More Related Content
Similar to SecArchitect (20)
SecArchitect
- 1. Extranet
/
DMZ
Endpoints
On-premises
Information Security Office
Clients
3rd
Party Hosting
Private Cloud
Public Cloud
Edge DLP
Web Filtering
Endpoint Protection (EP)
Endpoint Encryption(EE) SSL Decryption
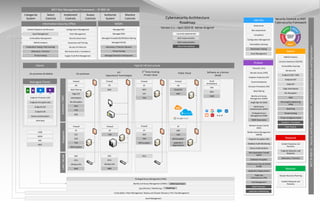
Cybersecurity Architecture
Roadmap
Version 2.1 – April 2019 © Adrian Grigorof
Penetration Testing / Red Teaming
2020 implementation
Currently implemented
Vulnerability Management
Incident Response and Recovery
SIEM & Analytics
Security Governance
Endpoint DR
Email
Antimalware
Firewall
WAF
WAF
Antimalware
DeviceAuthentication
Risk Assessments / Compliance
Configuration Management
Asset Management
Security Architecture
Awareness and Training
Software as a Service
(SaaS)
Hybrid Infrastructure
Log Collection / Monitoring /
Identity and Access Management (IDAM) /
CASB
SSO
On-premises & Mobile
Endpoint DLP
EP EP
EP
Cloud DLP
Identify
Configuration Management
Vulnerability Scanning
Security Controls vs NIST
Cybersecurity Framework
IPS
VPN Client
Risk Assessments
Asset Management
Recover
Incident Response and
Recovery
Disaster Recovery Planning
Respond
Endpoint Detection and
Response
Incident Response and
Recovery
DLP
DLP
Endpoint EDR / HIDS
Endpoint DLP
Detect
Intrusion Detection (IDS/IPS)
SSL Decryption
SIEM & Analytics
Edge DLP
Edge Antimalware
DeviceAuthentication
Public Key
Infrastructure ( PKI)
Network Access Control
(NAC)
Mobile DeviceManagement
(MDM)
Protect
Database Encryption
Email Antimalware
Cloud Access Security Broker
(CASB)
Database Audit Monitoring
Endpoint Encryption (EE)
Remote Access (VPN)
Endpoint Protection (EP)
Firewalls / ACLs
Web Application Firewall
(WAF)
Web Filtering
FIM
Firewall Firewall
EDR
Managed Clients
Noton the roadmap
Deception / Honeypots
Intrusion Prevention (IPS)
DDoS Protection
Governance
Compliance
File Integrity Monitoring
(FIM)
FIM
Penetration Testing
FIM
Vulnerability Scanning
Baselining
eDiscovery / Forensics
eDiscovery / Forensics
Supply Chain Risk Management
Threat Hunting
Application Whitelisting
Threat Intelligence Feeds
Patch Management
Threat Hunting
Code Analysis
FIM
EDR
MFA
Key Management
Wireless IDS
Privileged Access Management (PAM)
Vulnerability / Patch Management / Backup and Disaster Recovery / PKI / Key Management
DB Encryption
DB Encryption
2019 implementation
MSSPs
eDiscovery / Forensics Retainer
Managed SIEM
Managed Firewalls/IDS/IPS/Web Filtering
Managed IPS/IDS
Managed Detection and Response
Threat Hunting
Managed NAC
IDAM Governance
Baselining
Identity and Access
Management (IDAM)
Privileged Access
Management (PAM)
Multi-Factor
Authentication (MFA)
Single Sign-On (SSO)
IDAM Governance
LAN
/
WLAN
NAC
ACLs
EP
FIM
EDR
DB Encryption
IPS
NMS
Wireless IDS
NMS
EDR
Application Segmentation
Application
Segmentation
ACLs
WAF
MDM
NAC
CASB
MFA
Asset Management
IoT
Operational Technologies
Firewall
IPS
Wireless IDS
NAC
ACLs
NMS
WAF
Firewall
Firewall
EP
FIM
Firewall
NIST Risk Management Framework – SP 800-18
Categorize
System
Select
Controls
Implement
Controls
Assess
Controls
Authorize
System
Monitor
Controls
NIST
SP
800-53
-
Security
and
Privacy
Controls
for.
Federal
Information
Systems
and
Organizations