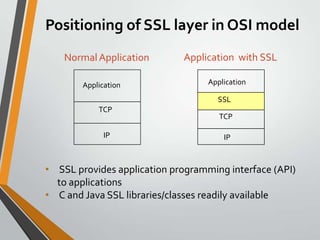
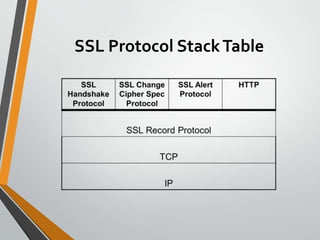
SSL (Secure Sockets Layer) is a security technology developed to create an encrypted link between web servers and browsers, ensuring data privacy and integrity. It operates using a handshake protocol for authentication and a record protocol for secure data transmission. The latest iteration, Transport Layer Security (TLS), has evolved from previous SSL versions, with widespread application across web browsers.