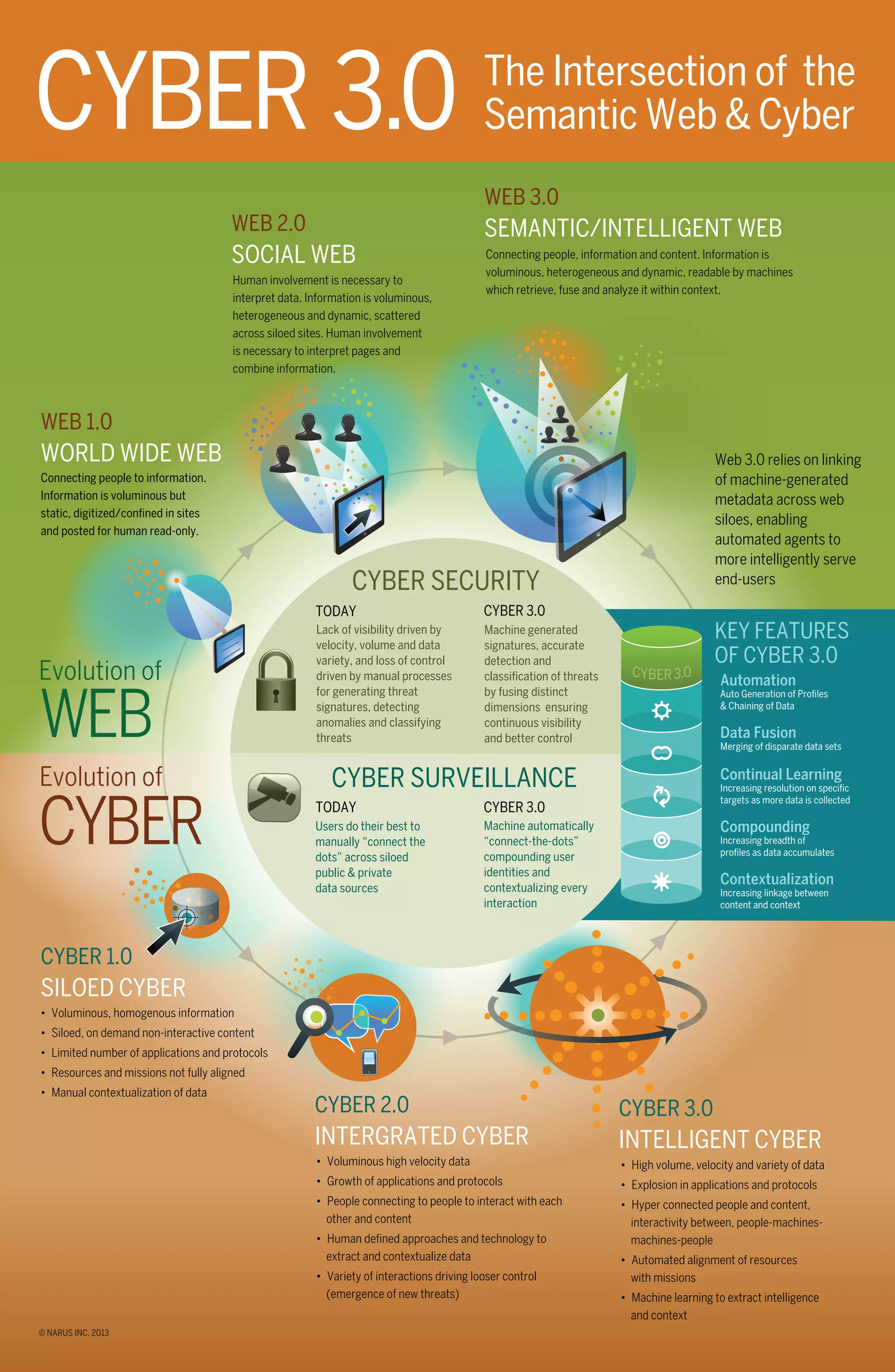
1) Cyber 3.0 relies on linking machine-generated metadata across silos to allow automated agents to more intelligently serve users.
2) It enables machines to automatically generate profiles, fuse distinct data dimensions, learn continually from more data, and automatically "connect the dots" to contextualize interactions.
3) This level of automation ensures continuous visibility and control for cyber security and surveillance by accurately detecting and classifying threats and connecting user identities across data sources.