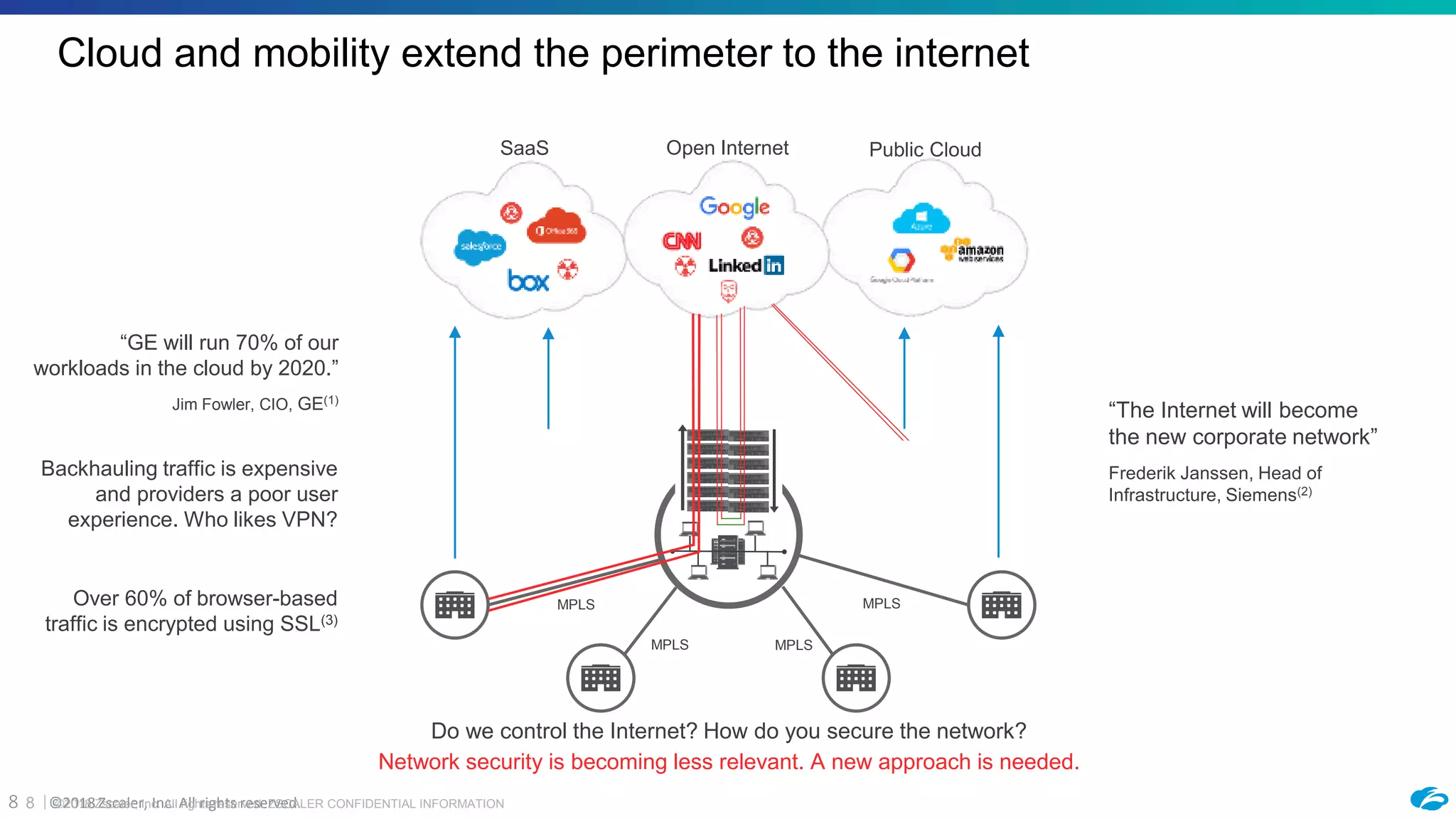
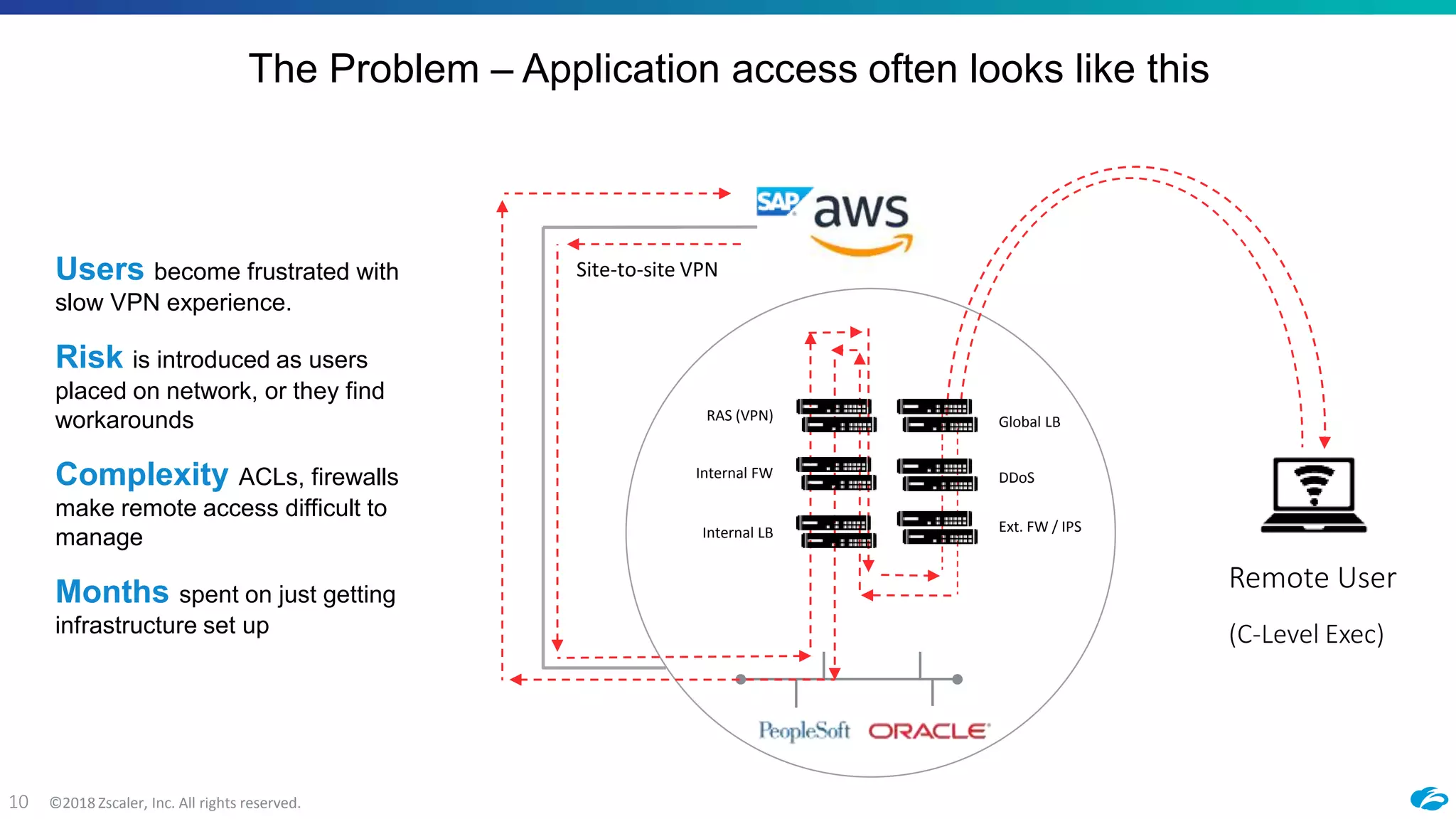
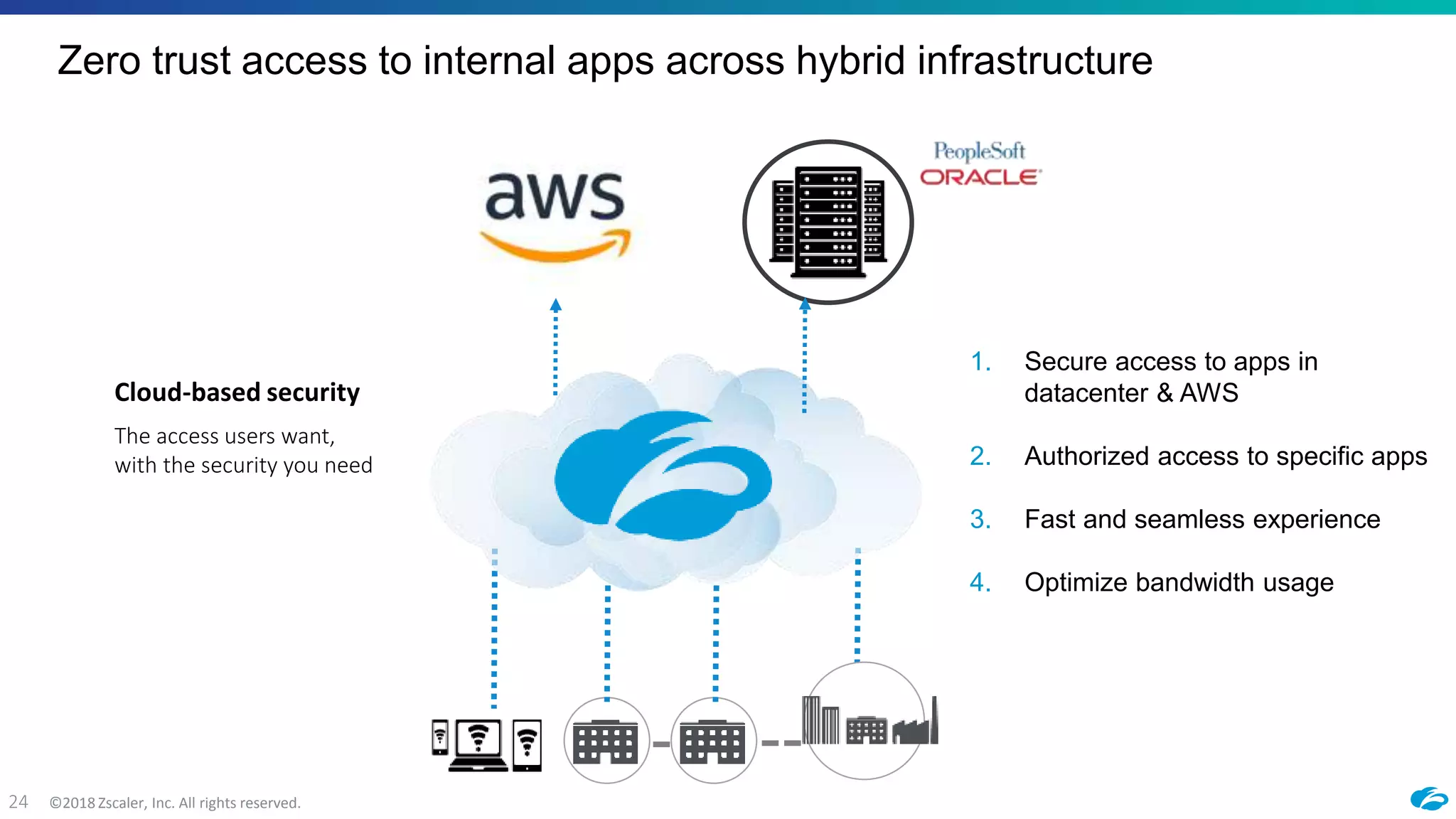
1) The document discusses Zscaler's cloud-based platform for providing secure access to applications in AWS and hybrid cloud environments. It outlines how Zscaler Private Access (ZPA) implements a zero-trust network architecture by brokering secure connections between users and applications without placing users on the internal network.
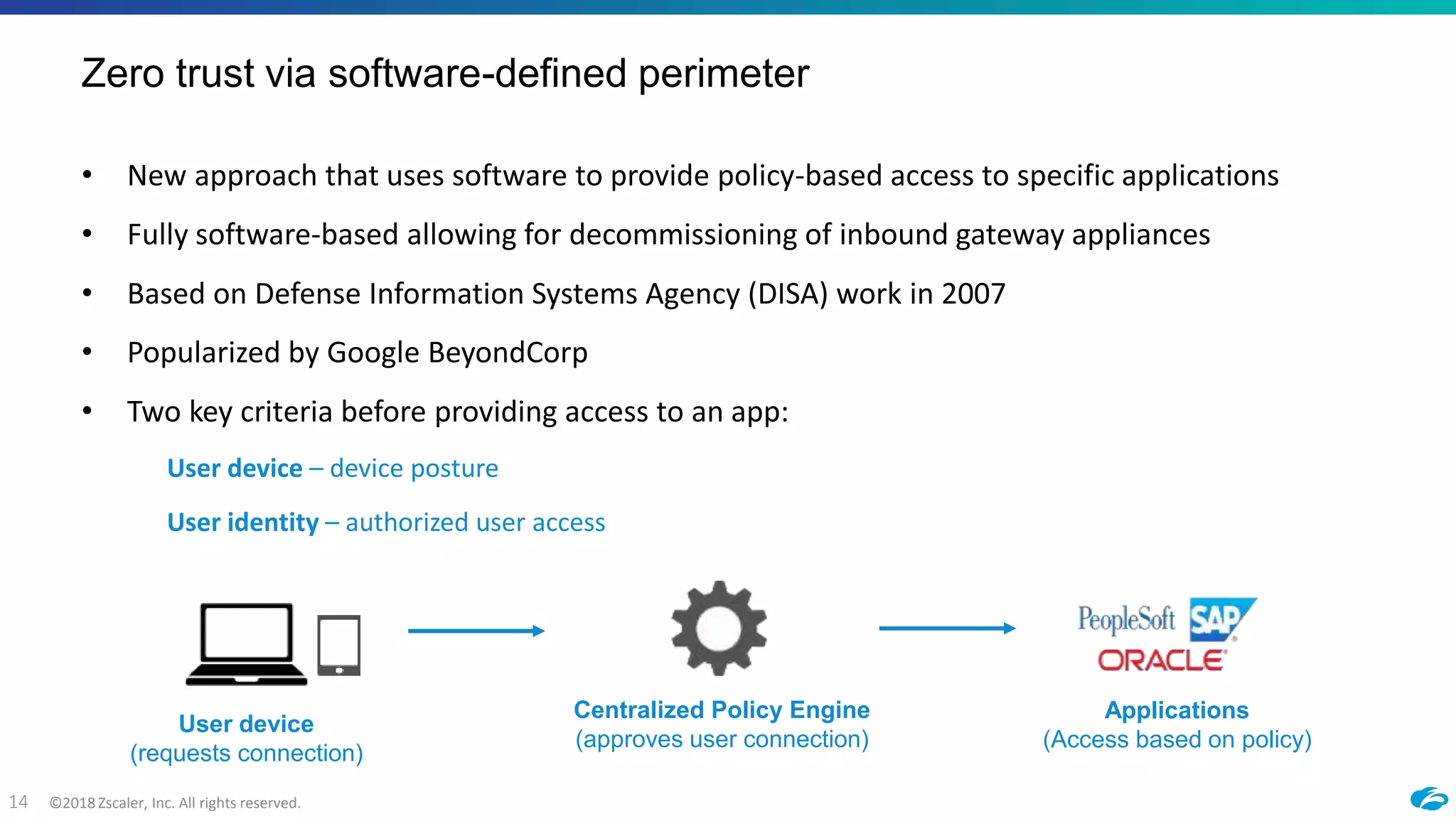
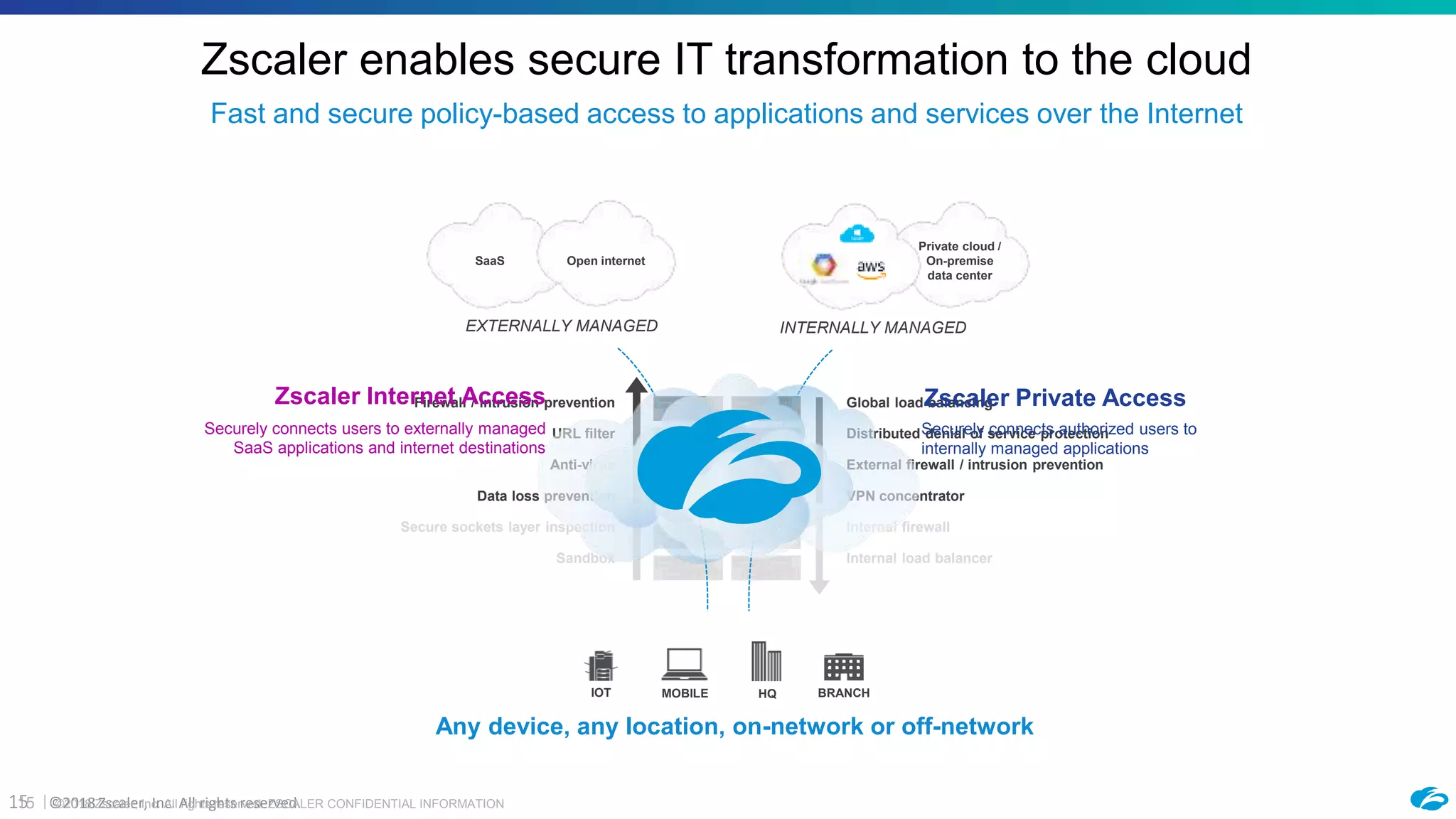
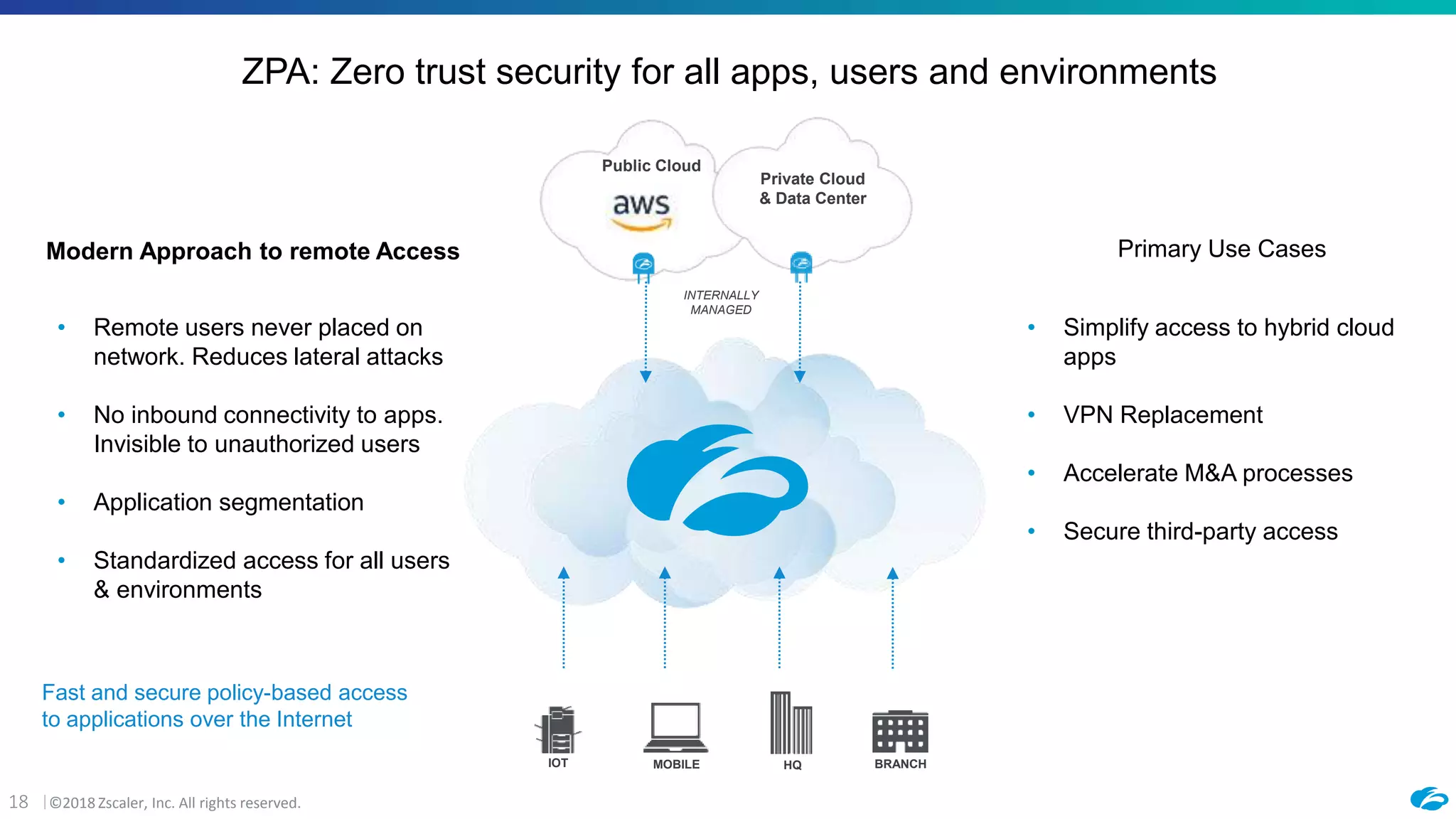
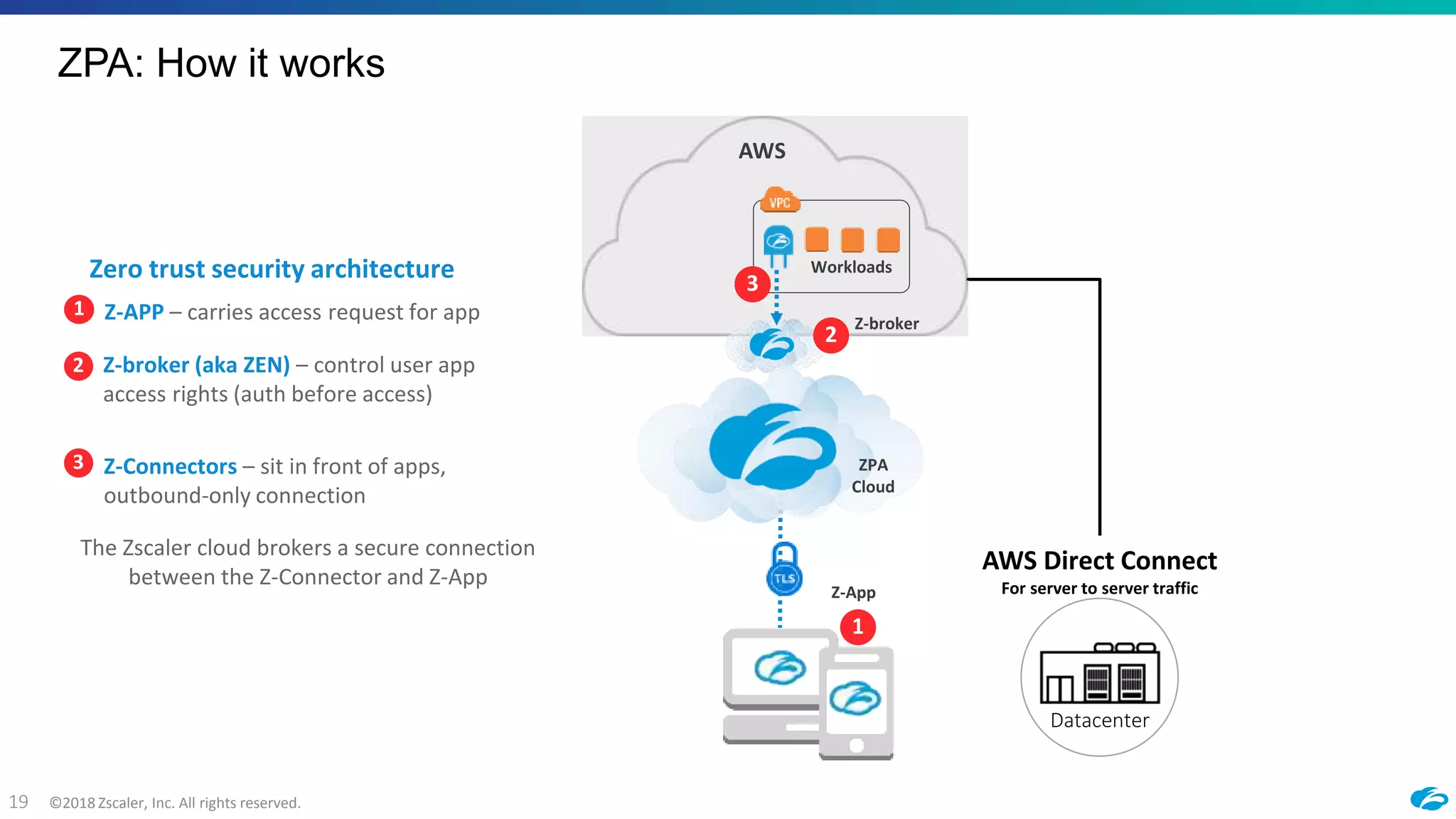
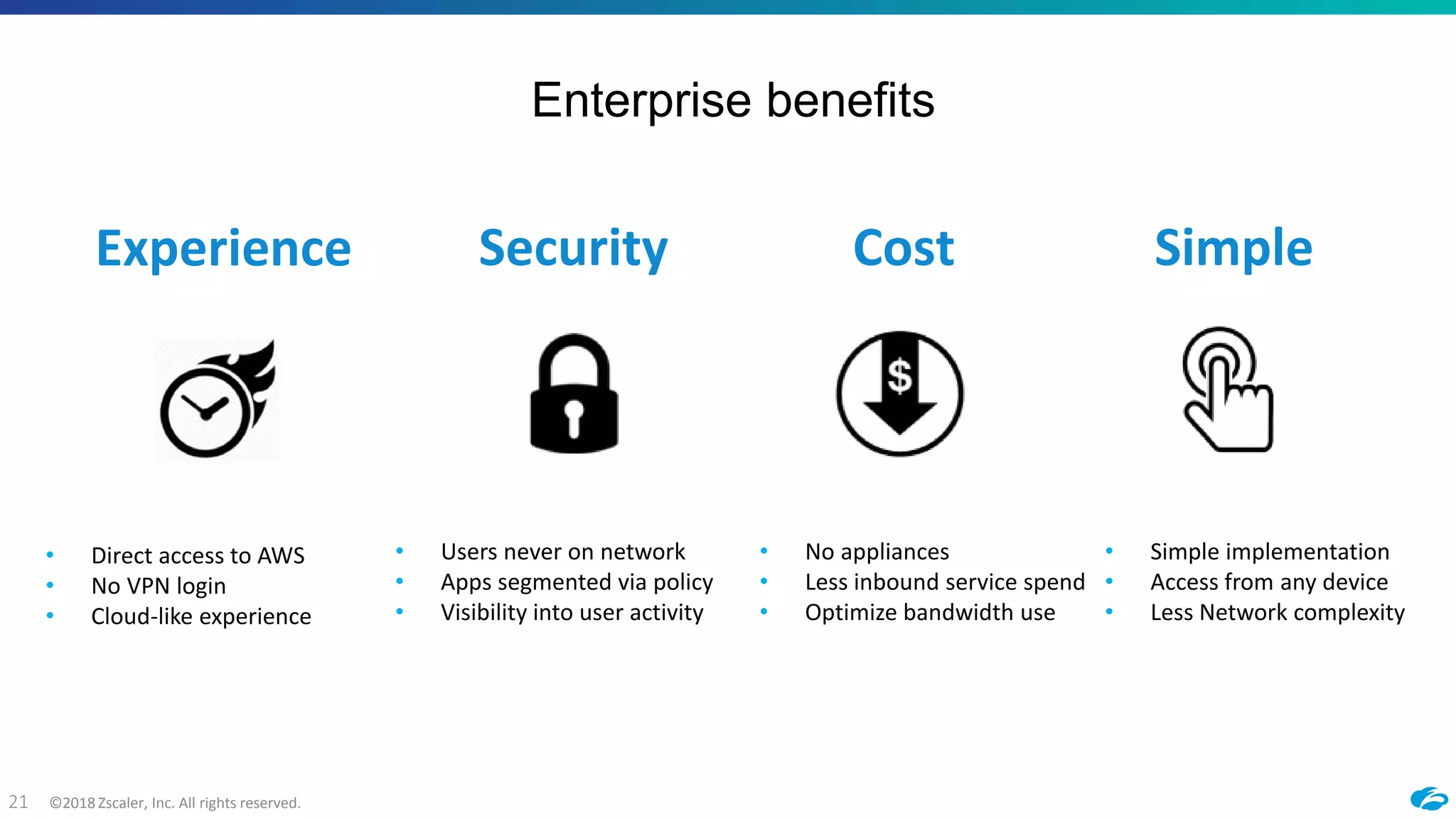
2) ZPA provides policy-based access to internally managed applications using software-defined perimeters rather than traditional VPNs. It segments applications and enforces security policies through the Zscaler cloud.
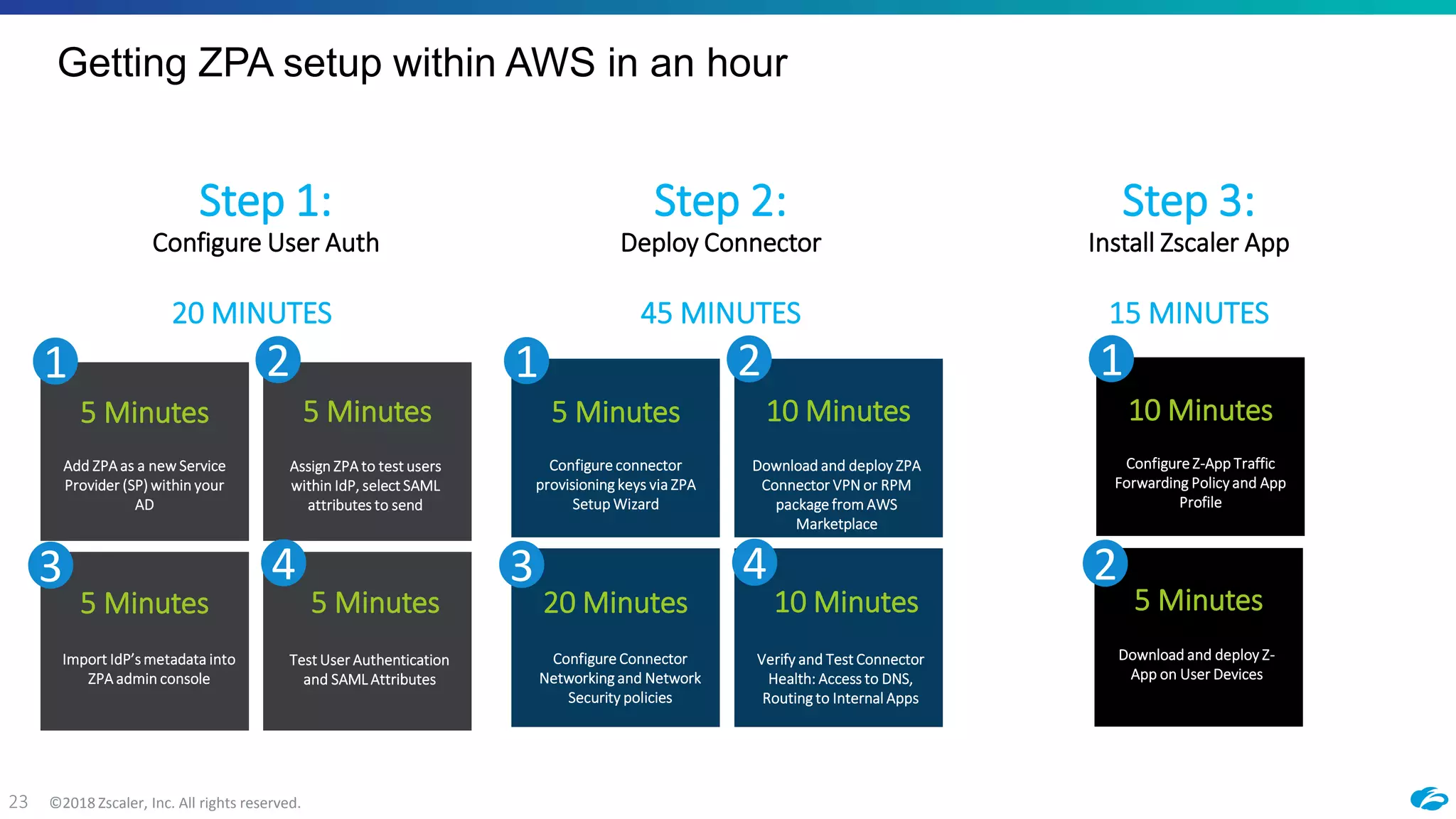
3) The document provides an example workflow showing how ZPA can be configured to enable secure access to migrated applications in AWS within an hour, without requiring inbound connectivity or remote access to internal networks.