The document outlines secure coding guidelines for implementing Content Security Policy (CSP) to prevent cross-site scripting (XSS) attacks. It emphasizes the importance of defining trusted origins and recommends separating JavaScript and CSS from HTML, avoiding inline scripts, and using 'self' directives in policies. Additionally, the document provides a Java servlet filter example for applying CSP headers to HTTP responses.

![11/11/2015 Secure Coding Guidelines for Content Security Policy | GnuDeveloper.com
http://www.gnudeveloper.com/cyber_security/secure_coding_guidelines_for_content_security_policy.html 4/4
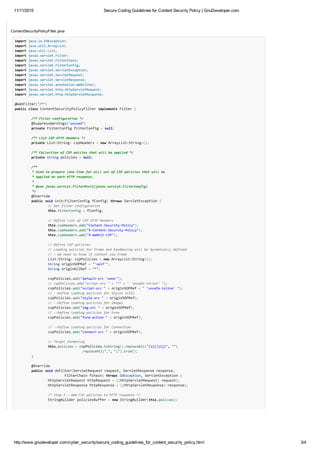
// Target formating
this.policies = cspPolicies.toString().replaceAll("([|])", "")
.replaceAll(",", ";").trim();
}
@Override
public void doFilter(ServletRequest request, ServletResponse response,
FilterChain fchain) throws IOException, ServletException {
HttpServletRequest httpRequest = ((HttpServletRequest) request);
HttpServletResponse httpResponse = ((HttpServletResponse) response);
/* Step 2 : Add CSP policies to HTTP response */
StringBuilder policiesBuffer = new StringBuilder(this.policies);
// Add policies to all HTTP headers
for (String header : this.cspHeaders) {
httpResponse.setHeader(header, policiesBuffer.toString());
}
/* Step 3 : Let request continue chain filter */
fchain.doFilter(request, response);
}
@Override
public void destroy() {
// TODO Auto‐generated method stub
}
}
Source Code Download :
ContentSecurityPolicyFilter.java
CSPFilter.war
Groups:
CyberSecurity](https://image.slidesharecdn.com/securecodingguidelinesforcontentsecuritypolicygnudeveloper-151111163122-lva1-app6892/85/Secure-coding-guidelines-for-content-security-policy-4-320.jpg)