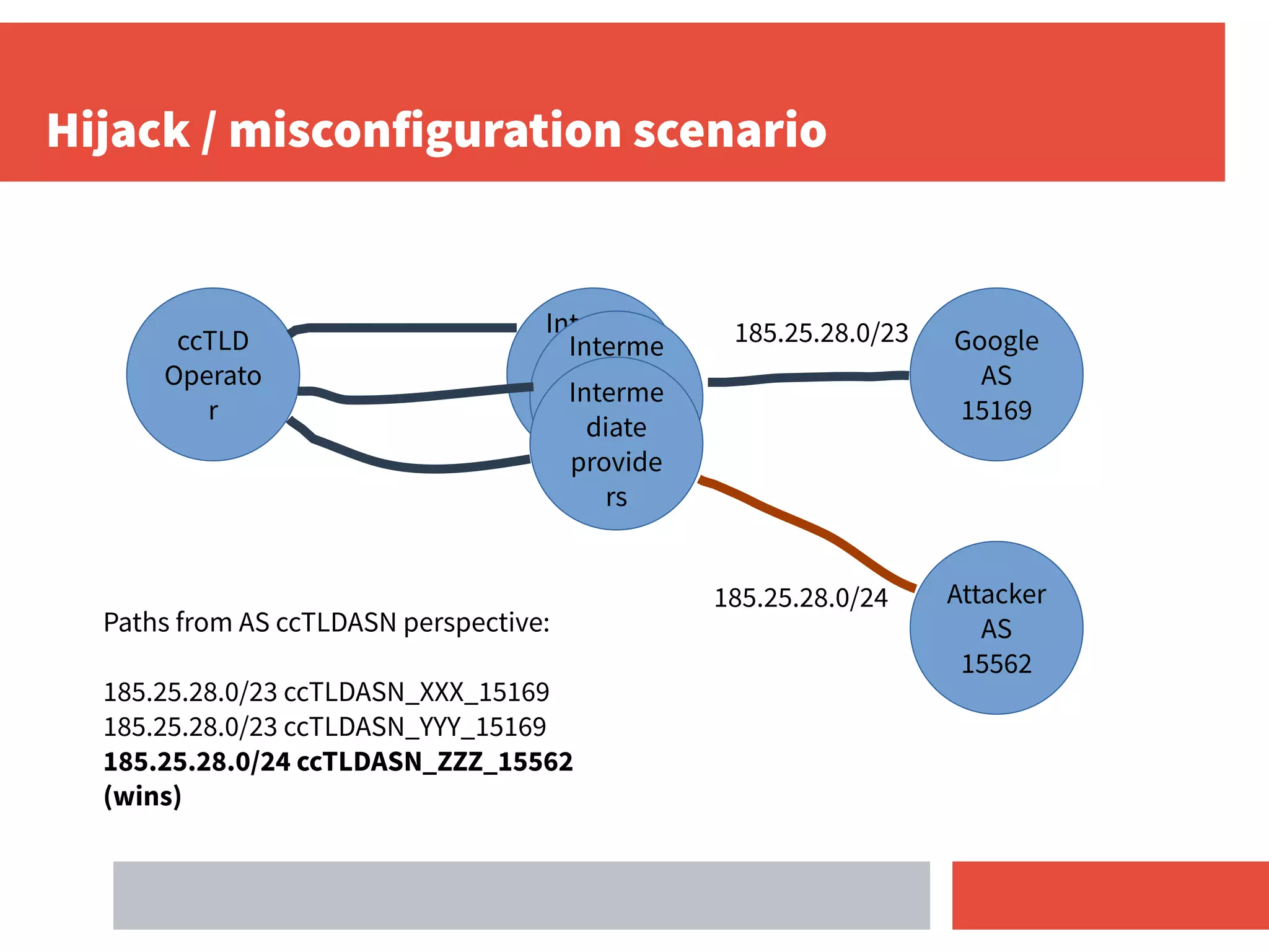
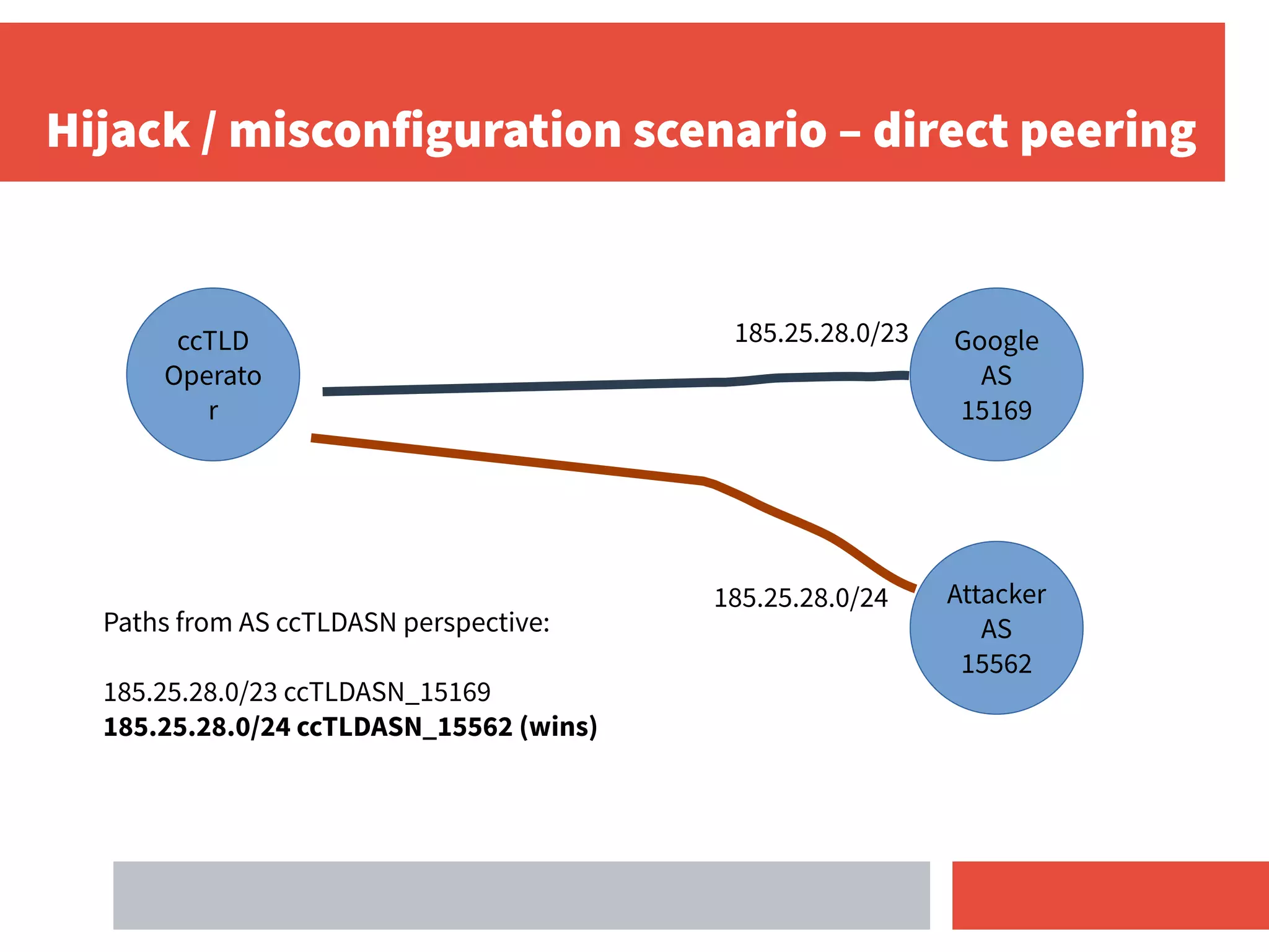
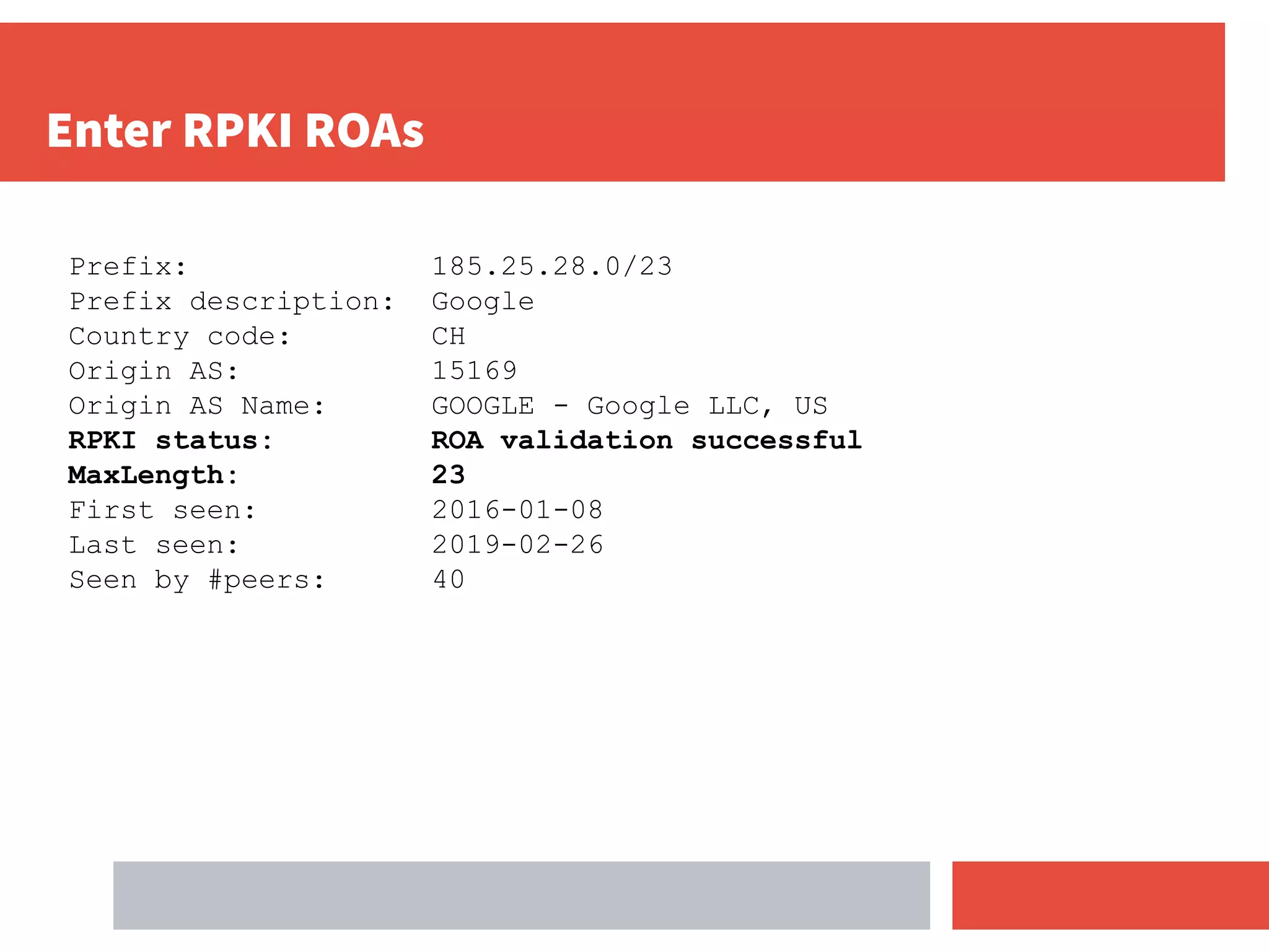
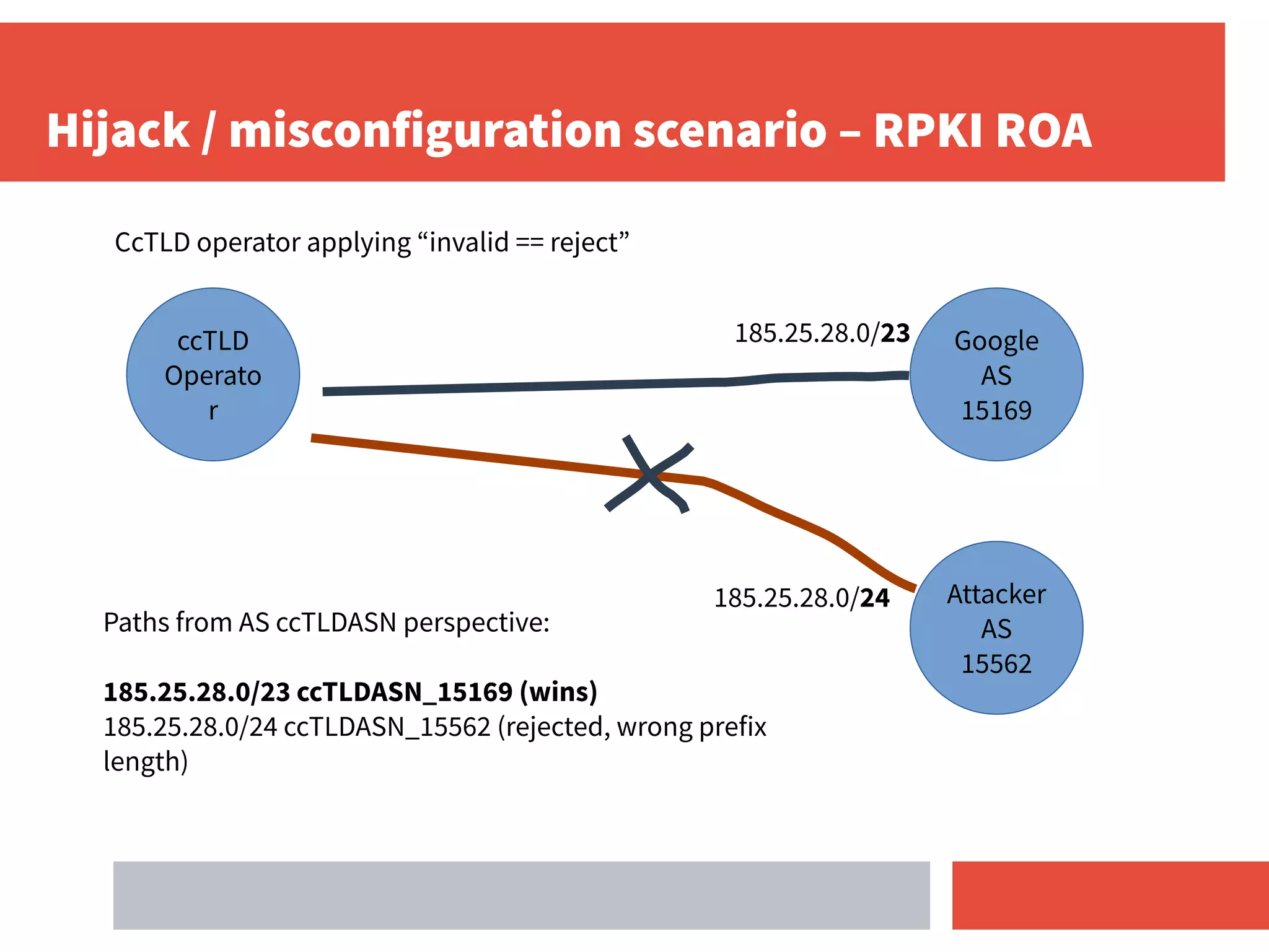
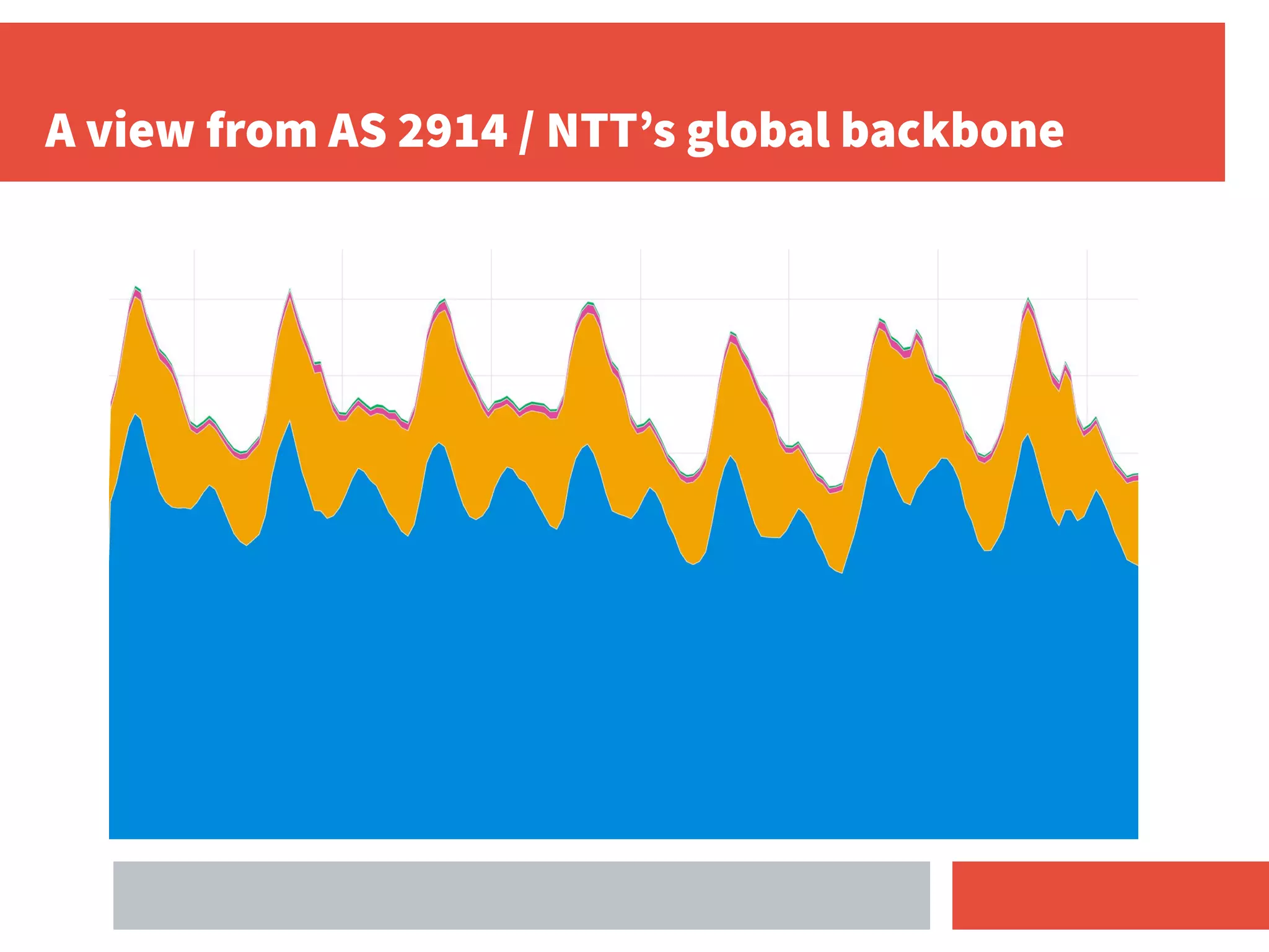
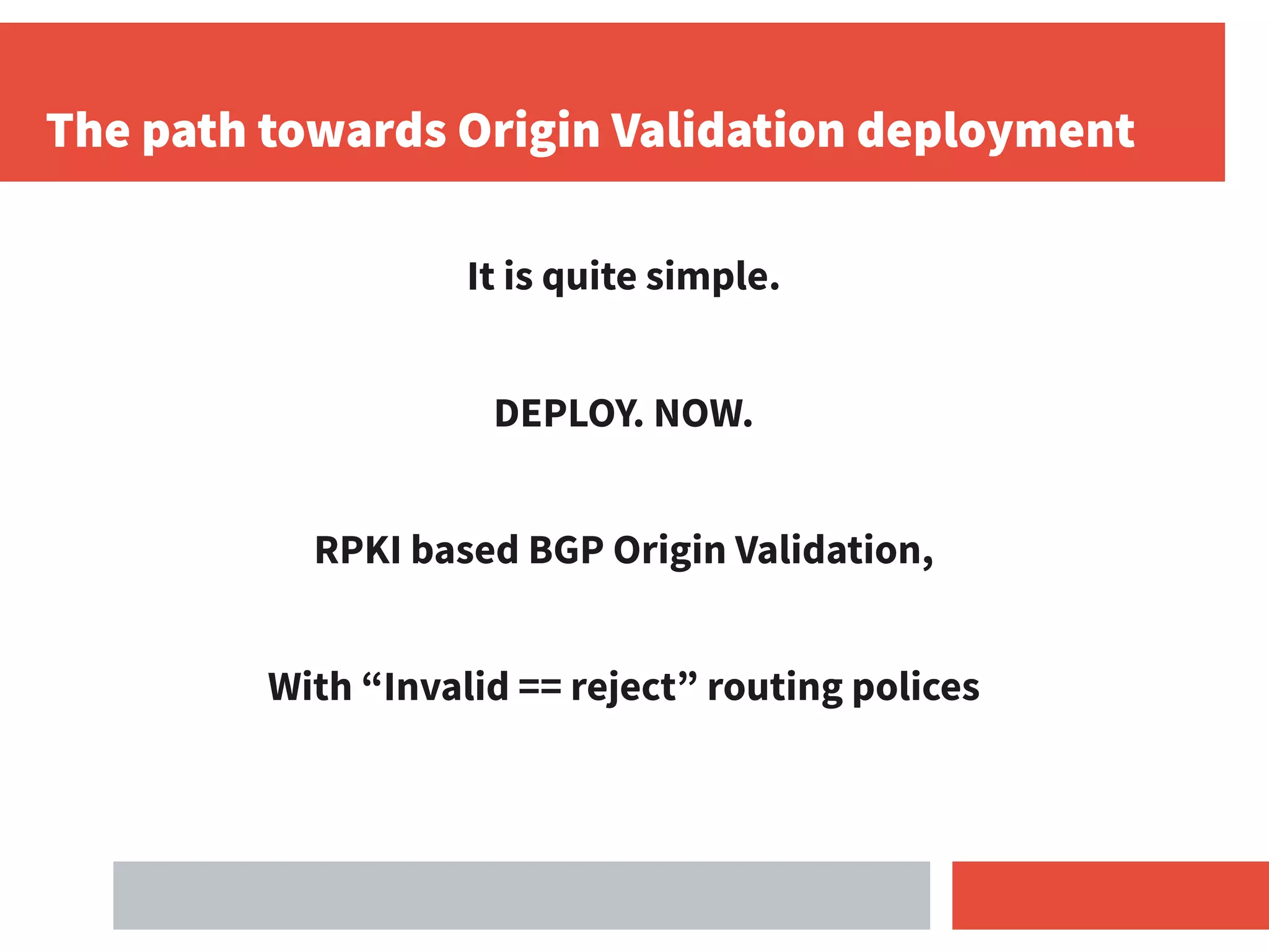
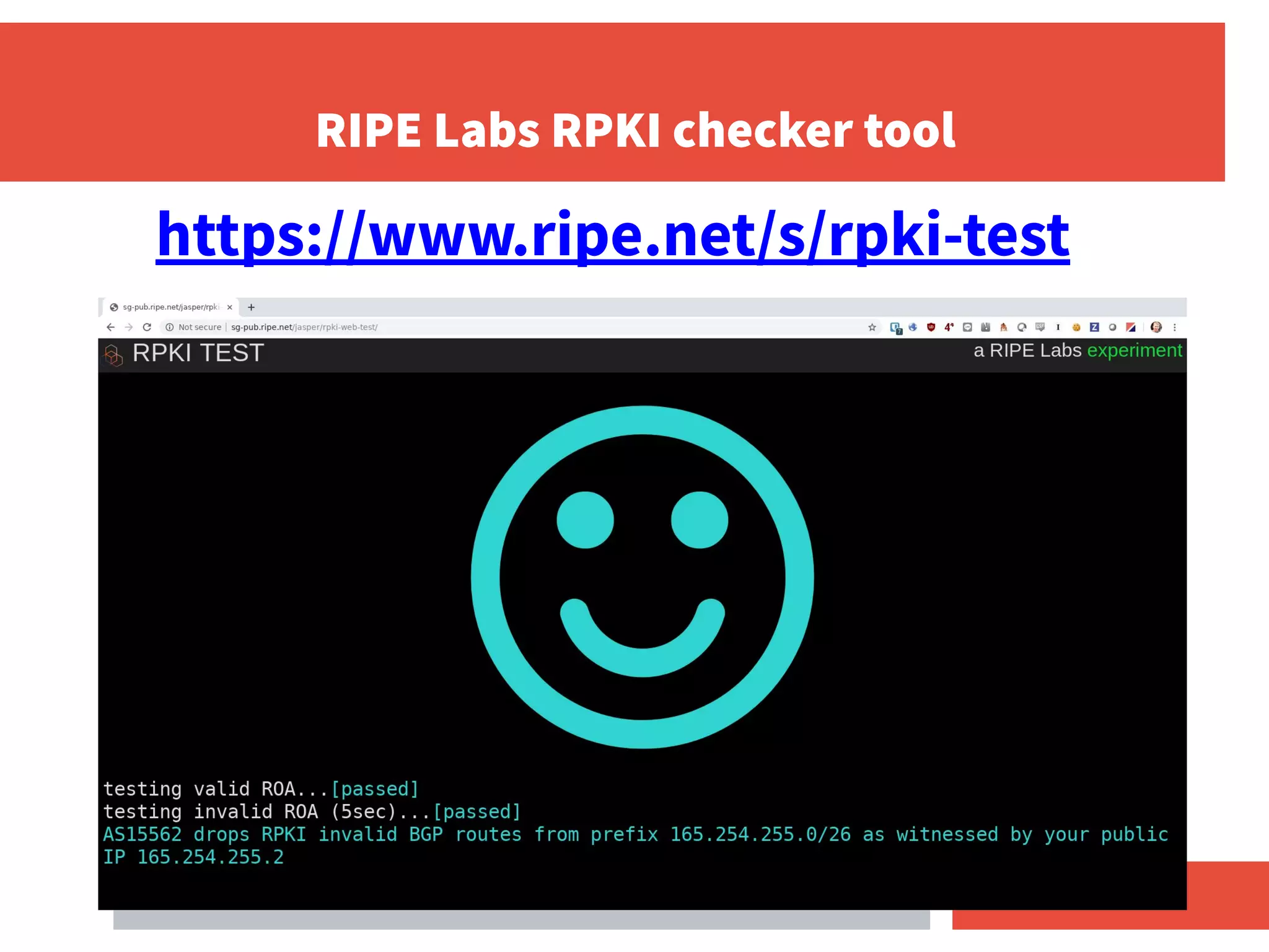
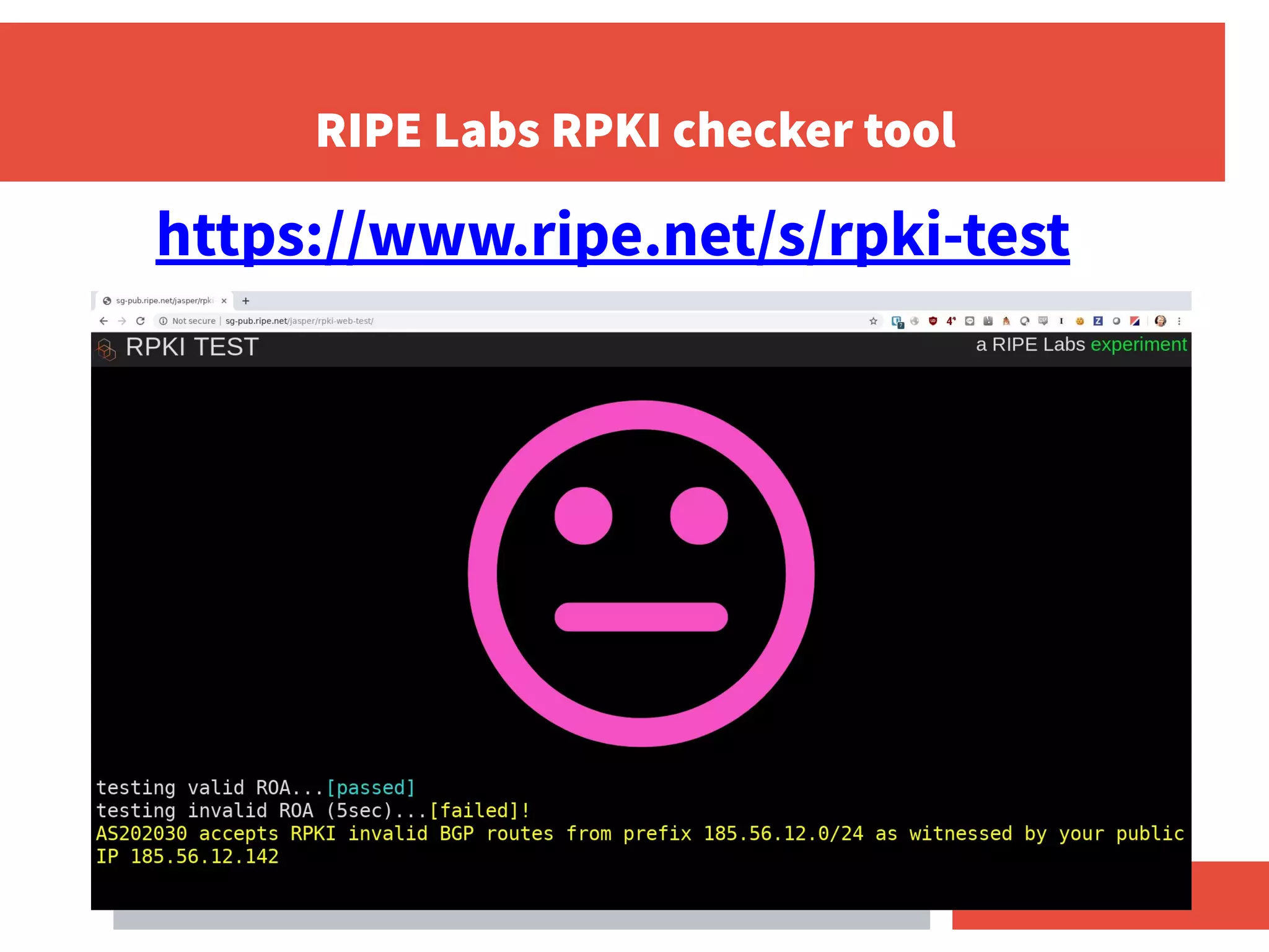
- RPKI-based BGP origin validation protects network operators from misconfigurations and route hijacking by other networks by validating that the originating ASN matches the ROA for the prefix.
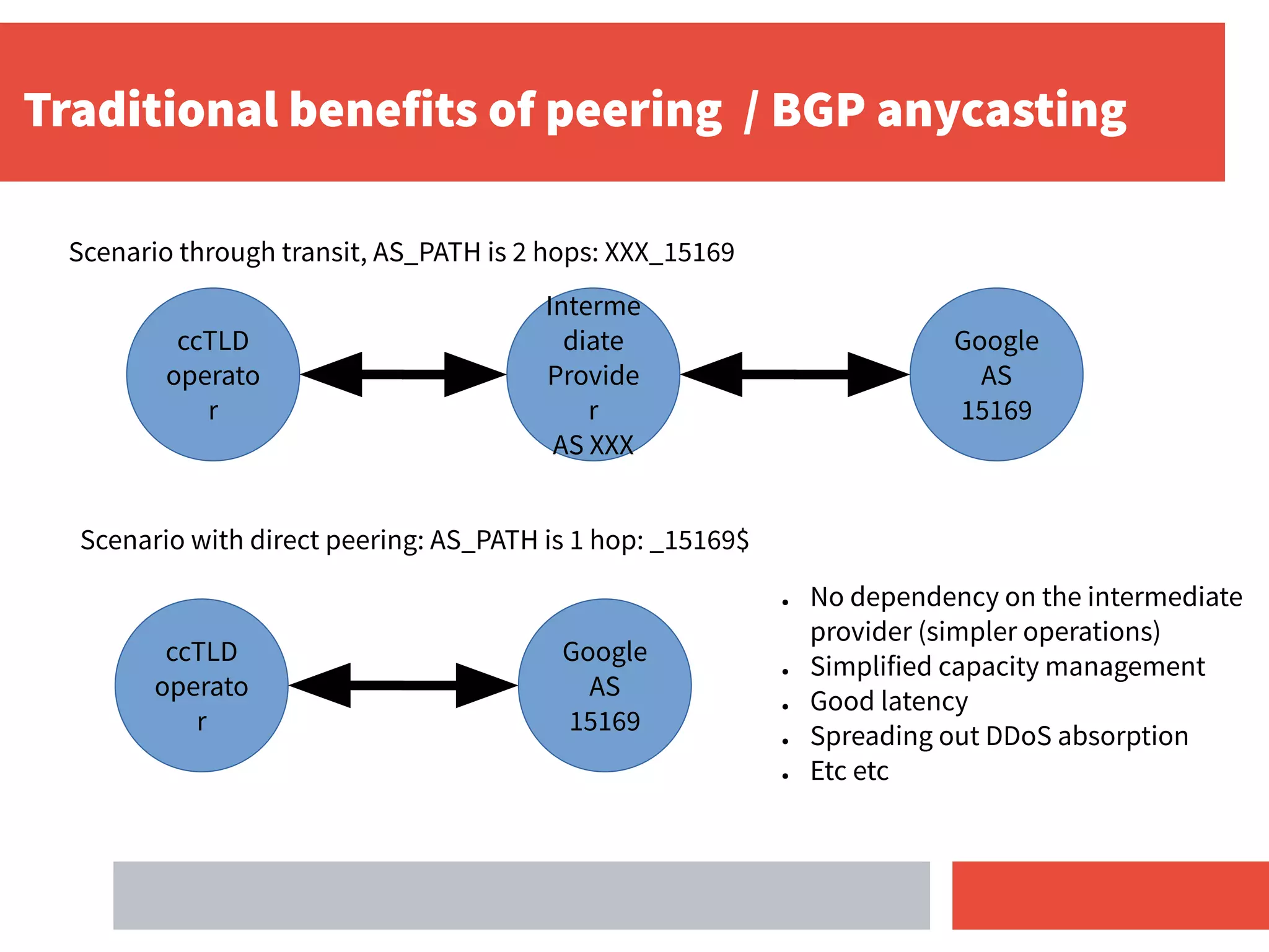
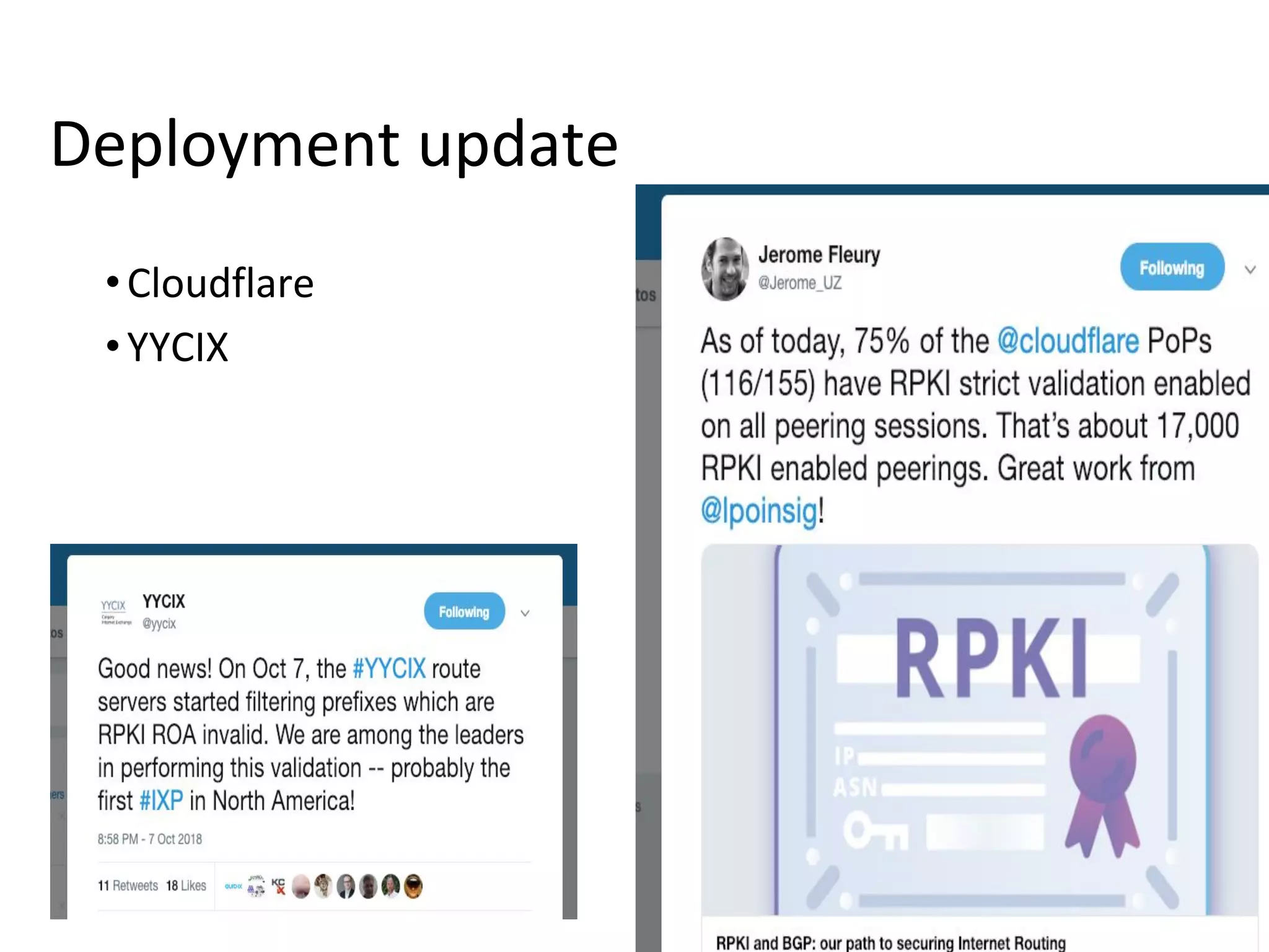
- Direct peering combined with RPKI deployment makes validation stronger by removing dependencies on intermediate transit providers.
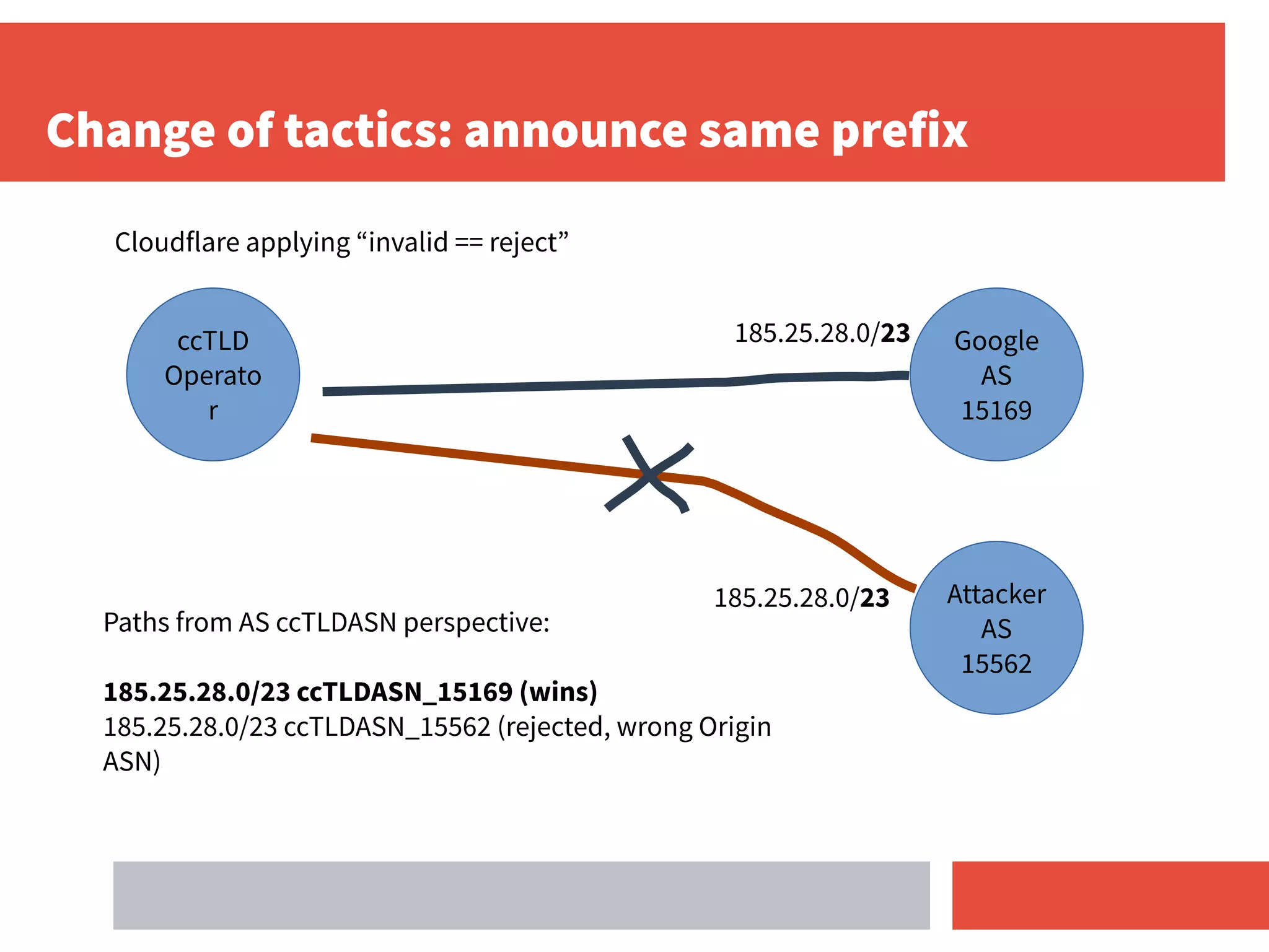
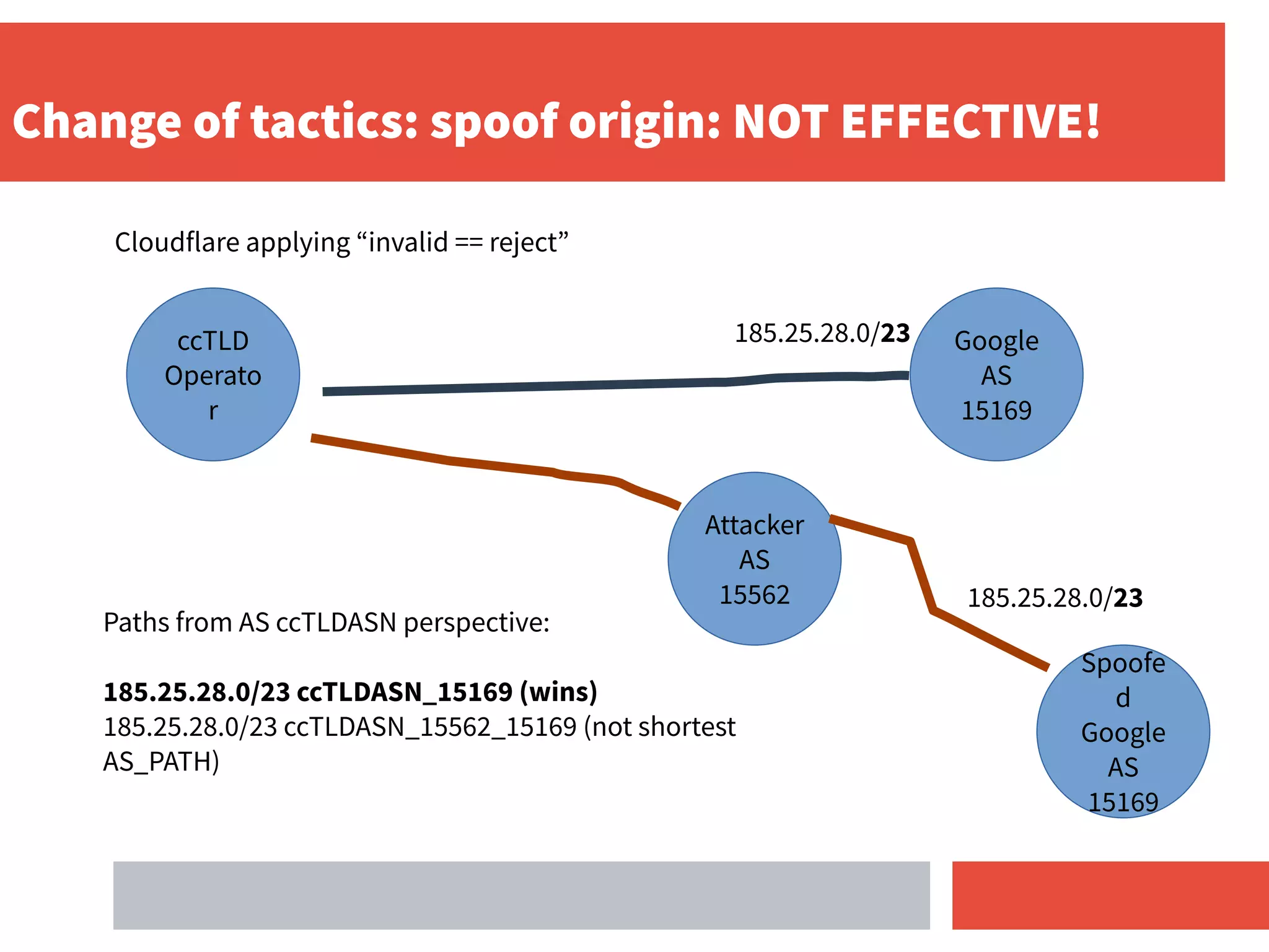
- For ccTLD operators, deploying RPKI and applying an "invalid route = reject" policy helps secure routing for their DNS prefixes and protects others as well.