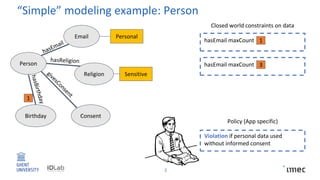
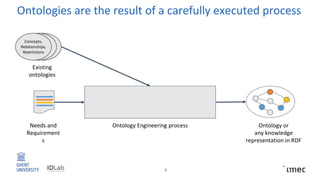
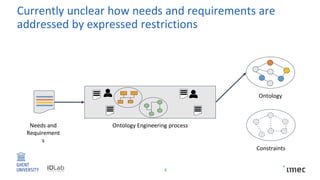
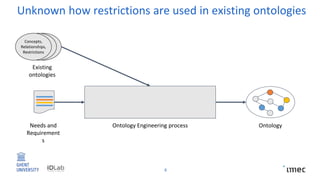
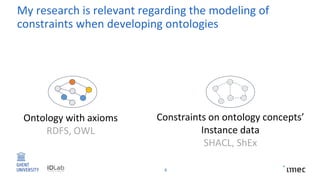
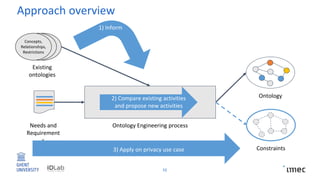
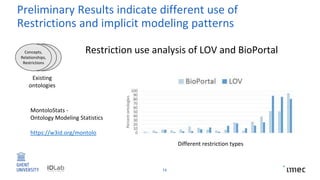
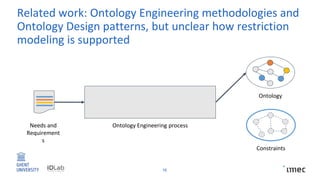
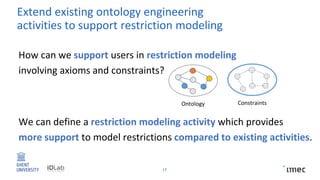
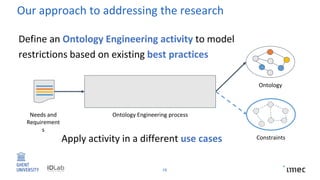
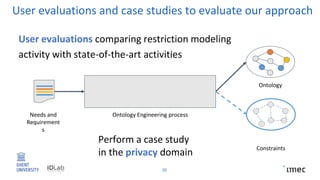
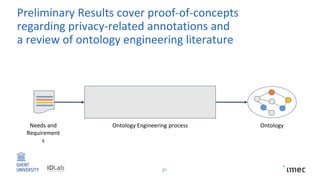
The document outlines research on policy-compliant data processing, focusing on RDF-based restrictions for data protection and the ontology engineering process. It discusses various aspects of restriction modeling, the existing gaps in guidelines for the use of restrictions, and proposes a restriction modeling activity to support compliance assessments, particularly in privacy-aware contexts. The research aims to analyze ontology restrictions and improve support for knowledge engineers in creating relevant data structures.