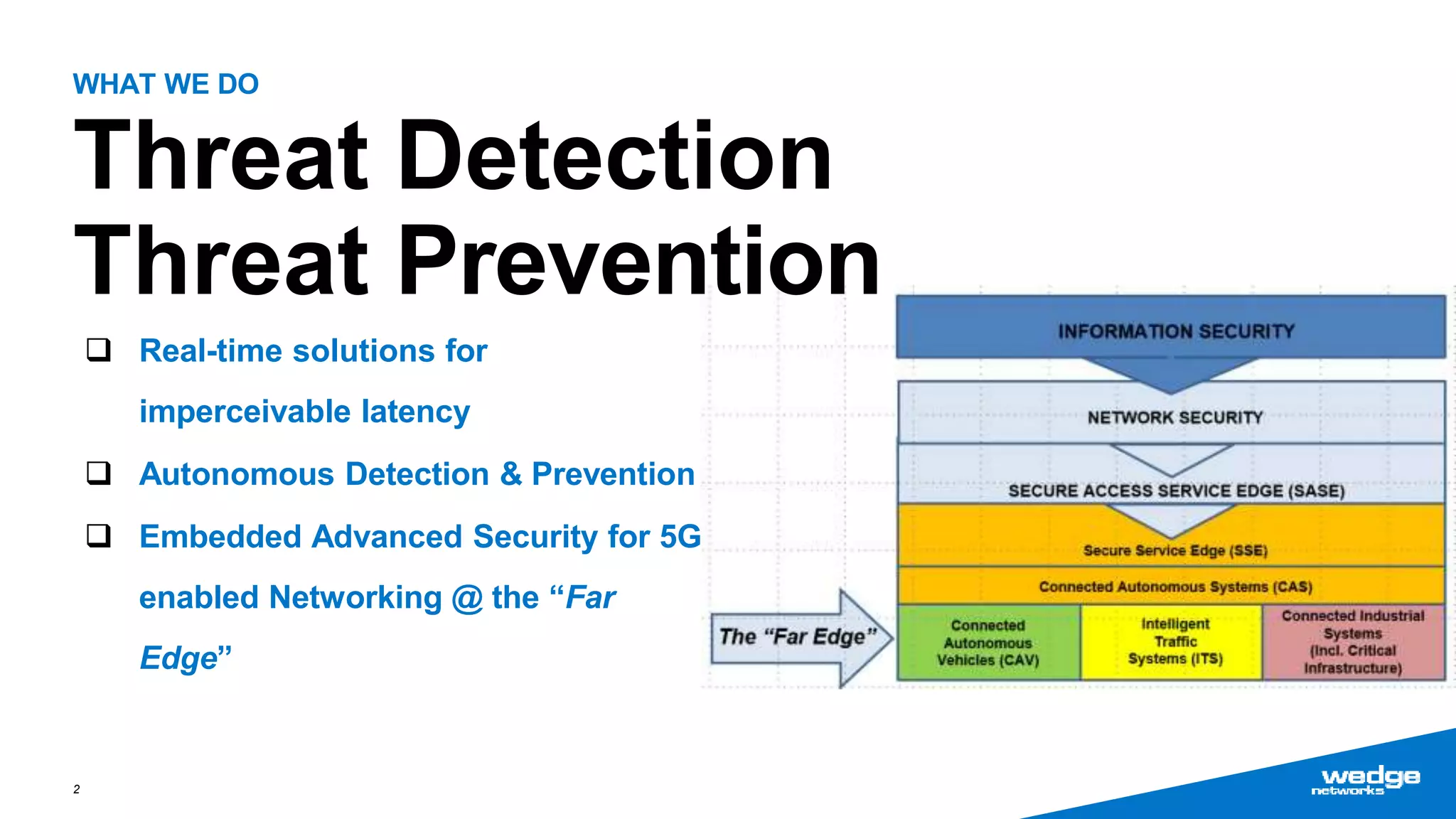
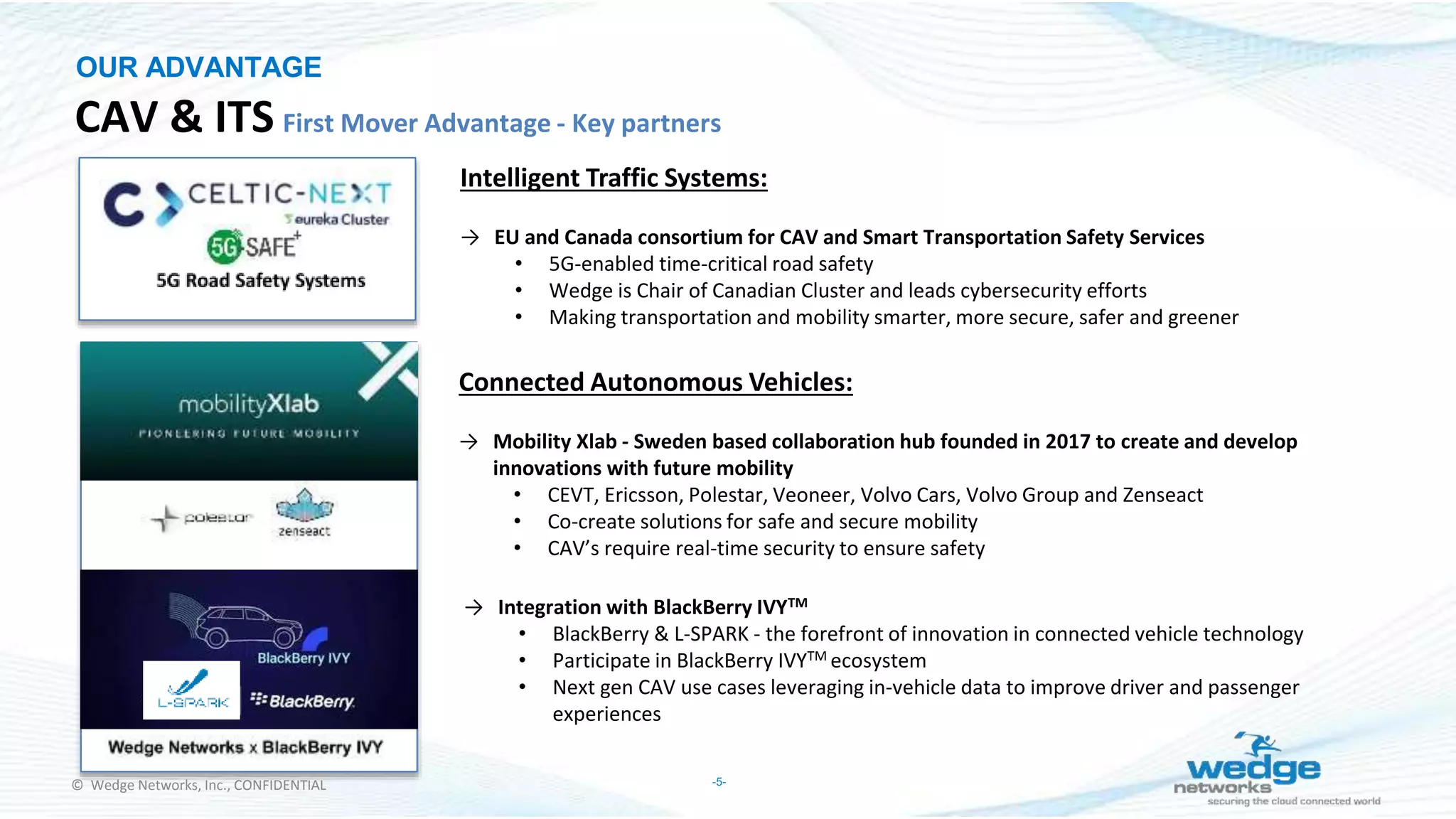
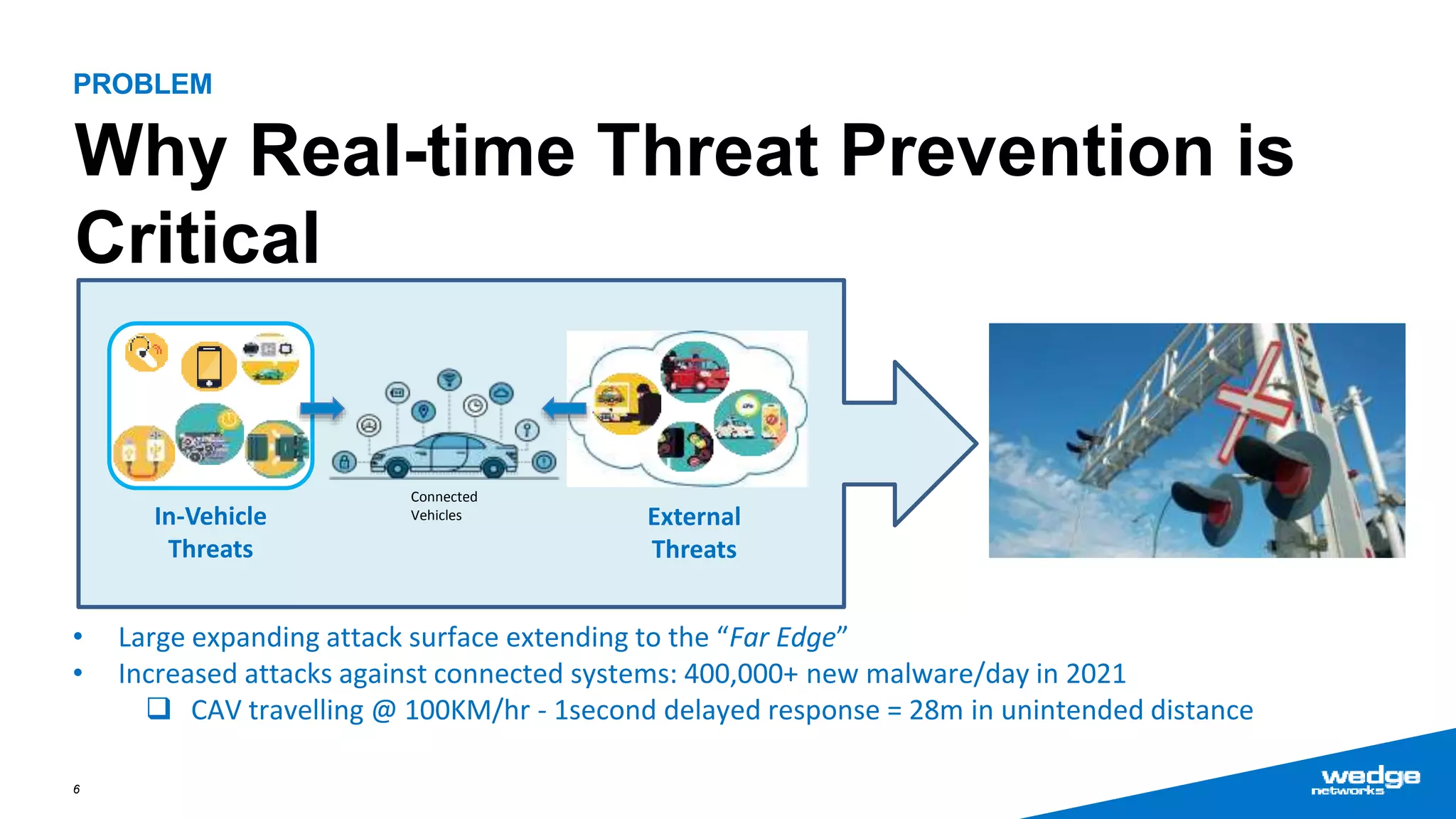
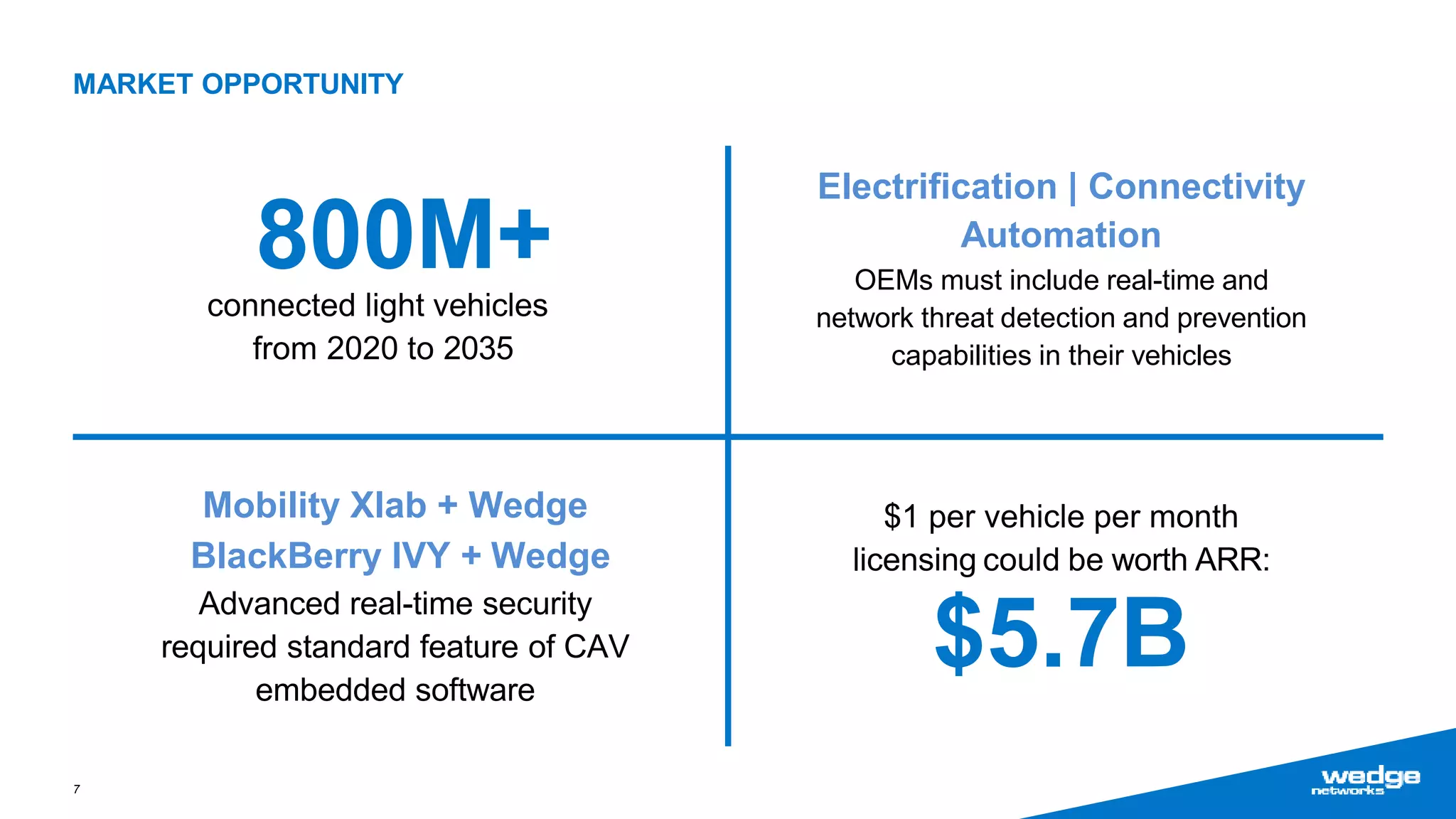
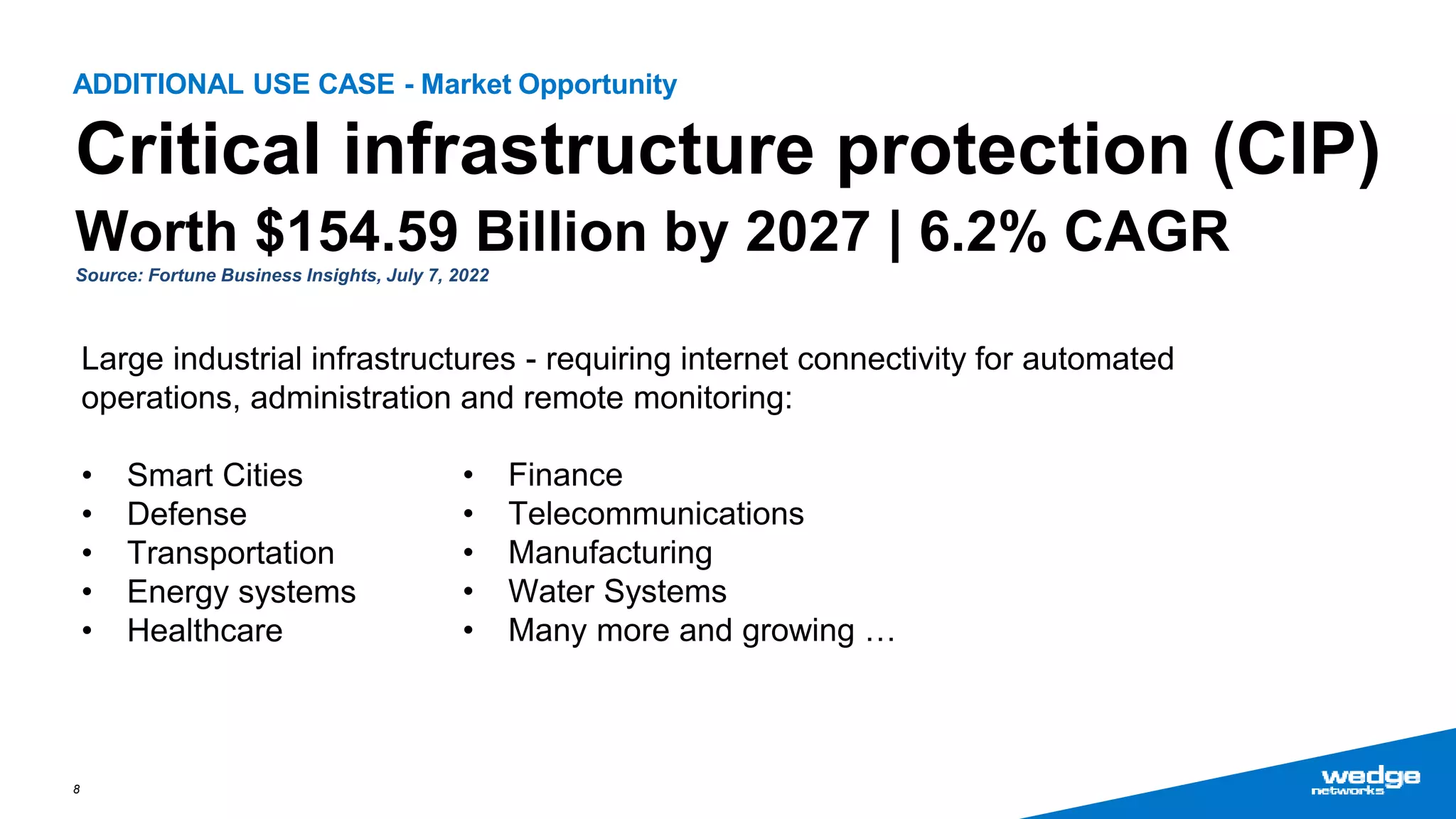
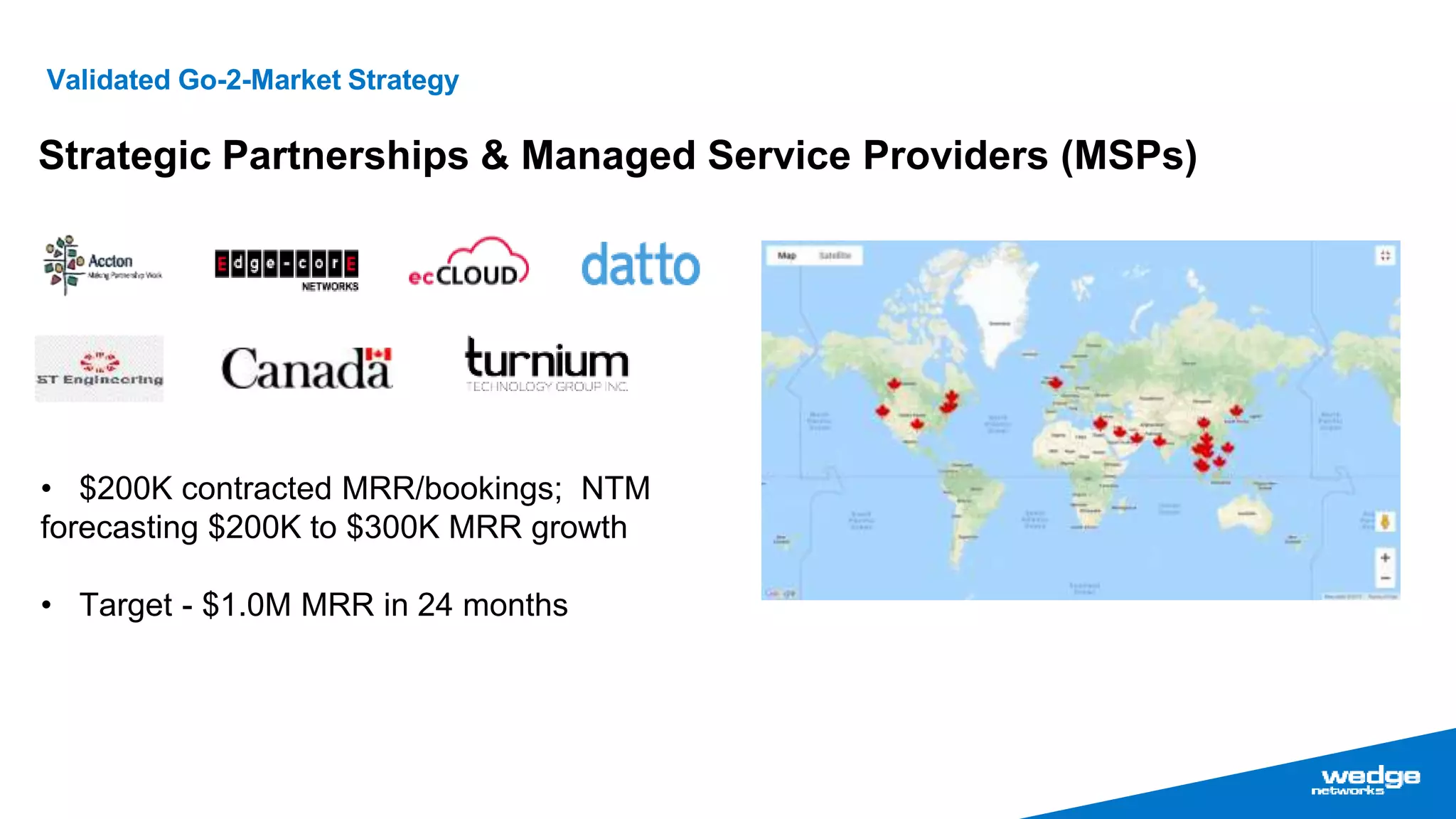
Wedge Networks specializes in real-time threat detection and prevention for connected autonomous systems, with a focus on applications such as connected vehicles and smart infrastructure. The company highlights its competitive advantage through strategic partnerships and patented technologies that enhance security solutions. With the growing demand for integrated cybersecurity in connected vehicles, Wedge aims for significant market opportunities, projecting substantial revenue growth in the coming years.