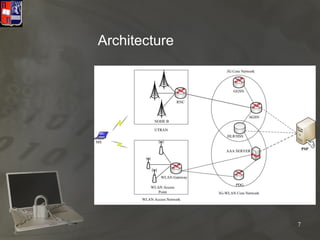
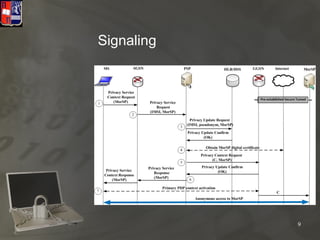
The thesis focuses on privacy techniques in fourth generation heterogeneous networks, addressing issues such as data mining and exposing credit card information. It proposes a model for enhancing privacy, security, and trust in mobile networks, specifically targeting e-commerce applications and micropayments. The evaluation indicates effective privacy and security measures while facilitating financial transactions without disclosing personal data.