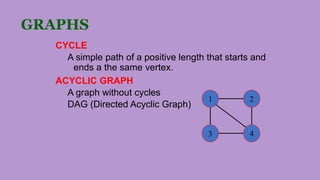
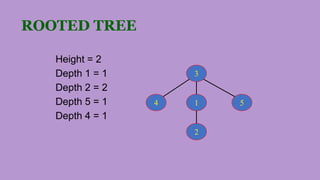
The document discusses different applications of algorithms including sorting, searching, string processing, graph problems, and numerical problems. It provides examples of algorithms for each application type, such as selection sort, bubble sort, and binary search for sorting, and breadth-first search and Dijkstra's algorithm for graphs. Key data structures are also summarized, including arrays, linked lists, stacks, queues, trees, and graphs. Common graph properties like paths, cycles, and connectivity are defined.