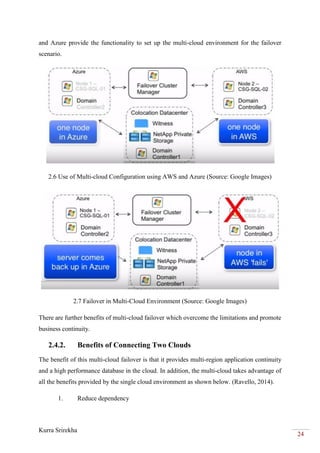
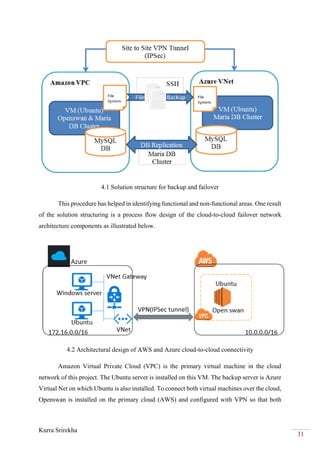
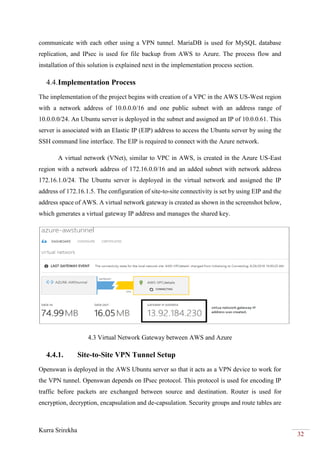
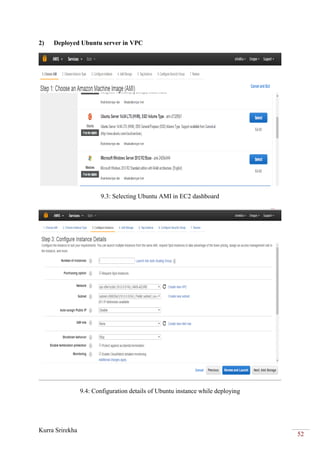
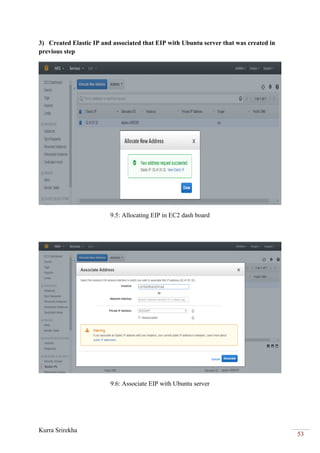
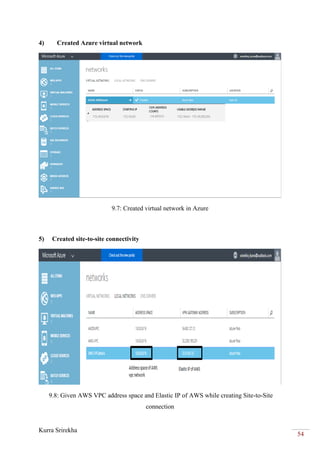
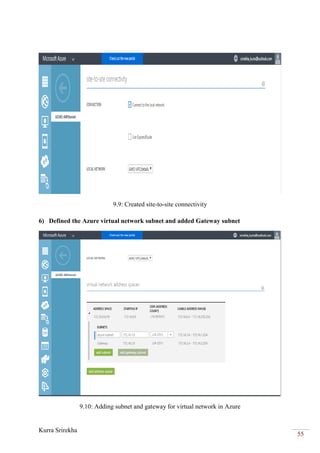
This project bridges the Amazon Web Services (AWS) cloud platform with the Microsoft Azure cloud platform using a virtual private network (VPN) to provide backup and failover capabilities. The objectives are to create a VPN tunnel between a virtual private cloud hosted in AWS and a virtual network in Azure, deploy virtual machines in both clouds, and establish database and file replication between the clouds. This will allow workloads and data to failover automatically from one cloud to the other in the event of an outage, providing high availability and business continuity.



























![Kurra Srirekha
34
After the deployment of the MariaDB cluster, a configuration file called “my.config”
is changed on each virtual machine with wsrep configuration options so that the MariaDB
cluster understands the endpoints for communication. In addition to this change, the
configuration file is changed for the VSRep option to provide the IP address and related details
of the other VM. Hence in the AWS VM, the IP address of Azure is provided and vice versa,
so that MariaDB acts as a mediator for replication between the two clouds. To configure VSRep
under the [mysqld] directory on each node, the “my.config” file is changed with their particular
hostnames, IP address and root passwords.
4.3 Configuration for wsrep Option in my.config
4.4 Configuration for VSRep Option in my.config
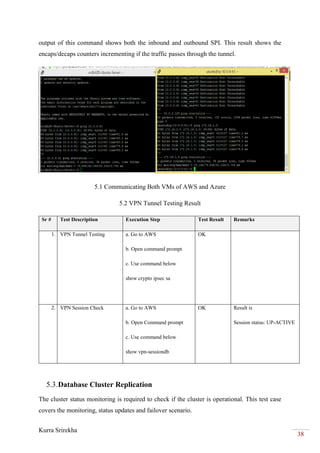
The configuration is completed successfully, and hence the bi-directional replication of
MySQL DB is initiated using the MariaDB cluster.
4.4.3. SSH Keys and SCP Command (File System Backup)](https://image.slidesharecdn.com/146ec863-4913-4c64-8fc3-2ab9cc80e787-161101074316/85/Sri-PRJ702-Project-Report-35-320.jpg)



![Kurra Srirekha
41
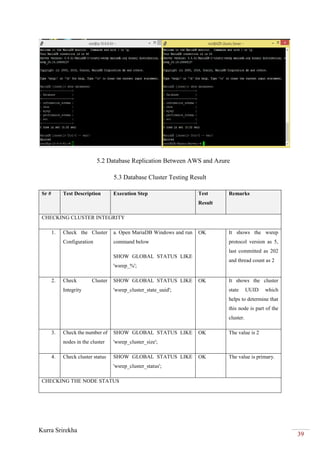
11. Check if database is
failed over
AWS database should be down and
Azure database should be up and
acting as primary
OK Azure database is
showing as primary
5.4.AWS-AZURE: Inter-Cloud Transfer (file transfers between two
clouds)
SSH and SCP are used for the file transfer between two VMs for backup and restore purposes
in the case of cloud failure. SSH is the general protocol, and SCP is the Linux SSH client
command. Hence this covers the test cases and results of file transfer scenarios as shown in the
table below.
5.3 File Transferring Between AWS and Azure
5.4 Cloud-to-Cloud Backup Testing Result
Sr # Test
Description
Execution Step Test
Result
Remarks
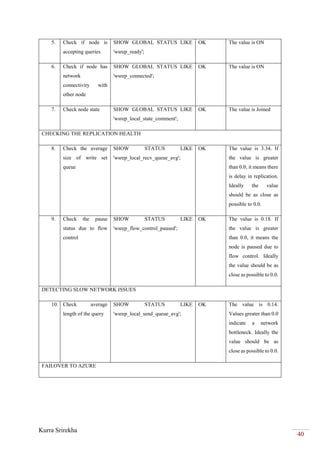
1. Check all SSH
connected
sessions
[root@router~]# netstat -tnpa | grep 'ESTABLISHED.
*sshd'
OK It shows two IP
addresses as
established with
SSH
2. Check if SSH
service is
running
sudo service ssh start OK](https://image.slidesharecdn.com/146ec863-4913-4c64-8fc3-2ab9cc80e787-161101074316/85/Sri-PRJ702-Project-Report-42-320.jpg)
![Kurra Srirekha
42
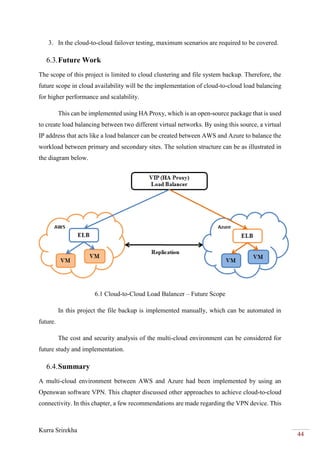
3. Check if SCP
is transferring
file through
SSH
[virtual machine ~]$ scp examplefile
yourusername@yourserver:/home/yourusername/
OK The file is
copied to the
virtual machine
correctly.
5.5.Results Evaluation
During this testing procedure, there are some important evaluations needed of the test results.
This testing is carried out to make sure the defined objectives are tested as part of this project
implementation. The evaluation is performed on two major test conditions as described next.
5.5.1. AWS-AZURE Failover
The failover is performed using the MariaDB cluster. The database on AWS is failed manually,
and it is evaluated that it immediately fails over to Azure. Because both databases are in sync
with the help of replication services, there was no outage, and hence they provided 100%
availability of the data. This testing is important for the mission-critical businesses that are
dependent on cloud computing.
5.5.2. AWS-AZURE Backup
For the AWS-to-Azure backup, the SSH protocol is used. The files are backed up using an SCP
Linux command. The AWS virtual machine is made unavailable, and the files are still
accessible from the Azure virtual machine. This evaluation verifies that, from the point of
failure, the cloud-to-cloud file system backup and recovery still function without any data loss
or unavailability during a disaster.
5.6.Summary
The testing is a critical part of this project as it tests the project through multiple scenarios as
defined in the test cases and provides the results. The failover from AWS to Azure is achieved
using the MariaDB cluster, and file system synchronisation is performed using SCP through
the SSH protocol.](https://image.slidesharecdn.com/146ec863-4913-4c64-8fc3-2ab9cc80e787-161101074316/85/Sri-PRJ702-Project-Report-43-320.jpg)











![Kurra Srirekha
65
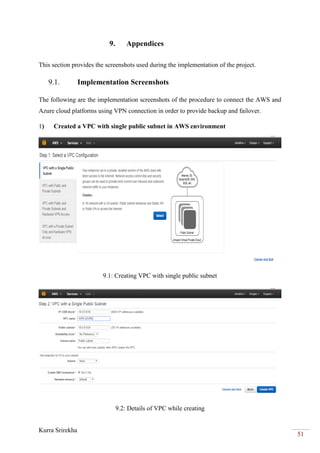
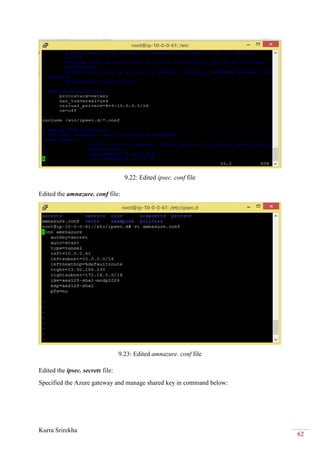
MariaDB Settings:
Now added the following lines for wsrep configuration options in my.cnf file
under [mysqld]directive as shown below in AWS server and Azure server.
VSRep Providers Configurations:
Here, configured the VSRep configurations under the [mysqld]directory on each node by
adding the following lines in /etc/mysql/my.cnf file with their specific IP address, hostnames
and root password.](https://image.slidesharecdn.com/146ec863-4913-4c64-8fc3-2ab9cc80e787-161101074316/85/Sri-PRJ702-Project-Report-66-320.jpg)
