, CO and Los Angeles, CA and provides a comparison between the two datasets through a statistical analysis supported by several graphs. Then, it clarifies how we conducted Apriori algorithm to produce interesting frequent patterns for criminal hotspots. In addition, the paper shows how we used Decision Tree classifier and Naïve Bayesian classifier in order to predict potential crime types. To further analyse crimes’ datasets, the paper introduces an analysis study by combining our findings of Denver crimes’ dataset with its demographics information in order to capture the factors that might affect the safety of neighborhoods. The results of this solution could be used to raise people’s awareness regarding the dangerous locations and to help agencies to predict future crimes in a specific location within
a particular time.
Recommended
Using Narcotics Arrest Data To Predict Violent Crime

Research proposal for geographically weighted regression model of crime analysis.
Investigation

He was responsible for numerous police programs such as the Explosive Ordnance Detail, Critical Incident Investigations, Mobile Command Post Team, SWAT, and the Crisis Negotiations Team. In March 2012, Eric was appointed as the 49th Chief of Police for the Stockton Police Department.
Argosy psy 303 module 1 assignment 3 measures of crime new

psy 303 new,argosy psy 303 new,argosy psy 303 new complete course,argosy psy 303 new entire course,psy 303 all assignments new,argosy psy 303 new module 1,argosy psy 303 new module 2,argosy psy 303 new module 3m argosy psy 303 new module 4,argosy psy 303 new module 5,argosy psy 303 new tutorials,psy 303 new assignments,psy 303 new help
Argosy psy 303 module 1 assignment 3 measures of crime new

psy 303 module 1 assignment 2 new,psy 303 module 1 assignment 3 measures of crime new,argosy psy 303 new,psy 303 new,argosy psy 303 new module 1 tutorial,psy 303 new module 1 assignment,argosy psy 303 new module 1 help
2017 U.S. State of Cybercrime

With 74% of organizations more concerned with cybersecurity attacks than they were last year, it is important to understand the factors raising these concerns.
Crime prediction based on crime types

This paper focuses on finding spatial and temporal criminal hotspots. It analyses two different real-world crimes datasets for Denver, CO and Los Angeles, CA and provides a comparison between the two datasets through a statistical analysis supported by several graphs. Then, it clarifies how we conducted Apriori algorithm to produce interesting frequent patterns for criminal hotspots. In addition, the paper shows how we used Decision Tree classifier and Naïve Bayesian classifier in order to predict potential crime types. To further analyse crimes’ datasets, the paper introduces an analysis study by combining our findings of Denver crimes’ dataset with its demographics information in order to capture the factors that might affect the safety of neighborhoods. The results of this solution could be used to raise people’s awareness regarding the dangerous locations and to help agencies to predict future crimes in a specific location within
a particular time.
What is data-driven government for public safety?

How can governments become data-driven and capitalize on the ton of valuable insight hidden in the flood of data we generate every day? Where has this already been implemented, and what are the effects? Get the big picture on public safety and incident and emergency management at http://ibm.co/saferplanet
Technical Seminar

Presentation on Big data analytics and mining for effective visualization and trends forecasting of crime data.
Cybercrime & global mapping

This paper presents suggestions for an exploratory approach to understanding cybercrime that we call “cybercartography” using a set of tools that have not been frequently applied to this domain. We refer to 1) fifty-plus years of experience by scientists and governments in integrating socioeconomic and political data organized by administrative boundaries with satellite raster and global gridded global data sets 2) gridded global models 3) global event data sets 4) centuries of experience with the art and science of cartography. To make this less abstract, consider the broad generalization that most current generation cyberthreat maps involve lots of blinking dots and network graphs superimposed over an outline or “blue marble” view of the world. Then compare some of the cartographic techniques that are often used to map other knowledge domains—for example, National Geographic-style cartography, high-resolution administrative boundary maps produced using the US census, and gridded global data sets. A deeper level of insight into the world of cybercrime can be gained in combining the standard cyberthreat network analyses with place-specific variables which can lead to greater insights into who the cybercriminals are, what makes a particular region fertile ground for these activities, why some regions are less susceptible to developing cybercriminals, and where new criminal activities are likely to spring-up and flourish. These different approaches are not superior to one another, but they can be complementary.
Crime Data Analysis and Prediction for city of Los Angeles

This is a research paper for LA county to know about the crime rate in that city.
Propose Data Mining AR-GA Model to Advance Crime analysis

http://iosrjournals.org/iosr-jce/pages/v14i5.html
Security personnel are increasingly having to think about the locati.docx

Security personnel are increasingly having to think about the location of their data in a world where data is becoming ever-more distributed. That and the concerns that organizations have about governmental and private surveillance are yet another burden these overworked folks need to shoulder. Data security looks fundamentally different to how it looked in the past. There truly are no hard parameters for data: it exists within organizational premises, in the cloud, on all manner of social media, on mobile devices of every flavor and, increasingly as we move towards the Internet of Things, on distributed sensors.
A 2014 survey of CISOs revealed data location is a huge concern. But the key question to ask is how much of the concern is related to security personnel’s hyper-sensitivity about risk, and how much is actually a reflection of a more risky environment? And this question speaks to what I believe will be the future of information security: context. For the purposes of this assignment, I classify context as location, time, type of device, type of user.
Requirements
How can user context be used to more effectively control data? Provide specific examples.
Identify at least three companies that have software that manages user context.
.
Analytics-Based Crime Prediction

As per studies conducted by the University of California, it is observed that crime in any area follows the same pattern as that of earthquake aftershocks. It is difficult to predict an earthquake, but once it happens the aftershocks following it are quite predictable. Same is true for the crimes happening in a geographical area.
Crime analysis and Prediction Crime analysis and Prediction

using data analysis and gis to predict crimes
150 words agree or disagreeThis week we discussed data mining an.docx

150 words agree or disagree
This week we discussed data mining and the various programs used as well as the goals of various organizations in regard to devoting resources to combing massive amounts of data for the proverbial "needle in the haystack". We learned about several notable examples of programs in use, to include the Signal Detection Theory (SDI), Analytic Framework for Intelligence (AFI), and the Data Analysis and Research for Trade Transparency System (DARTTS). I’ll skip the overview of each, as we have all read the lesson, but it’s safe to say no one underestimates the valuable resources these tools and methods have been to signals and intelligence analysts.
Social Networks and Link Analysis (SNA)
This link analysis has been applied recently after the burgeoning ubiquity of social media in just about every individual’s life. Link analysis is performed by mapping relations between events, and entities (Nissan, 2012). This analysis works by examining the links between events and entities, and categorizing those bonds by strength, in order to draw a picture of how strong the ties linking each event are. This is useful when trying to build a map of a terror cell or organized crime ring, allowing analysts (military, state, or even local police) to begin drawing parallels between occurrences such as types of MO used in a bank robbery, or specific engineering habits used in producing an IED. Nissan’s 2012 article even notes several such programs by name, “Crime Link”, “ORIONInvestigations”, and “Daisy”, all of which are tailored to provide visual representation of the connection between two given things.
According to the reading, one of the biggest issues in data mining was applying it to criminal activity (McCue, 2006) in a successful fashion. The framework and foundation of data mining was already there, stretching back nearly a century. The problem, however, was to meet and deal with the various restrictions put in place for law enforcement. There is no court order or legal warrant needed for a company to monitor their employee’s communications, and we all tacitly agree to such monitoring of our online behavior on social media sites and in google, but law enforcement actors, whether they be local or federal, operate under different authority than a private company.
I found the Predictive Policing theory or model to be pretty interesting. I recall watching the movie Minority Report with Tom Cruise and being really engrossed with the idea of predicting crimes before they happen. In the movie they used psychics, but we do a kind of similar thing in the real world, where departments are using proactive vs reactive policing techniques in order to curtail crime. I know that even I, a lowly patrolman, have the ability to generate calls for service reports listing type of crime and geographical area of the city, and I can use those reports to tailor my enforcement to catch more bad guys and stop more crime.
References
McCue, C. (2006.
Crime analysis mapping, intrusion detection using data mining

Crime analysis mapping, intrusion detection using data mining
Crime analysis mapping, intrusion detection using data mining

Crime analysis mapping, intrusion detection using data mining
Data Mining plays a key role in Crime Analysis. There are many different algorithms mentioned in previous research papers, among them are the virtual identifier, pruning strategy, support vector machines, and apriori algorithms. VID is to find relation between record and vid. The apriori algorithm helps the fuzzy association rules algorithm and it takes around six hundred seconds to detect a mail bomb attack. In this research paper, we identified Crime mapping analysis based on KNN (K – Nearest Neighbor) and ANN (Artificial Neural Network) algorithms to simplify this process. Crime Mapping is conducted and Funded by the Office of Community Oriented Policing Services (COPS). Evidence based research helps in analyzing the crimes. We calculate the crime rate based on the previous data using data mining techniques. Crime Analysis uses quantitative and qualitative data in combination with analytic techniques in resolving the cases. For public safety purposes, the crime mapping is an essential research area to concentrate on. We can identity the most frequently crime occurring zones with the help of data mining techniques. In Crime Analysis Mapping, we follow the following steps in order to reduce the crime rate: 1) Collect crime data 2) Group data 3) Clustering 4) Forecasting the data. Crime Analysis with crime mapping helps in understanding the concepts and practice of Crime Analysis in assisting police and helps in reduction and prevention of crimes and crime disorders.
Scared About Supply Chain Cybersecurity? 5 Reasons You Aren't Scared Enough

Many organizations and supply chain experts are concerned about cyber security. The risks stemming from supply chain cyber threats are real. In fact, the danger is more frightening and potentially harmful than we realize. Here’s why.
The International Journal of Engineering and Science (IJES)

The International Journal of Engineering & Science is aimed at providing a platform for researchers, engineers, scientists, or educators to publish their original research results, to exchange new ideas, to disseminate information in innovative designs, engineering experiences and technological skills. It is also the Journal's objective to promote engineering and technology education. All papers submitted to the Journal will be blind peer-reviewed. Only original articles will be published.
Written Response Submission FormYour Name First and last.docx

Written Response Submission Form
Your Name: First and last
Your E-Mail Address: Your e-mail hereInstructions
Write your responses where it reads “Enter your response here....” Write as much as needed to satisfy the requirements indicated. Each item contains the Rubric that will be used to evaluate your responses.
At the end of the template, you will list the references you used to support your responses.
Item 1
Examine the past 10 years of crime data in the Uniform Crime Report (UCR) and the National Crime Victimization Survey (NCVS). Identify three crime trends from the data (2–4 paragraphs).Your Response
Enter your response here.Rubric
013
Failing
1415
Needs Improvement
1620
Meets Expectations
Sub-Competency 1: Analyze crime and victimization data
Identify three trends in crime from the past 10 years of UCR and NCVS data.
Response is missing.
Response describes fewer than three trends, or the description of trends contains inaccuracies or is vague.
Response includes a clear explanation of three crime/victimization trends from the past decade identified from the UCR and/or NCVS databases.
Item 2
What are the strengths and weaknesses of each data source (the UCR and NCVS databases)? Consider their accuracy, coverage, applicability, collection methods, and any other characteristic you think is important to consider. Explain at least two strengths and two weaknesses of the databases (2–3 paragraphs).
Your Response
Enter your response here.Rubric
013
Failing
1415
Needs Improvement
1620
Meets Expectations
Sub-Competency 2: Assess strengths and weaknesses of criminological data sources.
Explain two strengths of the UCR and/or NCVS databases.
Response is missing.
Response is vague, lacking detail, or contains inaccuracies.
Response provides an explanation of at least two strengths of the databases. The explanation demonstrates thorough consideration of research design, collection techniques, dissemination strategies, and applicability within the field.
Explain two weaknesses of the UCR and/or NCVS databases.
Response is missing.
Response is vague, lacking detail, or contains inaccuracies.
Response provides an explanation of at least two weaknesses of the databases. The explanation demonstrates thorough consideration of research design, collection techniques, dissemination strategies, and applicability within the field.
Item 3
What criminological explanations for your identified crime trends can be derived from the UCR and/or NCVS databases? Describe at least two. Then provide an argument for other factors and variables (biological, social, structural, economic, etc.) that cause or influence your identified crime trends that are not present in the UCR/NCVS data. Reference theoretical and scholarly resources that support your criminological explanations (3–5 paragraphs).
Your Response
Enter your response here.Rubric
013
Failing
1415
Needs Improvement
1620
Meets Expectations
Sub-Competency 3: Assess correlative and causative relation ...
San Francisco Crime Prediction Report

Predict the category of crime in a particular location on analyzing the input variables such as latitude, longitude, date, day and location.
A REVIEW OF CYBERSECURITY AS AN EFFECTIVE TOOL FOR FIGHTING IDENTITY THEFT AC...

The study is focused on identity theft and cybersecurity in United States. Hence, the study is aimed at examining the impact of cybersecurity on identity theft in United States using a time series data which covers the period between 2001 and 2021. Trend analysis of complaints of identity theft and cybersecurity over the years was conducted; also, the nature of relationship between the two variables was established. Chi-Square analysis was used to examine the impact of cybersecurity on identity theft in United States. Line graphs were used to analyze the trend in the variable. Time series data was used in the study and the data was obtained from secondary sources; Statista.com, US Federal Trade Commission, Insurance Information Institute and Identitytheft.org. Result from the study revealed that consumers’ complaints on identity theft were on the increase every year. Total spending of the economy (both private and public
sector) on cybersecurity was on continuous increase over the years. More than 100% of spending in 2010 as incurred in 2018. The Chi-Square analysis revealed that cybersecurity does not have significant impact on identity theft. The study recommended that the government increase the level of public awareness to ensure that members of the public protect their personal and other information to ensure that they are not compromised for fraud or identity theft. Organizations also need to invest more in the security system and develop policies that will support the security system. At the country level, international treaties and collaboration should be encouraged to prosecute the fraudsters hiding behind national borders.
More Related Content
Similar to TDK_IST711
What is data-driven government for public safety?

How can governments become data-driven and capitalize on the ton of valuable insight hidden in the flood of data we generate every day? Where has this already been implemented, and what are the effects? Get the big picture on public safety and incident and emergency management at http://ibm.co/saferplanet
Technical Seminar

Presentation on Big data analytics and mining for effective visualization and trends forecasting of crime data.
Cybercrime & global mapping

This paper presents suggestions for an exploratory approach to understanding cybercrime that we call “cybercartography” using a set of tools that have not been frequently applied to this domain. We refer to 1) fifty-plus years of experience by scientists and governments in integrating socioeconomic and political data organized by administrative boundaries with satellite raster and global gridded global data sets 2) gridded global models 3) global event data sets 4) centuries of experience with the art and science of cartography. To make this less abstract, consider the broad generalization that most current generation cyberthreat maps involve lots of blinking dots and network graphs superimposed over an outline or “blue marble” view of the world. Then compare some of the cartographic techniques that are often used to map other knowledge domains—for example, National Geographic-style cartography, high-resolution administrative boundary maps produced using the US census, and gridded global data sets. A deeper level of insight into the world of cybercrime can be gained in combining the standard cyberthreat network analyses with place-specific variables which can lead to greater insights into who the cybercriminals are, what makes a particular region fertile ground for these activities, why some regions are less susceptible to developing cybercriminals, and where new criminal activities are likely to spring-up and flourish. These different approaches are not superior to one another, but they can be complementary.
Crime Data Analysis and Prediction for city of Los Angeles

This is a research paper for LA county to know about the crime rate in that city.
Propose Data Mining AR-GA Model to Advance Crime analysis

http://iosrjournals.org/iosr-jce/pages/v14i5.html
Security personnel are increasingly having to think about the locati.docx

Security personnel are increasingly having to think about the location of their data in a world where data is becoming ever-more distributed. That and the concerns that organizations have about governmental and private surveillance are yet another burden these overworked folks need to shoulder. Data security looks fundamentally different to how it looked in the past. There truly are no hard parameters for data: it exists within organizational premises, in the cloud, on all manner of social media, on mobile devices of every flavor and, increasingly as we move towards the Internet of Things, on distributed sensors.
A 2014 survey of CISOs revealed data location is a huge concern. But the key question to ask is how much of the concern is related to security personnel’s hyper-sensitivity about risk, and how much is actually a reflection of a more risky environment? And this question speaks to what I believe will be the future of information security: context. For the purposes of this assignment, I classify context as location, time, type of device, type of user.
Requirements
How can user context be used to more effectively control data? Provide specific examples.
Identify at least three companies that have software that manages user context.
.
Analytics-Based Crime Prediction

As per studies conducted by the University of California, it is observed that crime in any area follows the same pattern as that of earthquake aftershocks. It is difficult to predict an earthquake, but once it happens the aftershocks following it are quite predictable. Same is true for the crimes happening in a geographical area.
Crime analysis and Prediction Crime analysis and Prediction

using data analysis and gis to predict crimes
150 words agree or disagreeThis week we discussed data mining an.docx

150 words agree or disagree
This week we discussed data mining and the various programs used as well as the goals of various organizations in regard to devoting resources to combing massive amounts of data for the proverbial "needle in the haystack". We learned about several notable examples of programs in use, to include the Signal Detection Theory (SDI), Analytic Framework for Intelligence (AFI), and the Data Analysis and Research for Trade Transparency System (DARTTS). I’ll skip the overview of each, as we have all read the lesson, but it’s safe to say no one underestimates the valuable resources these tools and methods have been to signals and intelligence analysts.
Social Networks and Link Analysis (SNA)
This link analysis has been applied recently after the burgeoning ubiquity of social media in just about every individual’s life. Link analysis is performed by mapping relations between events, and entities (Nissan, 2012). This analysis works by examining the links between events and entities, and categorizing those bonds by strength, in order to draw a picture of how strong the ties linking each event are. This is useful when trying to build a map of a terror cell or organized crime ring, allowing analysts (military, state, or even local police) to begin drawing parallels between occurrences such as types of MO used in a bank robbery, or specific engineering habits used in producing an IED. Nissan’s 2012 article even notes several such programs by name, “Crime Link”, “ORIONInvestigations”, and “Daisy”, all of which are tailored to provide visual representation of the connection between two given things.
According to the reading, one of the biggest issues in data mining was applying it to criminal activity (McCue, 2006) in a successful fashion. The framework and foundation of data mining was already there, stretching back nearly a century. The problem, however, was to meet and deal with the various restrictions put in place for law enforcement. There is no court order or legal warrant needed for a company to monitor their employee’s communications, and we all tacitly agree to such monitoring of our online behavior on social media sites and in google, but law enforcement actors, whether they be local or federal, operate under different authority than a private company.
I found the Predictive Policing theory or model to be pretty interesting. I recall watching the movie Minority Report with Tom Cruise and being really engrossed with the idea of predicting crimes before they happen. In the movie they used psychics, but we do a kind of similar thing in the real world, where departments are using proactive vs reactive policing techniques in order to curtail crime. I know that even I, a lowly patrolman, have the ability to generate calls for service reports listing type of crime and geographical area of the city, and I can use those reports to tailor my enforcement to catch more bad guys and stop more crime.
References
McCue, C. (2006.
Crime analysis mapping, intrusion detection using data mining

Crime analysis mapping, intrusion detection using data mining
Crime analysis mapping, intrusion detection using data mining

Crime analysis mapping, intrusion detection using data mining
Data Mining plays a key role in Crime Analysis. There are many different algorithms mentioned in previous research papers, among them are the virtual identifier, pruning strategy, support vector machines, and apriori algorithms. VID is to find relation between record and vid. The apriori algorithm helps the fuzzy association rules algorithm and it takes around six hundred seconds to detect a mail bomb attack. In this research paper, we identified Crime mapping analysis based on KNN (K – Nearest Neighbor) and ANN (Artificial Neural Network) algorithms to simplify this process. Crime Mapping is conducted and Funded by the Office of Community Oriented Policing Services (COPS). Evidence based research helps in analyzing the crimes. We calculate the crime rate based on the previous data using data mining techniques. Crime Analysis uses quantitative and qualitative data in combination with analytic techniques in resolving the cases. For public safety purposes, the crime mapping is an essential research area to concentrate on. We can identity the most frequently crime occurring zones with the help of data mining techniques. In Crime Analysis Mapping, we follow the following steps in order to reduce the crime rate: 1) Collect crime data 2) Group data 3) Clustering 4) Forecasting the data. Crime Analysis with crime mapping helps in understanding the concepts and practice of Crime Analysis in assisting police and helps in reduction and prevention of crimes and crime disorders.
Scared About Supply Chain Cybersecurity? 5 Reasons You Aren't Scared Enough

Many organizations and supply chain experts are concerned about cyber security. The risks stemming from supply chain cyber threats are real. In fact, the danger is more frightening and potentially harmful than we realize. Here’s why.
The International Journal of Engineering and Science (IJES)

The International Journal of Engineering & Science is aimed at providing a platform for researchers, engineers, scientists, or educators to publish their original research results, to exchange new ideas, to disseminate information in innovative designs, engineering experiences and technological skills. It is also the Journal's objective to promote engineering and technology education. All papers submitted to the Journal will be blind peer-reviewed. Only original articles will be published.
Written Response Submission FormYour Name First and last.docx

Written Response Submission Form
Your Name: First and last
Your E-Mail Address: Your e-mail hereInstructions
Write your responses where it reads “Enter your response here....” Write as much as needed to satisfy the requirements indicated. Each item contains the Rubric that will be used to evaluate your responses.
At the end of the template, you will list the references you used to support your responses.
Item 1
Examine the past 10 years of crime data in the Uniform Crime Report (UCR) and the National Crime Victimization Survey (NCVS). Identify three crime trends from the data (2–4 paragraphs).Your Response
Enter your response here.Rubric
013
Failing
1415
Needs Improvement
1620
Meets Expectations
Sub-Competency 1: Analyze crime and victimization data
Identify three trends in crime from the past 10 years of UCR and NCVS data.
Response is missing.
Response describes fewer than three trends, or the description of trends contains inaccuracies or is vague.
Response includes a clear explanation of three crime/victimization trends from the past decade identified from the UCR and/or NCVS databases.
Item 2
What are the strengths and weaknesses of each data source (the UCR and NCVS databases)? Consider their accuracy, coverage, applicability, collection methods, and any other characteristic you think is important to consider. Explain at least two strengths and two weaknesses of the databases (2–3 paragraphs).
Your Response
Enter your response here.Rubric
013
Failing
1415
Needs Improvement
1620
Meets Expectations
Sub-Competency 2: Assess strengths and weaknesses of criminological data sources.
Explain two strengths of the UCR and/or NCVS databases.
Response is missing.
Response is vague, lacking detail, or contains inaccuracies.
Response provides an explanation of at least two strengths of the databases. The explanation demonstrates thorough consideration of research design, collection techniques, dissemination strategies, and applicability within the field.
Explain two weaknesses of the UCR and/or NCVS databases.
Response is missing.
Response is vague, lacking detail, or contains inaccuracies.
Response provides an explanation of at least two weaknesses of the databases. The explanation demonstrates thorough consideration of research design, collection techniques, dissemination strategies, and applicability within the field.
Item 3
What criminological explanations for your identified crime trends can be derived from the UCR and/or NCVS databases? Describe at least two. Then provide an argument for other factors and variables (biological, social, structural, economic, etc.) that cause or influence your identified crime trends that are not present in the UCR/NCVS data. Reference theoretical and scholarly resources that support your criminological explanations (3–5 paragraphs).
Your Response
Enter your response here.Rubric
013
Failing
1415
Needs Improvement
1620
Meets Expectations
Sub-Competency 3: Assess correlative and causative relation ...
San Francisco Crime Prediction Report

Predict the category of crime in a particular location on analyzing the input variables such as latitude, longitude, date, day and location.
A REVIEW OF CYBERSECURITY AS AN EFFECTIVE TOOL FOR FIGHTING IDENTITY THEFT AC...

The study is focused on identity theft and cybersecurity in United States. Hence, the study is aimed at examining the impact of cybersecurity on identity theft in United States using a time series data which covers the period between 2001 and 2021. Trend analysis of complaints of identity theft and cybersecurity over the years was conducted; also, the nature of relationship between the two variables was established. Chi-Square analysis was used to examine the impact of cybersecurity on identity theft in United States. Line graphs were used to analyze the trend in the variable. Time series data was used in the study and the data was obtained from secondary sources; Statista.com, US Federal Trade Commission, Insurance Information Institute and Identitytheft.org. Result from the study revealed that consumers’ complaints on identity theft were on the increase every year. Total spending of the economy (both private and public
sector) on cybersecurity was on continuous increase over the years. More than 100% of spending in 2010 as incurred in 2018. The Chi-Square analysis revealed that cybersecurity does not have significant impact on identity theft. The study recommended that the government increase the level of public awareness to ensure that members of the public protect their personal and other information to ensure that they are not compromised for fraud or identity theft. Organizations also need to invest more in the security system and develop policies that will support the security system. At the country level, international treaties and collaboration should be encouraged to prosecute the fraudsters hiding behind national borders.
Similar to TDK_IST711 (20)
Crime Data Analysis and Prediction for city of Los Angeles

Crime Data Analysis and Prediction for city of Los Angeles
Propose Data Mining AR-GA Model to Advance Crime analysis

Propose Data Mining AR-GA Model to Advance Crime analysis
PA-Consulting-Group_Cybercrime-Tipping-point-survey-report

PA-Consulting-Group_Cybercrime-Tipping-point-survey-report
Security personnel are increasingly having to think about the locati.docx

Security personnel are increasingly having to think about the locati.docx
Crime analysis and Prediction Crime analysis and Prediction

Crime analysis and Prediction Crime analysis and Prediction
150 words agree or disagreeThis week we discussed data mining an.docx

150 words agree or disagreeThis week we discussed data mining an.docx
Crime analysis mapping, intrusion detection using data mining

Crime analysis mapping, intrusion detection using data mining
Crime analysis mapping, intrusion detection using data mining

Crime analysis mapping, intrusion detection using data mining
Scared About Supply Chain Cybersecurity? 5 Reasons You Aren't Scared Enough

Scared About Supply Chain Cybersecurity? 5 Reasons You Aren't Scared Enough
San Francisco Crime Analysis Classification Kaggle contest

San Francisco Crime Analysis Classification Kaggle contest
The International Journal of Engineering and Science (IJES)

The International Journal of Engineering and Science (IJES)
Written Response Submission FormYour Name First and last.docx

Written Response Submission FormYour Name First and last.docx
A REVIEW OF CYBERSECURITY AS AN EFFECTIVE TOOL FOR FIGHTING IDENTITY THEFT AC...

A REVIEW OF CYBERSECURITY AS AN EFFECTIVE TOOL FOR FIGHTING IDENTITY THEFT AC...
TDK_IST711
- 1. CRIMEON CAMPUS States Population HighestCampusCrimesinUnitedStates:2012-2014 (#ofarrests) ThisDataiscollectedbytheCampusSafetyandSecuritySurveyasa partoftheCampusSafetyandSecuritySurvey(CSSS)program.CSSS wasacross-sectionalsurveythatcollectedinformationrequiredfor benefitsaboutcrime,criminalactivity,andfiresafetyatpostsecondary institutionsintheUnitedStates.Keystatisticsproducedfrom CSSSwere onthenumberandtypesofcrimescommittedatrespondingpostsec- ondaryinstitutionsandthenumberoffiresoninstitutionproperty.The Datausedisrecordedoveraperiod3yearsfrom 2012to2014.Datausedisrecordedoveraperiod3yearsfrom 2012to2014. TheDatahas11,554rowsand27columns. CA NYIN MI NC PA TX IN MI NY PA TX ClearpatternoftheWeaponLaw Violation beingtheleastcontributortothecrimeson campus.Foralltheothersixstatesexceptfor California.TheLiquorLaw Violationisthemajor contributortothecampuscrimescloselyfol- lowedbytheDrugLaw Violation. NC !!