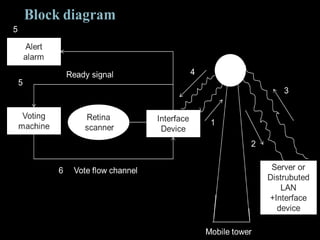
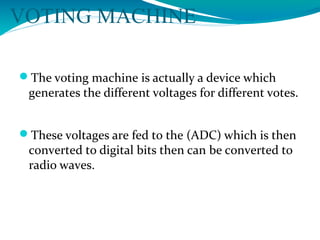
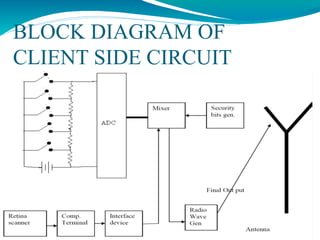
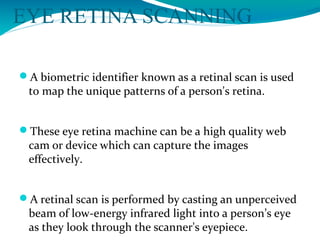
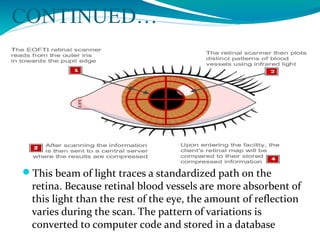
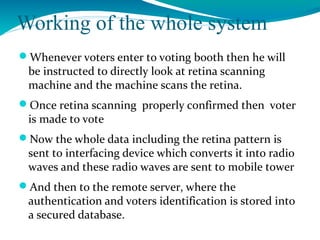
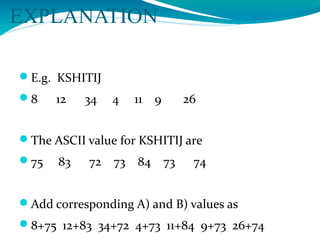
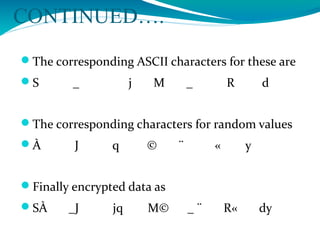
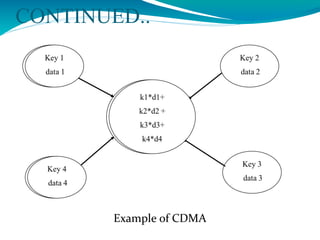
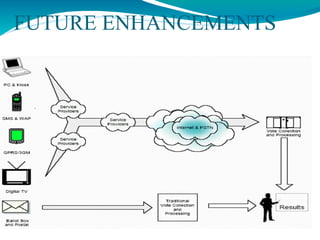
The document presents a proposal for a global wireless e-voting system that utilizes eye retina scanning to verify voter eligibility, aiming to enhance security and reduce corruption in the voting process. The proposed system stores vote counts on a remote server, allowing votes to be cast via mobile connections, which minimizes the risk of technical failures commonly found in traditional voting machines. Future enhancements are discussed to improve security, efficiency, and geographic accessibility, ultimately leading to faster and more reliable election outcomes.