This minor thesis by Bruno Valentin discusses the development of a pattern detection system for internet cafes to aid law enforcement in identifying criminals who exploit anonymity to commit offenses. The proposed solution involves a network of probes monitoring traffic and reporting real-time alerts to police, enabling swift action without relying on third-party information. The document evaluates existing solutions, outlines the system's architecture, and presents its effectiveness in addressing law enforcement challenges related to cybercrime.








![2
Background
2
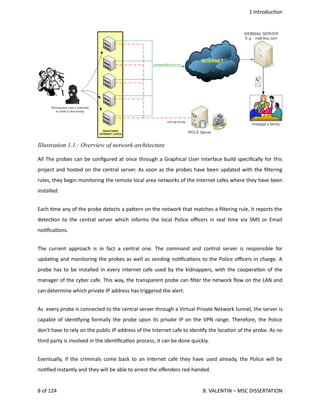
Background
As
seen
previously
in
the
introduc<on,
the
topic
of
the
current
document
is
to
set
up
a
solu<on
in
order
to
simultaneously
intercept
a
set
of
local
area
networks
from
a
remote
point
of
view,
and
for
Law
Enforcement
needs.
This
kind
of
subject
ma.er
is
ohen
not
published
or
disclosed
since
it
is
considered
as
sensi<ve
by
the
private
companies
which
are
designing
on‐purpose
equipment
and
the
Law
Enforcement
Agencies.
Though,
some
white
papers
have
been
released
publicly
by
academic
ins<tu<ons
and
private
sector.
An
overview
of
the
current
state
of
art
regarding
wire
tapping
has
been
done
to
determine
how
intercep<ons
can
be
implemented
for
solving
the
issue
exposed
in
this
disserta<on.
The
white
papers
and
other
documents
found
are
introducing
the
different
ways
of
intercep<ng
communica<ons
on
a
IP
network.
2.1
Internal
versus
external
interceptions
Depending
on
how
accessible
the
network
is
to
monitor
and
where
the
wiretapping
equipment
can
be
installed,
an
intercep<on
process
can
be
referred
to
as
internal
or
external.
Internal
intercep<on
allows
the
Law
Enforcement
Agencies
to
extract
the
data
directly
from
the
internal
networks
of
internet
service
providers
[2‐1]
involved
in
the
transmission
of
the
data
of
interest
over
the
Internet.
In
this
case,
the
whole
traffic
of
the
target
is
intercepted
and
delivered
to
the
LEA
in
its
raw
format.
This
is
commonly
completed
using
sohware
or
hardware
sniffers
capable
of
dealing
with
IP
traffic.
Of
course,
since
it
is
crucial,
from
a
Law
Enforcement
prospec<ve,
that
the
target
doesn't
know
they
are
being
monitored,
some
mechanisms
must
be
put
in
place
to
ensure
the
intercep<on
system
remains
transparent.
This
means
that
the
system
has
to
be
thought
of
and
designed
in
a
secure
manner.
[2‐1]
Unfortunately,
in
many
developed
countries,
ISPs
are
ohen
reluctant
to
provide
access
to
their
core
networks
to
the
LEA.
There
is
usually
a
strong
opposi<on
[2‐1]
leading
to
a
legal
figh<ng
between
LEA
and
service
providers.
When
pu_ng
in
place
an
internal
intercep<on
is
not
feasible,
intercep<on
must
be
performed
at
10
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-10-320.jpg)
![2
Background
network
access
level
outside
the
network
of
the
service
provider.
Typically,
this
means
that
the
intercep<on
material
has
to
be
connected
out
of
the
immediate
target
network,
for
instance
at
adjacent
networks
or
public
network
concentra<on
points
[2‐1].
This
network
pertains
usually
to
the
network
operator,
as
depicted
on
the
figure
below.
The
systems
capable
of
doing
external
intercep<ons
are
ohen
designed
and
commercialised
by
private
companies.
As
performing
an
external
intercep<on
is
much
more
complicated
than
doing
an
internal
one,
such
systems
tend
to
be
sophis<cated
and
not
officially
publicised.
In
fact,
WAN
monitoring
is
considerably
not
a
simple
task
to
complete.
It
must
support
a
much
wider
range
of
network
topologies
and
protocols
(PPP,
mul<link
PPP,
Cisco
HDLC,
frame
relay,
ATM)
[2‐2]
and
must
be
able
to
deal
with
several
levels
of
protocol
encapsula<on.
As
it
was
the
case
already
in
the
internal
intercep<on,
targets
must
be
unaware
that
they
are
under
electronic.
Therefore,
any
no<ceable
informa<on
that
could
reveal
the
monitoring
process
should
be
avoided
[2‐1].
For
instance,
the
“Traceroute”
command
could
show
a
new
router
hop
in
the
path
from
the
target
to
the
Internet.
Also,
degrada<on
or
interrup<on
of
service
has
to
be
avoided
as
much
as
can
be
by
the
use
of
appropriate
technologies.
In
conclusion,
any<me
it
is
applicable,
internal
intercep<on
is
considerably
more
straighporward
to
put
in
place.
Also,
the
content
data
resul<ng
from
this
intercep<on
can
be
filtered
more
effec<vely
since
IP
data
is
already
and
does
not
need
to
be
translated
prior
to
being
analysed.
11
of
124
B.
VALENTIN
–
MSC
DISSERTATION
Illustration 2.1: Typical configuration for xDSL](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-11-320.jpg)
![2
Background
2.2
Active
and
passive
monitoring
As
external
intercep<ons
are
not
very
well
documented
publicly,
the
emphasis
will
be
put
on
Internal
intercep<ons,
which
are
more
suitable
to
address
the
global
issue
stated
at
the
beginning
of
this
document.
There
are
typically
two
approaches
in
monitoring
a
network
flow
:
the
passive
and
the
ac<ve
ways.
First,
the
passive
monitoring,
also
referred
to
as
non‐intrusive
[2‐2],
has
the
ability
to
intercept
the
data
transmi.ed
over
a
network
without
interfering
with
the
flow
of
network
traffic.
This
kind
of
topology
is
said
to
be
invisible
and
undetectable
[2‐4]
and
even
if
the
intercep<on
equipment
comes
to
fail
for
any
reason,
the
data
will
con<nue
to
flow
across
the
network.
In
fact,
the
intercep<on
equipment
just
has
to
deal
with
a
copy
of
the
packets.
With
a
hub‐based
network,
each
worksta<on
can
see
the
traffic
transmi.ed
to
or
from
any
of
the
other
computers
connected
to
the
same
network.
Hence,
pu_ng
in
place
a
passive
monitoring
in
a
network
environment
composed
of
hubs
is
very
straighporward.
As
Robert
Graham
says
in
his
FAQ
[2‐3],
Ethernet
was
built
around
a
“shared”
principle:
all
the
machines
on
the
local
network
share
the
same
wire.
Contrarily,
switched
networks
cannot
be
monitored
as
easily.
In
fact,
in
a
switched
network
topology,
the
switch
isolates
the
network
traffic
of
each
worksta<on
and
restrict
the
transmission
to
the
worksta<ons
involved
in
the
ongoing
communica<on
only.
It
means
that
na<vely,
a
monitoring
equipment
connected
to
a
port
on
the
switch
cannot
see
the
traffic
intended
for
another
computer.
[2‐2]
12
of
124
B.
VALENTIN
–
MSC
DISSERTATION
Illustration 2.2: Passive monitoring](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-12-320.jpg)
![2
Background
Two
ways
exist
for
solving
the
issue
of
performing
intercep<ons
in
a
switched
network
topology.
The
first
one
is
tapping
all
single
segment
on
the
switch.
The
second
one
is
using
a
switch
which
comes
with
a
monitoring
port.
The
monitoring
port
is
a
specific
network
port
on
the
switch
that
provides
the
equipment
connected
to
this
port
with
a
copy
of
each
single
packet
transmi.ed
over
the
network.
Obviously,
this
approach
is
more
cost‐effec<ve
to
solve
this
problem
than
the
first
one
[2‐2].
In
addi<on,
some
techniques
exist
to
sniff
the
IP
flow
in
a
switched
network
environment
by
hijacking
the
traffic
[2‐3].
For
instance,
one
of
the
most
effec<ve
is
named
Switch
jamming.
This
technique
allows
to
flood
a
switch
with
a
lot
of
spoofed
mac
addresses.
This
big
amount
of
forged
mac
addresses
is
overflowing
the
mac
address
tables
of
the
switch.
That
leads
from
the
switch
prospec<ve
to
operate
as
a
hub.
Decision
computer
also
names
this
type
of
monitoring
“Mirror
mode”.
It
is
said
to
be
the
most
common
mode
used.
This
mode
has
to
be
used
when
the
data
flow
in
customer
site
is
large.
It
is
possible
to
handle
up
to
1000
users
with
this
kind
of
topology
[2‐4].
If
deployed
in
a
passive
mode,
an
IDS
can
monitor
the
traffic
without
being
capable
of
applying
any
modifica<on
to
the
packets
[2‐6]
Contrarily,
the
second
type
of
monitoring
is
called
ac<ve
monitoring.
Also
named
“intrusive
monitoring”
[2‐2],
it
splits
the
network
in
two
parts
and
allows
the
packets
to
be
transmi.ed
from
one
part
to
the
other
while
monitoring
the
data.
Since
it
is
usually
installed
in
a
strategic
point
on
the
network
(choke
point),
all
the
data
must
pass
through
this
equipment
in
order
to
be
transmi.ed
to
the
Internet.
13
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-13-320.jpg)
![2
Background
This
type
of
topology
is
used
when
the
data
is
required
to
be
manipulated
before
being
transmi.ed
over
the
network
[2‐2].
For
instance,
if
the
data
has
to
be
relayed
via
a
transparent
proxy,
the
ac<ve
monitoring
can
change
the
port
and
the
des<na<on
IP
in
real
<me
to
hijack
the
packets
from
their
original
path.
Again,
it
is
also
recommended
to
deploy
the
equipment
in
a
way
that
its
existence
is
hidden
from
the
other
devices
connected
to
the
network
[2‐6].
This
<me,
decision
computer
suggests
to
use
this
topology
they
name
“bridge
mode”
to
monitor
the
ac<vity
of
a
group
composed
of
up
to
200
users
[2‐4].
NetOp<cs
underlines
that
the
devices
deployed
“in‐line”
can
introduce
excessive
latency
due
to
internal
processing
[2‐6].
Moreover,
if
the
whole
traffic
flows
through
a
single
device,
it
needs
to
be
capable
of
dealing
with
all
the
packets
in
real‐<me.
For
instance,
monitoring
a
gigabit
backbone
though
a
spanned
100
megabit
port
is
impossible
since
not
all
the
packets
will
be
seen
by
the
device
[2‐6].
Depending
on
the
case,
passive
or
ac<ve
monitoring
can
be
adopted
accordingly
[2‐6].
Most
of
the
<me,
the
monitoring
equipment
is
deployed
at
the
enterprise
firewall
in
order
to
intercept
the
whole
traffic
coming
from
and
going
to
the
Internet.
However,
the
selected
topology
must
be
able
to
absorb
the
whole
network
flow
under
all
condi<ons
and
ensure
the
network
reliability
and
availability.
To
be
fully
func<onal,
the
IDS
must
be
able
to
access
the
network
in
full
duplex
and
full‐bandwidth.
14
of
124
B.
VALENTIN
–
MSC
DISSERTATION
Illustration 2.3: Active monitoring](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-14-320.jpg)
![2
Background
2.3
Deep
Packet
Inspection
The
key
concept
of
monitoring
communica<ons
in
an
IP
network
is
how
deep
the
intercep<on
process
will
dig
into
the
packets
in
order
to
inspect
them.
Intercep<ons
can
be
performed
at
different
layers
of
the
OSI
model.
Layer
2
and
3
monitoring
systems
are
commonly
referred
to
as
“protocol
analysers”
[2‐2].
However,
most
common
E‐mail
or
webmail
services
such
as
Hotmail
and
Yahoo
are
offered
by
service
providers
instead
of
network
operators.
Network
services
are
focused
rather
on
layers
6
and
7
which
are
a
bit
higher
in
the
IP
OSI
model.
[2‐1].
Therefore,
according
to
Thomas
Porter
[2‐6],
it
is
important
to
dis<nguish
between
the
different
depths
of
packet
inspec<on
:
Shallow
packet
inspec<on
[2‐6,
2‐8]
is
the
tradi<onal
way
of
examining
the
packets,
usually
in
a
firewall
located
at
the
boundary
of
a
corporate
network.
Shallow
packet
inspec<on
is
performed
at
a
choke
point
(a
point
between
two
networks
where
all
the
packets
must
pass)
.
It
usually
provides
network
address
transla<on,
logging,
and
basic
filtering
based
on
IP
and
ports.
Since
it
only
extracts
basic
protocol
informa<on,
Shallow
packet
inspec<on
deals
with
the
headers
and
is
insufficient
to
operate
filtering
of
applica<on‐related
data
[2‐8].
Deep
packet
inspec<on
is
the
most
advanced
technology
for
iden<fying
applica<on
data
carried
by
IP
packets
[2‐7].
It
digs
deeper
in
the
content
of
the
packet
by
analysing
the
header
of
each
layer
and
the
payload
carried
by
each
packet.
In
a
sense,
one
can
say
that
DPI
is
more
applica<on
aware
[2‐8].
15
of
124
B.
VALENTIN
–
MSC
DISSERTATION
Illustration 2.4: Shallow packet inspection - data from packet headers](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-15-320.jpg)
![2
Background
If
a
non
standard
applica<on
uses
a
standard
port
such
as
port
80
to
exchange
data,
deep
packet
inspec<on
will
be
able
to
determine
it
whereas
shallow
packet
inspec<on
will
just
no<ce
that
port
80
(supposed
to
be
HTTP)
is
used.
For
instance,
a
lot
of
applica<ons
use
standard
protocols
(HTTP)
to
transmit
the
content
data.
DPI
allows
to
dis<nguish
between
the
genuine
HTTP
traffic
and
the
other
applica<ons
using
HTTP
as
a
vector
of
transmission
[2‐6].
Deep
packet
Inspec<on
na<vely
examines
each
packet
and
applies
some
predefined
filtering
rules
to
it.
Depending
on
its
content,
the
packet
can
match
with
a
rule
and
can
be
accepted
or
rejected.
The
rules
can
be
based
for
instance,
on
signature
or
regular
expression
matching.
[2‐6].
DPI
allows
any
string
of
bytes
contained
in
the
packet
to
be
compared
with
the
rules
database
in
order
for
the
IDS
to
make
a
decision.
IDS
sohware
looks
for
pa.erns
outside
from
the
defined
policy.
One
of
the
most
commonly
used
IDS
is
called
snort.
Snort
allows
the
user
to
define
par<cular
condi<ons
that
generate
alarms
upon
detec<on
of
known
pa.erns
such
as
keywords.
In
his
paper,
Dr
Thomas
Porter
also
indicates
that
the
signature
database
must
be
easily
updatable
since
it
is
dynamic
[2‐5].
Indeed,
since
the
strings
the
IDS
has
to
search
for
can
change
during
the
intercep<on
process,
it
is
important
that
new
strings
can
be
appended
to
the
signature
database.
For
instance,
the
program
called
I‐Watch,
the
FBI
used
in
1996
,
could
be
programmed
to
capture
connec<ons
that
contained
a
par<cular
keyword
[2‐7].
The
length
of
the
packets
can
differ,
depending
on
the
total
payload
they
are
carrying.
Therefore,
since
it
is
impossible
for
the
IDS
to
know
precisely
where
to
get
the
strings
to
compare,
it
can
be
a
16
of
124
B.
VALENTIN
–
MSC
DISSERTATION
Illustration 2.5: Kazaa string match analysis](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-16-320.jpg)
![2
Background
computa<onally
expensive
task
to
search
through
the
packet
for
matching
strings
[2‐5].
In
conclusion,
Deep
Packet
Inspec<on
is
a
promising
technology,
now
implemented
in
appliances
manufactured
by
the
most
popular
vendors
such
as
Microsoh,
Cisco
and
Checkpoint.
Combining
Firewall
and
IDS
in
a
single
equipment
eases
the
configura<on
and
the
management
of
the
system
[2‐5].
The
Deep
packet
Inspec<on
is
mandatory
for
an
intercep<on
system
to
be
capable
of
analyzing
the
payload
of
an
IP
packet
to
a
level
necessary
to
intercept
‐
for
example
‐
accesses
of
a
par<cular
user
to
a
par<cular
web
mail
service.
2.4
Recording
of
just
Oiltering
the
trafOic?
Depending
on
the
type
of
intercep<ons
to
put
in
place,
one
ques<on
arises.
Is
it
necessary
to
record
and
store
all
the
data
or
is
it
sufficient
to
just
filter
them
?
Simson
Garfinkel
defines
an
approach
that
he
calls
“catch
it
as
you
can”
[2‐7].
It
describes
the
process
of
recording
every
type
of
packet
transmi.ed
through
the
intercep<on
system.
Since
it
immediately
writes
the
data
to
the
disk
and
perform
analysis
aherwards,
this
approach
requires
to
use
large
disks,
usually
configured
as
RAID
systems.
Another
way
of
filtering
the
data
is
the
approach
called
“stop,
look
and
listen”
[2‐7].
It
consists
in
analyzing
the
content
data
in
real‐<me
as
it
flows
over
the
network
and
record
the
relevant
packets
only.
As
a
consequence,
large
disks
are
not
required
any
more,
but
analyzing
the
packets
on‐the‐fly
can
take
much
computa<onal
resources
again.
This
approach
was
introduced
in
the
1990s
by
Marcus
Ranum
and
used
to
be
employed
in
the
FBI
wiretapping
system
called
“Carnivore”.
Anyhow,
the
hardware
selected
for
comple<ng
the
task
of
intercep<ng
the
data,
mainly
depends
on
the
size
of
the
network
to
monitor.
For
instance,
a
66MHz
486
computer
is
enough
to
capture
the
packets
on
a
384Kbps
DSL
link
whereas
a
much
bigger
computer
would
be
required
to
do
it
on
a
fully‐loaded
gigabit
network
[2‐7].
2.5
Delivery
of
the
data
How
the
intercepted
data
has
to
be
delivered
to
the
Law
Enforcement
Agencies
is
defined
in
the
ETSI
standard
and
CALEA
(Communica<on
Assistance
for
Law
Enforcement
Act).
17
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-17-320.jpg)
![2
Background
Clearly,
the
delivery
of
data
must
ensure
that
the
flow
has
been
securely
transmi.ed
by
taking
care
of
the
following
func<ons
:
Authen<ca<on,
Confiden<ality,
Integrity,
and
Non‐repudia<on.
For
the
data
to
be
transmi.ed
securely,
Aqsacom
recommend
to
use
dedicated
circuits
or
a
Virtual
Private
Network
circuit
over
the
public
Internet
[2‐1].
Internet
is
not
a
safe
place
to
transmit
confiden<al
data.
Most
of
the
informa<on
is
transmi.ed
in
clear
text,
with
no
protec<on.
Since
the
data
resul<ng
from
an
intercep<on
is
always
very
sensi<ve,
sending
them
over
a
public
network
as
Internet
must
be
avoided.
Dedicated
circuit
is
the
most
secure
link
because
the
line
is
dedicated
to
the
communica<on
between
Law
Enforcement
and
the
ISP
that
is
doing
the
intercep<on.
Since
this
dedicated
link
has
to
be
leased,
the
result
is
a
higher
cost
for
the
LEA.
It
is
strongly
recommended
to
use
a
Virtual
Private
Network
[2‐1]
over
the
Internet
to
transmit
the
data
as
it
can
take
care
of
all
the
required
func<ons
with
no
addi<onal
cost
for
the
LEA.
In
this
case,
a
secure
tunnel
is
build
between
both
the
LEA
and
the
en<ty
performing
the
intercep<on.
All
the
data
are
transmi.ed
though
this
encrypted
path.
[2‐9]
18
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-18-320.jpg)





![3
Problem
Statement
3.2.3
Blueye
project
Finally,
with
regard
to
keyword
based
network
sniffing,
a
project
has
been
ini<ated
by
the
BL7
group
and
made
available
for
download
for
windows
and
Linux
under
GPL2
license
on
their
website
[323‐1]
.
This
project
called
Blueye
Layer
7
sniffer
aims
at
detec<ng
keywords
in
a
high‐rate
network
stream
(wired
or
wireless
links)
in
real‐<me.
Ini<ally,
this
project
has
been
designed
to
allow
the
administrators
to
monitor
the
backbone
of
their
private
company
for
security
reasons.
For
instance,
it
can
be
used
in
the
field
of
intellectual property defense to prevent internal users to send sensitive content
outside the corporate network without being noticed.
Filtering rules can be defined and the configuration of blueye can
be changed by modifying a set of text files. So far, no graphical
user interface exists to perform this task.
As
soon
as
user‐defined
keywords
are
detected,
this
layer
7
sniffer
uses
them
to
extract
valuable
and
relevant
informa<on,
rebuilds
fragmented
TCP
session
and
stores
them
on
the
hard
disk
of
the
computer.
It
can
also
issue
some
alerts
by
email
on
relevant
events.
All
the
logged
packets
are
stored
as
PCAP
files
and
also
indexed
in
a
MySQL
database
for
later
iden<fica<on
and
retrieval.
The
system
is
scalable
to
fit
the
needs
of
intercep<ng
a
mul<‐sites
network
as
well.
For
this
purpose,
it
can
be
deployed
as
a
distributed
infrastructure
composed
of
several
front‐
ends
and
one
back‐end
which
stores
all
the
records
in
a
centralized
database.
Although
Blueye
is
just
a
piece
of
sohware
and
doesn't
have
anything
to
do
with
hardware
equipment,
it
relies
on
ninjabox
plaporms
to
sniff
the
network
flow.
Ninjabox
plaporms
are
commercialized
by
a
UK‐
based
company
named
Endace.
Ninja
plaporms
are
basically
3U
appliances
equipped
with
2
intel
xeon
dual
core
CPU
and
4GB
of
internal
memory.
They
come
with
2
built‐in
1Gb/s
network
ports.
They
are
also
equipped
with
a
RAID
array
composed
of
eight
250GB
hard
drives
for
an
overall
capacity
of
2TB.
3.2.4
Drawbacks
of
existing
solutions
The
exis<ng
solu<ons
iden<fied
have
all
been
designed
with
a
specific
goal
and
for
a
special
use.
However,
they
all
provide
some
func<onali<es
that
are
needed
and
useful
for
solving
the
current
issue
of
24
of
124
B.
VALENTIN
–
MSC
DISSERTATION
Illustration 3.3: blueye logo](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-24-320.jpg)












![4
Adopted
Approach
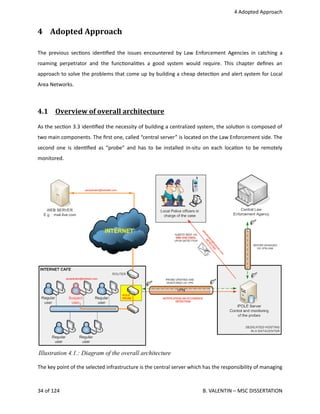
1 Hardware description
The
WRT54GL
[412‐1]
is
a
all‐in‐one
Internet‐sharing
router
from
the
manufacturer
Linksys.
This
equipment
includes
three
built‐in
modules
:
a
network
router,
a
4‐port
switch
and
a
Wireless
802.11B/G
access
point.
This
device
is
equipped
with
a
32‐bit
MIPS
architecture
Broadcom
5352EKPB
processor
opera<ng
at
200MHz
and
16
MiB
of
Random
Access
Memory.
It
also
comes
with
a
flash
memory
of
4
MiB
that
can
be
used
for
addi<onal
applica<ons.
A
wireless
chip
Broadcom
BCM43xx
802.11b/g
is
also
integrated
but
it
won't
be
used
in
the
scope
of
the
current
project.
As
this
router
is
expected
to
operate
as
a
filter
on
wired
networks,
the
wireless
part
will
be
disabled
and
the
antennas
will
be
removed.
Illustration 4.3.: Front view
Illustration 4.4.: Rear view
A
lot
of
various
versions
of
this
router
exist
[412‐1].
Some
of
them
could
have
been
used
as
well.
For
38
of
124
B.
VALENTIN
–
MSC
DISSERTATION
Illustration 4.2.: WRT54G connectivity](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-38-320.jpg)














![4
Adopted
Approach
probe
during
its
installa<on.
Here
is
an
example
of
how
to
use
the
script
to
generate
a
cer<ficate
for
a
new
probe
:
# ./mk_vpn_client Ipole05
NOTE: when you run ./clean-all, I will be doing a rm -rf on
/usr/share/doc/openvpn/examples/easy-rsa/keys
Generating a 1024 bit RSA private key
.............++++++
.++++++
writing new private key to 'Ipole05.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [FR]:
State or Province Name (full name) [IDF]:
Locality Name (eg, city) [PARIS]:
Organization Name (eg, company) [IPOLE.FR]:
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:Ipole05
Email Address [admin@ipole.fr]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
Using configuration from /usr/share/doc/openvpn/examples/easy-rsa/openssl.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'FR'
stateOrProvinceName :PRINTABLE:'IDF'
localityName :PRINTABLE:'PARIS'
organizationName :PRINTABLE:'IPOLE.FR'
commonName :PRINTABLE:'Ipole05'
emailAddress :IA5STRING:'admin@ipole.fr'
Certificate is to be certified until Apr 4 07:55:26 2018 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
Ipole05/
Ipole05/client.crt
Ipole05/client.key
Ipole05/ca.crt
Ipole05/ta.key
Ipole05/openvpn.conf
An
archive
file
is
made
available
in
the
/tmp
directory,
called
Ipole05.tgz.
This
file
contains
all
the
files
needed
for
the
probe
05
to
be
connected
to
this
VPN
server.
4.3.6
Web
pages
compression
and
installation
of
a
Web
Proxy
This
step
is
an
approach
to
solve
a
major
problem
that
may
come
up
while
filtering
web
content
in
a
network
stream
:
compression.
55
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-55-320.jpg)

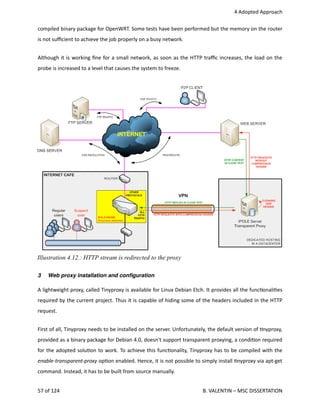
![4
Adopted
Approach
The
source
code
of
Tinyproxy
is
available
from
its
repository
on
Sourceforge
website
[425‐1].
It
is
downloaded
to
the
/tmp
directory.
Then,
the
archive
file
is
decompressed
and
the
directory
changed
to
enter
the
folder
containing
the
source
code.
cd /tmp
wget http://kent.dl.sourceforge.net/sourceforge/tinyproxy/tinyproxy-1.6.3.tar.gz
tar xvzf tinyproxy-1.6.3.tar.gz
cd tinyproxy-1.6.3
In
order
to
avoid
that
<nyproxy
appears
to
the
target
by
adding
its
name
in
the
“via”
field
of
HTTP
packets,
the
source
code
needs
to
be
modified
in
the
file
/tmp/<nyproxy‐1.6.3/reqs.c
:
Line 1022 : ''Via: %s, %hu.%hu %srn'',
Line 1030 : ''Via: %hu.%hu %srn'',
Aher
installing
the
generic
package
required
for
compila<on
(build‐essenAal),
Tinyproxy
is
being
compiled
with
the
relevant
op<ons
enabled
and
installed
as
root.
• enable‐xOnyproxy
:
Compile
in
support
for
the
X<nyproxy
header,
which
is
sent
to
any
web
server
in
the
domain
• enable‐filter
:
Allows
<nyproxy
to
filter
out
certain
domains
and
URLs
• enable‐transparent‐proxy :
Allow
<nyproxy
to
be
used
as
a
transparent
proxy
daemon
apt-get install build-essential
./configure --enable-xtinyproxy --enable-filter --enable-transparent-proxy
make
make install
The
proxy
operates
on
port
8888.
For
security
reasons,
it
is
bound
to
the
VPN
interface
and
it
is
listening
on
the
VPN
IP
address
only
(192.168.93.1).
Therefore,
it
will
allow
the
probes
connected
through
the
VPN
to
connect
(192.168.93.0/24)
and
it
won't
be
available
from
the
public
Internet.
Hence
it
would
become
an
open
proxy.
All
the
possible
HTTP
headers
[4310‐1]
have
to
be
listed
in
this
file
in
order
to
be
relayed
to
the
remote
server.
The
proxy
is
filtering
all
the
headers
that
are
commented
out
or
not
listed
.
Also,
It
is
mandatory
that
the
headers
associated
to
compression
are
inhibited.
Then,
as
the
proxy
should
not
be
iden<fied
in
case
a
web
page
is
not
found
(error
404)
for
instance,
a
blank
error
web
page
has
to
be
created.
Otherwise,
the
proxy
server
would
display
an
error
page
showing
its
name.
The
miscreant
would
have
serious
clues
that
his
data
are
relayed
through
a
proxy,
whatever
the
reason
is.
cat << FIN > /usr/local/etc/tinyproxy/default.html
58
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-58-320.jpg)


![4
Adopted
Approach
cat << FIN > /etc/syslog-ng/syslog-ng-mysql-pipe.sh
#!/bin/sh
# Take input from a FIFO and run execute it as a query for
# a mysql database.
if [ ! -e /etc/syslog-ng/mysql.syslog-ng.pipe ]; then
mkfifo --mode=666 /etc/syslog-ng/mysql.syslog-ng.pipe
chmod 666 /etc/syslog-ng/mysql.syslog-ng.pipe
else
while [ -e /etc/syslog-ng/mysql.syslog-ng.pipe ]
do
mysql -uipoleadmin --password=ipole ipole < /etc/syslog-ng/mysql.syslog-ng.pipe
done
fi
FIN
chmod +x /etc/syslog-ng/syslog-ng-mysql-pipe.sh
/etc/syslog-ng/syslog-ng-mysql-pipe.sh &
From
now
on,
the
logs
of
the
system
are
not
being
stored
in
text
files
any
more.
Instead,
all
the
logs
are
uploaded
in
a
MySQL
database.
That
will
make
a
future
selec<on
much
faster
and
easier
using
SQL
language.
4.3.8
Monitoring
the
probes
To
make
sure
not
to
miss
any
relevant
piece
of
informa<on,
It
is
really
important
that
the
probes
remain
online
on
a
permanent
basis.
Hence
the
central
Law
Enforcement
Agency
needs
to
be
informed
of
the
connec<on
status
of
each
probe
in
real
<me.
If
a
probe
comes
to
be
disconnected
in
an
Internet
cafe
under
monitoring,
due
to
an
incident
or
on
purpose
caused
by
the
manager
of
this
internet
cafe,
then
the
Police
Officers
will
need
to
know
it
and
react
immediately.
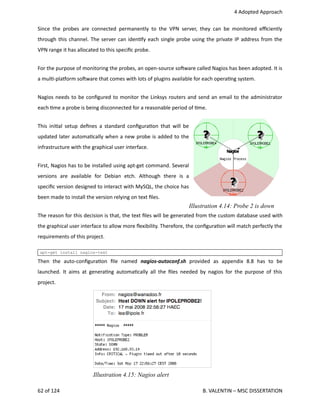
61
of
124
B.
VALENTIN
–
MSC
DISSERTATION
Illustration 4.13: Probe 2 is down on Nagios dashboard](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-61-320.jpg)


![4
Adopted
Approach
[ unknown] (1). Bruno VALENTIN <admin@ipole.fr>
[ unknown] (2) [jpeg image of size 2354]
Please decide how far you trust this user to correctly verify other users' keys
(by looking at passports, checking fingerprints from different sources, etc.)
1 = I don't know or won't say
2 = I do NOT trust
3 = I trust marginally
4 = I trust fully
5 = I trust ultimately
m = back to the main menu
Your decision? 5
Do you really want to set this key to ultimate trust? (y/N) y
pub 1024D/B66E932A created: 2002-04-20 expires: never usage: SC
trust: ultimate validity: unknown
sub 2048g/D038D198 created: 2002-04-20 expires: never usage: E
[ unknown] (1). Bruno VALENTIN <admin@ipole.fr>
[ unknown] (2) [jpeg image of size 2354]
Please note that the shown key validity is not necessarily correct
unless you restart the program.
Then
the
backup
procedure
can
be
set
up.
For
sending
the
files
to
the
server,
lhp
is
used
and
needs
to
be
installed.
apt-get install lftp
A
directory
is
created
to
store
the
backup
files
locally.
mkdir /backup
chmod 777 /backup
The
files
required
for
the
backup
procedure
to
work
properly
are
provided
as
appendix
8.3.
Those
files
are
saved
in
a
directory
called
/root/backup.
Although
the
file
backup.incl
and
backup.excl
have
been
configured
already,
they
can
be
refined
to
match
the
list
of
the
directories
to
backup.
The
backup.sh
file
contains
the
current
configura<on
for
the
backup
procedure
(gpg
key,
daemons
to
stop
and
to
restart)
and
the
backup
script
itself.
Finally,
a
cron
entry
is
added
to
execute
this
backup
task
on
a
daily
basis.
In
this
example,
the
content
of
the
server
will
be
saved
every
night
at
2
o'clock.
0 2 * * * /root/backup/backup.sh >/dev/null 2>&1
4.3.10
Securing
the
server
1 Firewall
Internet
is
a
pre.y
insecure
place.
It
is
impossible
to
trust
the
behavior
of
each
single
user
everywhere
in
the
world.
For
this
reason
it
is
recommended
to
define
a
real
security
policy
with
regards
to
who
is
permi.ed
to
access
the
server
and
from
which
loca<ons.
65
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-65-320.jpg)



![4
Adopted
Approach
Once
the
case
and
the
Police
officers
have
been
created,
the
next
step
is
to
define
the
recipients
of
no<fica<on
for
this
specific
case
(4.19).
The
number
of
recipients
is
not
limited
as
many
Police
officers
from
various
Police
units
can
deal
with
the
same
case
at
the
same
<me.
Likewise
,
the
keywords
for
the
case
can
be
defined
to
create
the
filtering
rules
which
are
immediately
uploaded
to
the
probes
(4.20).
Once
all
these
steps
are
completed,
the
global
infrastructure
should
be
up
and
running.
The
probes
should
now
be
trying
to
detect
the
occurrences
in
the
network
stream
of
each
Internet
cafe
where
they
are
installed.
New
cases
can
be
created
if
needed
and
new
probes
or
keywords
can
be
added
as
well.
4.4
Inst
allation
and
conOiguration
of
a
probe
4.4.1
Installation
of
a
Linux
operating
system
on
the
probe
For
the
purpose
of
this
project,
it
is
necessary
to
save
the
maximum
amount
of
storage
space
and
memory
on
the
router
to
make
it
capable
of
handling
the
requests
from
the
worksta<ons
on
the
LAN
and
achieving
all
the
required
func<onali<es
as
bridging,
IP
filtering
and
HTTP
request
redirec<on.
For
this
reason,
the
distribu<on
selected
to
be
installed
on
the
probes
is
OpenWRT
Whiterussian
RC6
micro,
as
it
is
the
smallest
OpenWRT
release.
Therefore
it
comes
with
a
minimal
number
of
pre‐installed
packages
so
addi<onal
applica<ons
have
to
be
installed
manually
aherwards.
The
image
of
the
distribu<on
can
be
downloaded
from
the
OpenWRT
website
[431‐1]
:
h.p://downloads.openwrt.org/whiterussian/rc6/micro/openwrt‐wrt54g‐squashfs.bin
Although
there
is
a
more
recent
version
of
OpenWRT
available
(kamikaze),
it
is
not
as
suitable
as
whiterussian
to
the
requirements
imposed
by
this
project.
In
fact,
it
is
bigger
so
there
is
not
so
much
space
leh
for
extra
applica<ons.
Aher
downloading
the
distribu<on,
the
installa<on
requires
that
the
user
connects
to
the
default
web
graphical
interface
installed
on
the
router.
As
a
DHCP
daemon
is
enabled,
connec<ng
a
computer
to
the
router
with
a
cable
and
opening
a
browser
with
the
URL
of
the
interface
(h.p://192.168.1.1)
is
sufficient.
70
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-70-320.jpg)







![4
Adopted
Approach
ipole01/83.143.24.12:2056 TLS: new session incoming connection from 83.143.24.12:2056
ipole01/83.143.24.12:2056 VERIFY OK: depth=1,
/C=FR/ST=IDF/L=PARIS/O=ipole.fr/CN=vpn.ipole.fr/emailAddress=admin@ipole.fr
ipole01/83.143.24.12:2056 VERIFY OK: depth=0,
/C=FR/ST=IDF/O=ipole.fr/CN=ipole01/emailAddress=admin@ipole.fr
ipole01/83.143.24.12:2056 Data Channel Encrypt: Cipher 'BF-CBC' initialized with 128 bit key
ipole01/83.143.24.12:2056 Data Channel Encrypt: Using 160 bit message hash 'SHA1' for HMAC
authentication
ipole01/83.143.24.12:2056 Data Channel Decrypt: Cipher 'BF-CBC' initialized with 128 bit key
ipole01/83.143.24.12:2056 Data Channel Decrypt: Using 160 bit message hash 'SHA1' for HMAC
authentication
ipole01/83.143.24.12:2056 TLS: move_session: dest=TM_ACTIVE src=TM_UNTRUSTED reinit_src=1
ipole01/83.143.24.12:2056 TLS: tls_multi_process: untrusted session promoted to trusted
ipole01/83.143.24.12:2056 Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 1024
bit RSA
ipole01/83.143.24.12:2056 PUSH: Received control message: 'PUSH_REQUEST'
ipole01/83.143.24.12:2056 SENT CONTROL [ipole01]: 'PUSH_REPLY,route 192.168.93.0
255.255.255.0,ping 10,ping-restart 60,ifconfig 192.168.93.10 192.168.93.9' (status=1)
4 OpenVPN automatic startup
If
the
VPN
connec<on
is
working
fine,
the
startup
script
to
launch
OpenVPN
automa<cally
on
startup
can
be
created
and
execu<on
of
the
script
can
be
allowed
by
se_ng
the
correct
permissions.
cat << FIN > /etc/init.d/S50Openvpn
#!/bin/sh
ntpclient -c 1 -s -h ntp.tuxfamily.net
openvpn --config /etc/openvpn/openvpn.conf --daemon
FIN
chmod 755 /etc/init.d/S50Openvpn
4.4.9
Syslog
conOiguration
As
well
as
the
decision
has
been
made
to
save
a
maximum
of
resources
on
the
router,
it
is
useful
to
avoid
satura<ng
the
memory
with
log
files.
For
this
reason,
the
logs
are
exported
to
the
central
server
through
the
VPN
connec<on.
For
this
purpose,
the
IP
of
the
server
has
to
be
set
in
the
non‐vola<le
RAM
of
the
router
nvram set log_ipaddr="192.168.93.1"
nvram commit
In
the
/etc/init.d/rcS
file,
one
op<on
is
removed
to
inform
the
Syslog
daemon
not
to
write
the
log
locally
but
rather
to
export
them
to
the
server.
syslogd -C 16 ${syslog_ip:+-L -R $syslog_ip}
# replaced by
syslogd -C 16 ${syslog_ip:+ -R $syslog_ip)
Then
the
router
can
be
rebooted
to
take
the
changes
into
considera<on
and
the
local
log
files
can
be
accessed
with
logread
to
ensure
they
are
empty.
reboot
logread
78
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-78-320.jpg)


![4
Adopted
Approach
Then
it
is
necessary
to
create
a
file
for
storing
the
rules
for
Snort.
This
file
will
be
updated
automa<cally
by
the
server
so
it
can
be
leh
empty
for
the
moment.
touch /etc/snort/rules/local.rules
Then,
the
default
op<ons
for
snort
are
defined
in
the
/etc/default/snort
file
cat << FIN > /etc/default/snort
INTERFACE="vlan0" # LAN
OPTIONS="-i $INTERFACE -c /etc/snort/snort.conf -D -N -q -s"
FIN
For
the
purpose
of
this
project,
vlan0
will
be
used
as
the
default
interface.
As
the
probe
should
be
able
to
iden<fy
the
private
IP
of
the
worksta<on
transmi_ng
the
packet
with
the
matching
payload,
it
is
using
vlan0
because
this
interface
represents
the
LAN
side
of
the
network.
The
other
op<ons
snort
is
currently
using
are
● ‐D
:
Run
Snort
in
background
mode
● ‐N
:
Turn
off
logging
(alerts
s<ll
work)
● ‐q
:
Quiet.
Don't
show
banner
and
status
report
● ‐s
:
Log
alert
messages
to
syslog
4 Automatic startup
Finally,
a
startup
script
has
to
be
created
as
done
previously
for
the
other
services
cat << FIN > /etc/init.d/S52snort
#!/bin/sh
DEFAULT=/etc/default/snort
LOG_D=/var/log/snort
RUN_D=/var/run
[ -f $DEFAULT ] && . $DEFAULT
PID_F=$RUN_D/snort_$INTERFACE.pid
case $1 in
start)
[ -d $LOG_D ] || mkdir -p $LOG_D
[ -d $RUN_D ] || mkdir -p $RUN_D
/usr/sbin/snort $OPTIONS
;;
stop)
[ -f $PID_F ] && kill $(cat $PID_F)
;;
*)
echo "usage: $0 (start|stop)"
exit 1
esac
exit $?
FIN
chmod +x /etc/init.d/S52snort
81
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-81-320.jpg)

![4
Adopted
Approach
Once
the
probe
has
booted
up
properly,
it
has
to
be
provided
with
a
new
IP
address
in
accordance
with
the
internal
IP
assignment
policy
of
the
site.
Of
course,
this
IP
address
should
not
be
allocated
to
another
network
equipment
already.
Although
it
is
not
mandatory
since
the
probe
has
to
act
as
a
bridge
between
two
networks,
alloca<ng
an
IP
address
to
this
equipment
allows
the
probe
to
access
the
Internet
and
establish
connec<on
with
the
VPN
server.
In
order
not
to
spend
much
<me
configuring
the
LAN
parameters
on
the
probe
during
the
on‐site
installa<on,
the
configura<on
script
created
in
chapter
4.4.12
is
used.
The
police
officer
in
charge
has
to
configure
his
laptop
with
the
IP
172.22.22.2,
pertaining
to
the
private
IP
range
shared
with
the
router
(chapter
4.4.4).
Using
an
SSH
client
like
pu.y
[461‐1],
he
can
connect
the
SSH
server
on
the
router,
listening
on
the
IP
172.22.22.1
port
60022.
Then
he
can
execute
the
configura<on
script
/etc/onsite_installaOon.sh
and
enter
all
the
parameters
of
the
network
he
is
currently
connected
to.
Once
this
opera<on
has
been
performed
and
the
configura<on
has
been
confirmed,
the
router
is
restarted
to
use
the
new
parameters.
The
router
is
now
connected
to
the
Internet
again
so
it
can
establish
the
connec<on
with
the
VPN
server.
4.5.2
Is
the
probe
connected
?
The
probe
is
configured
to
establish
the
connec<on
with
the
server
as
soon
as
the
Internet
is
accessible.
From
his
laptop,
the
inves<gator
can
check
that
the
probe
is
currently
connected.
Using
the
SSH
server
as
done
previously,
he
can
make
sure
that
the
VPN
tunnel
has
been
created
correctly
with
the
ifconfig
command.
A
new
network
interface
named
tun0
should
be
present
with
an
IP
address
allocated.
br0 Link encap:Ethernet HWaddr 00:18:39:C6:21:E6
inet addr:10.201.16.46 Bcast:10.255.255.255 Mask:255.0.0.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:29905 errors:0 dropped:0 overruns:0 frame:0
TX packets:12470 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:4029932 (3.8 MiB) TX bytes:2160158 (2.0 MiB)
br0:0 Link encap:Ethernet HWaddr 00:18:39:C6:21:E6
inet addr:172.22.22.1 Bcast:172.22.255.255 Mask:255.255.255.252
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
tun0 Link encap:UNSPEC HWaddr 00-00-00-00-00-00-00-00-00-00-00-00-00-00-00-00
inet addr:192.168.93.10 P-t-P:192.168.93.9 Mask:255.255.255.255
UP POINTOPOINT RUNNING NOARP MULTICAST MTU:1500 Metric:1
RX packets:2011 errors:0 dropped:0 overruns:0 frame:0
TX packets:1838 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:946908 (924.7 KiB) TX bytes:374899 (366.1 KiB)
83
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-83-320.jpg)


![5
Descrip<on
of
results
13 alteon1.34.ukl.yahoo.com (217.12.6.6) 43.528 ms 43.510 ms 44.800 ms
14 alteon1.34.ukl.yahoo.com (217.12.6.6) 43.236 ms 43.884 ms 43.909 ms
This
Traceroute,
executed
from
a
worksta<on
connected
to
Internal
LAN,
does
not
reveal
the
presence
of
the
probe.
There
is
no
prior
router
in
front
of
the
default
gateway
(10.202.16.45).
As
another
example,
during
an
FTP
connec<on
to
a
remote
FTP
site
(for
instance
sd.fw1.org),
the
IP
address
logged
by
the
des<na<on
server
should
be
the
public
IP
of
the
Internet
cafe,
not
the
IP
address
of
the
proxy.
May 16 11:22:40 sd.fw1.org proftpd[23574] sd.fw1.org (APuteaux-152-1-53-83.w82-
120.abo.wanadoo.fr[82.120.163.83]): FTP session opened.
May 16 11:22:40 sd.fw1.org proftpd[23574] sd.fw1.org (APuteaux-152-1-53-83.w82-
120.abo.wanadoo.fr[82.120.163.83]): ANON anonymous: Login successful.
May 16 11:22:40 sd.fw1.org proftpd[23574] sd.fw1.org (APuteaux-152-1-53-83.w82-
120.abo.wanadoo.fr[82.120.163.83]): Preparing to chroot to directory '/home/ftp'
May 16 11:22:40 sd.fw1.org proftpd[23574] sd.fw1.org (APuteaux-152-1-53-83.w82-
120.abo.wanadoo.fr[82.120.163.83]): FTP session closed.
May 16 11:22:52 sd.fw1.org proftpd[23577] sd.fw1.org (APuteaux-152-1-53-83.w82-
120.abo.wanadoo.fr[82.120.163.83]): FTP session opened.
May 16 11:22:52 sd.fw1.org proftpd[23577] sd.fw1.org (APuteaux-152-1-53-83.w82-
120.abo.wanadoo.fr[82.120.163.83]): ANON anonymous: Login successful.
May 16 11:22:52 sd.fw1.org proftpd[23577] sd.fw1.org (APuteaux-152-1-53-83.w82-
120.abo.wanadoo.fr[82.120.163.83]): Preparing to chroot to directory '/home/ftp'
May 16 11:22:58 sd.fw1.org proftpd[23577] sd.fw1.org (APuteaux-152-1-53-83.w82-
120.abo.wanadoo.fr[82.120.163.83]): FTP session closed.
The
above
FTP
logs
reveal
that
the
packets
have
not
been
redirected
through
any
other
server.
The
probe
has
simply
let
the
packets
go
from
the
worksta<on
to
the
router
on
the
LAN
and
then
onto
the
Internet.
5.2
Direct
HTTP
connection
without
proxy
redirection
In
the
following
example,
a
standard
connec<on
established
to
the
Live.com
website
has
been
analyzed
in
details
to
understand
what
is
the
content
of
regular
HTTP
packets
transmi.ed
from
and
to
a
common
webmail.
86
of
124
B.
VALENTIN
–
MSC
DISSERTATION
Illustration 5.1: Live.com login page](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-86-320.jpg)
![5
Descrip<on
of
results
HTTP
Request
Firefox,
the
web
browser
used
in
the
scope
of
this
analysis
clearly
indicates
in
the
HTTP
request
that
it
is
capable
of
dealing
with
compression.
Internet
explorer
and
most
common
browsers
would
have
done
the
same.
As
highlighted
below,
the
HTTP
request
contains
a
field
called
“Accept‐Encoding”
that
offers
the
remote
server
the
choice
of
compressing
the
data
prior
to
sending
them
to
the
client.
GET / HTTP/1.1
Host: www.live.com
User-Agent: Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.8.1.14) Gecko/20080418 Ubuntu/7.10
(gutsy) Firefox/2.0.0.14
Accept:
text/xml,application/xml,application/xhtml+xml,text/html;q=0.9,text/plain;q=0.8,image/png,*/*;q
=0.5
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip,deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Keep-Alive: 300
Connection: keep-alive
HTTP
Reply
As
a
consequence,
the
server
takes
this
ability
of
the
browser
in
considera<on
and
performs
a
compression
of
the
content
with
GZIP.
Of
course,
Firefox
will
decompress
the
data
prior
to
displaying
them
in
the
browser
window.
HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8
X-Powered-By: ASP.NET
P3P: CP="NON UNI COM NAV STA LOC CURa DEVa PSAa PSDa OUR IND",
policyref="http://privacy.msn.com/w3c/p3p.xml"
Vary: Accept-Encoding
Content-Encoding: gzip
Cache-Control: private, max-age=0
Date: Fri, 16 May 2008 08:47:16 GMT
Content-Length: 5860
Connection: keep-alive
Set-Cookie: SRCHUID=V=1&GUID=E733C59FA62B46158F49AC021E07DEED; expires=Mon, 20-Jul-2015
23:59:59 GMT; path=/
Set-Cookie: mkt1=norm=en-FR; domain=.live.com; path=/
Set-Cookie: mkt2=ui=en-US; domain=www.live.com; path=/
Set-Cookie: AFORM=NOFORM; expires=Mon, 20-Jul-2015 23:59:59 GMT; path=/
Set-Cookie: SFORM=NOFORM; expires=Fri, 16-May-2008 09:07:16 GMT; path=/
Set-Cookie: SRCHUSR=AUTOREDIR=0&GEOVAR=&DOB=20080516; expires=Mon, 14-May-2018 08:47:16 GMT;
path=/
Set-Cookie: SRCHSESS=GUID=65561A5906FC4B14A842B4BFA3262780&flt=0&PerfTracking=0&TS=1210927636;
expires=Fri, 16-May-2008 09:07:16 GMT; path=/
...........[yS.....~
Ey.{.e..^.).......fn%y....5..#.,..w
..t...bH.Uf...._......_.....T.G.W..|...
DQ.....I.1..+...]~Tt.........=.6...TE.G.r.h<>>j.m..f.........x.GRO..l......of..S...;..y.QB]....
(...><X..(..N....C.|
/.^T...TU.....8.H.wC..S...<.^..6..o..............7....}T.+.B...:.;.vy...4....#Vps...Bk._.C.C.L:
..D.t.z_43?.......B...i6E........_yQ.|G..b|a..Vw .|..t....k......O.Vs`...nS.M....l.9p
.[........w.
.j$>............^4.Xk..o.o
87
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-87-320.jpg)
![5
Descrip<on
of
results
Ks...Y...g..= .@6...Cpg...VA.3
*...b.).
3....Y];...[...Hs.dF.j.9}..U-.,
c...a.....j.]........Ymw.......v.......;..........v..;8;...;=..?...N.-...?
>=....Q@.U.)Q............)@e.g...c..z.r...FuV..k....-.
m.......3..67.1..........N...B;....4.......|R..6......q.7.S.....O.G...C..|
7Z.....uI.....W.....[.......t.?.....p..6.6..v...N.....":zpB.t'zN.S.Xs.&..p.'Ww.......^8..E..._
.u...Y..N.......&..L..-..Mh.y..G1.n......uq..&..d.:.......>]...A..
.Y,..N.!..I..%.4..](z...X(..~...................@.e...H.E....H|...
r..Z.xO'9.n..6...$.i.F..*._...$R.0J]..QQ......h@?.......R.Q..5.........).A.mj..a.c6
:S{..$.<.#..=`4...6.1.......i..5..%3.......#5...c;c...^..)X@}J...<<
......@#.".[.l.[.8S.,t...pA...V.n.d.....K..U...Z....vt.2...a..qO.<Bp..uf.p..u%g...p.C...Q.-...
...
T(.....7sTwG)....'<...U....".S..8....4.!.`.<......V..F[.b..[..W!.Gn.b.=9}Z...=.....{...._..4..
.....-..m.......x..
.{.F.>...I..mM.I.Iq.....u.5.Cm.../y.wh..i.'......u.U,.....
..!.rT$...r~C....nUZt.
[..*....#/K.....O0o..f.............F......!x.`,.......]..CB..cT.F.[.=^9..7r.r.l@.....b!~..
..w......g|..t6>....,...D.J.....k._K...0.....z3.....G...t.*..
....._..4...Y.)U..D....R.E.+Uj...O.s.%*.s.|.{N9.>4...M3vC.........Y....5
B............dj.^..s".c.....Y.~.zZ.`.
..i..M$Y......9..+N....;o..`.....r.X......E..-.......
..q...6.;.~..o.p.rVvHx...[`|.
<......u.)'....e.........../Hp.GP......vQ_$.i.............).e6..E..4.F...&P..Y...Z%...../.N.Zd
.8.d.NT......i..n..x..S....k+....-......]/..Gbt.*....E).%.}..."....^.(/./.@..1.].+.Rb
e...x.%%~t'...zN..nX....f>..>?.....s+ 44.#+...q<C..w./3...;./qg?.N>......2...K.23B.F.r..S...g
[.Pi..%{eE0s`...(...n.!.p.......
n...Q.5^.......x)Y=.kY{s....M.!.P....W.3s d....``t.Z...{.FKk..=.........--~.E.]..>...
.../V./#W.bA....@6.k.H..?Y.P.obq{.....}vz:..".~*.....O...7gB...}KN.s..?1.?@......|...}
`iI..^..p..J.d?_....'v*...u...........p..x..T{.k.W3g..@$......."..).n.n.n..y......Wo....#...H.
ew..#d...8...
I....x.z..OyRbI..X..MH..$..m...~.|..1..U.C..
From
a
law
enforcement
prospec<ve,
it
is
really
a
big
issue
because
the
probe
is
not
powerful
enough
to
decompress
and
filter
the
flow
in
real
<me.
Netstat
on
the
workstaOon
On
the
worksta<on,
the
list
of
ac<ve
connec<ons
reveals
that
this
computer
is
currently
connected
to
the
port
80
of
two
remote
servers.
This
means
that
the
connec<ons
are
currently
established
directly
and
no
hijacking
is
applied
to
the
request
before
sending
it.
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 127.0.0.1:631 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:25 0.0.0.0:* LISTEN
tcp 1231 0 10.1.1.29:52784 213.251.187.177:80 CLOSE_WAIT
tcp 832 0 10.1.1.29:46716 212.180.1.29:80 CLOSE_WAIT
tcp 0 0 10.1.1.29:44743 80.15.236.159:80 ESTABLISHED
tcp 1066 0 10.1.1.29:58646 213.251.187.177:80 CLOSE_WAIT
tcp 0 0 10.1.1.29:44742 80.15.236.159:80 ESTABLISHED
Netstat
on
the
central
server
A
quick
look
to
the
connec<ons
on
the
proxy
shows
that,
although
the
port
8888
is
wai<ng
for
connec<ons,
no
remote
computer
is
currently
connected
to
this
server.
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 192.168.93.1:3306 0.0.0.0:* LISTEN
88
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-88-320.jpg)


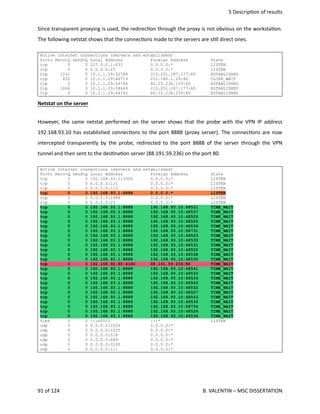
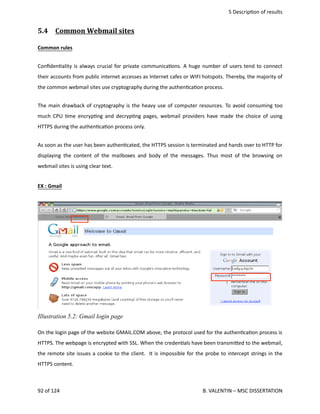
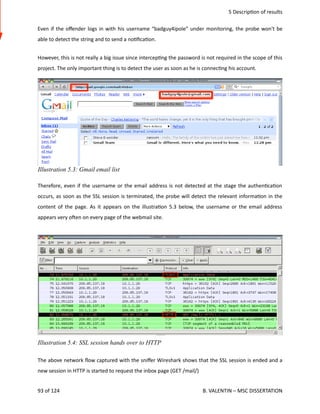
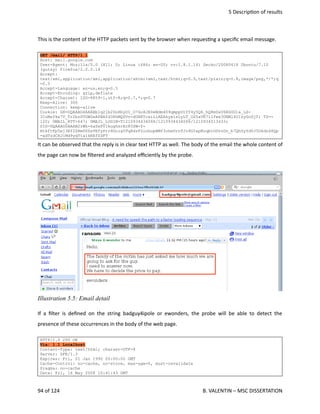
![5
Descrip<on
of
results
Set-Cookie: GMAIL_LOGIN=EXPIRED; Domain=.google.com; Expires=Thu, 15-May-08 10:41:43 GMT;
Path=/
Set-Cookie: GMAIL_AT=xn3j305qgl3irdc1uf2396j8h0j7qo; Path=/mail
Set-Cookie: S=gmail=TfV06wAO2V7F0MknZ_JrBw:gmail_yj=1QUSR9J9_rxeRkQAnPA3kw:gmproxy=Mo-
mBKR71gk:gmproxy_yj=ZMhTm5yNTD4:gmproxy_yj_sub=OGstQO-ZCLc; Path=/mail
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.01 Transitional//EN"
"http://www.w3.org/TR/html4/loose.dtd">
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<title>Gmail</title>
<link rel="shortcut icon" href="/mail/images/favicon.ico" type="image/x-icon">
<link rel="alternate" type="application/atom+xml" title="Gmail Atom Feed" href="feed/atom" />
<script><!--
var startTime=(new Date).getTime()
//-->
</script>
--- SOME TEXT HAS BEEN TRUNCATED HERE ---
</div>
<input type=text name=hist_state id=hist_state style=display:none>
<script>
var
globals={BUILD_CL:"7157386",BUILD_LABEL:"gmail_fe_503_p15",JS_VERSION:"zpuf6AhpH1w",JS_ARRAY_VE
RSION:"6",MODS:"T_k4pdTib5Lz",COOKIE_
PATH:"/mail",DEFAULT_PAGE_SIZE:50,ID_KEY:"9e9a24b29e",USER_EMAIL:"badguy4ipole@gmail.com",STYLE
SHEET_URL:"?ui=2&view=ss&ver=1dnrroapmzat8&am=T_k4pdTib5Lz",GENERAL_HELP_URL:"http://mail.googl
e.com/support/?ctx=%67mail",DBG_LOGGER_PREF:"",SHOW_BUILD_INFO:0,PRODUCT_NAME_TEXT:"Gmail",
PRODUCT_NAME_HTML:"Gmail",INIT_DATA:function(){return[["us","5b56df15058e89f2",[["l","images/2/
5/logo.png"],["n"],["m","New
features!"],["u"],["k","0"],["p","1000:500000,10,200000,5,100000,3,75000,2,0,1"],["h"]]],["ld",
[["^i",1,-1,-1,1],["^t",-1,-1,-1,1],["^b",-1,-1,-1,1],["^f",-1,-1,-1,1],["^r",-1,0,-
1,1],["^all",-1,-1,-1,1],["^s",0,-1,-1,1],["^k",-1,-1,-
1,1]],[]],["qu","0","6728","0","#006633",0,
0,0,"0","6.6"],["ft",'<span class="l73JSe" id="__fti__ic"><b>Import contacts</b></span> from
Yahoo, Outlook, and others into your Gmail contact list. <a style=color:#0000CC
target=_blank
href="http://mail.google.com/support/bin/answer.py?ctx=%67mail&hl=en&answer=8301">Learn
more</a>'],["cp",[1,1,1]],["p",["sx_tz","-120"],["sx_yjcap
s","1210886896145"],["ix_ca","1"],["sx_dl","en"],["bx_aa","1"],
["sx_pu"],["ix_pp"],["sx_sd","classic"]],["pi","Gmail","gmail_fe_503_p15","images/","html/","he
lp/","http://www.google.com/a/help/intl/en/","https://www.google.com/accounts/ManageAccount?ser
vice=mail&hl=en","en",0,,"https://www.google.com/accounts/PurchaseStorage?hl
=en","https://www.google.com/accounts/ManageStorage?hl=en","/mail/help/terms.html"],["ue",411,5
46,402,132,134,17,394,393,263,260,396,24,
385,264,304,307,443,512,444,309,445,446,311,447,312,317,316,318,186,292,295,416,421,182,301,183
,423,61,69,207,337,351,469,466,464,462,461,324,459,458,217,218,454,335,330,450,209,449,328,91,4
48,509,238,511,236,228,377,226,498,225,499,356,358,359,352,250,115,353,354,355,126,124,240,121,
363,241],["ui","badguy4ipole@gmail.com","badguy4ipole","gmail.com",0,0,"http://www.google.com/c
alendar/","https://www.google.com/accounts/ManageAccount?service=mail&hl=en",
"FR"],["uiv",50],["kb",[]],["mv",[0,"t75tfc7596rw"],[1,"12yxbiqyr77cu"]],["cfs",[],[]],["ama",-
1,5],["og",1,'<div id=gbar><nobr><span class=gb1><b>Gmail</b></span>
--- SOME TEXT HAS BEEN TRUNCATED HERE ---
<script>var VIEW_DATA=function(){return[["v","zpuf6AhpH1w","6","5b56df15058e89f2",""]
,["ub",[["^i",1210934503539]
,["^f",1210934503539]
,["^k",1210934503539]
,["^all",1210934503539]
,["^t",1210934503539]
,["^r",1210934503539]
,["^s",1210934503539]
,["^b",121093
4503539]
]
,1210934503285]
,["ti","Inbox",2,0,2,"in:inbox",[]
,"3",-1,0,2,0,[]
]
,["tb",0,2,["119ee7ffe903dc37","119ee7ffe903dc37","119ee7ffe903dc37",1,0,["^all","^i"]
,[]
95
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-95-320.jpg)
![5
Descrip<on
of
results
,"u003cspan classu003d"k62PNc" emailu003d"ewonders@yahoo.com"u003eSteve E-
wonderu003c/spanu003e","u003cbu003eu0026raquo;u003c/bu003eu0026nbsp;","ransom","Hello,
The family of the victim has just asked me how much we are going to ask for the guy. I
u0026hellip;",0,"","","May 15","Thu, May 15, 2008 at 11:32 PM",1210887184437900]
,["119ee7b98b7f5015","119ee7b98b7f5015","119ee7b98b7f5015",0,0,["^all","^i"]
,["^all","^i"]
--- SOME TEXT HAS BEEN TRUNCATED HERE ---
]
,["te"]
,["fb",["fr","Web Clip","ESPN.com","Webb spins rare 9-0 start; D-backs sweep
Rockies","http://sports.espn.go.com/mlb/recap?gameIdu003d280515129u0026amp;campaignu003drss
u0026amp;sourceu003dESPNHeadlines",,"1210918333000",]
,["fr","Web Clip","BusinessWeek Online --","US Mu0026amp;A: The Big
Thaw?","http://www.businessweek.com/investor/content/may2008/pi20080515_859749.htm?campaign_id
u003drss_daily",,"1210911540000",]
]
,["e",7,1210934503554,944,1755]
]};</script></body></html>
Yahoo
&
WindowsLive
(hotmail)
On
the
two
other
most
popular
webmail
providers
Yahoo
and
WindowsLive
(hotmail),
the
authen<ca<on
process
is
also
done
via
HTTPS.
HTTP
is
used
aherwards
to
send
the
real
content
of
the
mails.
96
of
124
B.
VALENTIN
–
MSC
DISSERTATION
Illustration 5.6: Authentication using HTTPS](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-96-320.jpg)
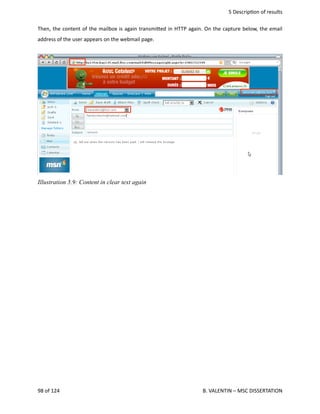





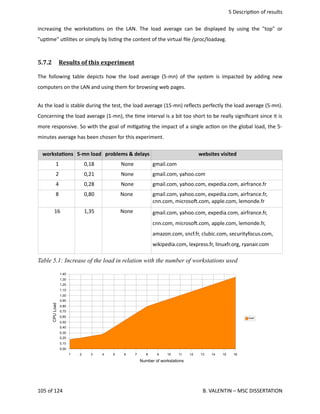
![5
Descrip<on
of
results
5.7.3
Conclusion
of
the
experiment
From
observa<on
of
the
system
load
during
this
test,
the
system
is
not
significantly
overloaded
even
with
16
computers
connected.
Whatever
the
sites
the
computers
were
browsing,
the
load
average
never
got
carried
away.
The
load
on
the
system
was
stable
during
each
step
of
the
experiment.
With
16
computers
browsing
at
a
rate
of
1
page
every
6
seconds
(rela<vely
quick
rate),
the
load
average
value
at
5
minutes
stabilizes
to
a
value
of
1.35,
which
is
not
considered
as
being
a
high
value
[57‐1].
This
is
confirmed
by
a
subjec<ve
observa<on
of
responsiveness
of
the
worksta<ons
involved.
No
problem
of
<meout
or
unusual
delay
have
been
no<ced
during
the
test.
Whatever
the
number
of
worksta<ons
(up
to
16),
the
browsing
was
s<ll
quick
and
the
browsers
got
all
the
requested
web
pages
properly
in
a
reasonable
delay
that
even
appeared
to
be
short.
Furthermore,
some
detec<on
tests
have
been
made
at
the
<me
the
load
average
value
was
1.35.
Every
<me
a
string
under
monitoring
was
sent
by
a
worksta<on
by
logging
in
to
a
webmail
for
instance,
the
no<fica<on
alerts
came
to
the
mobile
phone
within
a
maximum
<me
of
5
seconds.
Therefore,
it
can
be
stated
from
this
experiment
that
a
probe
can
take
care
of
filtering
a
16
ports
switch
with
no
par<cular
issue.
Since
most
internet
cafes
are
equipped
with
a
maximum
of
10
to
15
computers,
the
system
designed
in
the
scope
of
this
project
appears
to
be
sufficient
for
intercep<ng
keywords
on
the
LAN
of
a
cyber
cafe.
A
bigger
network
is
seldom
connected
to
a
switch
with
more
ports.
Usually,
the
network
is
segmented
in
groups
of
16
computers
connected
to
different
switches
with
the
appropriate
number
of
ports.
For
big
LANs,
a
solu<on
would
be
to
use
a
probe
for
every
single
switch.
It
means
that
this
infrastructure
could
be
used
to
monitor
a
network
composed
of
more
than
16
computers
,
even
if
the
test
has
not
been
made
so
far,
due
to
the
lack
of
availability
of
such
a
LAN
for
test
purpose.
Another
solu<on
could
be
to
replace
the
router
by
a
more
powerful
equipment
(Linksys
WRTSL54GS
at
266MHz
instead
of
200MHz
for
WRT54G)
or
by
a
laptop
opera<ng
on
Linux,
composed
of
two
network
cards
and
configured
with
the
same
packages
and
files.
This
way,
it
would
be
able
to
join
the
current
infrastructure
and
act
as
a
regular
probe.
106
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-106-320.jpg)









![7
List
of
references
7
List
of
references
Chapter
2
[2‐1] Aqsacom
–
Lawful
IntercepOon
for
IP
Networks
‐
09/2005
h.p://www.aqsacomna.com/us/index.cfm?iAr<cleID=48
[2‐2] ImageStream
–
Network
Monitoring
White
Paper
h.p://oem.imagestream.com/Monitoring_White_Paper.PDF
[2‐3] Robert
Graham
–
Sniffing
(Network
wiretap,
sniffer)
FAQ
‐
14/09/2000
h.p://web.archive.org/web/20050221103207/h.p://www.robertgraham.com/pubs/sniffing‐
faq.html
[2‐4] Decision
Computer
–
White
paper
for
E‐detecOve
system
(wired)
‐
09/2007
h.p://www.edecision4u.com/edecision4u/data/Wired_E‐Detec<ve_White_Paper.pdf
[2‐5]
Dr
Thomas
Porter
‐
The
perils
of
Deep
packet
inspecOon
‐
11/01/2005
h.p://www.securityfocus.com/infocus/1817
[2‐6] NetOpOcs
–
White
paper
:
deploying
Network
Taps
with
intrusion
detecOon
system
h.p://www.netop<cs.com/products/pdf/Taps‐and‐IDSs.pdf
[2‐7] Simson
Garfinkel
:
Network
Forensics
:
Tapping
the
Internet
‐
26/04/2002
h.p://www.oreillynet.com/pub/a/network/2002/04/26/ne.ap.html?page=1
[2‐8] Allot
CommuncaOon
:
Digging
deeper
into
Deep
Packet
InspecOon
(DPI)
‐
04/2007
h.p://www.getadvanced.net/learning/whitepapers/networkmanagement/Deep%20Packet%20I
nspec<on_White_Paper.pdf
[2‐9] CommunicaOons
Assistance
for
Law
Enforcement
Act
h.p://en.wikipedia.org/wiki/Communica<ons_Assistance_for_Law_Enforcement_Act
Chapter
3.2
117
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-117-320.jpg)
![7
List
of
references
[321‐1] Niksun
NetDetectorLive
appliance
:
h.p://www.niksun.com/NetDetectorLive.htm
[322‐1] Qosmos
Qwork
:
h.p://www.qosmos.net/rubrique.php3?id_rubrique=2
[323‐1] Blueye
project
:
h.p://www.blueye.it
Chapter
4.1
[412‐1] Hardware
versions
of
WRT54G
:
h.p://en.wikipedia.org/wiki/WRT54G
Chapter
4.2
[425‐1] Tinyproxy
website
:
h.p://<nyproxy.sourceforge.net
Chapter
4.3
[431‐1] OpenWRT
website
:
h.p://openwrt.org/
[4310‐1]
HTTP
Headers
:
h.p://www.w3.org/Protocols/rfc2616/rfc2616‐sec14.html
[4311‐1]
Ebtables
:
h.p://ebtables.sourceforge.net
Chapter
4.6
[461‐1] Pumy
:
h.p://www.chiark.greenend.org.uk/~sgtatham/pu.y/
Chapter
5.7
[57‐1] Load
average,
how
it
works
:
h.p://www.teamquest.com/resources/gunther/display/5/
118
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-118-320.jpg)
![8
Appendices
8
Appendices
8.1
Automatic
onsite
installation
script
This
script
/etc/onsite_installaOon.sh
is
intended
to
be
executed
during
the
on‐site
installa<on.
It
is
aimed
at
reconfiguring
the
main
network
parameters
to
match
those
of
the
local
network
the
probe
is
inserted
on.
#!/bin/sh
# /etc/onsite_installation.sh
echo "===================================================="
echo "This is a quick configuration script for IPole probe"
echo "It allows the probe to match the local parameters of"
echo "the LAN it is connected to"
echo "===================================================="
while [ "$all_ok" != "Y" ] && [ "$all_ok" != "y" ]
do
echo ""
echo -n "IP Address : " && read lan_ipaddr
echo -n "Netmask : " && read lan_netmask
echo -n "Gateway : " && read lan_gateway
echo -n "DNS server : " && read lan_dns
echo ""
echo -n "Is everything correct ? (Y/N) " && read all_ok
done
nvram set lan_ipaddr=$lan_ipaddr
nvram set lan_netmask=$lan_netmask
nvram set lan_gateway=$lan_gateway
nvram set lan_dns=$lan_dns
nvram commit
8.2
OpenVPN
client
conOiguration
Oile
sample
This
is
a
sample
of
a
client
configura<on
file
for
OpenVPN.
This
file
will
be
added
to
the
archive
file
generated
by
the
VPN
server
to
all
of
its
clients.
This
file
has
to
be
named
client.conf.sample
and
stored
in
the
/etc/openvpn
directory
of
the
server.
client
dev tun
proto udp
remote [IP_ADDRESS] [PORT]
resolv-retry infinite
nobind
persist-key
persist-tun
ca /etc/openvpn/ca.crt
cert /etc/openvpn/client.crt
key /etc/openvpn/client.key
tls-auth /etc/openvpn/ta.key 1
comp-lzo
verb 1
119
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-119-320.jpg)
![8
Appendices
8.3
ConOiguration
Oiles
for
the
backup
procedure
The
three
following
files
are
parts
of
the
backup
procedure.
The
script
backup.sh
is
the
backup
script
itself
and
is
configurable
by
modifying
a
set
of
op<ons.
The
two
other
scripts
define
the
directories
to
include
and
to
exclude.
8.3.1
backup.sh
#!/bin/sh
# BACKUP SCRIPT
# Options to modify
GPGRECIPIENT="admin@ipole.fr"
FTPSITE="ftpperso.free.fr"
FTPLOGIN="ftp_login"
FTPPASS="ftp_password"
# Daemons to stop and to start
STOPDAEMONS="apache2 mysql"
STARTDAEMONS="mysql apache2"
# Other options
dpkg --get-selections > /tmp/selections.txt
COMPUTER=`hostname -f`
BASEDIRECTORY="/root/backup"
DIRECTORIESLIST="$BASEDIRECTORY/backup.incl"
DIRECTORIESEXCLUDE="$BASEDIRECTORY/backup.excl"
TIMEDIR="$BASEDIRECTORY/last-full"
TAR="/bin/tar"
BACKUPDIR="/backup"
EXT="tar"
GZIP=Y
MD5=Y
VERIFY=N
DM=`date +%a`
# Backup procedure
if [ "$VERIFY" = "Y" ]
then
CHECK="--verify"
else
CHECK=""
fi
for DAEMON in $STOPDAEMONS
do
/etc/init.d/$DAEMON stop
done
cd /
NEWER=""
if [ -f $BACKUPDIR/$COMPUTER-$DM-full.$EXT ]; then
rm $BACKUPDIR/$COMPUTER-$DM-full.$EXT
fi
BKFILE=$COMPUTER-$DM-full
$TAR $NEWER $CHECK -cvpf $BACKUPDIR/$BKFILE.$EXT -X $DIRECTORIESEXCLUDE -T
$DIRECTORIESLIST
for DAEMON in $STARTDAEMONS
do
/etc/init.d/$DAEMON start
done
120
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-120-320.jpg)
![8
Appendices
if [ "$GZIP" = "Y" -a ! "$BKFILE" = "" ]
then
cd $BACKUPDIR
gzip $BKFILE.$EXT
mv $BKFILE.$EXT.gz $BKFILE.tgz
EXT="tgz"
fi
if [ "$MD5" = "Y" -a ! "$BKFILE" = "" ]
then
cd $BACKUPDIR
rm $BKFILE.$EXT.md5 2>/dev/null
md5sum $BKFILE.$EXT > $BKFILE.$EXT.md5
fi
if [ -f $BKFILE.$EXT.gpg ]
then
rm $BKFILE.$EXT.gpg
fi
gpg --encrypt -r $GPGRECIPIENT $BKFILE.$EXT
rm $BKFILE.$EXT
lftp -c 'open -u '$FTPLOGIN','$FTPPASS' -e "mirror --reverse --only-newer /backup/ /"
'$FTPSITE
8.3.2
backup.incl
/tmp/selections.txt
/etc
/root
/var/spool/cron/crontabs
/var/lib/mysql
/var/www
8.3.3
backup.excl
# empty by default
121
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-121-320.jpg)
![8
Appendices
8.4
Firewall
scripts
The
following
scripts
on.sh
and
off.sh
allow
respec<vely
to
enable
or
disable
the
firewall
on
the
server
8.4.1
on.sh
###############################
### SCRIPT ON.SH ###
###############################
#!/bin/sh
# Variables to configure to match the configuration of the server
EXT_IP="88.191.58.238"
VPN_IP="192.168.93.1"
VPN_RANGE="192.168.93.0/24"
EVERYWHERE="0/0"
# Disables the current firewall
/etc/firewall/off.sh
# No spoofing
if [ -e /proc/sys/net/ipv4/conf/all/rp_filter ]
then
for filtre in /proc/sys/net/ipv4/conf/*/rp_filter
do
echo 1 > $filtre
done
fi
# loads the required modules
modprobe ip_tables
modprobe ip_nat_ftp
modprobe ip_nat_irc
modprobe iptable_filter
modprobe iptable_nat
# flushes all existing rules
iptables -F
iptables -X
# init of NAT and MANGLE tables
iptables -t nat -F
iptables -t nat -X
iptables -t nat -P PREROUTING ACCEPT
iptables -t nat -P POSTROUTING ACCEPT
iptables -t nat -P OUTPUT ACCEPT
iptables -t mangle -F
iptables -t mangle -X
iptables -t mangle -P PREROUTING ACCEPT
iptables -t mangle -P OUTPUT ACCEPT
# how to log dropped packets
iptables -N LOG_DROP
iptables -A LOG_DROP -j LOG --log-prefix '[IPTABLES DROP] : '
iptables -A LOG_DROP -j DROP
# how to log accepted packets
iptables -N LOG_ACCEPT
iptables -A LOG_ACCEPT -j LOG --log-prefix '[IPTABLES ACCEPT] : '
iptables -A LOG_ACCEPT -j ACCEPT
# everything is dropped by default
iptables -P INPUT DROP
iptables -P OUTPUT DROP
iptables -P FORWARD DROP
122
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-122-320.jpg)

![8
Appendices
echo ""
echo "[FIREWALL ENABLED]"
8.4.2
off.sh
###############################
### SCRIPT OFF.SH ###
###############################
#!/bin/sh
# Default Policy : ACCEPT
#
iptables -P INPUT ACCEPT
iptables -P FORWARD ACCEPT
iptables -P OUTPUT ACCEPT
#
# Also for NAT table
#
iptables -t nat -P PREROUTING ACCEPT
iptables -t nat -P POSTROUTING ACCEPT
iptables -t nat -P OUTPUT ACCEPT
#
# Flushes existing rules
#
iptables -F
iptables -t nat -F
iptables -X
iptables -t nat -X
# Firewall disabled
echo "[FIREWALL DISABLED]"
124
of
124
B.
VALENTIN
–
MSC
DISSERTATION](https://image.slidesharecdn.com/ipoleprojectbrunovalentin-160818151836/85/Pattern-detection-in-a-remote-LAN-environment-EN-124-320.jpg)