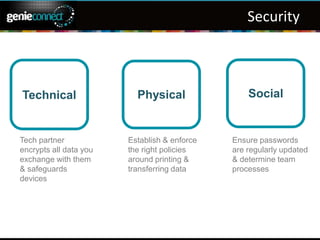
The document outlines essential practices for securing sensitive event data, covering types of data and security measures. It emphasizes the importance of encrypting data, implementing strict physical and social policies, and regularly updating passwords. Key recommendations include conducting penetration testing and ensuring strong vendor security standards.