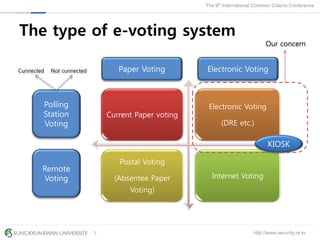
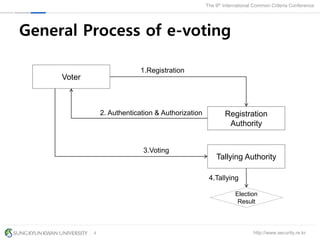
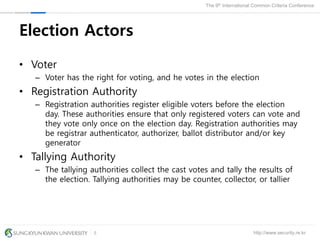
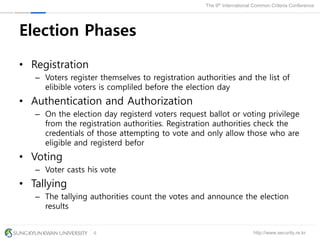
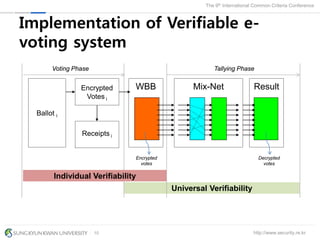
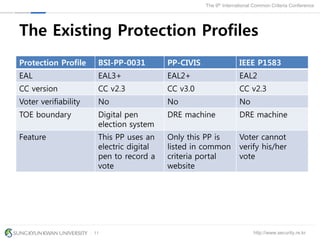
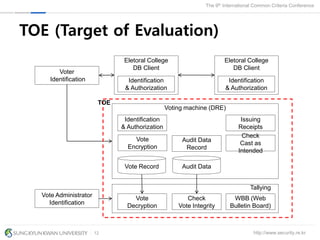
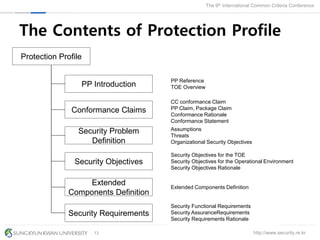
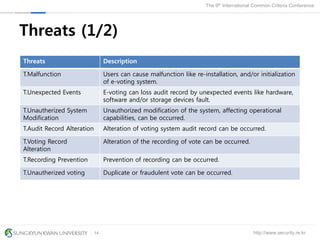
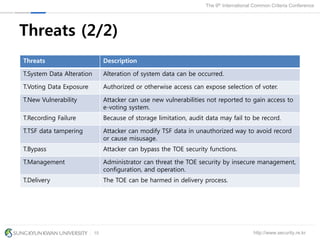
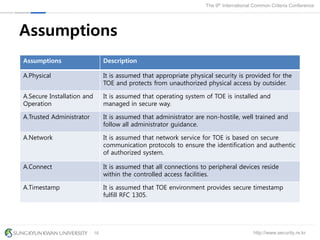
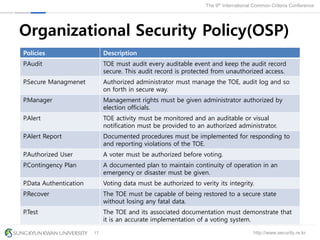
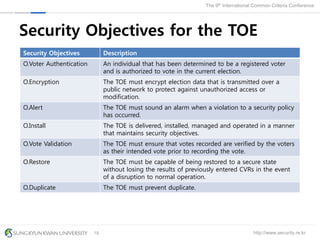
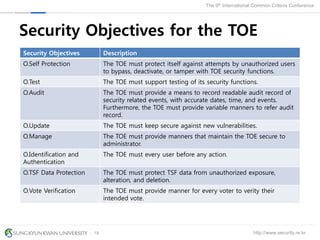
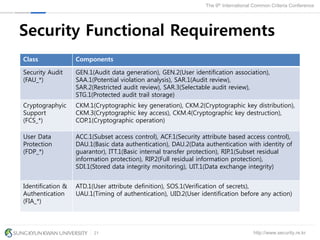
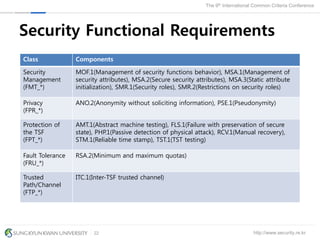
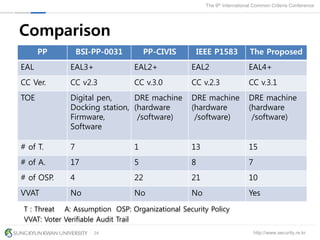
The document presents a protection profile for e-voting systems, detailing various types of e-voting, their processes, and security requirements. It addresses issues of voter verifiability and security risks, emphasizing the need for confidence in election outcomes through evaluation against Common Criteria standards. The paper concludes with a call for improved protection profiles that incorporate verifiable voting mechanisms.