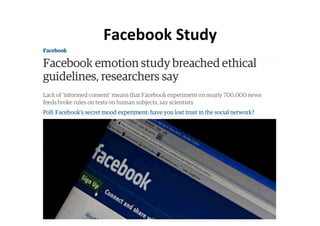
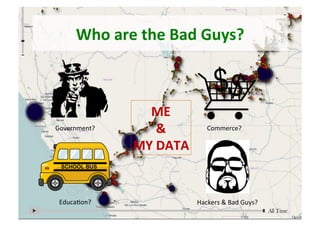
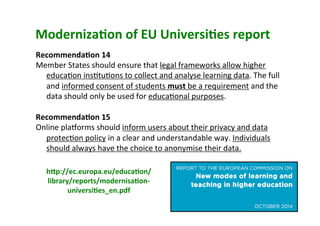
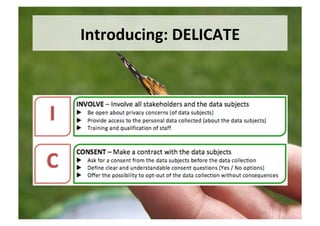
The document discusses the complexities and challenges of implementing learning analytics (LA) in public education, emphasizing the balance between potential benefits and privacy concerns. It highlights the necessity for clear legal frameworks and informed consent for data collection and usage, while addressing fears related to data ownership and privacy. Furthermore, it suggests that transparency in data policies does not always equate to trust, highlighting the asymmetrical power dynamics between users and large organizations.