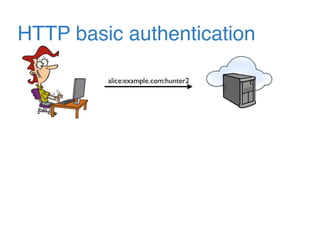
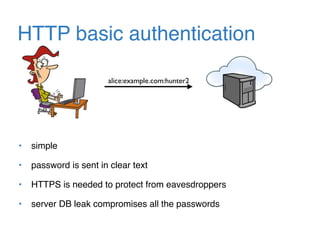
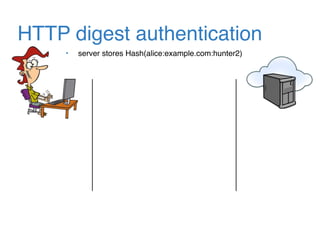
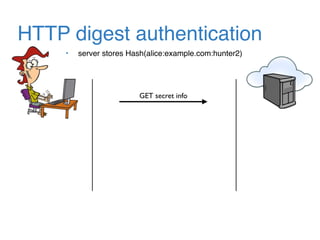
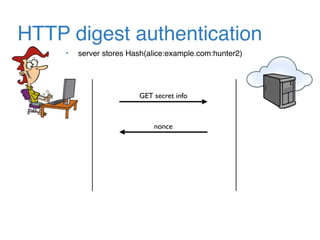
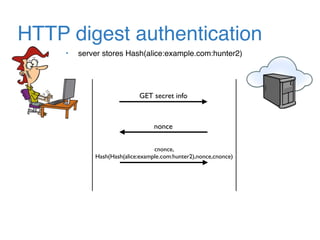
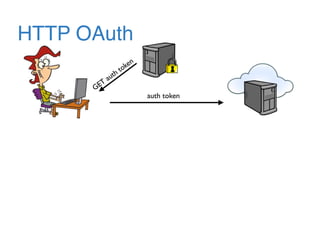
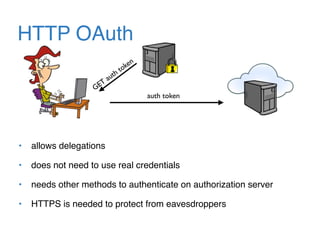
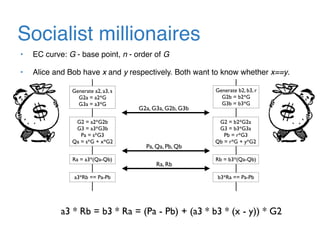
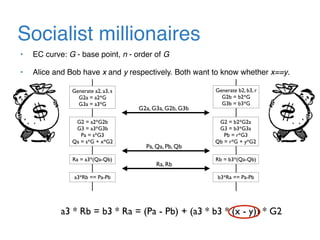
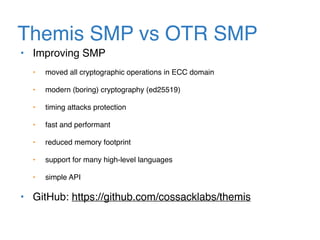
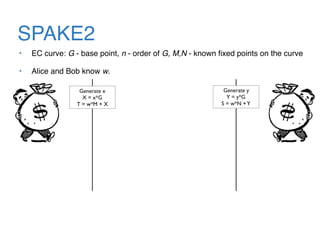
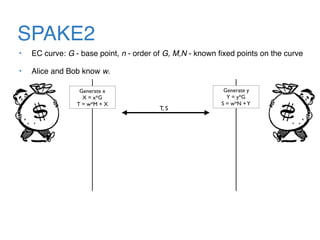
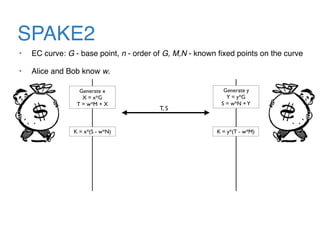
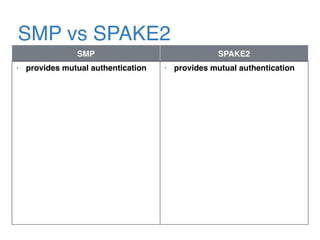
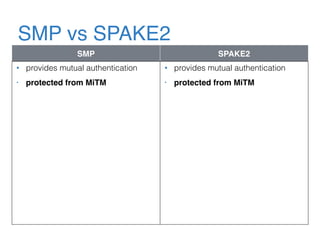
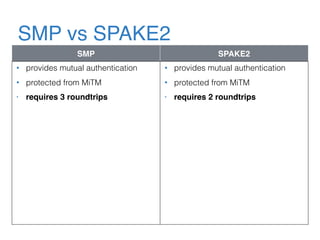
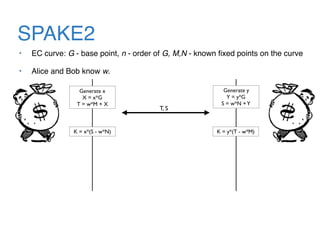
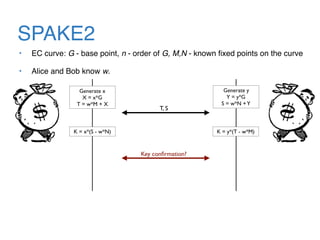
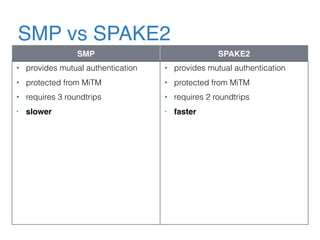
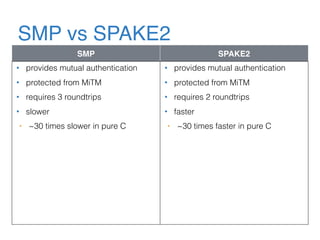
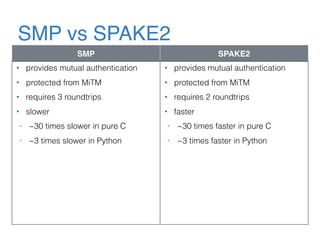
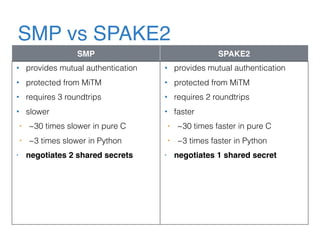
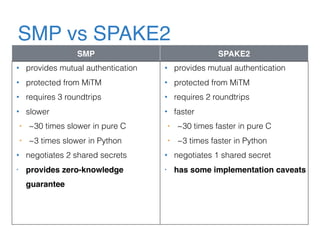
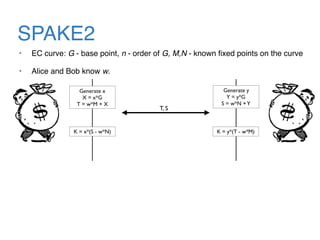
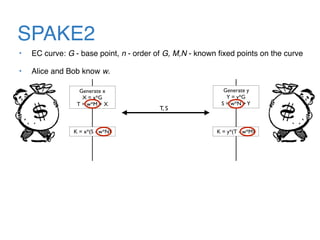
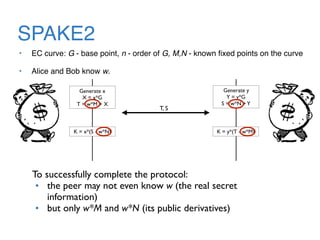
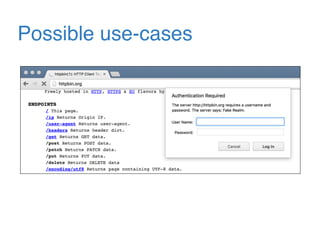
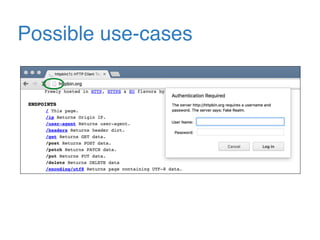
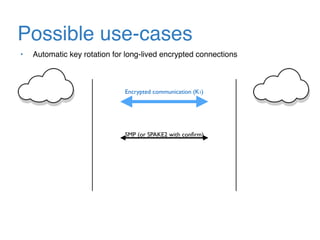
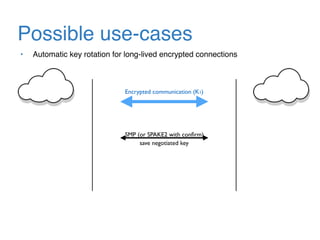
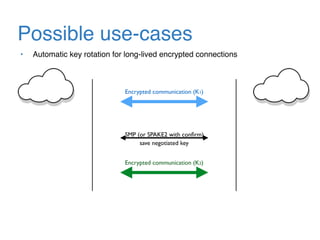
The document discusses the evolution of password authentication schemes, beginning with historical methods and moving to modern techniques such as HTTP Basic Authentication, Digest Authentication, OAuth, and password-authenticated key agreement protocols like SPAKE2. While several methods enhance security through hashing and encrypted communication, they remain vulnerable to various attacks, underscoring the need for high-entropy passwords and secure channels. It also compares the performance and security of different protocols, concluding that newer protocols offer better efficiency and security features.