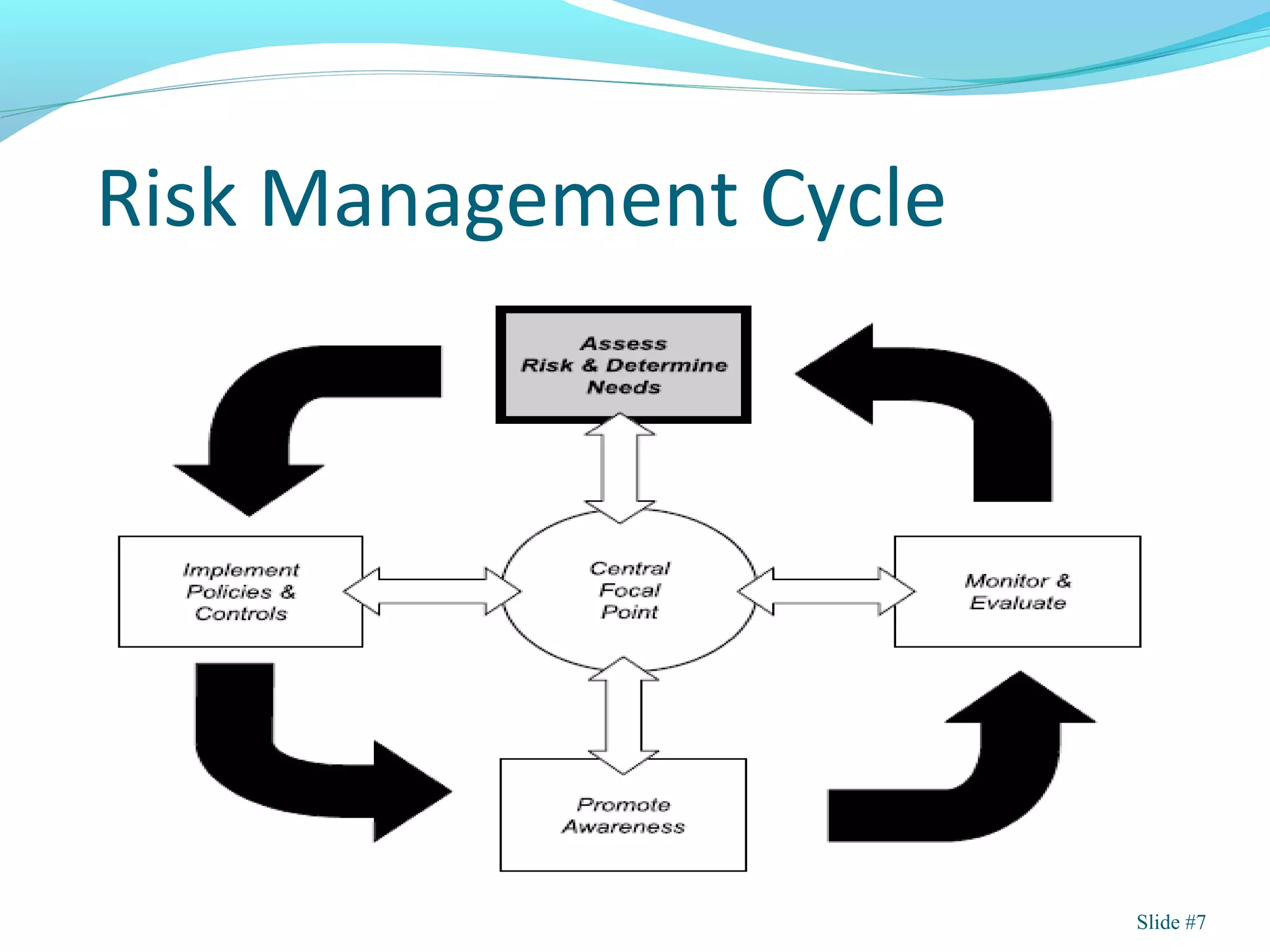
Project risk analysis involves assessing risks and uncertainties that could threaten a project. It is a component of risk management. The key aspects of project risk analysis covered in the document are:
1) Identifying assets, threats, and vulnerabilities associated with a project.
2) Determining the likelihood and potential impact of identified risks.
3) Evaluating potential controls and their costs to mitigate risks.
Both quantitative and qualitative approaches can be used, with quantitative using numbers to assess risk impact and likelihood, while qualitative uses descriptive terms. The overall goal is to understand project risks and help decision makers determine appropriate risk responses.