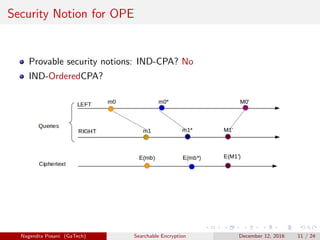
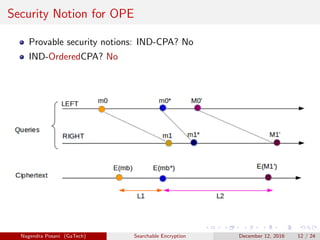
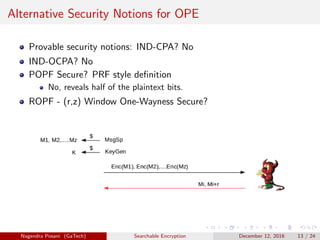
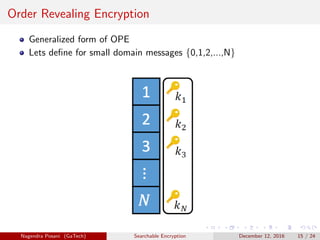
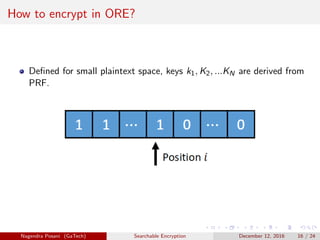
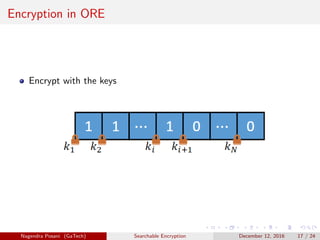
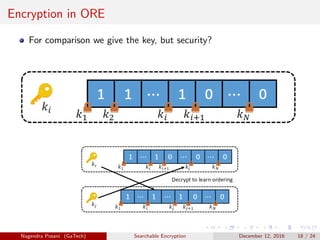
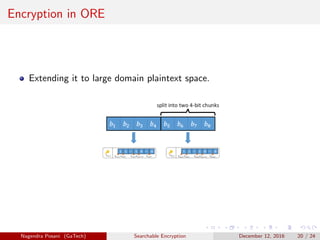
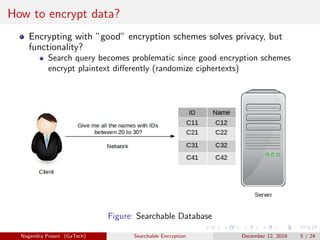
The document discusses the importance of searchable encryption in the context of data breaches and privacy concerns. It covers various encryption schemes, including Order Preserving Encryption (OPE), Order Revealing Encryption (ORE), and Partial Order Preserving Encryption (POPE), highlighting their functionalities, security notions, and limitations. The work emphasizes the need for secure and efficient search capabilities in encrypted data storage.


![Literature
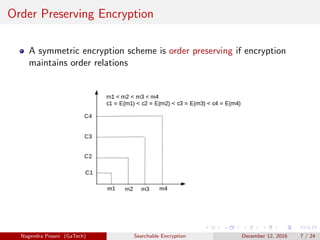
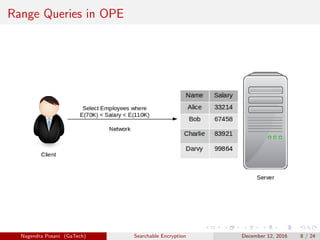
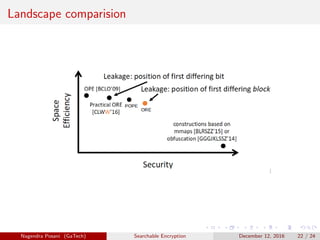
Order Preserving Encryption (OPE) [1], [2]
Variants of OPE [3]
Partical Order Preserving Encryption (POPE) [4]
Order Revealing Encryption (ORE) [5], [6]
Nagendra Posani (GaTech) Searchable Encryption December 12, 2016 6 / 24](https://image.slidesharecdn.com/cs6260searchableencryptionpresentation-170103012438/85/Searchable-Encryption-10-320.jpg)